one.ethics and proposes
1.proposes:
- monitoring the states on your computer, see if there any suspicious software
- using
sysinternalsorsystracerto analyze the backdoor we already generated in exp2 and exp3. - assuming this condition:something wired you think happen to your computer. try some way we have learned to analyze the computer. use monitor system to locate the suspicious software.
2.content:
- system operating monitor
1.log the ip from website viamission schedulecheck where these ip coming from.
2.using sysmon to find out if there any suspicious event. - analyze backdoor
1.tcp_reverse connect(focus on ddl)
2.install to target computer(focus on file)
3.any other operation
two:experiment detail
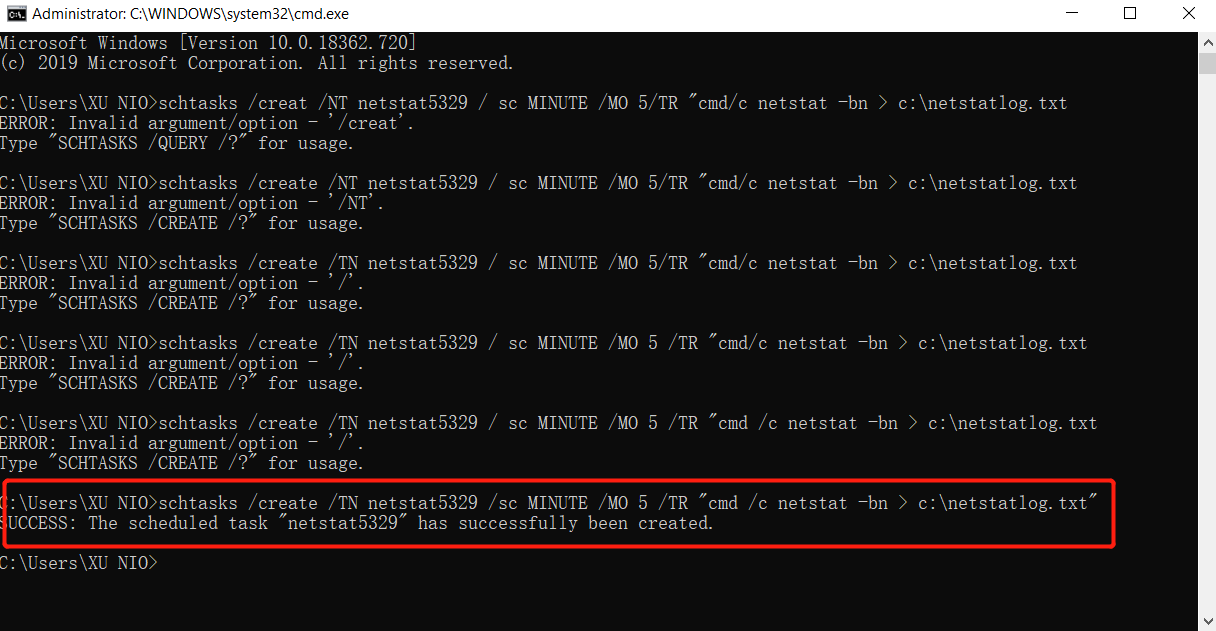
1.using schtask command to monitor
-
command
schtasks /create /TN netstat5329 /sc MINUTE /MO 5 /TR "cmd /c netstat -bn > c:\netstatlog.txt"to generate
![]()
