CDH构建大数据平台-配置集群的Sentry授权安全
CDH构建大数据平台-配置集群的Sentry授权安全
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
虽然HDFS授权和使用ACL的服务级授权确实在Hadoop用户授权方面起着至关重要的作用,但是在Hadoop中确实没有总体授权系统。之前我分享了使用Kerberos配置大数据集群的认证安全。本篇博客用来讲解大数据集群的授权安全。认证安全是解决谁可以访问集群,而授权安全是用来解决可以访问集群的人(即经过安全认证的人)能做什么样的事情。
Apache Sentry力图为Hadoop环境提供统一的授权方式,从而Hadoop管理员可以准确指定用户在Hadoop系统中可以执行的操作。Sentry基于角色的访问系统使管理员能够在细粒度级别控制用户访问。为了在集群中设置细粒度授权,必须对数据进行分类,并指定需要访问特定数据集的用户及所需的访问级别。可以综合使用Hive和Sentry来指定细粒度的授权。
一.Sentry基础
1>.什么是Sentry
Apache Sentry为存储在HDFS中的数据提供了细粒度的基于角色的授权。
Sentry为HDFS数据提供基于角色授权控制(RBAC)。
Sentry目前可以与Apache Hive、Hive Metastore/ HCatalog、Apache Solr、Impala和HDFS良好结合。 Sentry被设计作为Hadoop组件的可插拔授权引擎。它允许用户定义授权 规则,来验证用户或应用对Hadoop资源的访问请求。Sentry是高度模块 化的,可以支持Hadoop中各种数据模型的授权。
2>.Sentry相关概念
Authentication
验证凭证以可靠地鉴别一个用户
Authorization
限制一个用户对给定资源的存取权限
User
通过底层认证系统来识别的个体
Group
一组User,由认证系统管理
Privilege
一条指令或规则,以允许对某对象的存取
Role
一组Privilege,或一个包含多条存取规则的模版
Authorization models
定义了受授权规则约束的对象和允许操作的粒度 如在SQL模型中,对象可以是数据库或表,操作 可以是SELECT、INSERT、CREATE。在Search模 型中,对象可以是索引、配置、集合、文档,操 作可以是query和update。
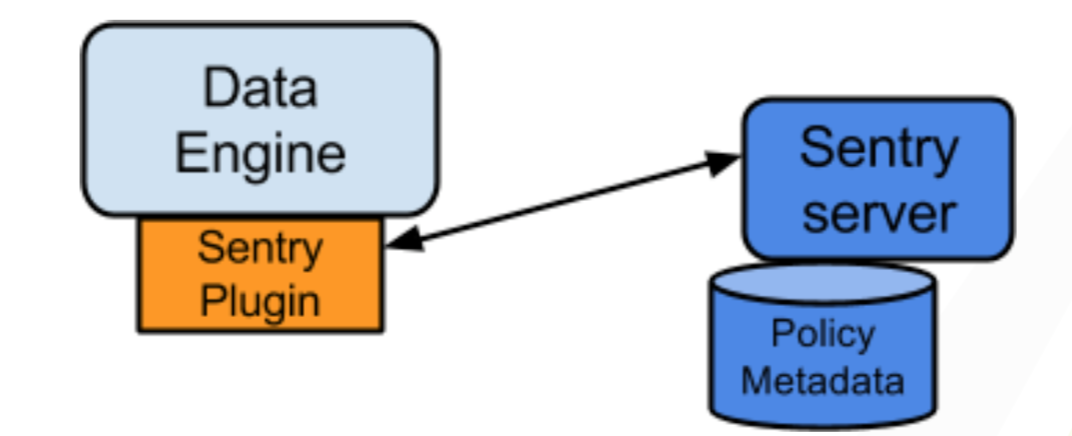
3>.授权过程主要有三个部件参与
Sentry Server:
Sertry RPC Server管理授权元数据。它支持检索和操作元数据的安全接口。在CDH5.13及以上,可以配置多个Sentry Server以获得高可用性。
Data Engine:
是一个数据处理应用,例如Hive或Impala,其需要授权访问数据或元数据资源。Data Engine加载Sentry Plugin,所有访问资源的客户端请求都被截获并路由到Sentry Plugin进行验证。
Sentry Plugin:
在Data Engine中运行。它供了处理Sentry Server 中存储的授权元数据的接口,并且包括了使用从服务器检索的授权元数据来评估访问请求的授权策略引擎。
4>.Sentry的授权控制过程
Sentry依靠底层认证系统来鉴别用户,如Kerberos或LDAP。它也使用Hadoop中配置的组映射机制,以保证Sentry和其他Hadoop组件看到相同的组映射。 Sentry使用基于角色的存取控制(RBAC),这是一种企业内管理大量用户和数据对象的授权的有力机制。当建立一个新用户时,只需将其加入一个指定的组,即可使该用户具备该组所拥有的所有角色。 因此Sentry的授权控制过程为: 1>.建立用户时,为其分配一个组(通过操作系统或LDAP); 2>.创建Sentry的角色; 3>.将一个或多个细粒度的权限赋给角色; 4>.将一个或多个角色赋给组。这样,该组下的用户就具备这些角色所对应的权限了;
二.Sentry的配置
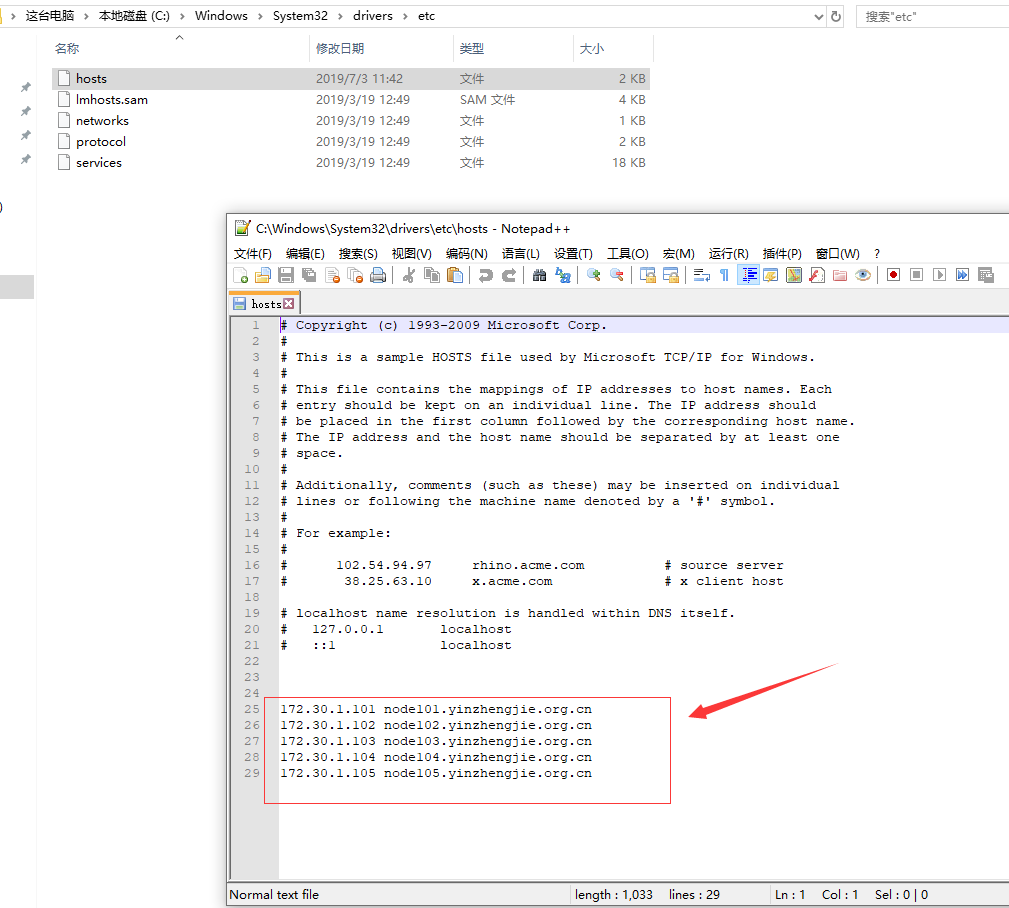
1>.添加虚拟机主机对应的解析
2>.Hue中导入测试数据
详情请参考:https://www.cnblogs.com/yinzhengjie/p/10940648.html
3>.添加Sentry服务
详情请参考:https://www.cnblogs.com/yinzhengjie/p/11138776.html
三.配置Sentry授权实战案例
1>.在集群的每个节点创建相应的用户和组
[root@node101.yinzhengjie.org.cn ~]# ansible cdh --list-hosts hosts (3): node101.yinzhengjie.org.cn node102.yinzhengjie.org.cn node103.yinzhengjie.org.cn [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# ansible cdh -m shell -a 'groupadd selector' node101.yinzhengjie.org.cn | SUCCESS | rc=0 >> node103.yinzhengjie.org.cn | SUCCESS | rc=0 >> node102.yinzhengjie.org.cn | SUCCESS | rc=0 >> [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# ansible cdh -m shell -a 'groupadd inserter' node101.yinzhengjie.org.cn | SUCCESS | rc=0 >> node102.yinzhengjie.org.cn | SUCCESS | rc=0 >> node103.yinzhengjie.org.cn | SUCCESS | rc=0 >> [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# ansible