28. RBAC
28.1 Kubernetes API 鉴权流程
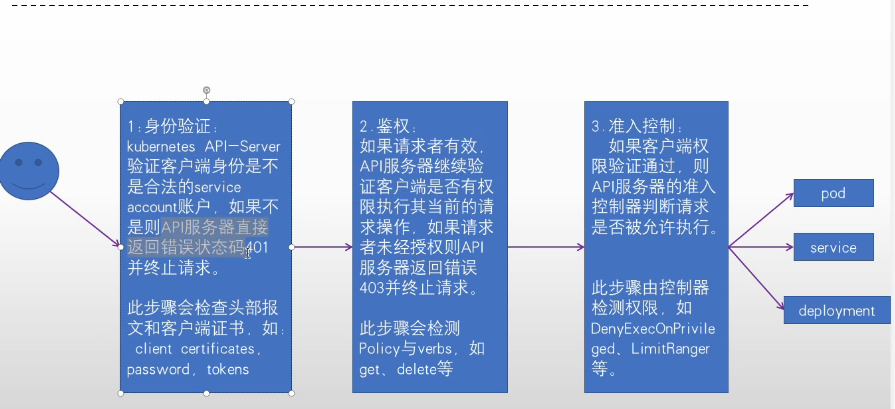
| kubernetes API-Server验证客户端身份是不是合法的service account账户,如果不是则API服务器直接返回错误状态码401并终止请求,此步骤会检查头部报文和客户端证书如:client certificates,password,tokens |
| 如果请求者有效,API服务器继续验证客户端是否有权限执行当前的请求操作,如果请求者未经授权则API服务器返回错误403并终止请求 此步骤会检测Policy与verbs,如get、delete |
| 如果客户端权限验证通过,则API服务器的准入控制器判断请求是否呗允许执行 |
| 此步骤由控制器检测权限,如:DenyExecOnPrivileged、LimitRanger等 |
28.2 RBAC简介
| RBAC API声明了四种Kubernetes对象:Role、ClusterRole、RoleBinding和ClusterRoleBinding |
| |
| Role:定义一组规则,用于访问命名空间中的Kubernetes资源 |
| |
| RoleBinding:定义用户和角色(Role)的绑定关系 |
| |
| ClusterRole:定义了一组访问集群中Kubernetes资源包括所有命名空间的规则 |
| |
| ClusterRoleBinding:定义了用户和集群角色(ClusterRole)的绑定关系 |

28.3 创建角色生成token授权并登录
| root@k8s-master1:~ |
| serviceaccount/quyi created |
| root@k8s-master1:~ |
| NAME SECRETS AGE |
| default 0 7d3h |
| quyi 0 8s |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| |
| kind: Role |
| apiVersion: rbac.authorization.k8s.io/v1 |
| metadata: |
| namespace: demo |
| name: quyi-role |
| rules: |
| - apiGroups: ["*"] |
| resources: ["pods/exec"] |
| |
| |
| verbs: ["get", "list", "watch", "create"] |
| |
| |
| - apiGroups: ["*"] |
| resources: ["pods"] |
| |
| |
| verbs: ["get", "list", "watch", "delete"] |
| |
| - apiGroups: ["apps/v1"] |
| resources: ["deployments"] |
| |
| |
| verbs: ["get", "watch", "list"] |
| |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| NAME CREATED AT |
| quyi-role 2022-12-17T06:27:20Z |
| |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| kind: RoleBinding |
| apiVersion: rbac.authorization.k8s.io/v1 |
| metadata: |
| name: role-bind-quyi |
| namespace: demo |
| subjects: |
| - kind: ServiceAccount |
| name: quyi |
| namespace: demo |
| roleRef: |
| kind: Role |
| name: quyi-role |
| apiGroup: rbac.authorization.k8s.io |
| |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: RoleBinding |
| metadata: |
| annotations: |
| kubectl.kubernetes.io/last-applied-configuration: | |
| {"apiVersion":"rbac.authorization.k8s.io/v1","kind":"RoleBinding","metadata":{"annotations":{},"name":"role-bind-quyi","namespace":"demo"},"roleRef":{"apiGroup":"rbac.authorization.k8s.io","kind":"Role","name":"quyi-role"},"subjects":[{"kind":"ServiceAccount","name":"quyi","namespace":"demo"}]} |
| creationTimestamp: "2022-12-17T06:33:14Z" |
| name: role-bind-quyi |
| namespace: demo |
| resourceVersion: "279142" |
| uid: 6e261f82-1112-4cd9-b8e2-36aaf80e0426 |
| roleRef: |
| apiGroup: rbac.authorization.k8s.io |
| kind: Role |
| name: quyi-role |
| subjects: |
| - kind: ServiceAccount |
| name: quyi |
| namespace: demo |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| apiVersion: v1 |
| kind: Secret |
| type: kubernetes.io/service-account-token |
| metadata: |
| name: quyi-admin-user |
| namespace: demo |
| annotations: |
| kubernetes.io/service-account.name: "quyi" |
| |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| NAME TYPE DATA AGE |
| quyi-admin-user kubernetes.io/service-account-token 3 9s |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| Name: quyi-admin-user |
| Namespace: demo |
| Labels: <none> |
| Annotations: kubernetes.io/service-account.name: quyi |
| kubernetes.io/service-account.uid: 0e05998b-30d7-4749-a1a0-72da075b49d5 |
| |
| Type: kubernetes.io/service-account-token |
| |
| Data |
| ==== |
| ca.crt: 1302 bytes |
| |
| namespace: 4 bytes |