TNis short for TASKNAME
scmeans the method to measure time. we use MINUTE as an unit.
bshows the executable file's name.
ncan show to port
trcommand need to tpye.
>file path we will input. -
in the C drive directory, we create a txt file and type
date /t >> c:\netstat5329.txt time /t >> c:\netstat5329.txt netstat -bn >> c:\netstat5329.txt
change file suffix fromtxttobat -
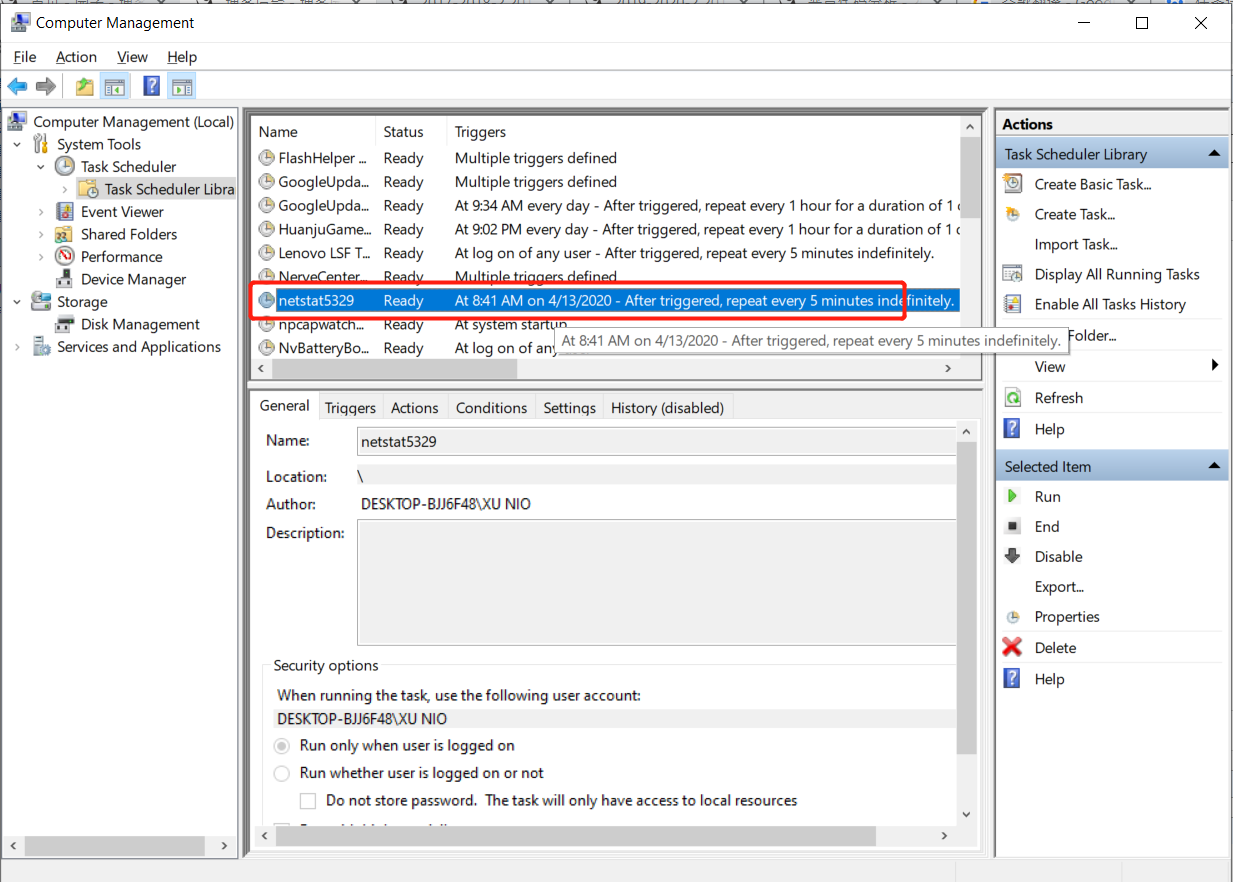
open
Task Schedulerto edit
![]()
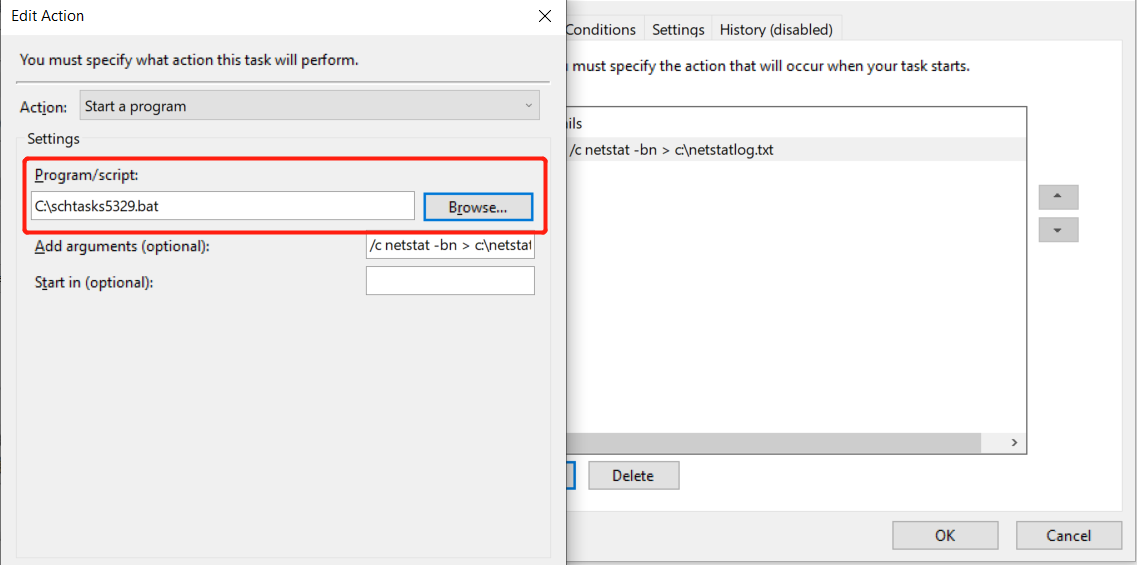
-
overwrite the path to the bat we created.
![]()
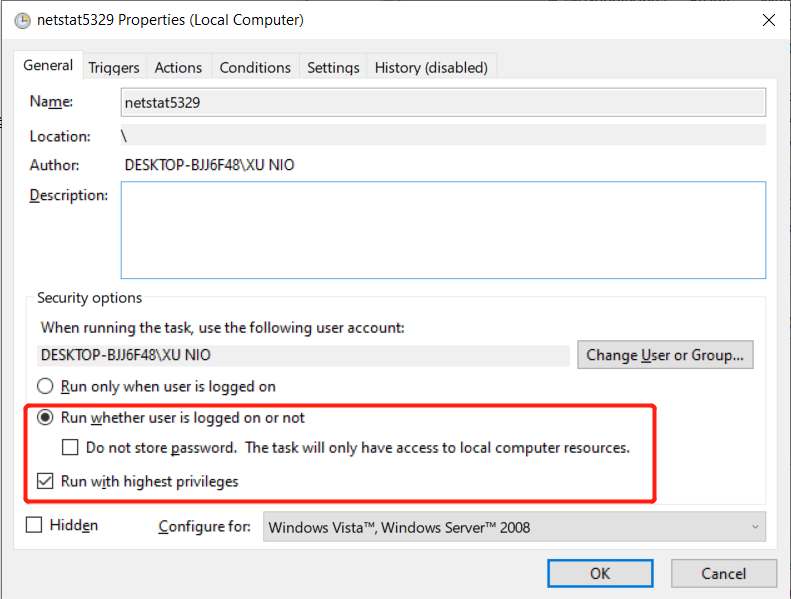
-
root this shedule
![]()
refer to nice blog i know how import data to excel.
![]()
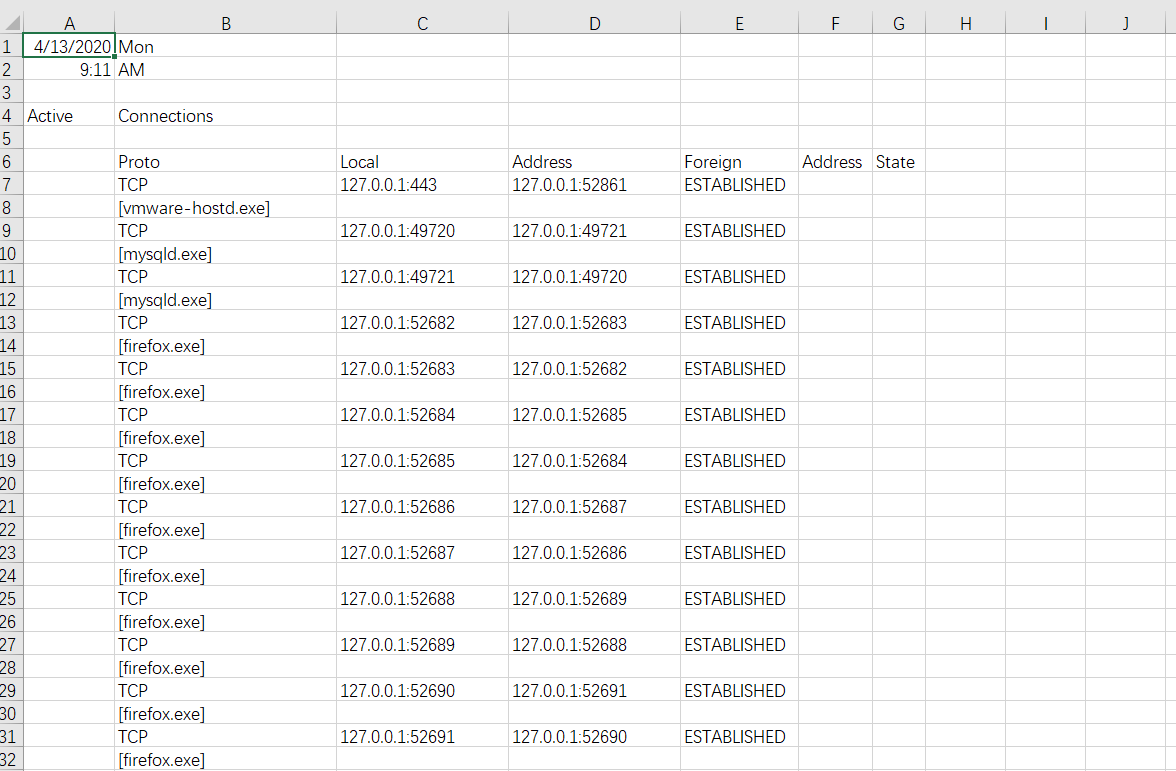
-
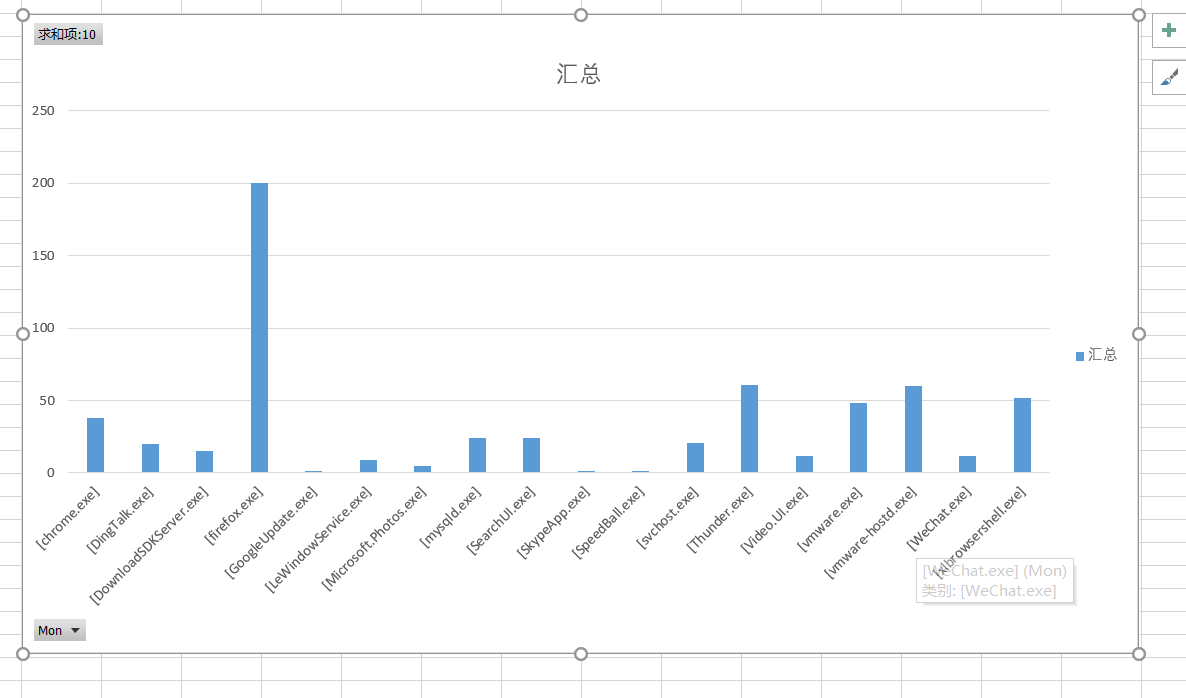
yeah,after we use excel to sort date and creat chart.i can see the net-log now.
![]()
-
clearly. on the top is firefox. i think firefox it much faster than chrome. i cant figure why sometimes chrome cant connect to web weirdly. also you can see VM to virtual machine.
