Httpd服务入门知识-https(http over ssl)安全配置
Httpd服务入门知识-https(http over ssl)安全配置
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.SSL会话的简化过程
(1)客户端发送可供选择的加密方式,并向服务器请求证书 (2)服务器端发送证书以及选定的加密方式给客户端 (3)客户端取得证书并进行证书验证 如果信任给其发证书的CA (a)验证证书来源的合法性;用CA的公钥解密证书上数字签名 (b)验证证书的内容的合法性:完整性验证 (c)检查证书的有效期限 (d)检查证书是否被吊销 (e)证书中拥有者的名字,与访问的目标主机要一致 (4)客户端生成临时会话密钥(对称密钥),并使用服务器端的公钥加密此数据发送给服务器,完成密钥交换 (5)服务用此密钥加密用户请求的资源,响应给客户端 注意:
SSL是基于IP地址实现,单IP的主机仅可以使用一个https虚拟主机
二.使用"mode_ssl"模块实现https加密认证
1>.安装加密模块

[root@node101.yinzhengjie.org.cn ~]# yum -y install mod_ssl Loaded plugins: fastestmirror Determining fastest mirrors epel/x86_64/metalink | 7.6 kB 00:00:00 * base: mirrors.tuna.tsinghua.edu.cn * epel: mirrors.tuna.tsinghua.edu.cn * extras: mirrors.huaweicloud.com * updates: mirror.bit.edu.cn base | 3.6 kB 00:00:00 epel | 5.3 kB 00:00:00 extras | 2.9 kB 00:00:00 updates | 2.9 kB 00:00:00 (1/2): epel/x86_64/updateinfo | 1.0 MB 00:00:01 (2/2): epel/x86_64/primary_db | 6.9 MB 00:00:04 Resolving Dependencies --> Running transaction check ---> Package mod_ssl.x86_64 1:2.4.6-90.el7.centos will be installed --> Finished Dependency Resolution Dependencies Resolved ===================================================================================================================== Package Arch Version Repository Size ===================================================================================================================== Installing: mod_ssl x86_64 1:2.4.6-90.el7.centos base 112 k Transaction Summary ===================================================================================================================== Install 1 Package Total download size: 112 k Installed size: 224 k Downloading packages: mod_ssl-2.4.6-90.el7.centos.x86_64.rpm | 112 kB 00:00:00 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : 1:mod_ssl-2.4.6-90.el7.centos.x86_64 1/1 Verifying : 1:mod_ssl-2.4.6-90.el7.centos.x86_64 1/1 Installed: mod_ssl.x86_64 1:2.4.6-90.el7.centos Complete! [root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# rpm -ql mod_ssl /etc/httpd/conf.d/ssl.conf #配置apache httpd的加密 /etc/httpd/conf.modules.d/00-ssl.conf #自动加载模块的配置文件 /usr/lib64/httpd/modules/mod_ssl.so #安装了加密模块 /usr/libexec/httpd-ssl-pass-dialog /var/cache/httpd/ssl [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf.d/ssl.conf Listen 443 https SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog SSLSessionCache shmcb:/run/httpd/sslcache(512000) SSLSessionCacheTimeout 300 SSLRandomSeed startup file:/dev/urandom 256 SSLRandomSeed connect builtin SSLCryptoDevice builtin <VirtualHost _default_:443> ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLCipherSuite HIGH:3DES:!aNULL:!MD5:!SEED:!IDEA SSLCertificateFile /etc/pki/tls/certs/localhost.crt SSLCertificateKeyFile /etc/pki/tls/private/localhost.key <Files ~ "\.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> BrowserMatch "MSIE [2-5]" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log \ "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b" </VirtualHost> [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf.d/ssl.conf | grep SSLCertificateFile SSLCertificateFile /etc/pki/tls/certs/localhost.crt [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /etc/pki/tls/certs/localhost.crt -rw------- 1 root root 1493 Dec 9 17:46 /etc/pki/tls/certs/localhost.crt [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf.d/ssl.conf | grep SSLCertificateKeyFile SSLCertificateKeyFile /etc/pki/tls/private/localhost.key [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /etc/pki/tls/private/localhost.key -rw------- 1 root root 1675 Dec 9 17:46 /etc/pki/tls/private/localhost.key [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# rpm -q --scripts mod_ssl postinstall scriptlet (using /bin/sh): umask 077 if [ -f /etc/pki/tls/private/localhost.key -o -f /etc/pki/tls/certs/localhost.crt ]; then exit 0 fi /usr/bin/openssl genrsa -rand /proc/apm:/proc/cpuinfo:/proc/dma:/proc/filesystems:/proc/interrupts:/proc/ioports:/pro c/pci:/proc/rtc:/proc/uptime 2048 > /etc/pki/tls/private/localhost.key 2> /dev/null FQDN=`hostname` if [ "x${FQDN}" = "x" -o ${#FQDN} -gt 59 ]; then FQDN=localhost.localdomain fi cat << EOF | /usr/bin/openssl req -new -key /etc/pki/tls/private/localhost.key \ -x509 -sha256 -days 365 -set_serial $RANDOM -extensions v3_req \ -out /etc/pki/tls/certs/localhost.crt 2>/dev/null -- SomeState SomeCity SomeOrganization SomeOrganizationalUnit ${FQDN} root@${FQDN} EOF [root@node101.yinzhengjie.org.cn ~]#
2>.重启服务并通过https协议访问
[root@node101.yinzhengjie.org.cn ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:80 *:* LISTEN 0 128 *:22 *:* LISTEN 0 128 :::22 :::* [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl restart httpd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:80 *:* LISTEN 0 128 *:22 *:* LISTEN 0 128 *:443 *:* LISTEN 0 128 :::22 :::* [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#
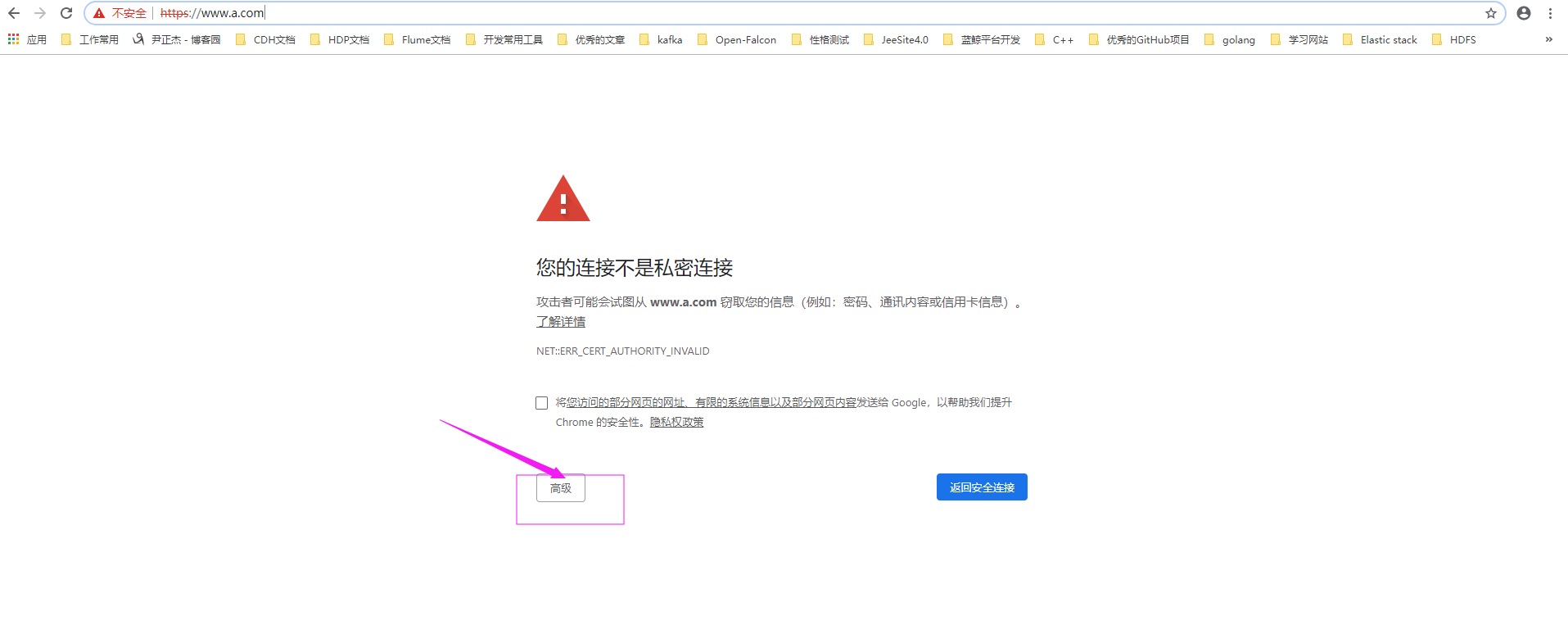
如上图所示,点击"高级",弹出如下图所示的对话框。
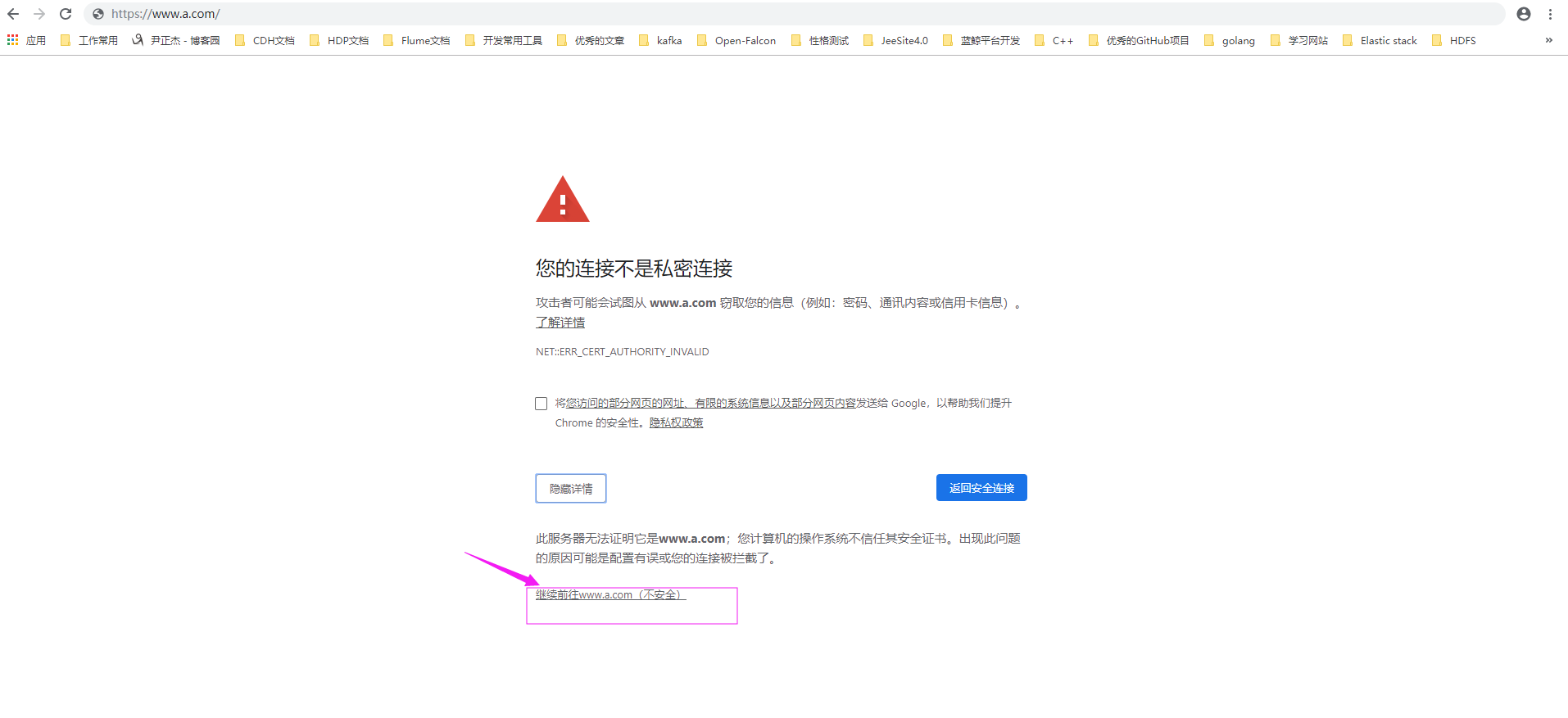
如上图所示,点击"继续前往",之后就进入到咱们自己的https服务啦。
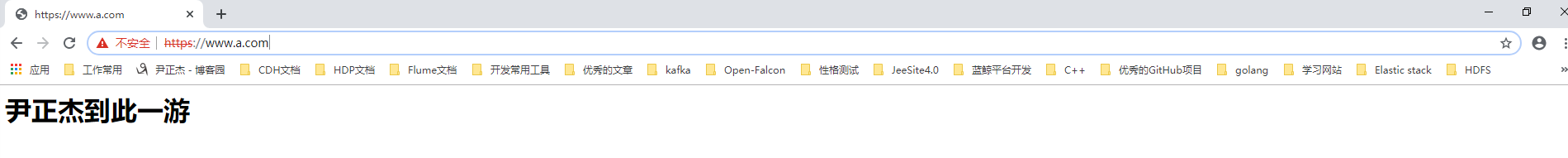
细心的小伙伴可能已经发现啦,我们虽然是基于主机名方式访问,理论上应该访问到的内容是FQDN所对应的虚拟主机,但内容却和我们预期的不服,这是什么原因呢?