cdh -m shell -a 'useradd -u 1005 -g selector zhangsan' node101.yinzhengjie.org.cn | SUCCESS | rc=0 >> node102.yinzhengjie.org.cn | SUCCESS | rc=0 >> node103.yinzhengjie.org.cn | SUCCESS | rc=0 >> [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# ansible cdh -m shell -a 'useradd -u 1006 -g inserter lisi' node101.yinzhengjie.org.cn | SUCCESS | rc=0 >> node102.yinzhengjie.org.cn | SUCCESS | rc=0 >> node103.yinzhengjie.org.cn | SUCCESS | rc=0 >> [root@node101.yinzhengjie.org.cn ~]#
2>.进行Kerberos认证
启用Kerberos详情请参考:https://www.cnblogs.com/yinzhengjie/articles/10483362.html
[root@node101.yinzhengjie.org.cn ~]# klist klist: No credentials cache found (filename: /tmp/krb5cc_0) [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# find / -name hive.keytab /opt/cloudera-manager/cm-5.15.1/run/cloudera-scm-agent/process/137-hive-HIVEMETASTORE/hive.keytab #需要注意的是,编号越大,代表是最近一次修改哟,我们这里是基于二进制方式安装,因此key存在我们指定的目录中,而基于yum方式安装会直接存放在"/run/cloudera-scm-agent/process"目录下。 /opt/cloudera-manager/cm-5.15.1/run/cloudera-scm-agent/process/136-hive-HIVESERVER2/hive.keytab /opt/cloudera-manager/cm-5.15.1/run/cloudera-scm-agent/process/109-hive-HIVEMETASTORE/hive.keytab /opt/cloudera-manager/cm-5.15.1/run/cloudera-scm-agent/process/108-hive-HIVESERVER2/hive.keytab [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# kinit -kt /opt/cloudera-manager/cm-5.15.1/run/cloudera-scm-agent/process/137-hive-HIVEMETASTORE/hive.keytab hive/node101.yinzhengjie.org.cn #使用keytab进行认证 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# klist #很显然,这里是认证成功的 Ticket cache: FILE:/tmp/krb5cc_0 Default principal: hive/node101.yinzhengjie.org.cn@YINZHENGJIE.ORG.CN # Valid starting Expires Service principal 07/05/2019 18:37:46 07/06/2019 18:37:46 krbtgt/YINZHENGJIE.ORG.CN@YINZHENGJIE.ORG.CN renew until 07/12/2019 18:37:46 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#
3>.进行Kerberos认证后,使用Beeline工具登陆hive
[root@node101.yinzhengjie.org.cn ~]# ss -ntl | grep 10000 LISTEN 0 50 *:10000 *:* [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# beeline Java HotSpot(TM) 64-Bit Server VM warning: ignoring option MaxPermSize=512M; support was removed in 8.0 Java HotSpot(TM) 64-Bit Server VM warning: ignoring option MaxPermSize=512M; support was removed in 8.0 Beeline version 1.1.0-cdh5.15.1 by Apache Hive beeline> beeline> beeline> !connect jdbc:hive2://node101.yinzhengjie.org.cn:10000/default;principal=hive/node101.yinzhengjie.org.cn@YINZHENGJIE.ORG.CN scan complete in 1ms Connecting to jdbc:hive2://node101.yinzhengjie.org.cn:10000/default;principal=hive/node101.yinzhengjie.org.cn@YINZHENGJIE.ORG.CN Connected to: Apache Hive (version 1.1.0-cdh5.15.1) Driver: Hive