-
i use thunder to download some file.
2.usingsysmon to monitor.
1.download Sysinternals Utilities,sysmonis just one software in Sysinternals Utilities.
2.select target. flit trusted log to less the recording.
3.configure sysmon20175329 in the directory of sysmon
<Sysmon schemaversion="10.42">
<!-- Capture all hashes -->
<HashAlgorithms>*</HashAlgorithms>
<EventFiltering>
<!-- Log all drivers except if the signature -->
<!-- contains Microsoft or Windows -->
<ProcessCreate onmatch="exclude">
<Image condition="end with">chrome.exe</Image>
</ProcessCreate>
<ProcessCreate onmatch="include">
<ParentImage condition="end with">cmd.exe</ParentImage>
</ProcessCreate>
<FileCreateTime onmatch="exclude" >
<Image condition="end with">chrome.exe</Image>
</FileCreateTime>
<NetworkConnect onmatch="exclude">
<Image condition="end with">chrome.exe</Image>
<SourcePort condition="is">137</SourcePort>
<SourceIp condition="is">127.0.0.1</SourceIp>
</NetworkConnect>
<NetworkConnect onmatch="include">
<DestinationPort condition="is">80</DestinationPort>
<DestinationPort condition="is">443</DestinationPort>
</NetworkConnect>
<CreateRemoteThread onmatch="include">
<TargetImage condition="end with">explorer.exe</TargetImage>
<TargetImage condition="end with">svchost.exe</TargetImage>
<TargetImage condition="end with">firefox.exe</TargetImage>
<TargetImage condition="end with">winlogon.exe</TargetImage>
<SourceImage condition="end with">powershell.exe</SourceImage>
</CreateRemoteThread>
</EventFiltering>
</Sysmon>
- select
sysmonx64to check the properties
![]()
Sysmon64 -i sysmon20175329.xmlto run and install
![]()
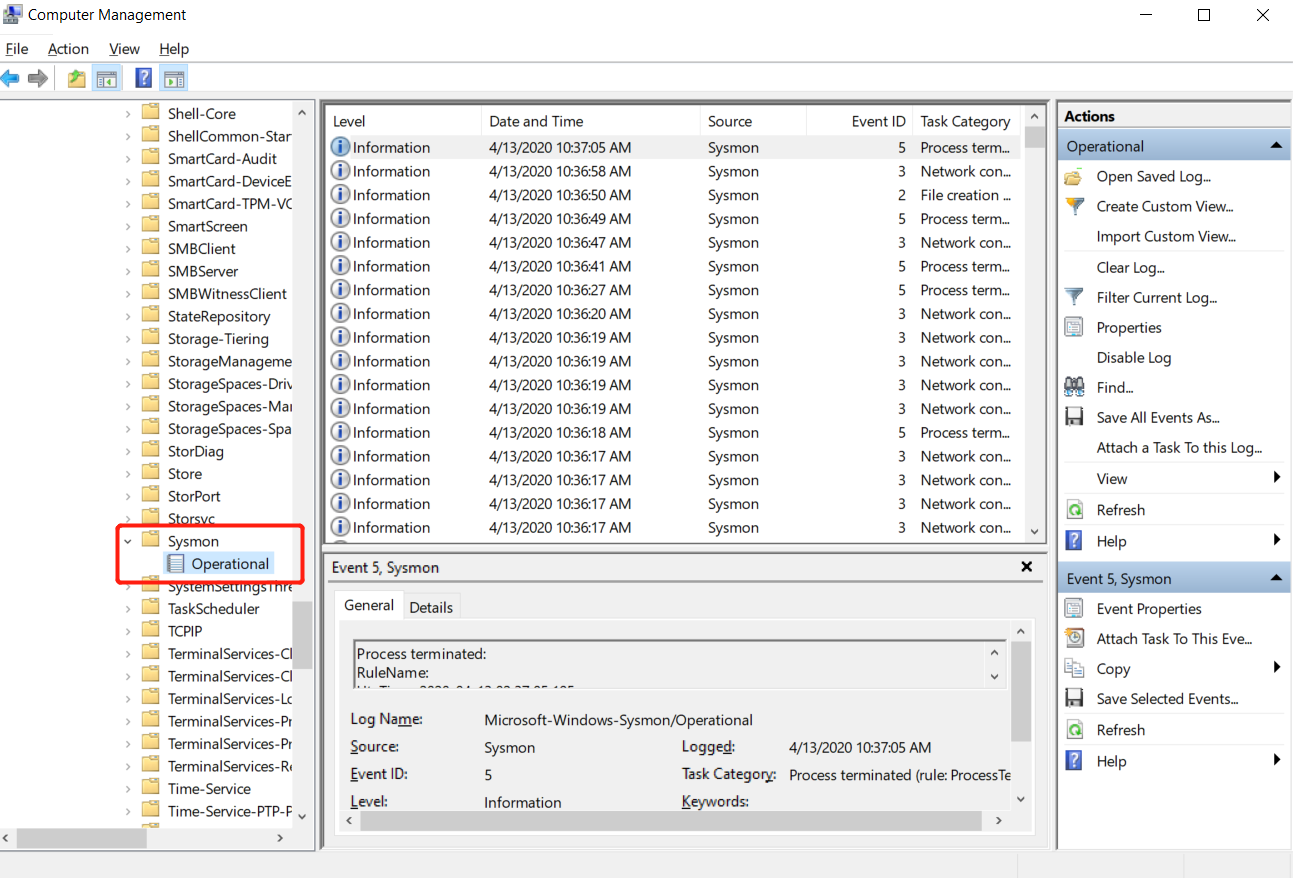
- open
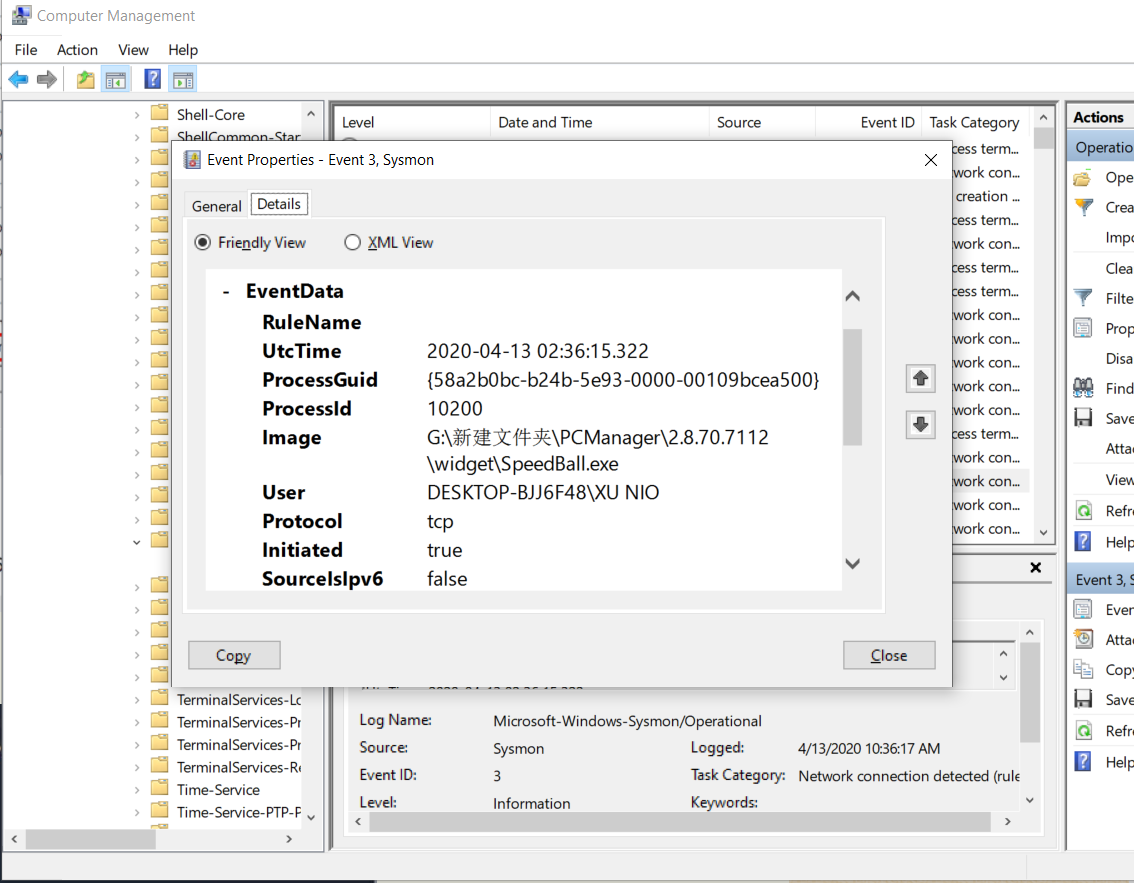
computer managerto check the new event PID etc..