这是因为SSL是基于IP地址实现,单IP的主机仅可以使用一个https虚拟主机。

[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf/httpd.conf ServerRoot "/etc/httpd" Listen 80 Include conf.modules.d/*.conf User apache Group apache ServerAdmin root@localhost <Directory /> AllowOverride none Require all denied </Directory> DocumentRoot "/var/www/html" <Directory "/var/www"> AllowOverride None Require all granted </Directory> <Directory "/var/www/html"> Options Indexes FollowSymLinks AllowOverride None Require all granted </Directory> <IfModule dir_module> DirectoryIndex index.html </IfModule> <Files ".ht*"> Require all denied </Files> ErrorLog "logs/error_log" LogLevel warn <IfModule log_config_module> LogFormat "%h %l %u %{%Y-%m-%d %H:%M:%S}t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" testlog LogFormat "%h %l %u %t \"%r\" %>s %b" common <IfModule logio_module> LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\" %I %O" combinedio </IfModule> CustomLog "logs/access_log" testlog </IfModule> <IfModule alias_module> ScriptAlias /cgi-bin/ "/var/www/cgi-bin/" </IfModule> <Directory "/var/www/cgi-bin"> AllowOverride None Options None Require all granted </Directory> <IfModule mime_module> TypesConfig /etc/mime.types AddType application/x-compress .Z AddType application/x-gzip .gz .tgz AddType text/html .shtml AddOutputFilter INCLUDES .shtml </IfModule> AddDefaultCharset UTF-8 <IfModule mime_magic_module> MIMEMagicFile conf/magic </IfModule> EnableSendfile on IncludeOptional conf.d/*.conf [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf/httpd.conf | grep ServerRoot ServerRoot "/etc/httpd" [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf/httpd.conf | grep IncludeOptional IncludeOptional conf.d/*.conf [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/virtualHost.conf <VirtualHost "*:80"> DocumentRoot "/var/www/html/asite" ServerName "www.a.com" <Directory "/var/www/html/asite"> Require all granted </Directory> CustomLog "/var/log/httpd/access_asite_log" testlog </VirtualHost> <VirtualHost "*:80"> DocumentRoot "/var/www/html/bsite" ServerName "www.b.org" <Directory "/var/www/html/bsite"> Require all granted </Directory> CustomLog "/var/log/httpd/access_bsite_log" testlog </VirtualHost> <VirtualHost "*:80"> DocumentRoot "/var/www/html/csite" ServerName "www.c.net" <Directory "/var/www/html/csite"> Require all granted </Directory> CustomLog "/var/log/httpd/access_csite_log" testlog </VirtualHost> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -t Syntax OK [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:80 *:* LISTEN 0 128 *:22 *:* LISTEN 0 128 :::22 :::* [root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/asite/index.html <h1>www.a.com</h1> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/bsite/index.html <h1>www.b.org</h1> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/csite/index.html <h1>www.c.net</h1> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/index.html #不难发现,上面的试验结果是通过访问虚拟主机的方式,但内容均被响应成该文件啦~这是由于https不支持多个虚拟主机~ <h1>尹正杰到此一游</h1> [root@node101.yinzhengjie.org.cn ~]#
三.window安装证书(上面的试验案例总是提示证书不安全,咱们为了让它绝对安全可以手动让其安装)
1>.如下图所示,点击"证书"
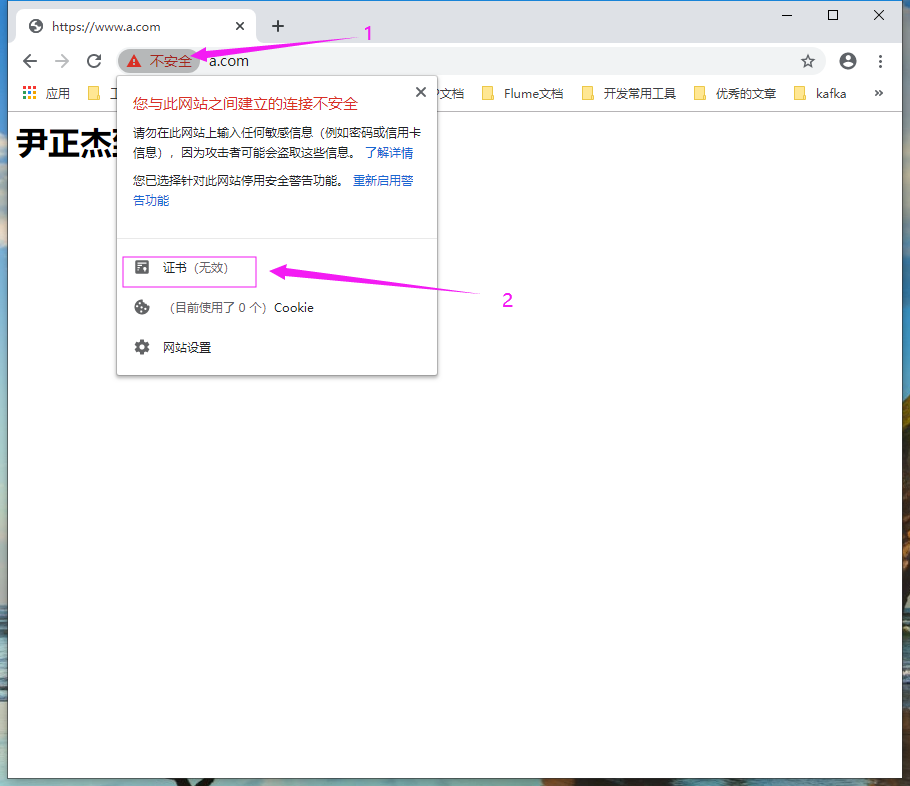
2>.点击证书对话框的"详细信息"菜单并点击"复制到文件"
3>.如下图所示,点击"下一步"

4>.如下图所示,继续点击"下一步"
5>.保存证书,并点击"下一步"

6>.如下图所示,点击"完成"后,导出证书成功
7>.双击导出的证书文件,会弹出如下所示的对话框,并点击"安装证书"
8>.如下图所示,选择"本地计算机",并点击"下一步"
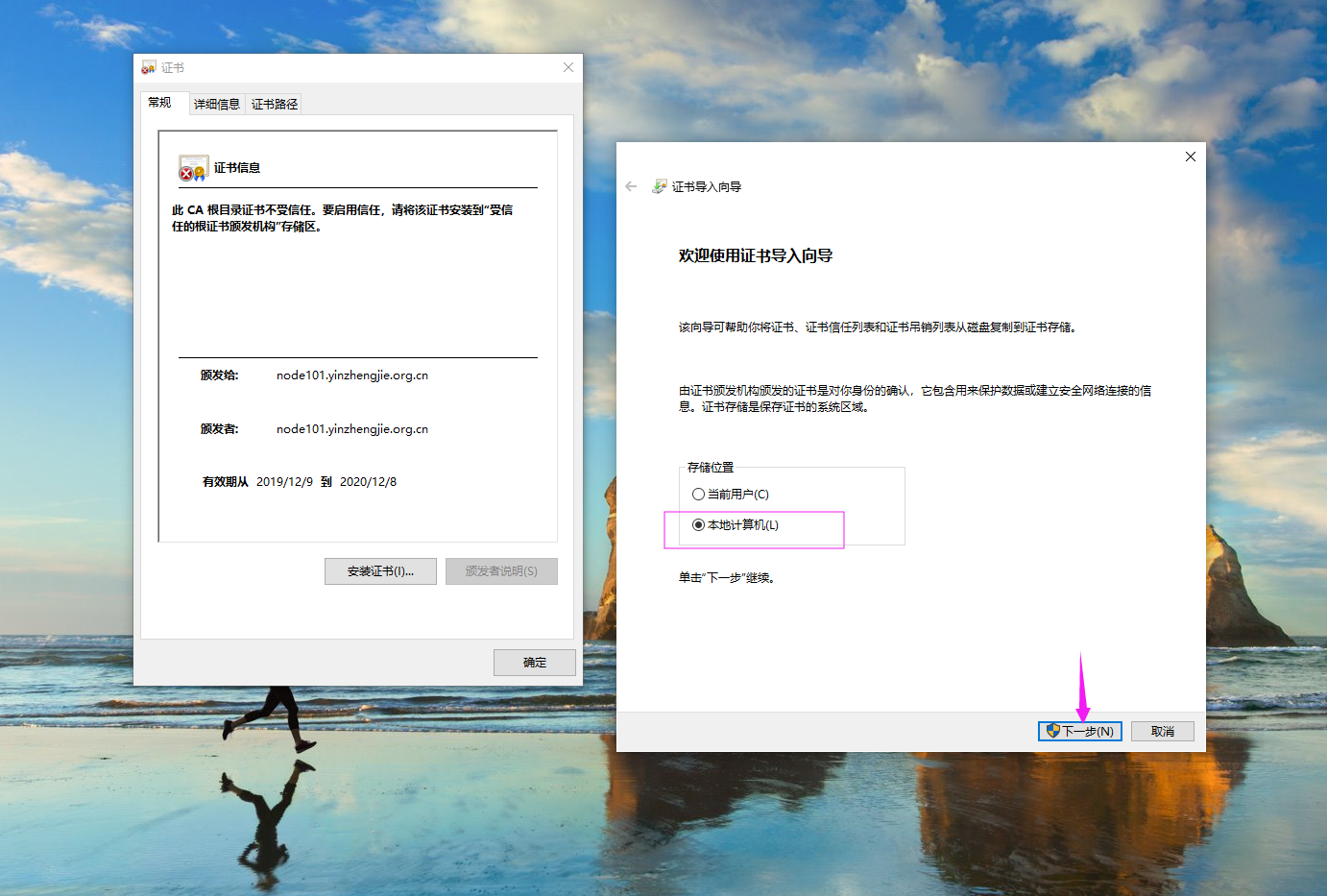
如上图所示,有两个选项,如果咱们选择的是"本地计算机",在删除时该证书时比较麻烦,因此我们推荐使用默认的选项,即"当前用户",如下图所示,点击继续。
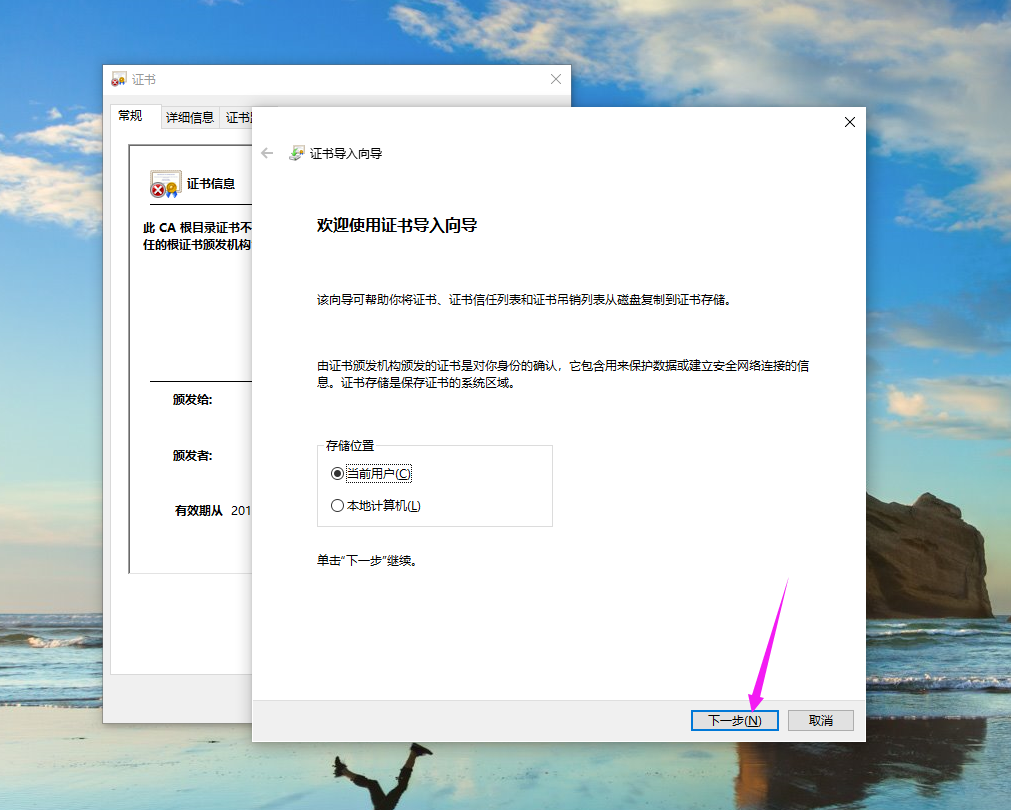
9>.如下图所示,点击"浏览"并选择"受信任的根证书颁发机构"后,再点击"下一步"
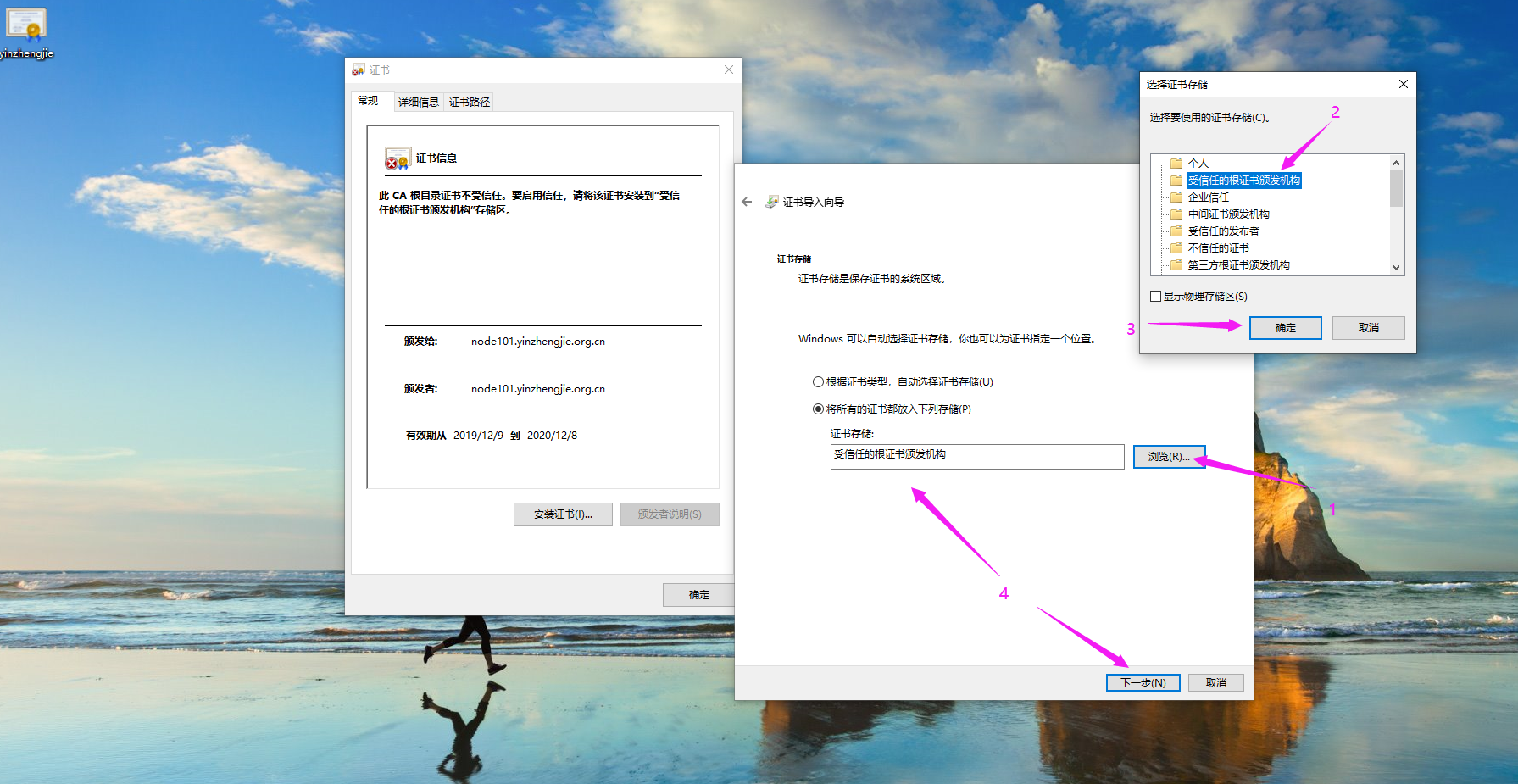
10>.如下图所示,点击"完成"
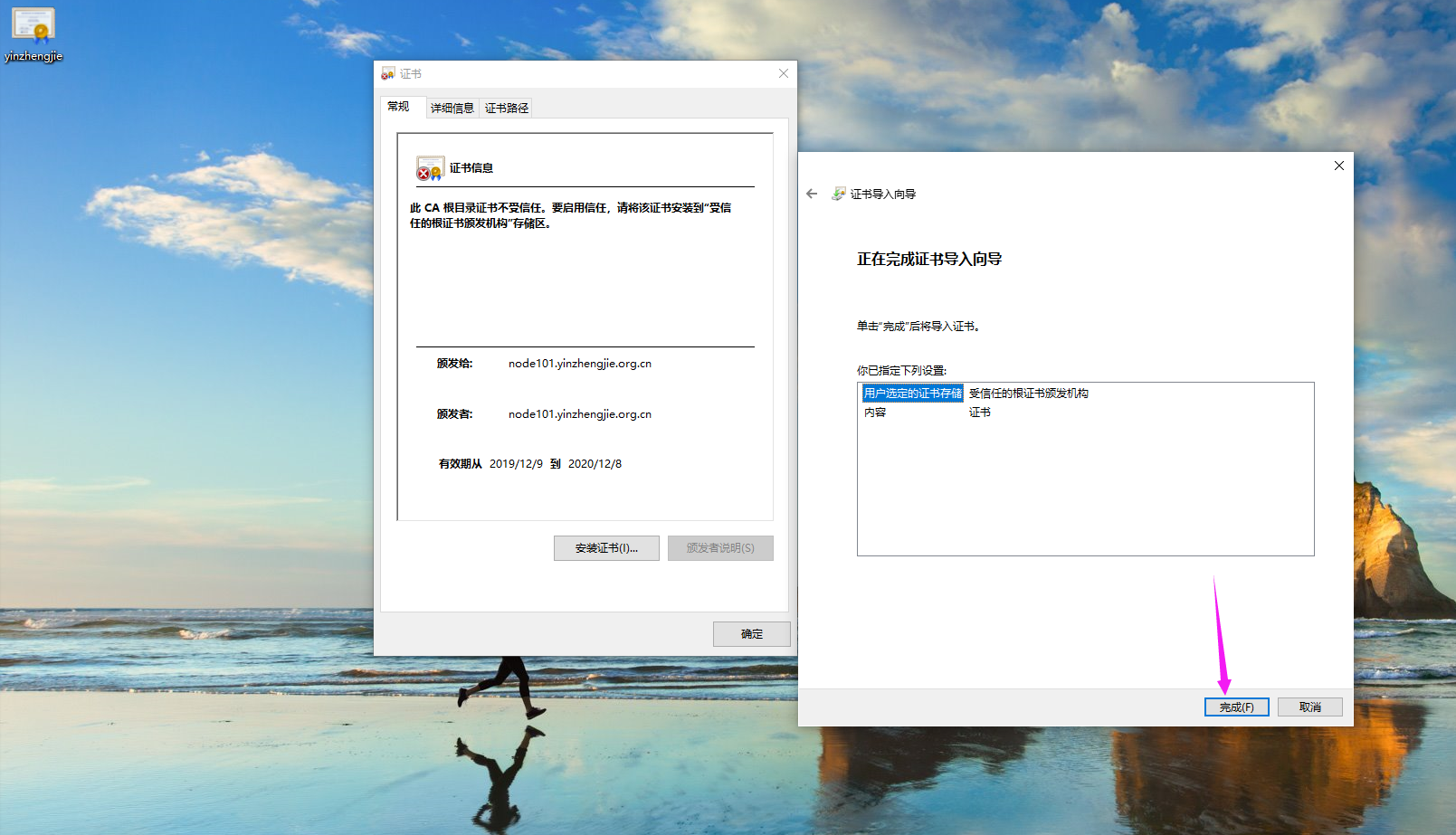
11>.成功完成证书导入
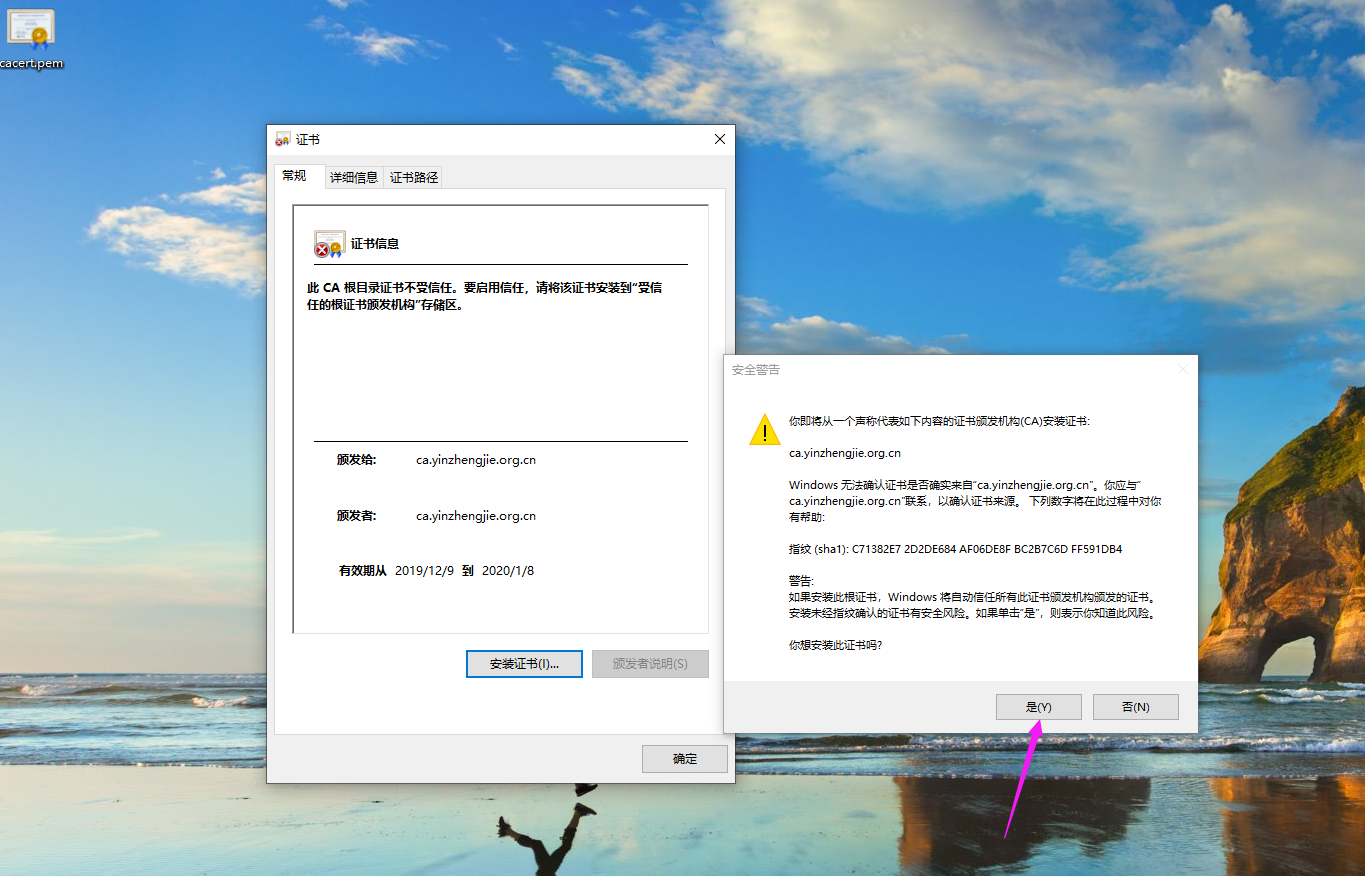
如上图所示,肯能会弹出这样的对话框,点击"是"即可完成导入。
四.删除导入的证书
1>.如下图所示,进入谷歌浏览器"设置"界面,并点击"高级"
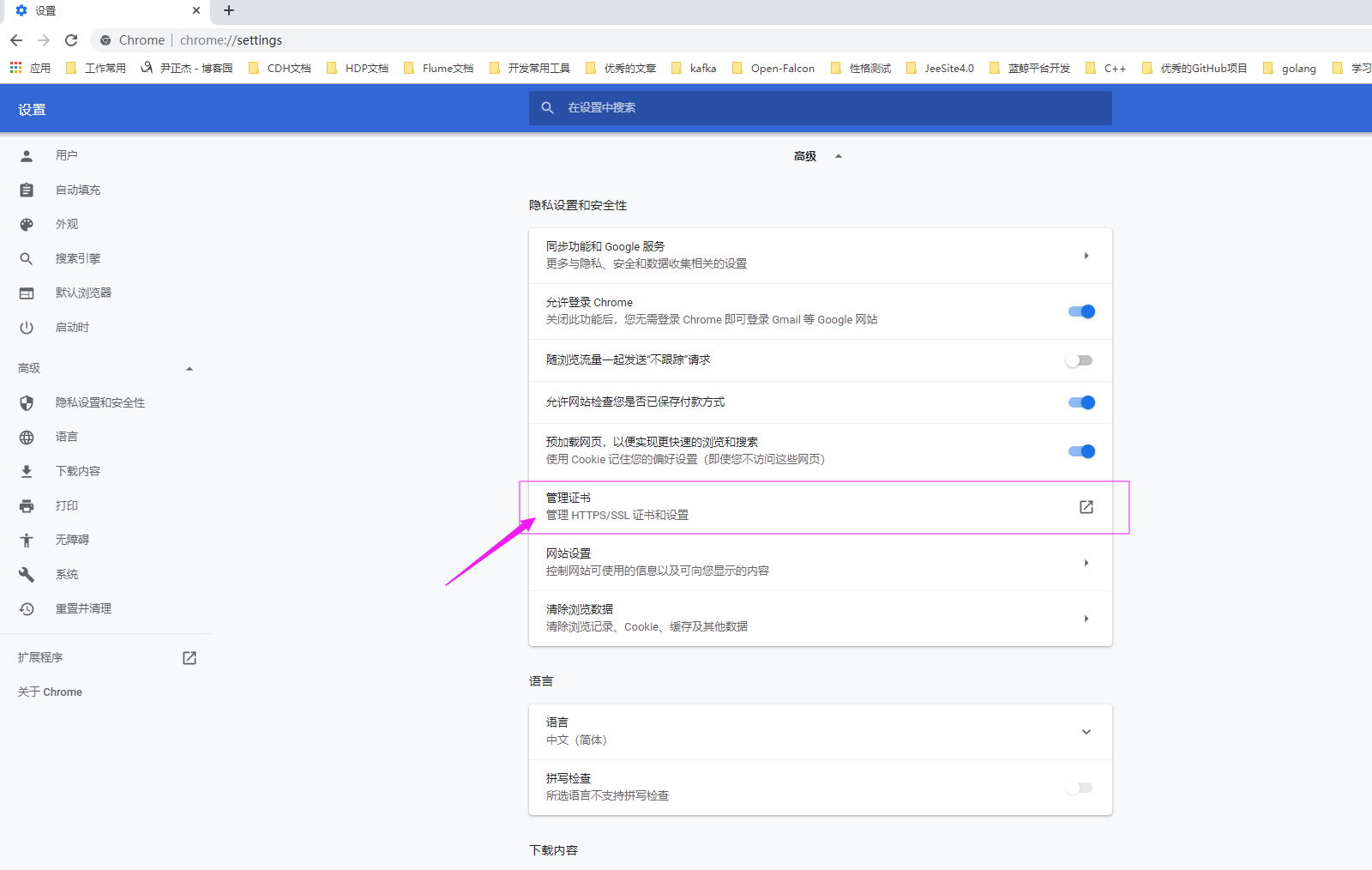
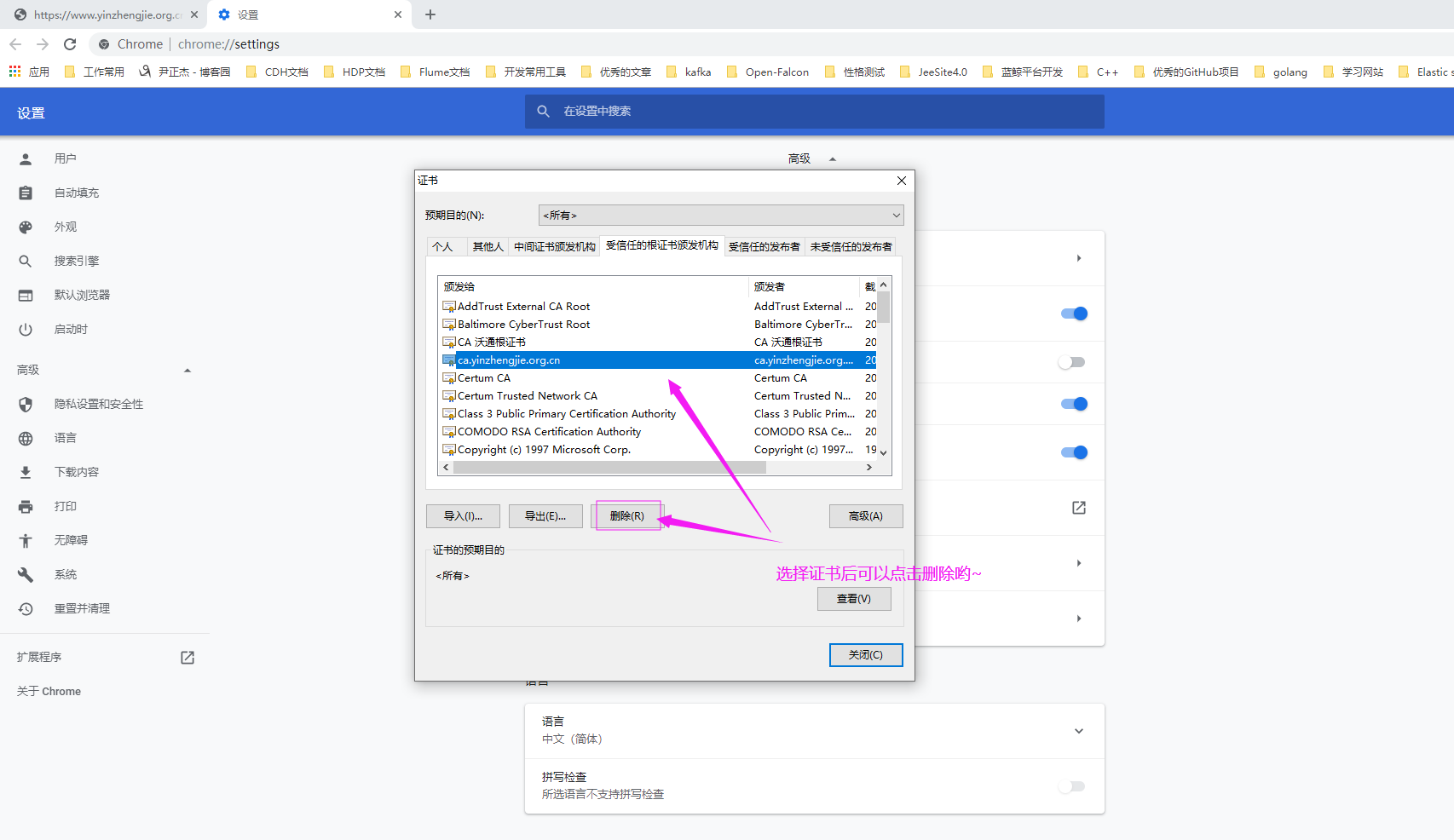
2>.如下图所示,点击"管理证书"
3>.如下图所示,选择对应的证书并删除。
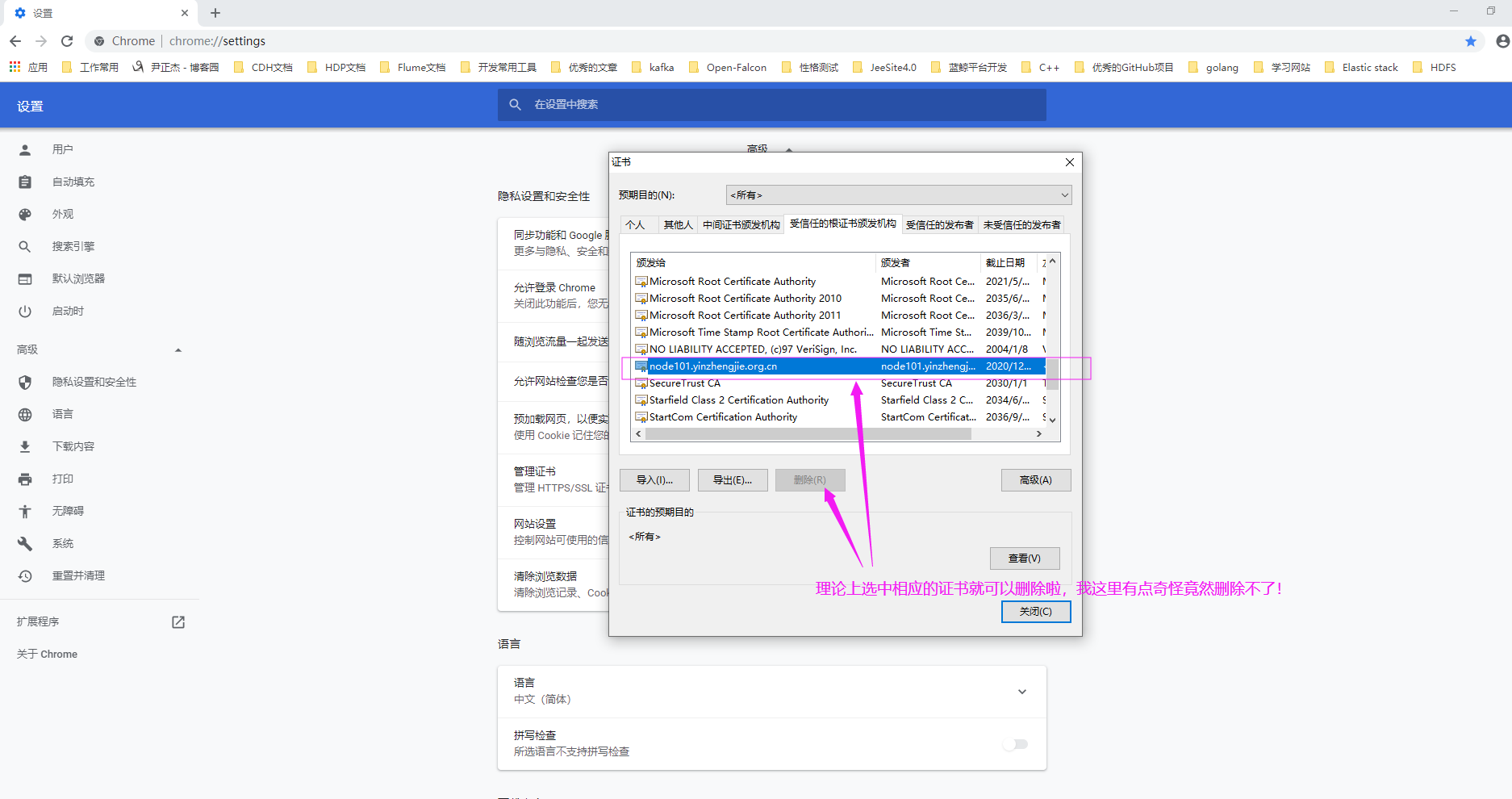
如上图所示,如果在安装证书的时候选择的是"本地计算机",则发现删除时很麻烦,无法选中删除按钮哟~ 如下图所示,如果在安装证书时选择的是默认"当前用户",则可以选择"删除按钮"。
五.通过自建CA证书实现https加密认证
1>.创建私有CA证书签名

[root@node101.yinzhengjie.org.cn ~]# yum -y install tree Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: mirrors.tuna.tsinghua.edu.cn * epel: mirrors.tuna.tsinghua.edu.cn * extras: mirrors.huaweicloud.com * updates: mirror.bit.edu.cn Resolving Dependencies --> Running transaction check ---> Package tree.x86_64 0:1.6.0-10.el7 will be installed --> Finished Dependency Resolution Dependencies Resolved ===================================================================================================================== Package Arch Version Repository Size ===================================================================================================================== Installing: tree x86_64 1.6.0-10.el7 base 46 k Transaction Summary ===================================================================================================================== Install 