|NO.Z.00009|——————————|^^ 部署 ^^|——|Kubernetes&二进制部署.V05|——|部署Master Node|
一、部署Master Node:生成kube-apiserver证书
### --- 自签证书颁发机构(CA)
[root@k8s-master ~]# cd TLS/k8s/
[root@k8s-master k8s]# cat > ca-config.json<< EOF
> {
> "signing": {
> "default": {
> "expiry": "87600h"
> },
> "profiles": {
> "kubernetes": {
> "expiry": "87600h",
> "usages": [
> "signing",
> "key encipherment",
> "server auth",
> "client auth"
> ]
> }
> }
> }
> }
> EOF[root@k8s-master k8s]# cat > ca-csr.json<< EOF
> {
> "CN": "kubernetes",
> "key": {
> "algo": "rsa",
> "size": 2048
> },
> "names": [
> {
> "C": "CN",
> "L": "Beijing",
> "ST": "Beijing",
> "O": "k8s",
> "OU": "System"
> }
> ]
> }
> EOF### --- 生成证书
[root@k8s-master k8s]# cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
2021/02/21 15:04:01 [INFO] generating a new CA key and certificate from CSR
2021/02/21 15:04:01 [INFO] generate received request
2021/02/21 15:04:01 [INFO] received CSR
2021/02/21 15:04:01 [INFO] generating key: rsa-2048
2021/02/21 15:04:02 [INFO] encoded CSR
2021/02/21 15:04:02 [INFO] signed certificate with serial number 458860324905470174378828992213776476390630171697
[root@k8s-master k8s]# ls *pem
ca-key.pem ca.pem### --- 使用自签CA签发kube-apiserver HTTPS证书
[root@k8s-master k8s]# cd ~/TLS/k8s/
[root@k8s-master k8s]# cat > server-csr.json<< EOF
> {
> "CN": "kubernetes",
> "hosts": [
> "10.0.0.1",
> "127.0.0.1",
> "10.10.10.11",
> "10.10.10.12",
> "10.10.10.13",
> "10.10.10.14",
> "10.10.10.21",
> "10.10.10.22",
> "20.20.20.23",
> "kubernetes",
> "kubernetes.default",
> "kubernetes.default.svc",
> "kubernetes.default.svc.cluster",
> "kubernetes.default.svc.cluster.local"
> ],
> "key": {
> "algo": "rsa",
> "size": 2048
> },
> "names": [
> {
> "C": "CN",
> "L": "BeiJing",
> "ST": "BeiJing",
> "O": "k8s",
> "OU": "System"
> }
> ]
> }
> EOF### --- 生成证书
[root@k8s-master k8s]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes server-csr.json | cfssljson -bare server
2021/02/21 15:10:30 [INFO] generate received request
2021/02/21 15:10:30 [INFO] received CSR
2021/02/21 15:10:30 [INFO] generating key: rsa-2048
2021/02/21 15:10:30 [INFO] encoded CSR
2021/02/21 15:10:30 [INFO] signed certificate with serial number 609265889790977678758654408246111931762727275377
2021/02/21 15:10:30 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").[root@k8s-master k8s]# ls server*pem
server-key.pem server.pem二、从GitHub下载二进制文件
### --- 从GitHub下载二进制文件
~~~ 下载地址:https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG/CHANGELOG-1.18.md#v1183