JDBC (version 1.1.0-cdh5.15.1) Transaction isolation: TRANSACTION_REPEATABLE_READ 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> USE default; INFO : Compiling command(queryId=hive_20190705185959_acddcade-b843-4155-86f2-cc61bd47c481): USE default INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705185959_acddcade-b843-4155-86f2-cc61bd47c481); Time taken: 0.07 seconds INFO : Executing command(queryId=hive_20190705185959_acddcade-b843-4155-86f2-cc61bd47c481): USE default INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705185959_acddcade-b843-4155-86f2-cc61bd47c481); Time taken: 0.006 seconds INFO : OK No rows affected (0.086 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> SHOW TABLES; INFO : Compiling command(queryId=hive_20190705185959_0d82de06-bdd7-45b6-a268-1b987d97c150): SHOW TABLES INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:[FieldSchema(name:tab_name, type:string, comment:from deserializer)], properties:null) INFO : Completed compiling command(queryId=hive_20190705185959_0d82de06-bdd7-45b6-a268-1b987d97c150); Time taken: 0.045 seconds INFO : Executing command(queryId=hive_20190705185959_0d82de06-bdd7-45b6-a268-1b987d97c150): SHOW TABLES INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705185959_0d82de06-bdd7-45b6-a268-1b987d97c150); Time taken: 0.067 seconds INFO : OK +------------+--+ | tab_name | +------------+--+ | customers | | sample_07 | | sample_08 | | web_logs | +------------+--+ 4 rows selected (0.134 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10>
4>.创建admin角色并将其权限赋值给hive组(这样hive组里的用户都是hive的管理员)
0: jdbc:hive2://node101.yinzhengjie.org.cn:10> CREATE ROLE admin; INFO : Compiling command(queryId=hive_20190705184646_637a7aa6-6ecb-4928-8a0f-7f382799ba55): CREATE ROLE admin INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705184646_637a7aa6-6ecb-4928-8a0f-7f382799ba55); Time taken: 0.076 seconds INFO : Executing command(queryId=hive_20190705184646_637a7aa6-6ecb-4928-8a0f-7f382799ba55): CREATE ROLE admin INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705184646_637a7aa6-6ecb-4928-8a0f-7f382799ba55); Time taken: 0.077 seconds INFO : OK No rows affected (1.325 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> GRANT ALL ON SERVER server1 TO ROLE admin; INFO : Compiling command(queryId=hive_20190705184949_e61e8fb9-bb59-4398-8371-05c48a7784c5): GRANT ALL ON SERVER server1 TO ROLE admin INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705184949_e61e8fb9-bb59-4398-8371-05c48a7784c5); Time taken: 0.062 seconds INFO : Executing command(queryId=hive_20190705184949_e61e8fb9-bb59-4398-8371-05c48a7784c5): GRANT ALL ON SERVER server1 TO ROLE admin INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705184949_e61e8fb9-bb59-4398-8371-05c48a7784c5); Time taken: 0.048 seconds INFO : OK No rows affected (0.121 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> GRANT ROLE admin TO GROUP hive; INFO : Compiling command(queryId=hive_20190705185050_7a6d6080-2331-4037-8f8e-c60035c9bf17): GRANT ROLE admin TO GROUP hive INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705185050_7a6d6080-2331-4037-8f8e-c60035c9bf17); Time taken: 0.053 seconds INFO : Executing command(queryId=hive_20190705185050_7a6d6080-2331-4037-8f8e-c60035c9bf17): GRANT ROLE admin TO GROUP hive INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705185050_7a6d6080-2331-4037-8f8e-c60035c9bf17); Time taken: 0.046 seconds INFO : OK No rows affected (0.11 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10>
5>.创建reads角色(读取我们之前使用hue生成default库的测试数据)并赋值给selector组
0: jdbc:hive2://node101.yinzhengjie.org.cn:10> CREATE ROLE reads; INFO : Compiling command(queryId=hive_20190705190000_a8f3ebf0-93fa-4984-baf2-af0149f8cb92): CREATE ROLE reads INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190000_a8f3ebf0-93fa-4984-baf2-af0149f8cb92); Time taken: 0.045 seconds INFO : Executing command(queryId=hive_20190705190000_a8f3ebf0-93fa-4984-baf2-af0149f8cb92): CREATE ROLE reads INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190000_a8f3ebf0-93fa-4984-baf2-af0149f8cb92); Time taken: 0.025 seconds INFO : OK No rows affected (0.081 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> REVOKE ALL ON DATABASE default FROM ROLE reads; INFO : Compiling command(queryId=hive_20190705190101_ab80261e-a4b0-459c-9818-40b780fb19b3): REVOKE ALL ON DATABASE default FROM ROLE reads INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190101_ab80261e-a4b0-459c-9818-40b780fb19b3); Time taken: 0.058 seconds INFO : Executing command(queryId=hive_20190705190101_ab80261e-a4b0-459c-9818-40b780fb19b3): REVOKE ALL ON DATABASE default FROM ROLE reads INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190101_ab80261e-a4b0-459c-9818-40b780fb19b3); Time taken: 0.047 seconds INFO : OK No rows affected (0.115 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> GRANT SELECT ON DATABASE defalut TO ROLE reads; INFO : Compiling command(queryId=hive_20190705190202_6abacb86-4922-49e9-a619-22fbdf88c32a): GRANT SELECT ON DATABASE defalut TO ROLE reads INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190202_6abacb86-4922-49e9-a619-22fbdf88c32a); Time taken: 0.044 seconds INFO : Executing command(queryId=hive_20190705190202_6abacb86-4922-49e9-a619-22fbdf88c32a): GRANT SELECT ON DATABASE defalut TO ROLE reads INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190202_6abacb86-4922-49e9-a619-22fbdf88c32a); Time taken: 0.02 seconds INFO : OK No rows affected (0.073 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> GRANT ROLE reads TO GROUP selector; INFO : Compiling command(queryId=hive_20190705190303_c07118d5-3c09-4249-8b12-8237d6c8f513): GRANT ROLE reads TO GROUP selector INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190303_c07118d5-3c09-4249-8b12-8237d6c8f513); Time taken: 0.051 seconds INFO : Executing command(queryId=hive_20190705190303_c07118d5-3c09-4249-8b12-8237d6c8f513): GRANT ROLE reads TO GROUP selector INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190303_c07118d5-3c09-4249-8b12-8237d6c8f513); Time taken: 0.018 seconds INFO : OK No rows affected (0.081 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10>
6>.创建writes橘色(读写defalut库下的sample_08表)并赋值给inserter组
0: jdbc:hive2://node101.yinzhengjie.org.cn:10> CREATE ROLE writes; INFO : Compiling command(queryId=hive_20190705190404_28fad467-b059-4355-861c-9ab0885f9f74): CREATE ROLE writes INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190404_28fad467-b059-4355-861c-9ab0885f9f74); Time taken: 0.051 seconds INFO : Executing command(queryId=hive_20190705190404_28fad467-b059-4355-861c-9ab0885f9f74): CREATE ROLE writes INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190404_28fad467-b059-4355-861c-9ab0885f9f74); Time taken: 0.013 seconds INFO : OK No rows affected (0.074 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> REVOKE ALL ON DATABASE default FROM ROLE writes; INFO : Compiling command(queryId=hive_20190705190505_efbed76d-b986-4d9b-9510-7d35485bfd9a): REVOKE ALL ON DATABASE default FROM ROLE writes INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190505_efbed76d-b986-4d9b-9510-7d35485bfd9a); Time taken: 0.052 seconds INFO : Executing command(queryId=hive_20190705190505_efbed76d-b986-4d9b-9510-7d35485bfd9a): REVOKE ALL ON DATABASE default FROM ROLE writes INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190505_efbed76d-b986-4d9b-9510-7d35485bfd9a); Time taken: 0.013 seconds INFO : OK No rows affected (0.076 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> GRANT ALL ON default.sample_08 TO ROLE writes; INFO : Compiling command(queryId=hive_20190705190707_26a1cd08-ec9e-46b9-9368-f4401e349cfd): GRANT ALL ON defult.sample_08 TO ROLE writes INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190707_26a1cd08-ec9e-46b9-9368-f4401e349cfd); Time taken: 0.055 seconds INFO : Executing command(queryId=hive_20190705190707_26a1cd08-ec9e-46b9-9368-f4401e349cfd): GRANT ALL ON defult.sample_08 TO ROLE writes INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190707_26a1cd08-ec9e-46b9-9368-f4401e349cfd); Time