1 Package Total download size: 46 k Installed size: 87 k Downloading packages: tree-1.6.0-10.el7.x86_64.rpm | 46 kB 00:00:05 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : tree-1.6.0-10.el7.x86_64 1/1 Verifying : tree-1.6.0-10.el7.x86_64 1/1 Installed: tree.x86_64 0:1.6.0-10.el7 Complete! [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# cat /etc/pki/tls/openssl.cnf # # OpenSSL example configuration file. # This is mostly being used for generation of certificate requests. # # This definition stops the following lines choking if HOME isn't # defined. HOME = . RANDFILE = $ENV::HOME/.rnd # Extra OBJECT IDENTIFIER info: #oid_file = $ENV::HOME/.oid oid_section = new_oids # To use this configuration file with the "-extfile" option of the # "openssl x509" utility, name here the section containing the # X.509v3 extensions to use: # extensions = # (Alternatively, use a configuration file that has only # X.509v3 extensions in its main [= default] section.) [ new_oids ] # We can add new OIDs in here for use by 'ca', 'req' and 'ts'. # Add a simple OID like this: # testoid1=1.2.3.4 # Or use config file substitution like this: # testoid2=${testoid1}.5.6 # Policies used by the TSA examples. tsa_policy1 = 1.2.3.4.1 tsa_policy2 = 1.2.3.4.5.6 tsa_policy3 = 1.2.3.4.5.7 #################################################################### [ ca ] default_ca = CA_default # The default ca section #################################################################### [ CA_default ] dir = /etc/pki/CA # Where everything is kept certs = $dir/certs # Where the issued certs are kept crl_dir = $dir/crl # Where the issued crl are kept database = $dir/index.txt # database index file. #unique_subject = no # Set to 'no' to allow creation of # several ctificates with same subject. new_certs_dir = $dir/newcerts # default place for new certs. certificate = $dir/cacert.pem # The CA certificate serial = $dir/serial # The current serial number crlnumber = $dir/crlnumber # the current crl number # must be commented out to leave a V1 CRL crl = $dir/crl.pem # The current CRL private_key = $dir/private/cakey.pem# The private key RANDFILE = $dir/private/.rand # private random number file x509_extensions = usr_cert # The extentions to add to the cert # Comment out the following two lines for the "traditional" # (and highly broken) format. name_opt = ca_default # Subject Name options cert_opt = ca_default # Certificate field options # Extension copying option: use with caution. # copy_extensions = copy # Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs # so this is commented out by default to leave a V1 CRL. # crlnumber must also be commented out to leave a V1 CRL. # crl_extensions = crl_ext default_days = 365 # how long to certify for default_crl_days= 30 # how long before next CRL default_md = sha256 # use SHA-256 by default preserve = no # keep passed DN ordering # A few difference way of specifying how similar the request should look # For type CA, the listed attributes must be the same, and the optional # and supplied fields are just that :-) policy = policy_match # For the CA policy [ policy_match ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional # For the 'anything' policy # At this point in time, you must list all acceptable 'object' # types. [ policy_anything ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional #################################################################### [ req ] default_bits = 2048 default_md = sha256 default_keyfile = privkey.pem distinguished_name = req_distinguished_name attributes = req_attributes x509_extensions = v3_ca # The extentions to add to the self signed cert # Passwords for private keys if not present they will be prompted for # input_password = secret # output_password = secret # This sets a mask for permitted string types. There are several options. # default: PrintableString, T61String, BMPString. # pkix : PrintableString, BMPString (PKIX recommendation before 2004) # utf8only: only UTF8Strings (PKIX recommendation after 2004). # nombstr : PrintableString, T61String (no BMPStrings or UTF8Strings). # MASK:XXXX a literal mask value. # WARNING: ancient versions of Netscape crash on BMPStrings or UTF8Strings. string_mask = utf8only # req_extensions = v3_req # The extensions to add to a certificate request [ req_distinguished_name ] countryName = Country Name (2 letter code) countryName_default = XX countryName_min = 2 countryName_max = 2 stateOrProvinceName = State or Province Name (full name) #stateOrProvinceName_default = Default Province localityName = Locality Name (eg, city) localityName_default = Default City 0.organizationName = Organization Name (eg, company) 0.organizationName_default = Default Company Ltd # we can do this but it is not needed normally :-) #1.organizationName = Second Organization Name (eg, company) #1.organizationName_default = World Wide Web Pty Ltd