|NO.Z.00018|——————————|CloudNative|——|Kubernetes&RBAC介绍.V01|——|命名空间|
一、集群的安全机制
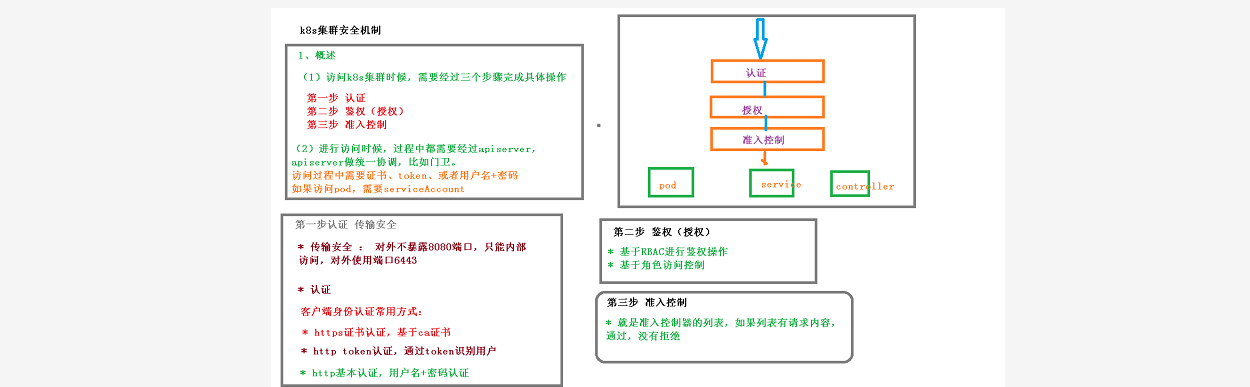
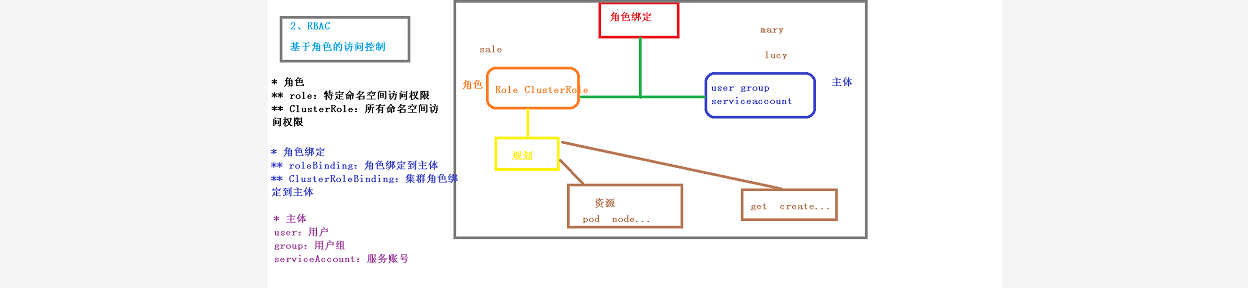
二、k8s集群安全机制-rbac实现鉴权
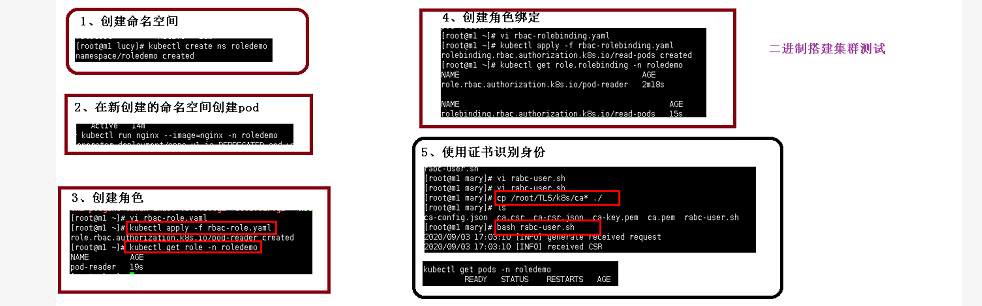
一、创建一个命名空间
### --- 创建一个命名空间
[root@k8s-master ~]# kubectl get ns
NAME STATUS AGE
default Active 3d23h
kube-node-lease Active 3d23h
kube-public Active 3d23h
kube-system Active 3d23h[root@k8s-master ~]# kubectl create ns roledemo
namespace/roledemo created
[root@k8s-master ~]# kubectl get ns
roledemo Active 3s### --- 在新创建的命名空间下创建一个pod
[root@k8s-master ~]# kubectl run nginx --image=nginx -n roledemo
pod/nginx created
[root@k8s-master ~]# kubectl get pods -n roledemo
NAME READY STATUS RESTARTS AGE
nginx 0/1 ErrImagePull 0 59s### --- 创建角色,将rbac-role.yaml该文件上传到服务器
[root@k8s-master ~]# cat rbac-role.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace:roledemo # 命名空间的名称和刚才创建的一致
name: pod-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["pods"]
verbs: ["get", "watch", "list"] # 权限 [root@k8s-master ~]# kubectl apply -f rbac-role.yaml
role.rbac.authorization.k8s.io/pod-reader created~~~ 查看创建的角色
[root@k8s-master ~]# kubectl get role -n roledemo
NAME CREATED AT
pod-reader 2021-02-23T08:03:31Z### --- 创建角色绑定过程
[root@k8s-master ~]# cat rbac-rolebinding.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: roledemo
subjects:
- kind: User
name: mary # Name is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role # this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io[root@k8s-master ~]# kubectl apply -f rbac-rolebinding.yaml
rolebinding.rbac.authorization.k8s.io/read-pods created~~~ 查看绑定结果
[root@k8s-master ~]# kubectl get role,rolebinding -n roledemo
NAME CREATED AT
role.rbac.authorization.k8s.io/pod-reader 2021-02-23T08:03:31Z
NAME ROLE AGE
rolebinding.rbac.authorization.k8s.io/read-pods Role/pod-reader 94s ### --- 使用证书来识别它的身份,将rabc-user.sh该文件上传到服务器
[root@k8s-master ~]# mkdir mary
[root@k8s-master ~]# cd mary/
cat > mary-csr.json <<EOF
{
"CN": "mary",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOFcfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes mary-csr.json | cfssljson -bare mary
kubectl config set-cluster kubernetes \
--certificate-authority=ca.pem \
--embed-certs=true \
--server=https://10.10.10.11:6443 \
--kubeconfig=mary-kubeconfigkubectl config set-credentials mary \
--client-key=mary-key.pem \
--client-certificate=mary.pem \
--embed-certs=true \
--kubeconfig=mary-kubeconfig
kubectl config set-context default \
--cluster=kubernetes \
--user=mary \
--kubeconfig=mary-kubeconfig
kubectl config use-context default --kubeconfig=mary-kubeconfig ### --- 执行脚本文件,将证书文件拷贝到当前目录
[root@k8s-master mary]# bash rabc-user.sh
~~~ 会多出两个文件
[root@k8s-master mary]# ls
mary-csr.json mary-kubeconfig ~~~ 里面有证书信息
[root@k8s-master mary]# cat mary-kubeconfig
~~~ 什么也查看不到,是使用rbac的方式创建的。
[root@k8s-master mary]# kubectl get svc -n roledemo
No resources found in roledemo namespace.Walter Savage Landor:strove with none,for none was worth my strife.Nature I loved and, next to Nature, Art:I warm'd both hands before the fire of life.It sinks, and I am ready to depart
——W.S.Landor





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通