~~~ 注:打开连接你会发现里面有很多包,下载一个server包就够了,包含了Master和Worker Node二进制文件
[root@k8s-master ~]# wget -c https://dl.k8s.io/v1.18.3/kubernetes-server-linux-amd64.tar.gz### --- 解压二进制包
[root@k8s-master ~]# mkdir -p /opt/kubernetes/{bin,cfg,ssl,logs}
[root@k8s-master ~]# tar -zxvf kubernetes-server-linux-amd64.tar.gz
[root@k8s-master ~]# cd kubernetes/server/bin
[root@k8s-master bin]# cp kube-apiserver kube-scheduler kube-controller-manager /opt/kubernetes/bin/
[root@k8s-master bin]# cp kubectl /usr/bin/三、部署kube-apiserver
### --- 创建配置文件
~~~ 注:上面两个 \\ 第一个是转义符,第二个是换行符,使用转义符是为了使用EOF保留换行符。
~~~ -logtostderr:启用日志
~~~ -v:日志等级
~~~ -log-dir:日志目录
~~~ -etcd-servers: etcd集群地址
~~~ -bind-addrss:监听地址
~~~ -secure-port:https安全端口
~~~ -advertise-address:集群通告地址
~~~ -allow-privileged:启用授权
~~~ -service-cluster-ip-range: Service虚拟IP地址段
~~~ -enable-admission-plugins:准入控制模块
~~~ -authorization-mode:认证授权,启用RBAC授权和节点自管理
~~~ -enable-bootstrap-token-auth:启用TLSbootstrap机制
~~~ -token-auth-file:bootstrap token文件
~~~ -service-node-port-range: Service nodeport类型默认分配端口范围
~~~ -kubelet-client-xxx:apiserver访问kubelet客户端证书
~~~ -tls-xxx-file:apiserver https证书
~~~ -etcd-xxxfile:连接Etcd集群证书
~~~ -audit-log-xxx:审计日志
[root@k8s-master ~]# cat > /opt/kubernetes/cfg/kube-apiserver.conf << EOF
> KUBE_APISERVER_OPTS="--logtostderr=false \\
> --v=2 \\
> --log-dir=/opt/kubernetes/logs \\
> --etcd-servers=https://10.10.10.11:2379,https://10.10.10.12:2379,https://10.10.10.13:2379 \\
> --bind-address=10.10.10.11 \\
> --secure-port=6443 \\
> --advertise-address=10.10.10.11 \\
> --allow-privileged=true \\
> --service-cluster-ip-range=10.0.0.0/24 \\
> --enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction \\
> --authorization-mode=RBAC,Node \\
> --enable-bootstrap-token-auth=true \\
> --token-auth-file=/opt/kubernetes/cfg/token.csv \\
> --service-node-port-range=30000-32767 \\
> --kubelet-client-certificate=/opt/kubernetes/ssl/server.pem \\
> --kubelet-client-key=/opt/kubernetes/ssl/server-key.pem \\
> --tls-cert-file=/opt/kubernetes/ssl/server.pem \\
> --tls-private-key-file=/opt/kubernetes/ssl/server-key.pem \\
> --client-ca-file=/opt/kubernetes/ssl/ca.pem \\
> --service-account-key-file=/opt/kubernetes/ssl/ca-key.pem \\
> --etcd-cafile=/opt/etcd/ssl/ca.pem \\
> --etcd-certfile=/opt/etcd/ssl/server.pem \\
> --etcd-keyfile=/opt/etcd/ssl/server-key.pem \\
> --audit-log-maxage=30 \\
> --audit-log-maxbackup=3 \\
> --audit-log-maxsize=100 \\