organizationalUnitName = Organizational Unit Name (eg, section) #organizationalUnitName_default = commonName = Common Name (eg, your name or your server\'s hostname) commonName_max = 64 emailAddress = Email Address emailAddress_max = 64 # SET-ex3 = SET extension number 3 [ req_attributes ] challengePassword = A challenge password challengePassword_min = 4 challengePassword_max = 20 unstructuredName = An optional company name [ usr_cert ] # These extensions are added when 'ca' signs a request. # This goes against PKIX guidelines but some CAs do it and some software # requires this to avoid interpreting an end user certificate as a CA. basicConstraints=CA:FALSE # Here are some examples of the usage of nsCertType. If it is omitted # the certificate can be used for anything *except* object signing. # This is OK for an SSL server. # nsCertType = server # For an object signing certificate this would be used. # nsCertType = objsign # For normal client use this is typical # nsCertType = client, email # and for everything including object signing: # nsCertType = client, email, objsign # This is typical in keyUsage for a client certificate. # keyUsage = nonRepudiation, digitalSignature, keyEncipherment # This will be displayed in Netscape's comment listbox. nsComment = "OpenSSL Generated Certificate" # PKIX recommendations harmless if included in all certificates. subjectKeyIdentifier=hash authorityKeyIdentifier=keyid,issuer # This stuff is for subjectAltName and issuerAltname. # Import the email address. # subjectAltName=email:copy # An alternative to produce certificates that aren't # deprecated according to PKIX. # subjectAltName=email:move # Copy subject details # issuerAltName=issuer:copy #nsCaRevocationUrl = http://www.domain.dom/ca-crl.pem #nsBaseUrl #nsRevocationUrl #nsRenewalUrl #nsCaPolicyUrl #nsSslServerName # This is required for TSA certificates. # extendedKeyUsage = critical,timeStamping [ v3_req ] # Extensions to add to a certificate request basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment [ v3_ca ] # Extensions for a typical CA # PKIX recommendation. subjectKeyIdentifier=hash authorityKeyIdentifier=keyid:always,issuer # This is what PKIX recommends but some broken software chokes on critical # extensions. #basicConstraints = critical,CA:true # So we do this instead. basicConstraints = CA:true # Key usage: this is typical for a CA certificate. However since it will # prevent it being used as an test self-signed certificate it is best # left out by default. # keyUsage = cRLSign, keyCertSign # Some might want this also # nsCertType = sslCA, emailCA # Include email address in subject alt name: another PKIX recommendation # subjectAltName=email:copy # Copy issuer details # issuerAltName=issuer:copy # DER hex encoding of an extension: beware experts only! # obj=DER:02:03 # Where 'obj' is a standard or added object # You can even override a supported extension: # basicConstraints= critical, DER:30:03:01:01:FF [ crl_ext ] # CRL extensions. # Only issuerAltName and authorityKeyIdentifier make any sense in a CRL. # issuerAltName=issuer:copy authorityKeyIdentifier=keyid:always [ proxy_cert_ext ] # These extensions should be added when creating a proxy certificate # This goes against PKIX guidelines but some CAs do it and some software # requires this to avoid interpreting an end user certificate as a CA. basicConstraints=CA:FALSE # Here are some examples of the usage of nsCertType. If it is omitted # the certificate can be used for anything *except* object signing. # This is OK for an SSL server. # nsCertType = server # For an object signing certificate this would be used. # nsCertType = objsign # For normal client use this is typical # nsCertType = client, email # and for everything including object signing: # nsCertType = client, email, objsign # This is typical in keyUsage for a client certificate. # keyUsage = nonRepudiation, digitalSignature, keyEncipherment # This will be displayed in Netscape's comment listbox. nsComment = "OpenSSL Generated Certificate" # PKIX recommendations harmless if included in all certificates. subjectKeyIdentifier=hash authorityKeyIdentifier=keyid,issuer # This stuff is for subjectAltName and issuerAltname. # Import the email address. # subjectAltName=email:copy # An alternative to produce certificates that aren't # deprecated according to PKIX. # subjectAltName=email:move # Copy subject details # issuerAltName=issuer:copy #nsCaRevocationUrl = http://www.domain.dom/ca-crl.pem #nsBaseUrl #nsRevocationUrl #nsRenewalUrl #nsCaPolicyUrl #nsSslServerName # This really needs to be in place for it to be a proxy certificate. proxyCertInfo=critical,language:id-ppl-anyLanguage,pathlen:3,policy:foo #################################################################### [ tsa ] default_tsa = tsa_config1 # the default TSA section [ tsa_config1 ] # These are used by the TSA reply generation only. dir = ./demoCA # TSA root directory serial = $dir/tsaserial # The current serial number (mandatory) crypto_device = builtin # OpenSSL engine to use for signing signer_cert = $dir/tsacert.pem # The TSA signing certificate # (optional) certs = $dir/cacert.pem # Certificate chain to include in reply # (optional) signer_key = $dir/private/tsakey.pem # The TSA private key (optional) default_policy = tsa_policy1 # Policy if request did not specify it # (optional) other_policies = tsa_policy2, tsa_policy3 # acceptable policies (optional) digests = sha1, sha256, sha384, sha512 # Acceptable message digests (mandatory) accuracy = secs:1, millisecs:500, microsecs:100 # (optional) clock_precision_digits = 0 # number of digits after dot. (optional) ordering = yes # Is ordering defined for timestamps? # (optional, default: no) tsa_name = yes # Must the TSA name be included in the reply? # (optional, default: no) ess_cert_id_chain = no # Must the ESS cert id chain be included? # (optional, default: no) [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# tree /etc/pki/CA/ /etc/pki/CA/ ├── certs ├── crl ├── newcerts └── private directories, 0 files [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# (umask 066;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) #创建证书的私钥文件 Generating RSA private key, 2048 bit long modulus .....+++ .........+++ e is 65537 (0x10001) [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# tree /etc/pki/CA/ /etc/pki/CA/ ├── certs ├── crl ├── newcerts └── private └── cakey.pem directories, 1 file [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# tree /etc/pki/CA/ /etc/pki/CA/ ├── certs ├── crl ├── newcerts └── private └── cakey.pem 4 directories, 1 file [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem #生成自签名证书 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:www.yinzhengjie.org.cn Organizational Unit Name (eg, section) []:devops Common Name (eg, your name or your server's hostname) []:ca.yinzhengjie.org.cn Email Address []: [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# tree /etc/pki/CA/ /etc/pki/CA/ ├── cacert.pem ├── certs ├── crl ├── newcerts └── private └── cakey.pem 4 directories, 2 files [root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# touch /etc/pki/CA/index.txt #数据库索引文件,创建出来就好,后面位整数签名时程序会自动往里面写入数据 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# echo 01 > /etc/pki/CA/serial #指定下一个申请整数的编号 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# tree /etc/pki/CA/ /etc/pki/CA/ ├── cacert.pem ├── certs ├── crl ├── index.txt ├── newcerts ├── private │ └── cakey.pem └── serial 4 directories, 4 files [root@node101.yinzhengjie.org.cn ~]#
2>.为httpd服务器申请数字证书
[root@node101.yinzhengjie.org.cn ~]# mkdir /etc/httpd/conf.d/ssl #创建存放证书相关文件目录 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cd /etc/httpd/conf.d/ssl/ [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# (umask 077;openssl genrsa -out httpd.key 1024) #生成私钥文件 Generating RSA private key, 1024 bit long modulus .................++++++ ............++++++ e is 65537 (0x10001) [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# openssl req -new -key httpd.key -out httpd.csr #生成证书申请文件,下面标记红色的3个字符串必须和CA证书一样(国家,省,公司)哟~ You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:www.yinzhengjie.org.cn Organizational Unit Name (eg, section) []:beiguozhuanyehu Common Name (eg, your name or your server's hostname) []:*.yinzhengjie.org.cn Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# ll total 8 -rw-r--r-- 1 root root 700 Dec 9 18:57 httpd.csr -rw------- 1 root root 887 Dec 9 18:53 httpd.key [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# cd /etc/pki/CA/ [root@node101.yinzhengjie.org.cn /etc/pki/CA]# [root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -in /etc/httpd/conf.d/ssl/httpd.csr -out certs/httpd.crt -days 100 #颁发证书,指定证书的有效期为100天,默认是365天。 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Dec 9 11:00:06 2019 GMT Not After : Mar 18 11:00:06 2020 GMT Subject: countryName = CN stateOrProvinceName = beijing organizationName = www.yinzhengjie.org.cn organizationalUnitName = beiguozhuanyehu commonName = *.yinzhengjie.org.cn X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: BE:F9:E0:ED:78:3F:B4:E1:B5:9A:21:3B:D7:72:6F:30:37:3E:8F:9F X509v3 Authority Key Identifier: keyid:FF:01:D8:A2:56:77:C4:93:23:27:42:E2:9B:7E:44:68:15:1F:29:5F Certificate is to be certified until Mar 18 11:00:06 2020 GMT (100 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@node101.yinzhengjie.org.cn /etc/pki/CA]# [root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree . ├── cacert.pem ├── certs │ └── httpd.crt ├── crl ├── index.txt ├── index.txt.attr ├── index.txt.old ├── newcerts │ └── 01.pem ├── private │ └── cakey.pem ├── serial └── serial.old 4 directories, 9 files [root@node101.yinzhengjie.org.cn /etc/pki/CA]# [root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat index.txt #这是我们之前手动创建的文件,发现内容被更新了,存放的是证书的相关信息 V 200318110006Z 01 unknown /C=CN/ST=beijing/O=www.yinzhengjie.org.cn/OU=beiguozhuanyehu/CN=*.yinzhengjie.org.cn [root@node101.yinzhengjie.org.cn /etc/pki/CA]# [root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat serial #由于我们已经申请了一个证书,因此下一个申请证书的编号会自动加1。 