taken: 0.021 seconds INFO : OK No rows affected (0.084 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> GRANT ROLE writes TO GROUP inserter; INFO : Compiling command(queryId=hive_20190705190707_ef1970b1-4c27-450b-8468-ecdf27e6ee33): GRANT ROLE writes TO GROUP inserter INFO : Semantic Analysis Completed INFO : Returning Hive schema: Schema(fieldSchemas:null, properties:null) INFO : Completed compiling command(queryId=hive_20190705190707_ef1970b1-4c27-450b-8468-ecdf27e6ee33); Time taken: 0.043 seconds INFO : Executing command(queryId=hive_20190705190707_ef1970b1-4c27-450b-8468-ecdf27e6ee33): GRANT ROLE writes TO GROUP inserter INFO : Starting task [Stage-0:DDL] in serial mode INFO : Completed executing command(queryId=hive_20190705190707_ef1970b1-4c27-450b-8468-ecdf27e6ee33); Time taken: 0.014 seconds INFO : OK No rows affected (0.065 seconds) 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10>
7>.登陆KDC服务器,创建相应的测试用户
[root@node104.yinzhengjie.org.cn ~]# kadmin.local Authenticating as principal root/admin@YINZHENGJIE.ORG.CN with password. kadmin.local: kadmin.local: addprinc zhangsan WARNING: no policy specified for zhangsan@YINZHENGJIE.ORG.CN; defaulting to no policy Enter password for principal "zhangsan@YINZHENGJIE.ORG.CN": Re-enter password for principal "zhangsan@YINZHENGJIE.ORG.CN": Principal "zhangsan@YINZHENGJIE.ORG.CN" created. kadmin.local: kadmin.local: addprinc lisi WARNING: no policy specified for lisi@YINZHENGJIE.ORG.CN; defaulting to no policy Enter password for principal "lisi@YINZHENGJIE.ORG.CN": Re-enter password for principal "lisi@YINZHENGJIE.ORG.CN": Principal "lisi@YINZHENGJIE.ORG.CN" created. kadmin.local: kadmin.local: xst -k /etc/security/zhangsan.keytab zhangsan Entry for principal zhangsan with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type des3-cbc-sha1 added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type arcfour-hmac added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type camellia256-cts-cmac added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type camellia128-cts-cmac added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type des-hmac-sha1 added to keytab WRFILE:/etc/security/zhangsan.keytab. Entry for principal zhangsan with kvno 2, encryption type des-cbc-md5 added to keytab WRFILE:/etc/security/zhangsan.keytab. kadmin.local: kadmin.local: xst -k /etc/security/lisi.keytab lisi Entry for principal lisi with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type des3-cbc-sha1 added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type arcfour-hmac added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type