| token: eyJhbGciOiJSUzI1NiIsImtpZCI6Im1TckdJQzhDUVIxM2RqeWxCV211TXQ1b3M1N1hYSlljTEptU2lhanRWT2cifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZW1vIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InF1eWktYWRtaW4tdXNlciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJxdXlpIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMGUwNTk5OGItMzBkNy00NzQ5LWExYTAtNzJkYTA3NWI0OWQ1Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRlbW86cXV5aSJ9.JKebBWn7NiI3Dyz_etkks_6FMvawFqG2-V1VcH3Vu32xjLUs_9CbqSDBVoV2pF3Olp_KeMcRKypTDj5cPdMrNuvqX17DEfcuhZU11RgInwPtlx6otEf1I9Wsg5qRGByJZ1AKjLzpdsEk_zHBZQaRsr9aMD3Ao3Hir-UYwqrHR2UOGq-wvlmyZ9ODF5z4RRJYYDQxOFmWIXPZ7ch5iEo2cXiIvhdNb5uRdHoY1ucYusbWUQunBkeH5qZG3djAaigK3KE3YBlntK2_1xHvnjLGPqkCYj1RwO2YU17QfRK8gkSS7_yBcpQkEHJD3eV8-ovuq-_jOXbdRdSC5py124mSEw |
| root@k8s-master1:~/20220814/RBAC-yaml-case |
| |
28.4 生成kubeconfig文件登录
| |
| root@k8s-master1:~/dashboard-v2.6.0 |
| |
| root@k8s-master1:~/dashboard-v2.6.0 |
| |
28.5 普通用户实现kubeconfig文件登录
| root@k8s-master1:~/20220814/RBAC-yaml-case/certs |
| { |
| "CN": "China", |
| "hosts": [], |
| "key": { |
| "algo": "rsa", |
| "size": 2048 |
| }, |
| "names": [ |
| { |
| "C": "CN", |
| "ST": "BeiJing", |
| "L": "BeiJing", |
| "O": "k8s", |
| "OU": "System" |
| } |
| ] |
| } |
| root@k8s-deploy-ha:~ |
| { |
| "signing": { |
| "default": { |
| "expiry": "438000h" |
| }, |
| "profiles": { |
| "kubernetes": { |
| "usages": [ |
| "signing", |
| "key encipherment", |
| "server auth", |
| "client auth" |
| ], |
| "expiry": "438000h" |
| } |
| }, |
| "profiles": { |
| "kcfg": { |
| "usages": [ |
| "signing", |
| "key encipherment", |
| "client auth" |
| ], |
| "expiry": "438000h" |
| } |
| } |
| } |
| } |
| |
| cfssl gencert -ca=/etc/kubernetes/ssl/ca.pem -ca-key=/etc/kubernetes/ssl/ca-key.pem -config=./ca-config.json -profile=kubernetes ./quyi-csr.json | cfssljson -bare quyi |
| |
| root@k8s-master1:~/20220814/RBAC-yaml-case/certs |
| |
| |
| kubectl config set-cluster cluster1 --certificate-authority=/etc/kubernetes/ssl/ca.pem --embed-certs=true --server=https://127.0.0.1:6443 --kubeconfig=quyi.kubeconfig |
| |
| |
| cp *.pem /etc/kubernetes/ssl/ |
| |
| kubectl config set-credentials quyi \ |
| --client-certificate=/etc/kubernetes/ssl/quyi.pem \ |
| --client-key=/etc/kubernetes/ssl/quyi-key.pem \ |
| --embed-certs=true \ |
| --kubeconfig=quyi.kubeconfig |
| 然后这个文件里面就会有一个用户了quyi.kubeconfig |
| |
| |
| https://kubernetes.io/zh/docs/concepts/configuration/organize-cluster-access-kubeconfig/ |
| |
| kubectl config set-context cluster1 \ |
| --cluster=cluster1 \ |
| --user=quyi \ |
| --namespace=demo \ |
| --kubeconfig=quyi.kubeconfig |
| 然后就有一些集群信息了 |
| contexts: |
| - context: |
| cluster: cluster1 |
| namespace: demo |
| user: quyi |
| name: cluster1 |
| |
| |
| kubectl config use-context cluster1 --kubeconfig=quyi.kubeconfig |
| |
| |
| token: eyJhbGciOiJSUzI1NiIsImtpZCI6Im1TckdJQzhDUVIxM2RqeWxCV211TXQ1b3M1N1hYSlljTEptU2lhanRWT2cifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZW1vIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InF1eWktYWRtaW4tdXNlciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJxdXlpIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMGUwNTk5OGItMzBkNy00NzQ5LWExYTAtNzJkYTA3NWI0OWQ1Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRlbW86cXV5aSJ9.JKebBWn7NiI3Dyz_etkks_6FMvawFqG2-V1VcH3Vu32xjLUs_9CbqSDBVoV2pF3Olp_KeMcRKypTDj5cPdMrNuvqX17DEfcuhZU11RgInwPtlx6otEf1I9Wsg5qRGByJZ1AKjLzpdsEk_zHBZQaRsr9aMD3Ao3Hir-UYwqrHR2UOGq-wvlmyZ9ODF5z4RRJYYDQxOFmWIXPZ7ch5iEo2cXiIvhdNb5uRdHoY1ucYusbWUQunBkeH5qZG3djAaigK3KE3YBlntK2_1xHvnjLGPqkCYj1RwO2YU17QfRK8gkSS7_yBcpQkEHJD3eV8-ovuq-_jOXbdRdSC5py124mSEw |