02 [root@node101.yinzhengjie.org.cn /etc/pki/CA]# cp certs/httpd.crt /etc/httpd/conf.d/ssl/ #证书文件拷贝到咱们自定义httpd存放证书文件达的目录中 [root@node101.yinzhengjie.org.cn /etc/pki/CA]# [root@node101.yinzhengjie.org.cn /etc/pki/CA]# cp cacert.pem /etc/httpd/conf.d/ssl/ #将ca的证书文件也拷贝到咱们自定义httpd存放证书文件的目录中 [root@node101.yinzhengjie.org.cn /etc/pki/CA]# [root@node101.yinzhengjie.org.cn /etc/pki/CA]# cd /etc/httpd/conf.d/ssl/ [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# ll total 16 -rw-r--r-- 1 root root 1399 Dec 9 19:01 cacert.pem -rw-r--r-- 1 root root 3853 Dec 9 19:01 httpd.crt -rw-r--r-- 1 root root 700 Dec 9 18:57 httpd.csr #由于证书申请已经完成,因此该文件的存在意义不大了,我们可以删除掉它。 -rw------- 1 root root 887 Dec 9 18:53 httpd.key [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]# [root@node101.yinzhengjie.org.cn /etc/httpd/conf.d/ssl]#
3>.编辑httpd服务器的配置文件
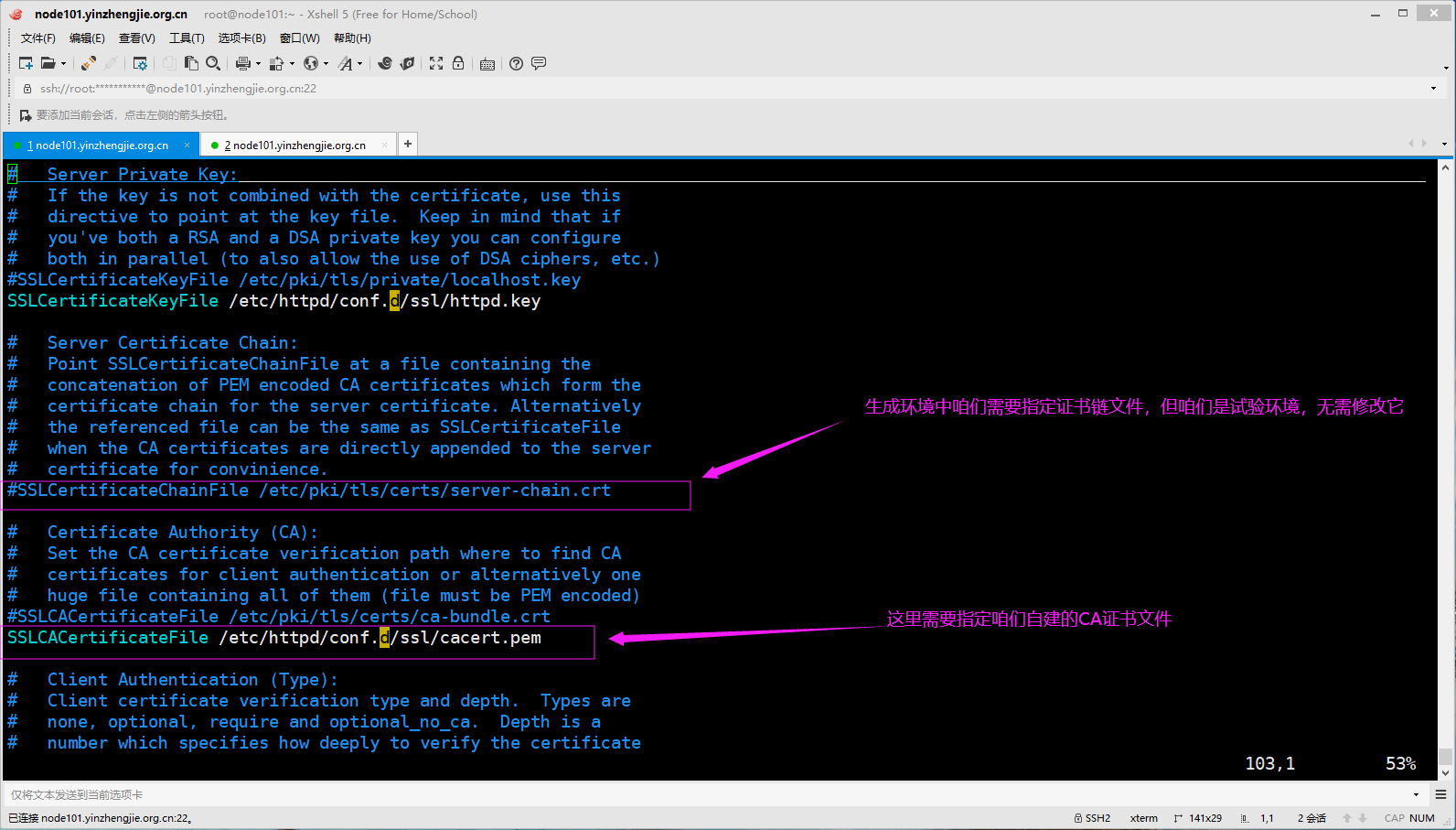
[root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/conf.d/ssl total 16 -rw-r--r-- 1 root root 1399 Dec 9 19:01 cacert.pem -rw-r--r-- 1 root root 3853 Dec 9 19:01 httpd.crt -rw-r--r-- 1 root root 700 Dec 9 18:57 httpd.csr -rw------- 1 root root 887 Dec 9 18:53 httpd.key [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf.d/ssl.conf Listen 443 https SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog SSLSessionCache shmcb:/run/httpd/sslcache(512000) SSLSessionCacheTimeout 300 SSLRandomSeed startup file:/dev/urandom 256 SSLRandomSeed connect builtin SSLCryptoDevice builtin <VirtualHost _default_:443> ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLCipherSuite HIGH:3DES:!aNULL:!MD5:!SEED:!IDEA SSLCertificateFile /etc/httpd/conf.d/ssl/httpd.crt SSLCertificateKeyFile /etc/httpd/conf.d/ssl/httpd.key SSLCACertificateFile /etc/httpd/conf.d/ssl/cacert.pem <Files ~ "\.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> BrowserMatch "MSIE [2-5]" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log \ "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b" </VirtualHost> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#
4>通过https协议访问咱们的httpd服务器

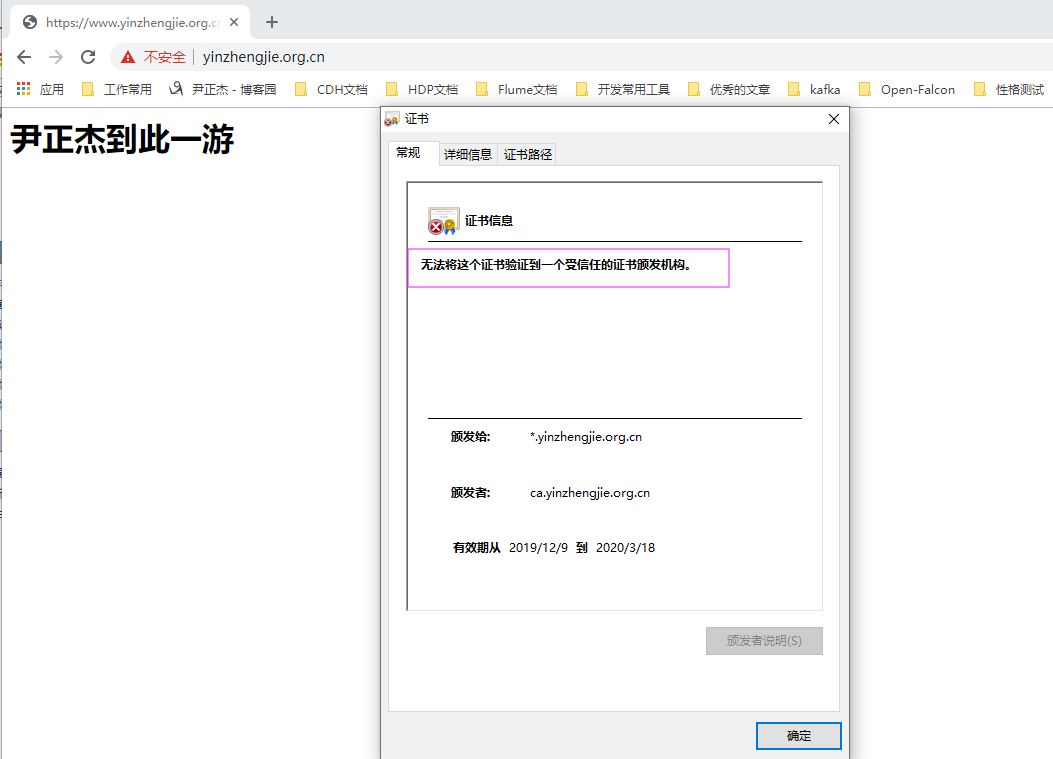
5>.如下图所示,查看证书的"常规"信息
6>.从服务器端下载证书文件
7>.更改证书文件后缀
8>.双击证书文件,并点击"安装证书",后续步骤上面有提到过,这里就忽略啦
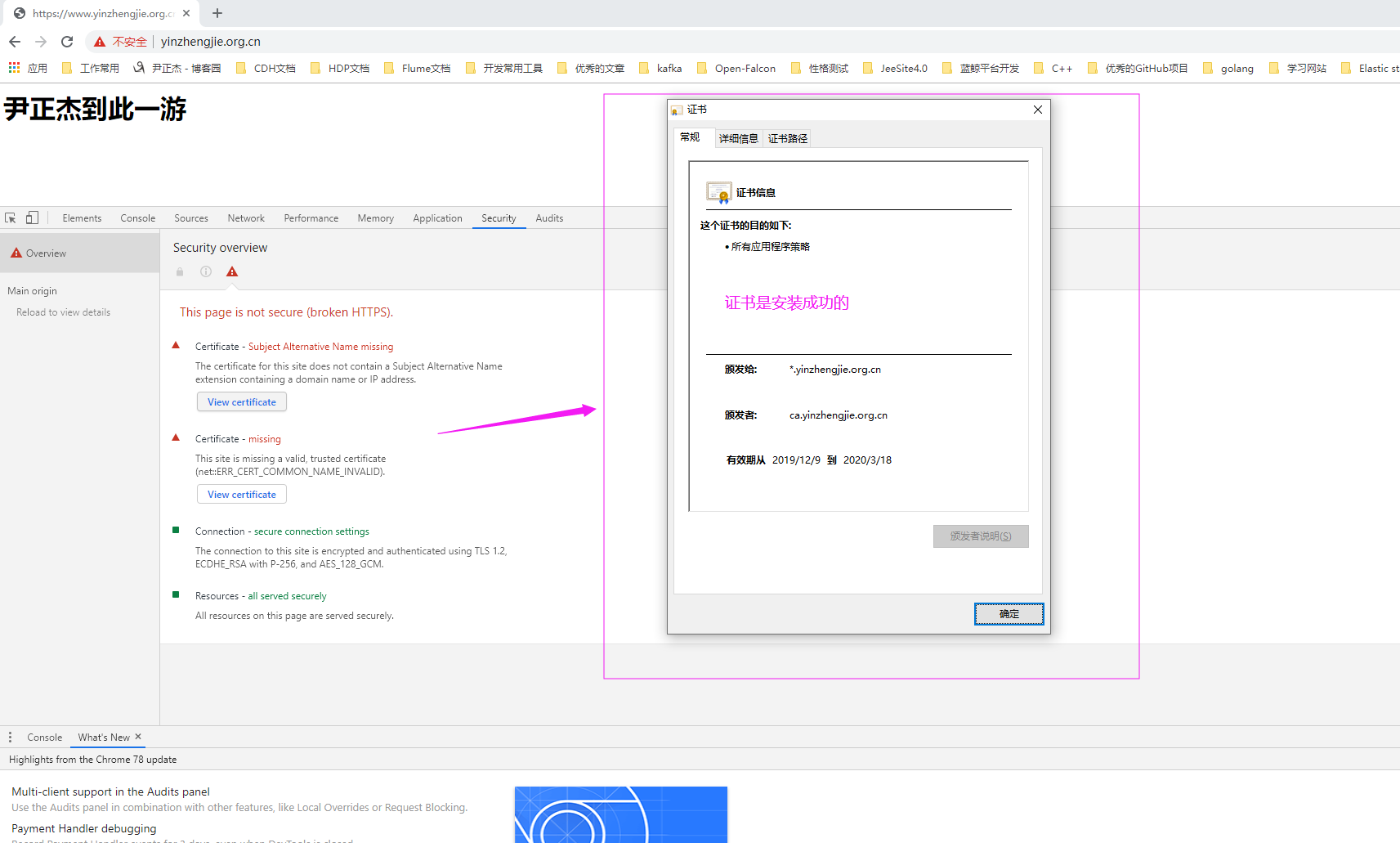
9>.客户端测试

[root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# openssl s_client -connect www.yinzhengjie.org.cn:443 -CAfile /etc/httpd/conf.d/ssl/cacert.pem CONNECTED(00000003) depth=1 C = CN, ST = beijing, L = beijing, O = www.yinzhengjie.org.cn, OU = devops, CN = ca.yinzhengjie.org.cn verify return:1 depth=0 C = CN, ST = beijing, O = www.yinzhengjie.org.cn, OU = beiguozhuanyehu, CN = *.yinzhengjie.org.cn verify return:1 --- Certificate chain 0 s:/C=CN/ST=beijing/O=www.yinzhengjie.org.cn/OU=beiguozhuanyehu/CN=*.yinzhengjie.org.cn i:/C=CN/ST=beijing/L=beijing/O=www.yinzhengjie.org.cn/OU=devops/CN=ca.yinzhengjie.org.cn 1 s:/C=CN/ST=beijing/L=beijing/O=www.yinzhengjie.org.cn/OU=devops/CN=ca.yinzhengjie.org.cn i:/C=CN/ST=beijing/L=beijing/O=www.yinzhengjie.org.cn/OU=devops/CN=ca.yinzhengjie.org.cn --- Server certificate -----BEGIN CERTIFICATE----- MIIDbzCCAlegAwIBAgIBATANBgkqhkiG9w0BAQsFADCBgzELMAkGA1UEBhMCQ04x EDAOBgNVBAgMB2JlaWppbmcxEDAOBgNVBAcMB2JlaWppbmcxHzAdBgNVBAoMFnd3 dy55aW56aGVuZ2ppZS5vcmcuY24xDzANBgNVBAsMBmRldm9wczEeMBwGA1UEAwwV Y2EueWluemhlbmdqaWUub3JnLmNuMB4XDTE5MTIwOTExMDAwNloXDTIwMDMxODEx MDAwNloweTELMAkGA1UEBhMCQ04xEDAOBgNVBAgMB2JlaWppbmcxHzAdBgNVBAoM Fnd3dy55aW56aGVuZ2ppZS5vcmcuY24xGDAWBgNVBAsMD2JlaWd1b3podWFueWVo dTEdMBsGA1UEAwwUKi55aW56aGVuZ2ppZS5vcmcuY24wgZ8wDQYJKoZIhvcNAQEB BQADgY0AMIGJAoGBALJMIc3emzFJRelMJMF1nab8KwEYxBkqk3Iwu9rJ/UEYC7Wg RP1wx9IIpXXO6L98rDmLfcEMS6388KDQZglcJ5Sf7Qch6ilV3hru5gYXjoIals+W 82nB1rDhS2ivXqv6wu7gIMnOjkukhM1nOjYewsBF1iWN4GtcvgW8kV5K0IDRAgMB AAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJh dGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBS++eDteD+04bWaITvXcm8wNz6PnzAf BgNVHSMEGDAWgBT/AdiiVnfEkyMnQuKbfkRoFR8pXzANBgkqhkiG9w0BAQsFAAOC AQEAYYivZaQe8vz1WYZdmJZ/1O1y0OSH/VwJAAxKdWZNFISh0SxRljnW1tOpItmP RXmAOcHlRzomBj6vjvyYlRrTvxa+7MIMR6EcGcu7aVAnNIYWxVP+Y6fHma/5Na7W Sj8XHkXNmT7xBlc8ykUWX5w9ZfwpPnly38EXSXywVUYDH9bt7Mzdi1Q4UywP2ysu 0AhrPJ0UdNVEGI2yGhroiVsHjHyUTj4HKwEZIm/uQWcjWdwlLzB79ilGF97B4tdw bGhYWANlvi2teyxg4O0hJQTTmv1ad5Fr306HNUZPnfZaG8IDxBigkv1+WCjodbap /25vDTjHnKbnV+zUg8MyTfeq3g== -----END CERTIFICATE----- subject=/C=CN/ST=beijing/O=www.yinzhengjie.org.cn/OU=beiguozhuanyehu/CN=*.yinzhengjie.org.cn issuer=/C=CN/ST=beijing/L=beijing/O=www.yinzhengjie.org.cn/OU=devops/CN=ca.yinzhengjie.org.cn --- No client certificate CA names sent Peer signing digest: SHA512 Server Temp Key: ECDH, P-256, 256 bits --- SSL handshake has read 2440 bytes and written 415 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 1024 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: 96CA50CB30562B491E8555CDF41EE662C66CB9AB7A1A535692BDDABED4513DE9 Session-ID-ctx: Master-Key: B52FCF27C5ED19ED984D5BB1044C8D408AF9F102A69EBF5F4B57B06ACE2342796BA27761100F511892801F57DBBE5B42 Key-Arg : None Krb5 Principal: None PSK identity: None PSK identity hint: None TLS session ticket lifetime hint: 300 (seconds) TLS session ticket: 0000 - 29 6f 93 a1 56 29 02 72-b7 26 24 9c 3c 9f 63 cf )o..V).r.