> --audit-log-path=/opt/kubernetes/logs/k8s-audit.log"
> EOF### --- 拷贝方才生成的证书
~~~ 把刚才生成的网证书拷贝到配置文件中的路径:
[root@k8s-master ~]# cp ~/TLS/k8s/ca*pem ~/TLS/k8s/server*pem /opt/kubernetes/ssl/
[root@k8s-master ~]# ls /opt/kubernetes/ssl/
ca-key.pem ca.pem server-key.pem server.pem### --- 启用TLS Bootstrapping机制
~~~ TLS Bootstraping:Master apiserver启用TLS认证后,
~~~ Node节点kubelet和kube-proxy要与kube-apiserver进行通信,
~~~ 必须使用CA签发的有效证书才可以,当Node节点很多时,
~~~ 这种客户端证书颁发需要大量的工作,同样也会增加集群扩展复杂度,
~~~ 为了简化流程,Kubernetes引入了TLS bootstraping机制来自动颁发客户端证书,
~~~ kubelet会以一个低权限用户自动向apiserver申请证书,
~~~ kubelet的证书由apiserver动态签署,所以强烈建议在Node上使用这种方式,
~~~ 目前主要用于kubelet/kube-proxy还是由我们统一颁发一个证书
### --- TLS bootstraping工作流程: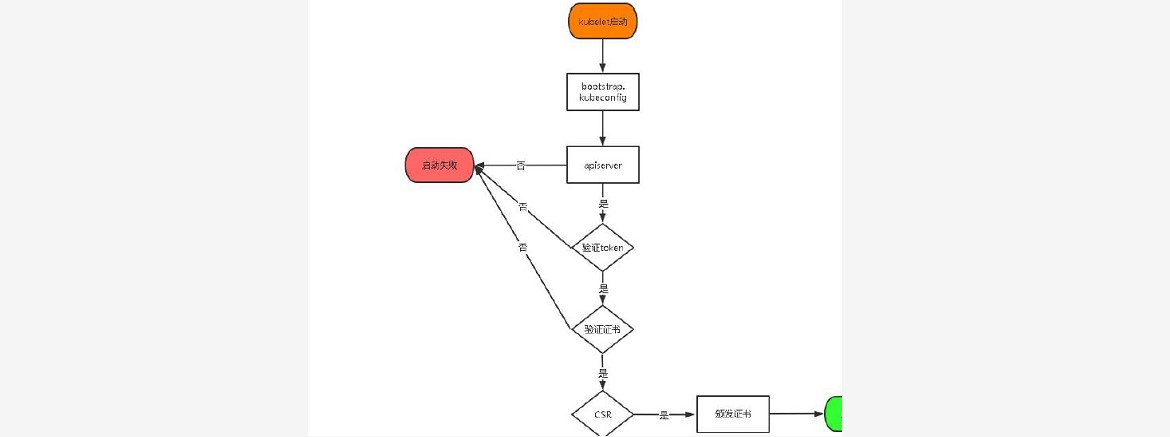
~~~ 创建上述配置文件中token文件:
~~~ 格式:token. 用户名,UID,用户组
[root@k8s-master ~]# cat > /opt/kubernetes/cfg/token.csv << EOF
> 61dd7ce372bc27b3794787e5cf74e0e8,kubelet-bootstrap,10001,"system:nodebootstrapper"
> EOF~~~ token也可以自行生成替换
[root@k8s-master ~]# head -c 16 /dev/urandom | od -An -t x | tr -d ' '
61dd7ce372bc27b3794787e5cf74e0e8### --- system的管理apiserver
[root@k8s-master ~]# cat > /usr/lib/systemd/system/kube-apiserver.service << EOF
> [Unit]
> Description=Kubernetes API Server
> Documentation=https://github.com/kubernetes/kubernetes
> [Service]
> EnvironmentFile=/opt/kubernetes/cfg/kube-apiserver.conf
> ExecStart=/opt/kubernetes/bin/kube-apiserver \$KUBE_APISERVER_OPTS
> Restart=on-failure
> [Install]
> WantedBy=multi-user.target
> EOF### --- 启动并设置开机启动
[root@k8s-master ~]# systemctl daemon-reload
[root@k8s-master ~]# systemctl start kube-apiserver
[root@k8s-master ~]# systemctl enable kube-apiserver### --- 授权kubelet-bootstrap用户允许请求证书
[root@k8s-master ~]# kubectl create clusterrolebinding kubelet-bootstrap \
> --clusterrole=system:node-bootstrapper \
> --user=kubelet-bootstrap
~~~ 自动输出参数
clusterrolebinding.rbac.authorization.k8s.io/kubelet-bootstrap created 四、部署kube-controller-manager
### --- 创建配置文件
~~~ --master:通过本地非安全本地端口8080连接apiserver
~~~ --leader-elect:当该组件启动多个时,自动选举(HA)
~~~ --cluster-siging-cert-file/ -cluster-signing-key-file:自动为kubelet颁发证书的CA,与apiserver保持一致
[root@k8s-master ~]# cat > /opt/kubernetes/cfg/kube-controller-manager.conf << EOF
> KUBE_CONTROLLER_MANAGER_OPTS="--logtostderr=false \\
> --v=2 \\
> --log-dir=/opt/kubernetes/logs \\
> --leader-elect=true \\
> --master=127.0.0.1:8080 \\
> --bind-address=127.0.0.1 \\
> --allocate-node-cidrs=true \\
> --cluster-cidr=10.244.0.0/16 \\
> --service-cluster-ip-range=10.0.0.0/24 \\