camellia256-cts-cmac added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type camellia128-cts-cmac added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type des-hmac-sha1 added to keytab WRFILE:/etc/security/lisi.keytab. Entry for principal lisi with kvno 2, encryption type des-cbc-md5 added to keytab WRFILE:/etc/security/lisi.keytab. kadmin.local: kadmin.local: quit [root@node104.yinzhengjie.org.cn ~]# [root@node104.yinzhengjie.org.cn ~]# ll /etc/security/*.keytab -rw------- 1 root root 546 Jul 5 19:12 /etc/security/lisi.keytab -rw------- 1 root root 578 Jul 5 19:12 /etc/security/zhangsan.keytab [root@node104.yinzhengjie.org.cn ~]# [root@node104.yinzhengjie.org.cn ~]# scp /etc/security/*.keytab root@node102.yinzhengjie.org.cn:/etc/security/ root@node102.yinzhengjie.org.cn's password: lisi.keytab 100% 546 147.4KB/s 00:00 zhangsan.keytab 100% 578 387.9KB/s 00:00 [root@node104.yinzhengjie.org.cn ~]# [root@node104.yinzhengjie.org.cn ~]#
8>.使用zhangsan用户测试
[root@node102.yinzhengjie.org.cn ~]# ll /etc/security/*.keytab -rw------- 1 root root 546 Jul 5 19:16 /etc/security/lisi.keytab -rw------- 1 root root 578 Jul 5 19:16 /etc/security/zhangsan.keytab [root@node102.yinzhengjie.org.cn ~]# [root@node102.yinzhengjie.org.cn ~]# klist klist: No credentials cache found (filename: /tmp/krb5cc_0) [root@node102.yinzhengjie.org.cn ~]# [root@node102.yinzhengjie.org.cn ~]# kinit -kt /etc/security/zhangsan.keytab zhangsan [root@node102.yinzhengjie.org.cn ~]# [root@node102.yinzhengjie.org.cn ~]# klist Ticket cache: FILE:/tmp/krb5cc_0 Default principal: zhangsan@YINZHENGJIE.ORG.CN Valid starting Expires Service principal 07/05/2019 19:17:38 07/06/2019 19:17:38 krbtgt/YINZHENGJIE.ORG.CN@YINZHENGJIE.ORG.CN renew until 07/12/2019 19:17:38 [root@node102.yinzhengjie.org.cn ~]# [root@node102.yinzhengjie.org.cn ~]# [root@node102.yinzhengjie.org.cn ~]# beeline Java HotSpot(TM) 64-Bit Server VM warning: ignoring option MaxPermSize=512M; support was removed in 8.0 Java HotSpot(TM) 64-Bit Server VM warning: ignoring option MaxPermSize=512M; support was removed in 8.0 Beeline version 1.1.0-cdh5.15.1 by Apache Hive beeline> !connect jdbc:hive2://node101.yinzhengjie.org.cn:10000/default;principal=hive/node101.yinzhengjie.org.cn@YINZHENGJIE.ORG.CN scan complete in 2ms Connecting to jdbc:hive2://node101.yinzhengjie.org.cn:10000/default;principal=hive/node101.yinzhengjie.org.cn@YINZHENGJIE.ORG.CN Connected to: Apache Hive (version 1.1.0-cdh5.15.1) Driver: Hive JDBC (version 1.1.0-cdh5.15.1) Transaction isolation: TRANSACTION_REPEATABLE_READ 0: jdbc:hive2://node101.yinzhengjie.org.cn:10> 0: jdbc:hive2://node101.yinzhengjie.org.cn:10>
9>.使用lisi用户测试
10>.