&$.<.c. 0010 - 57 aa 1d f6 b2 e4 91 db-74 22 b7 ee b4 6d 74 c0 W.......t"...mt. 0020 - fe 99 a6 6f d6 d6 7d 1c-43 0f 07 32 15 84 34 2f ...o..}.C..2..4/ 0030 - fe 96 02 7c ef 4c 3e 86-02 99 05 3a ac 67 5d 5b ...|.L>....:.g][ 0040 - e5 ac 28 e8 d7 d9 d9 61-f7 31 d1 e0 a2 49 4e c1 ..(....a.1...IN. 0050 - 1d 91 a4 bd 73 5d 43 a5-ab 80 15 09 1a e4 8e be ....s]C......... 0060 - 94 91 67 fb f9 14 01 be-fc fa 56 a4 db ad 09 70 ..g.......V....p 0070 - 64 19 db f2 99 02 68 45-49 e1 a2 e7 ab 25 97 15 d.....hEI....%.. 0080 - 51 74 dc 9f 79 89 5d 7b-a9 4c d8 51 3c 23 59 9b Qt..y.]{.L.Q<#Y. 0090 - f9 86 98 24 1c 7d 86 bb-ce 88 a9 8d 6e 23 42 ca ...$.}......n#B. 00a0 - b2 d7 51 b2 c8 9f 9f f4-be 97 a3 d7 e4 d9 e6 63 ..Q............c 00b0 - c1 c5 46 02 f2 42 e2 d1-ef 45 98 f3 4a 34 ab be ..F..B...E..J4.. Start Time: 1575893577 Timeout : 300 (sec) Verify return code: 0 (ok) ---
[root@node101.yinzhengjie.org.cn ~]# curl -k https://www.yinzhengjie.org.cn --cacert /etc/httpd/conf.d/ssl/cacert.pem #忽略证书检查访问网页 <h1>尹正杰到此一游</h1> [root@node101.yinzhengjie.org.cn ~]#
六.将http请求转发至https的URL
1>.http重定向https概述
重定向 Redirect [status] URL-path URL
status状态: Permanent: 返回永久重定向状态码 301 Temp:返回临时重定向状态码302. 此为默认值
示例: Redirect temp / https://www.yinzhengjie.org.cn/
2>.查看京东公司的重定向策略
[root@node101.yinzhengjie.org.cn ~]# curl -I http://www.360buy.com #查看京东的早期域名 HTTP/1.1 301 Moved Permanently #这是永久性的跳转,这意味着这家公司可能后期不使用该域名啦~ Server: nginx Date: Mon, 09 Dec 2019 12:19:19 GMT Content-Type: text/html Content-Length: 178 Connection: keep-alive Location: http://www.jd.com/ Age: 3472 Via: http/1.1 ORI-BJ-CT-YF-PCS-22 (jcs [cSsSfU]), https/1.1 ORI-CLOUD-YF-MIX-171 (jcs [cHs f ]), http/1.1 JN-UNI-2-MIX-17 (jcs [cRs f ]) Access-Control-Allow-Origin: * Timing-Allow-Origin: * X-Trace: 301-1575890487408-0-0-0-0-0;301-1575890487408-0-0-0-1-1;301-1575890493062-0-0-0-1-1;301-1575893959089-0-0-0-1-1 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# curl -I http://www.jd.com #查看目前京东的域名,注意咱们使用的并不是https哟~ HTTP/1.1 302 Moved Temporarily #我们发现他会把http临时重定向到https上去。 Server: nginx Date: Mon, 09 Dec 2019 12:19:45 GMT Content-Type: text/html Content-Length: 154 Connection: keep-alive Location: https://www.jd.com/ Access-Control-Allow-Origin: * Timing-Allow-Origin: * X-Trace: 302-1575893985694-0-0-0-0-0 Strict-Transport-Security: max-age=360 [root@node101.yinzhengjie.org.cn ~]#
3>.修改httpd的配置文件
[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf/httpd.conf ServerRoot "/etc/httpd" Listen 80 Include conf.modules.d/*.conf User apache Group apache ServerAdmin root@localhost <Directory /> AllowOverride none Require all denied </Directory> DocumentRoot "/var/www/html" <Directory "/var/www"> AllowOverride None Require all granted </Directory> <Directory "/var/www/html"> Options Indexes FollowSymLinks AllowOverride None Require all granted </Directory> <IfModule dir_module> DirectoryIndex index.html </IfModule> <Files ".ht*"> Require all denied </Files> ErrorLog "logs/error_log" LogLevel warn <IfModule log_config_module> LogFormat "%h %l %u %{%Y-%m-%d %H:%M:%S}t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" testlog LogFormat "%h %l %u %t \"%r\" %>s %b" common <IfModule logio_module> LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\" %I %O" combinedio </IfModule> CustomLog "logs/access_log" testlog </IfModule> <IfModule alias_module> ScriptAlias /cgi-bin/ "/var/www/cgi-bin/" </IfModule> <Directory "/var/www/cgi-bin"> AllowOverride None Options None Require all granted </Directory> <IfModule mime_module> TypesConfig /etc/mime.types AddType application/x-compress .Z AddType application/x-gzip .gz .tgz AddType text/html .shtml AddOutputFilter INCLUDES .shtml </IfModule> AddDefaultCharset UTF-8 <IfModule mime_magic_module> MIMEMagicFile conf/magic </IfModule> EnableSendfile on IncludeOptional conf.d/*.conf Redirect temp / https://www.yinzhengjie.org.cn/ #没错,就是它有重定向功能。 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -t Syntax OK [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:80 *:* LISTEN 0 128 *:22 *:* LISTEN 0 128 *:443 *:* LISTEN 0 128 :::22 :::* [root@node101.yinzhengjie.org.cn ~]#
4>.使用客户端访问测试发现问题

[root@node101.yinzhengjie.org.cn ~]# curl -kIL http://www.yinzhengjie.org.cn HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:32:03 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 curl: (47) Maximum (50) redirects followed [root@node101.yinzhengjie.org.cn ~]#