![]()
3.analyze malicious code
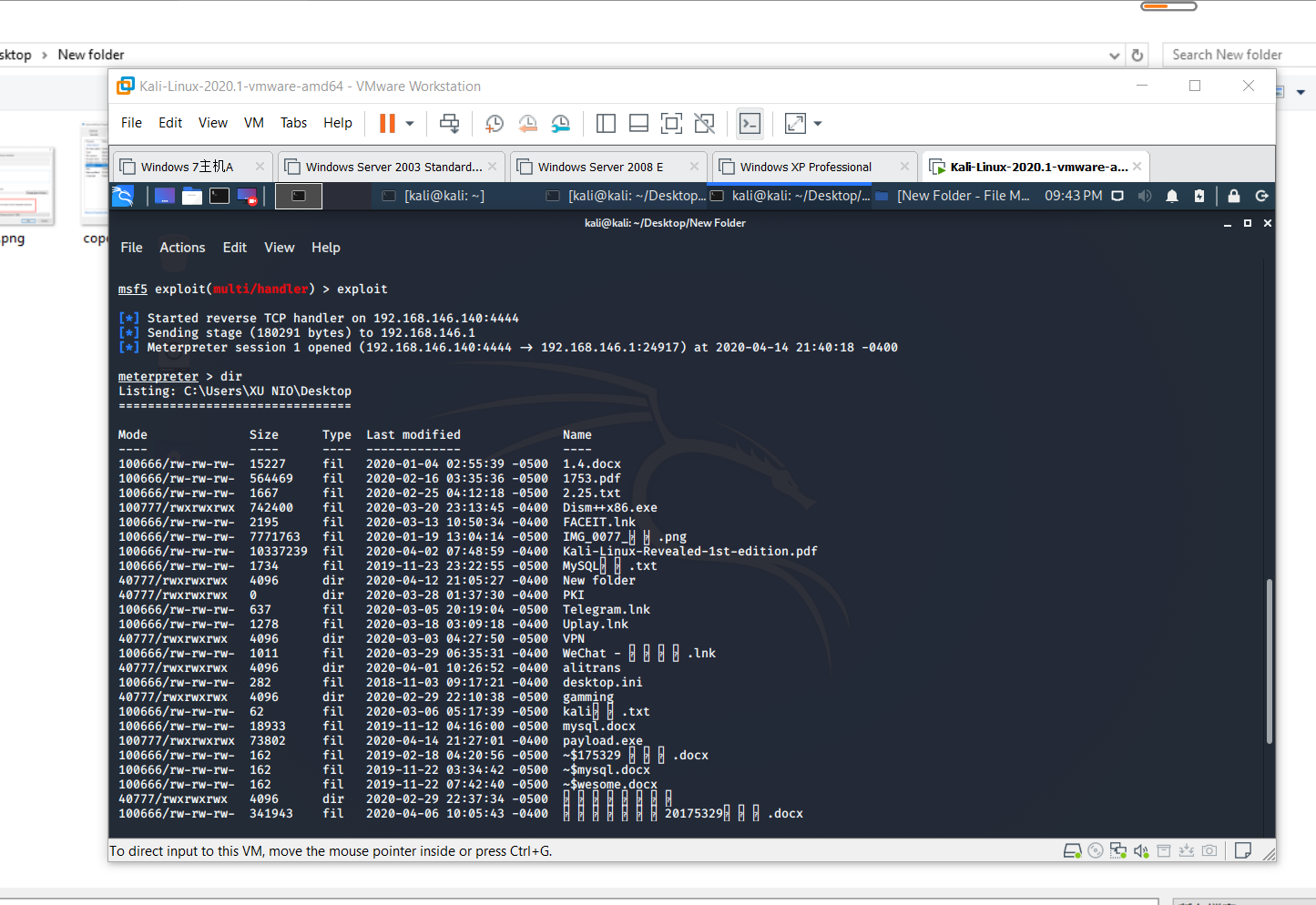
- just repeat exp2 we have done to get shell.
![]()
- here we need to use a tool called Systracer
![]()
- take snapshot:we can analyze dynamic movement from kali.
- dope!after a full scan and i check the list to find out the backdoor.
![]()
- we just need to compare to find out what's going on after inject malicious app to our computer.
![]()
- according to the request. check the operation difference.here i find one when using
cmdcommand.
![]()
- as we can see.i dont open
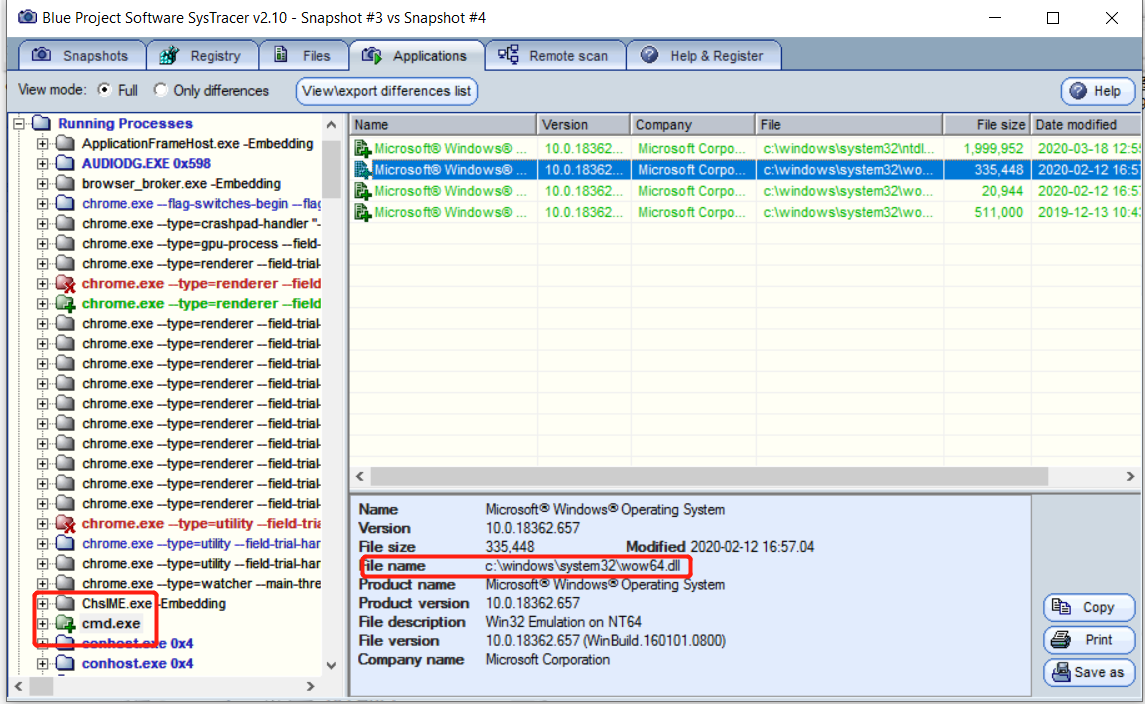
cmdterminal in windows 10.but hack by linux to get shell.so the differences are obvious.if u find some weird operation that u havent done before but the monitor show these operations are getting your private information. like they usecmdcommand to change your computer password.etc.. your computer is definitely hacked! - check the register
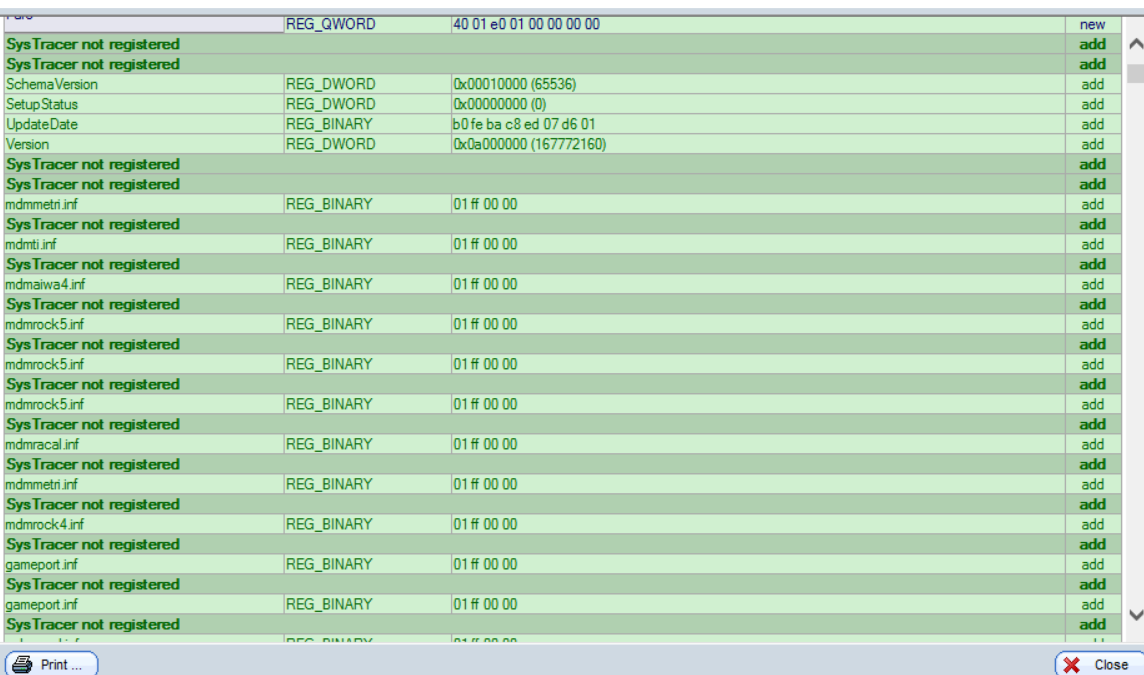
![]()
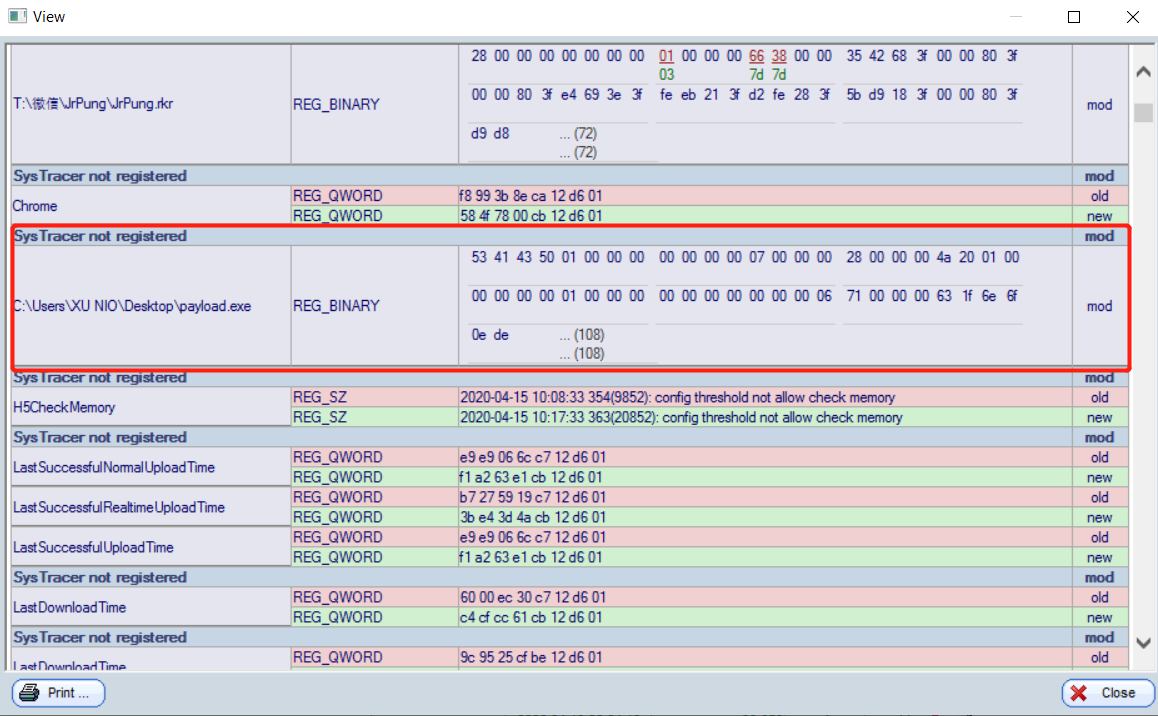
here we are. payload.exe is the backdoor i injected.we can only see the change but we cant look into it due to SysTracer not registered.also the whole change is showed via binary. we need tool to compile to see what the hacker did.
i am not sure if its about the backdoor.so i goole inf for detail
![]()
![]()
i guess the backdoor use a way to make it auto-start up so it need to edit the drive to make it happen.