> --cluster-signing-cert-file=/opt/kubernetes/ssl/ca.pem \\
> --cluster-signing-key-file=/opt/kubernetes/ssl/ca-key.pem \\
> --root-ca-file=/opt/kubernetes/ssl/ca.pem \\
> --service-account-private-key-file=/opt/kubernetes/ssl/ca-key.pem \\
> --experimental-cluster-signing-duration=87600h0m0s"
> EOF### --- systemd管理controller-manager
[root@k8s-master ~]# cat > /usr/lib/systemd/system/kube-controller-manager.service << EOF
> [Unit]
> Description=Kubernetes Controller Manager
> Documentation=https://github.com/kubernetes/kubernetes
> [Service]
> EnvironmentFile=/opt/kubernetes/cfg/kube-controller-manager.conf
> ExecStart=/opt/kubernetes/bin/kube-controller-manager \$KUBE_CONTROLLER_MANAGER_OPTS
> Restart=on-failure
> [Install]
> WantedBy=multi-user.target
> EOF### --- 启动并设置开机启动
[root@k8s-master ~]# systemctl daemon-reload
[root@k8s-master ~]# systemctl start kube-controller-manager.service
[root@k8s-master ~]# systemctl enable kube-controller-manager.service五、部署kube-scheduler
### --- 创建配置文件
~~~ -master:通过本地非安全端口8080连接apiserver
~~~ leader-elect:当该组件启动多个时,自动选举(HA)
[root@k8s-master ~]# cat > /opt/kubernetes/cfg/kube-scheduler.conf << EOF
> KUBE_SCHEDULER_OPTS="--logtostderr=false \
> --v=2 \
> --log-dir=/opt/kubernetes/logs \
> --leader-elect \
> --master=127.0.0.1:8080 \
> --bind-address=127.0.0.1"
> EOF### --- systemd管理scheduler
[root@k8s-master ~]# cat > /usr/lib/systemd/system/kube-scheduler.service << EOF
> [Unit]
> Description=Kubernetes Scheduler
> Documentation=https://github.com/kubernetes/kubernetes
> [Service]
> EnvironmentFile=/opt/kubernetes/cfg/kube-scheduler.conf
> ExecStart=/opt/kubernetes/bin/kube-scheduler \$KUBE_SCHEDULER_OPTS
> Restart=on-failure
> [Install]
> WantedBy=multi-user.target
> EOF### --- 启动并设置开机启动
[root@k8s-master ~]# systemctl daemon-reload
[root@k8s-master ~]# systemctl start kube-scheduler
[root@k8s-master ~]# systemctl enable kube-scheduler六、查看集群状态
### --- 查看集群状态
~~~ 所有组件都已经启动成功,通过kubectl工具查看当前集群组件状态
~~~ 如果输出说明Master节点组件运行正常
[root@k8s-master ~]# kubectl get cs
NAME STATUS MESSAGE ERROR
controller-manager Healthy ok
scheduler Healthy ok
etcd-1 Healthy {"health":"true"}
etcd-2 Healthy {"health":"true"}
etcd-0 Healthy {"health":"true"} Walter Savage Landor:strove with none,for none was worth my strife.Nature I loved and, next to Nature, Art:I warm'd both hands before the fire of life.It sinks, and I am ready to depart
——W.S.Landor





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通