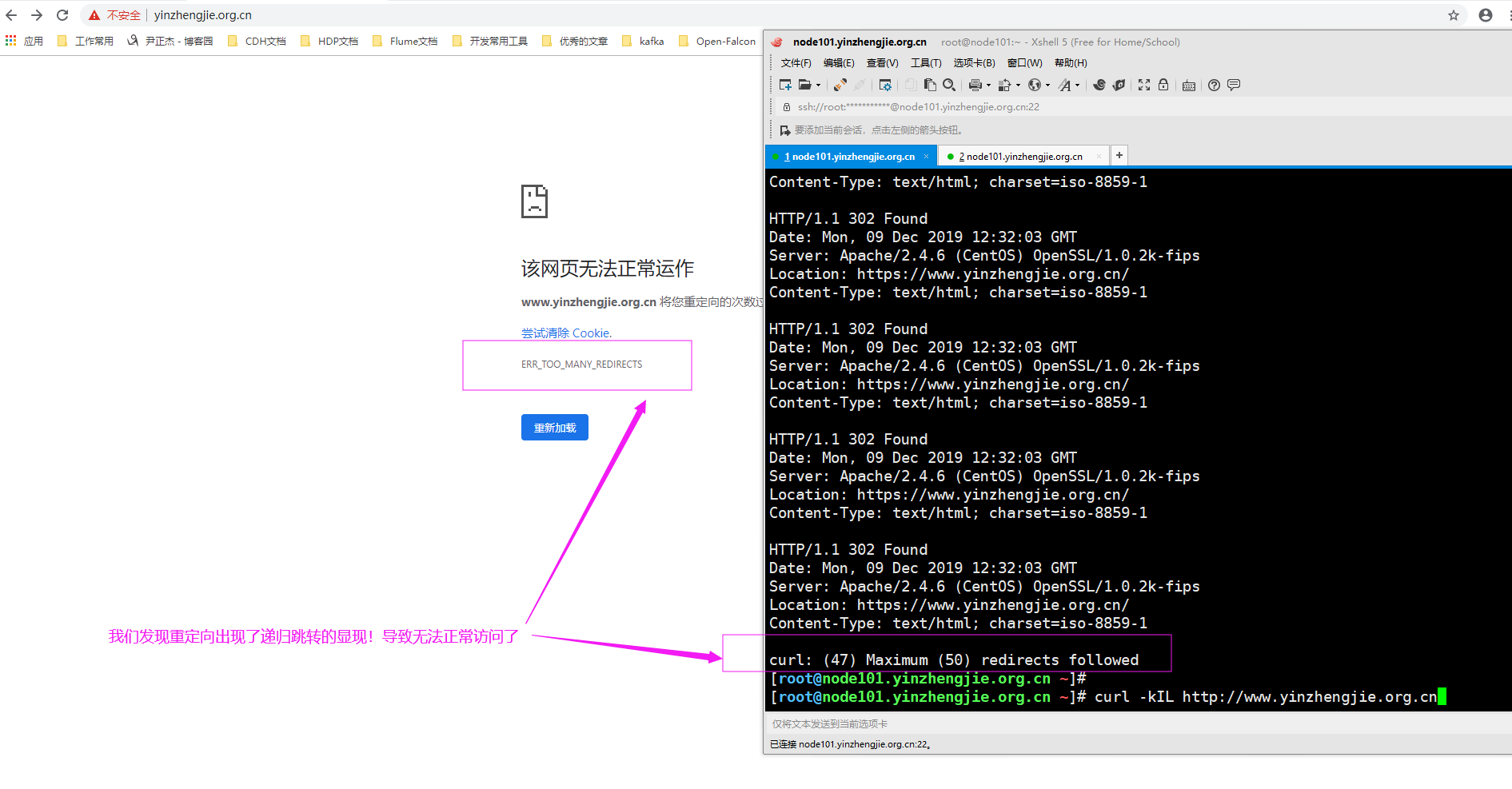
5>.引入HSTS(HTTP Strict Transport Security)解决上面递归跳转的问题
HSTS:HTTP Strict Transport Security 服务器端配置支持HSTS后,会在给浏览器返回的HTTP首部中携带HSTS字段。浏览器获取到该信息后,会将所有HTTP访问请求在内部做307跳转到HTTPS。而无需任何网络过程 HSTS preload list 是Chrome浏览器中的HSTS预载入列表,在该列表中的网站,使用Chrome浏览器访问时,会自动转换成HTTPS。Firefox、Safari、Edge浏览器也会采用这个列表 实现重定向示例: [root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf/httpd.conf ServerRoot "/etc/httpd" Listen 80 Include conf.modules.d/*.conf User apache Group apache ServerAdmin root@localhost <Directory /> AllowOverride none Require all denied </Directory> DocumentRoot "/var/www/html" <Directory "/var/www"> AllowOverride None Require all granted </Directory> <Directory "/var/www/html"> Options Indexes FollowSymLinks AllowOverride None Require all granted </Directory> <IfModule dir_module> DirectoryIndex index.html </IfModule> <Files ".ht*"> Require all denied </Files> ErrorLog "logs/error_log" LogLevel warn <IfModule log_config_module> LogFormat "%h %l %u %{%Y-%m-%d %H:%M:%S}t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" testlog LogFormat "%h %l %u %t \"%r\" %>s %b" common <IfModule logio_module> LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\" %I %O" combinedio </IfModule> CustomLog "logs/access_log" testlog </IfModule> <IfModule alias_module> ScriptAlias /cgi-bin/ "/var/www/cgi-bin/" </IfModule> <Directory "/var/www/cgi-bin"> AllowOverride None Options None Require all granted </Directory> <IfModule mime_module> TypesConfig /etc/mime.types AddType application/x-compress .Z AddType application/x-gzip .gz .tgz AddType text/html .shtml AddOutputFilter INCLUDES .shtml </IfModule> AddDefaultCharset UTF-8 <IfModule mime_magic_module> MIMEMagicFile conf/magic </IfModule> EnableSendfile on IncludeOptional conf.d/*.conf RewriteEngine on #只需要将上面的"Redirect temp / https://www.yinzhengjie.org.cn/"语句换成当前行和下一行这两行就能解决递归重定向的问题。 RewriteRule ^(/.*)$ https://%{HTTP_HOST}$1 [redirect=302] [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -t Syntax OK [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:80 *:* LISTEN 0 128 *:22 *:* LISTEN 0 128 *:443 *:* LISTEN 0 128 :::22 :::* [root@node101.yinzhengjie.org.cn ~]#
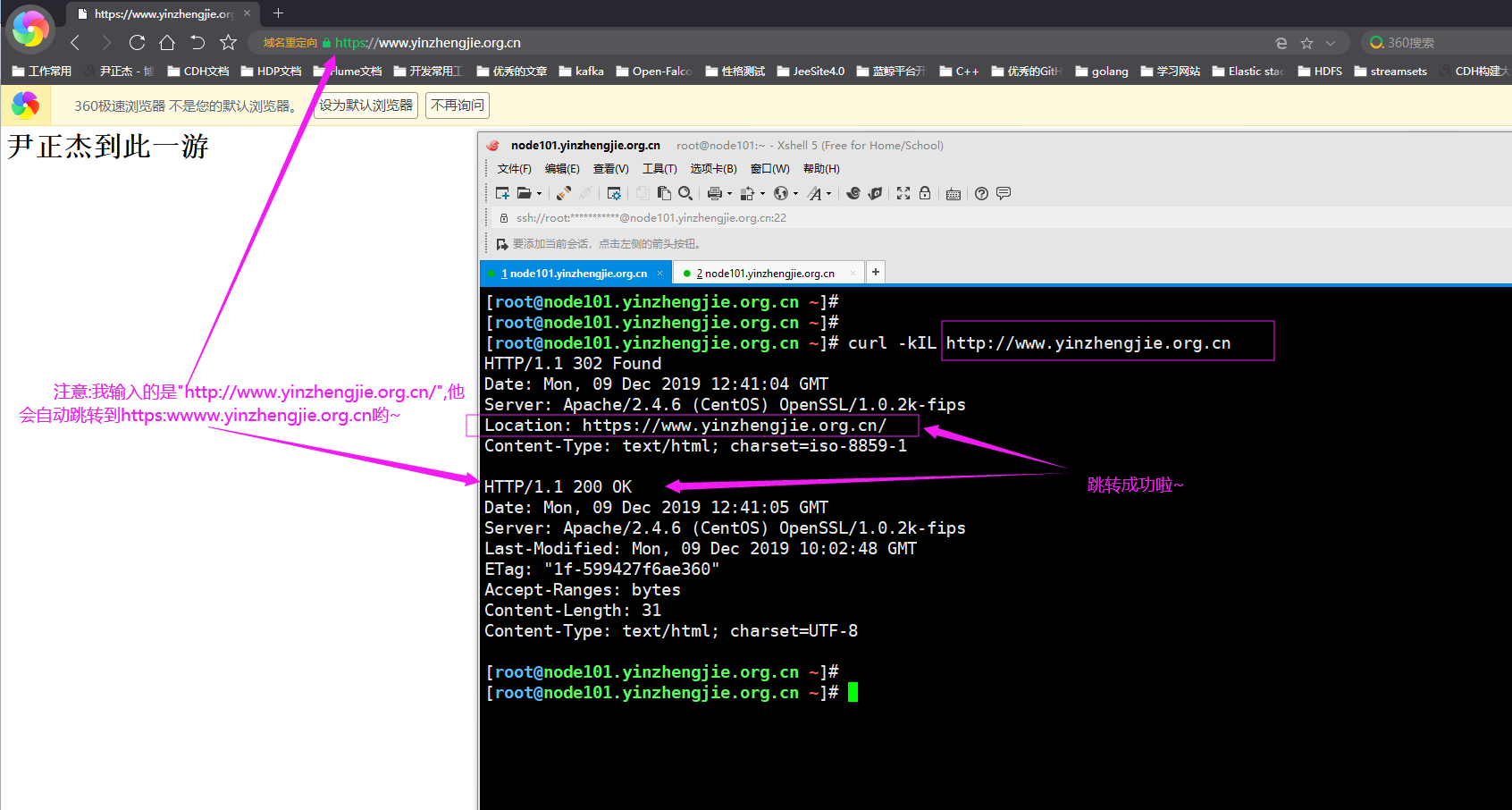
实现HSTS示例:(生产环境建议启用该功能) [root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/httpd/conf/httpd.conf ServerRoot "/etc/httpd" Listen 80 Include conf.modules.d/*.conf User apache Group apache ServerAdmin root@localhost <Directory /> AllowOverride none Require all denied </Directory> DocumentRoot "/var/www/html" <Directory "/var/www"> AllowOverride None Require all granted </Directory> <Directory "/var/www/html"> Options Indexes FollowSymLinks AllowOverride None Require all granted </Directory> <IfModule dir_module> DirectoryIndex index.html </IfModule> <Files ".ht*"> Require all denied </Files> ErrorLog "logs/error_log" LogLevel warn <IfModule log_config_module> LogFormat "%h %l %u %{%Y-%m-%d %H:%M:%S}t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" testlog LogFormat "%h %l %u %t \"%r\" %>s %b" common <IfModule logio_module> LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\" %I %O" combinedio </IfModule> CustomLog "logs/access_log" testlog </IfModule> <IfModule alias_module> ScriptAlias /cgi-bin/ "/var/www/cgi-bin/" </IfModule> <Directory "/var/www/cgi-bin"> AllowOverride None Options None Require all granted </Directory> <IfModule mime_module> TypesConfig /etc/mime.types AddType application/x-compress .Z AddType application/x-gzip .gz .tgz AddType text/html .shtml AddOutputFilter INCLUDES .shtml </IfModule> AddDefaultCharset UTF-8 <IfModule mime_magic_module> MIMEMagicFile conf/magic </IfModule> EnableSendfile on IncludeOptional conf.d/*.conf Header always set Strict-Transport-Security "max-age=31536000" #看这里,它就是启用了HSTS功能,下面两行是实现https到https重定向的~ RewriteEngine on RewriteRule ^(/.*)$ https://%{HTTP_HOST}$1 [redirect=302] [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -t Syntax OK [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# curl -I http://www.yinzhengjie.org.cn #仔细观察此行的输出部分和上图的输出部分 HTTP/1.1 302 Found Date: Mon, 09 Dec 2019 12:59:52 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips Strict-Transport-Security: max-age=31536000 #不难发现,这里有相应的HSTS相关参数,表示支持HSTS支持的时长为1年,单位默认为秒。 Location: https://www.yinzhengjie.org.cn/ Content-Type: text/html; charset=iso-8859-1 [root@node101.yinzhengjie.org.cn ~]#
本文来自博客园,作者:尹正杰,转载请注明原文链接:https://www.cnblogs.com/yinzhengjie/p/12008896.html,个人微信: "JasonYin2020"(添加时请备注来源及意图备注,有偿付费)
当你的才华还撑不起你的野心的时候,你就应该静下心来学习。当你的能力还驾驭不了你的目标的时候,你就应该沉下心来历练。问问自己,想要怎样的人生。







【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· AI与.NET技术实操系列(二):开始使用ML.NET
· 记一次.NET内存居高不下排查解决与启示
· 探究高空视频全景AR技术的实现原理
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具
2018-12-09 Hadoop生态圈-构建企业级平台安全方案
2016-12-09 网易免费邮件开启smtp教程
2016-12-09 zabbix添加邮件报警机制