when i check my mate's blog they wrote about some ddl. i just list these thought i cant find these ddl. - msvcrt.dll: C language runtime executable file provided by Microsoft in the windows operating system
- kernel32.dll: belongs to the kernel-level file, it controls the system's memory management, data input and output operations and interrupt processing, is necessary
- advapi32.dll: a part of a high-level API application interface service library, which contains functions related to object security, registry manipulation and event logs, and will be subject to virus intrusion and tampering, resulting in system file loss and damage
- wsock32.dll: Windows Sockets application program interface, used to support many Internet and network applications, is a very critical or suspicious file to the system.
- ws2_32.dll: Windows Sockets application program interface. Some viruses will create a pseudo "ws2_32.dll" file or folder in the antivirus software directory. From the antivirus software's point of view, this is called a file required for program operation. This so-called "file" does not have the system "ws2_32.dll "The function of the file, so anti-virus software, etc. will not run and it prompts: the application failed to initialize normally.
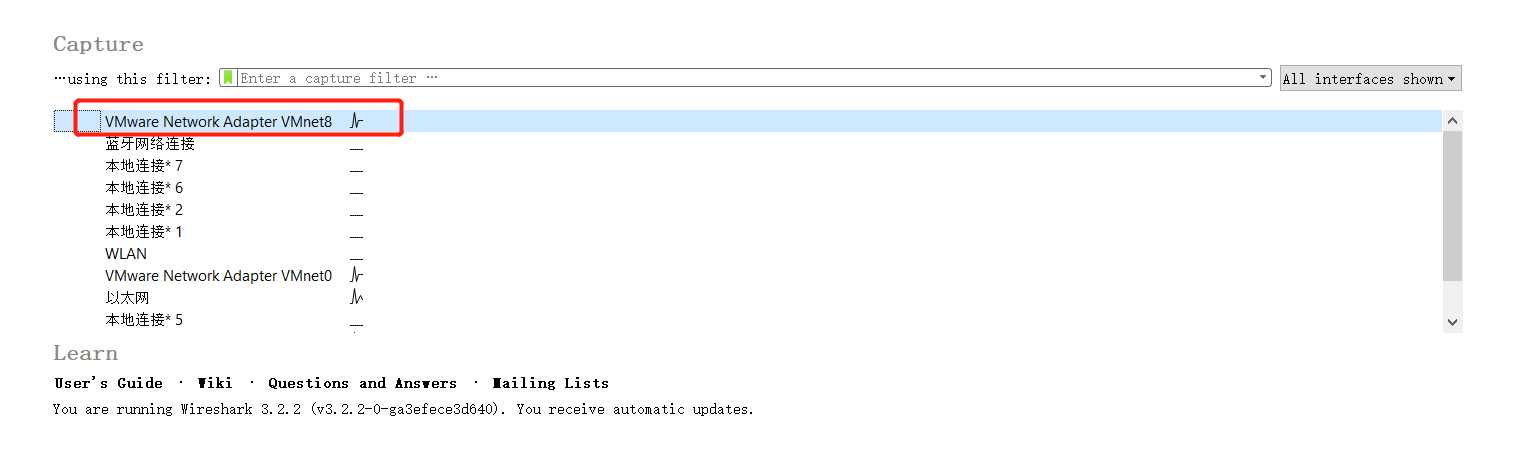
4.wireshark
- due to i cant capture the package at Ethernet and i already know the attack from my VM so i just capture from the VMware Network Adapter VMnet8.
![]()
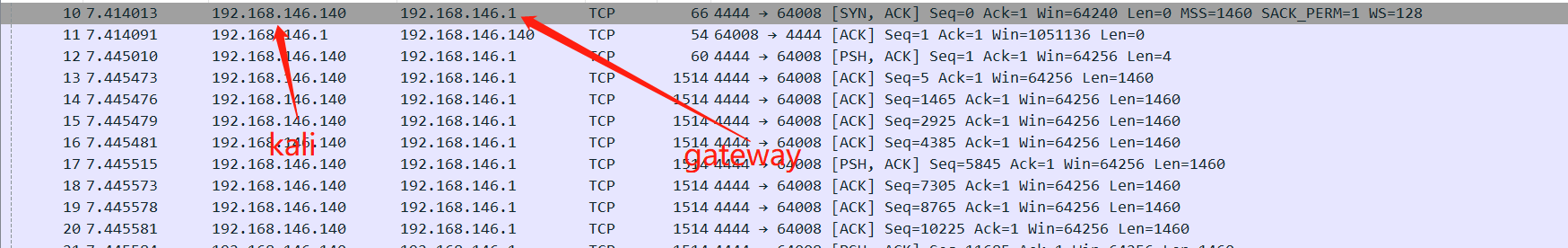
- thus ever package we see here is from the kali to the gateway.we can see three-way handshake here via tcp protocal.
![]()
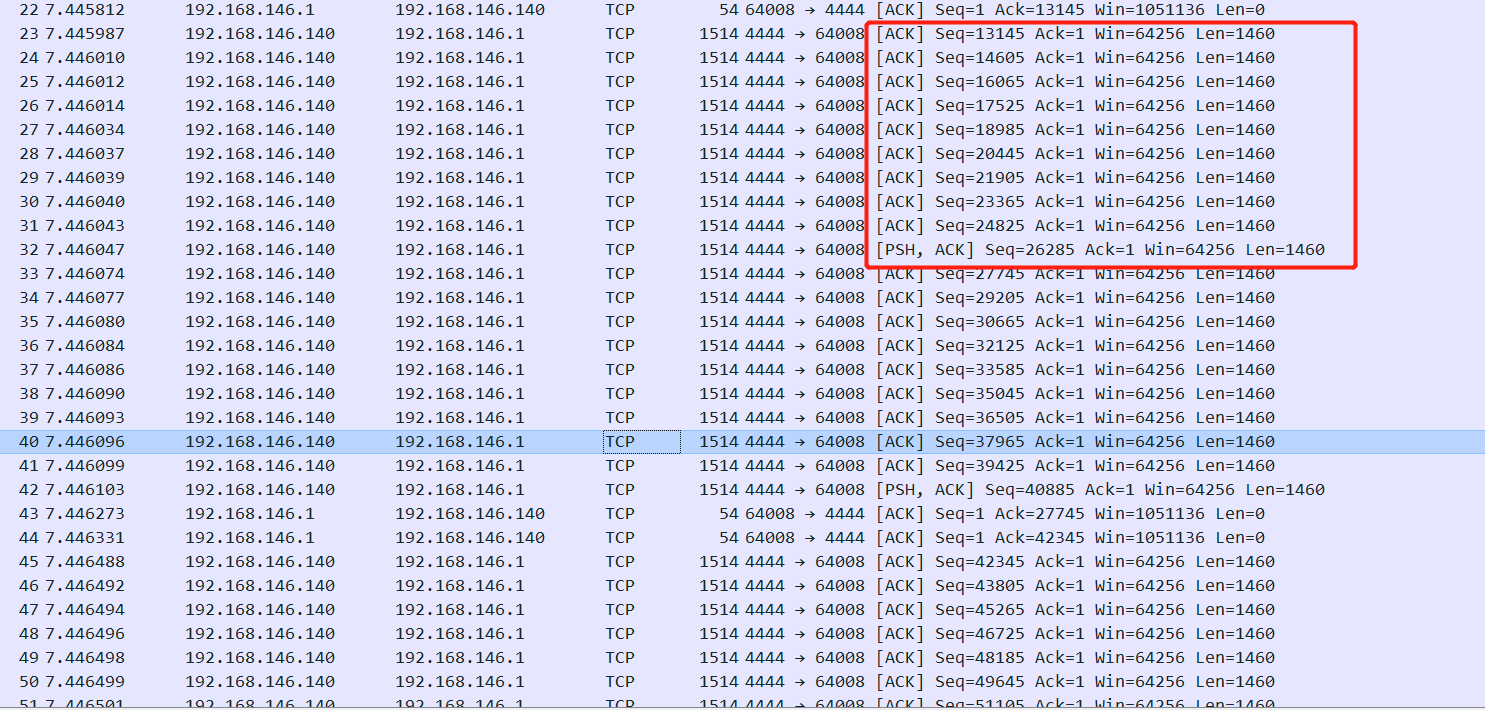
- look into for detail.
![]()
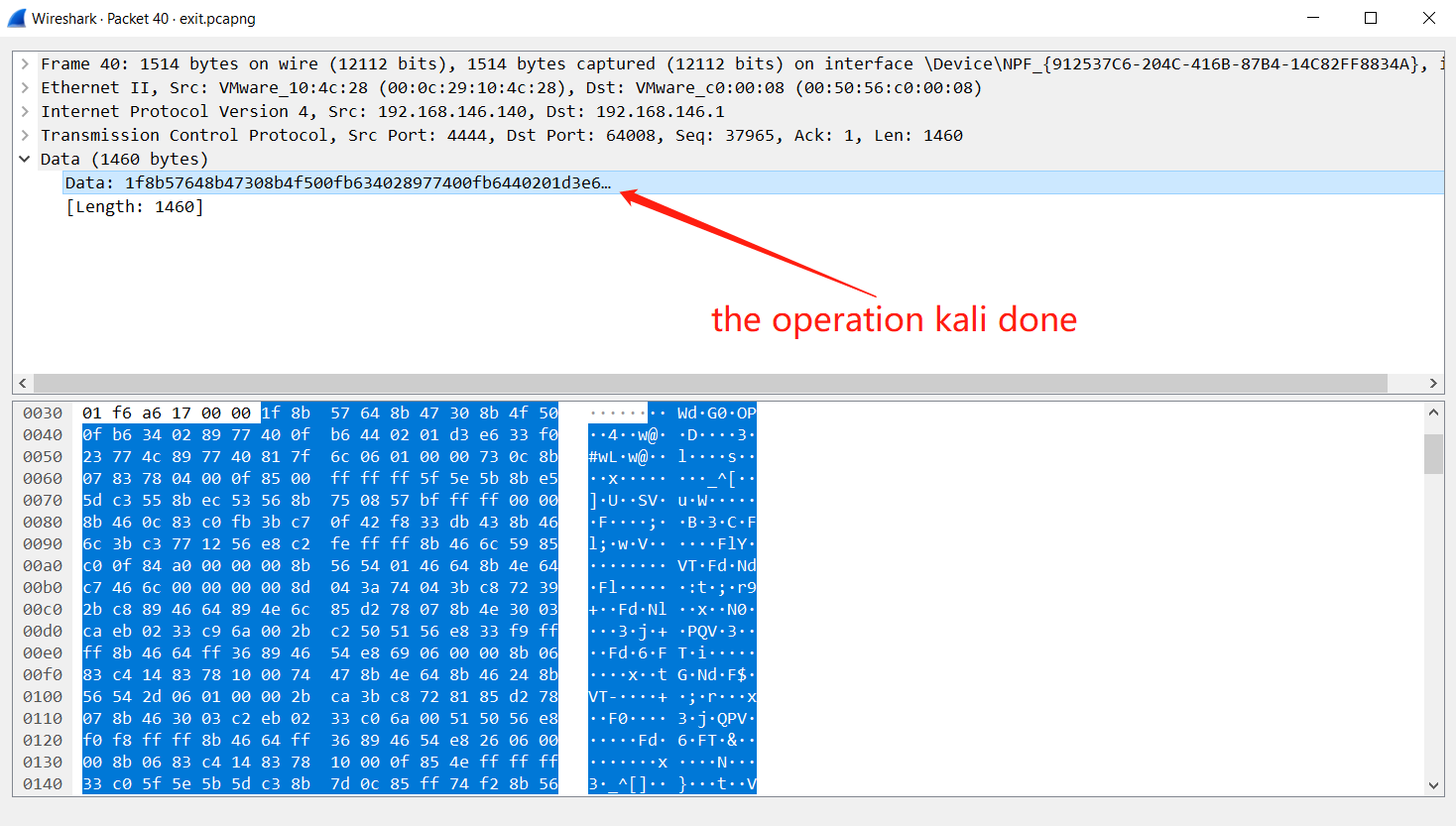
when kali connect to the target. the all operations are transform by tcp protocal. they all use ack as identification.
![]()
three.Last but not least
Q&A
Q:when i trying to use systracer to track down the backdoor.its weird to show these
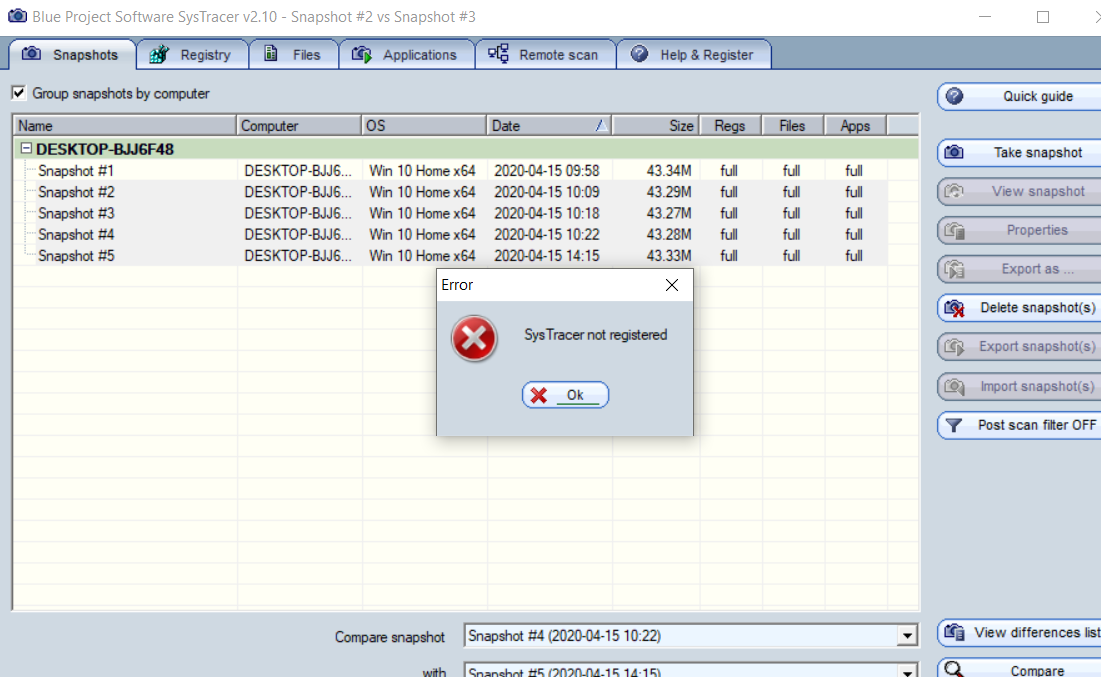
A:just restart this application.
Q:If you suspect malicious code on a host at work, but just guess, all you want to monitor what the system is doing every day. Please design what operations you want to monitor and what method to use for monitoring.
A:
- Process monitoring: Use Process Explorer
- View the network connection: use Windows task plan netstat
- View data packets: use wireshark to capture packets and analyze data flow
- View ports: use nmap to view suspicious ports
- Finally, you can also use the sysmon tool to configure the port, registry information, network connection and other information you want to monitor, and view it through the log file generated by it
Q:If you have determined that there is a problem with a program or process, what tools do you have to get further information about it?
A:
- Use the command tasklist to view the program process number
- Use SysTracer to take snapshots at break time, compare and analyze the captured snapshots, and analyze the differences between files, registry, applications, etc.
- Shell inspection using PEiD
- Use PE explorer to view the code information contained in the PE file header
- Use Process Monitor to analyze the program. Process Monitor is equivalent to Filemon + Regmon, where Filemon is used to monitor any file operation process in the system, and Regmon is used to monitor the registry read and write operation process
NOTE
by the end of this experiment. i just want to share some notes that i have learn from this experiment.Finishing this exp by myself,i know that hacker cant hack your computer silently,everything is recorded by computer.we just need know how to use tools to help us to track the hacker.maybe next time,when i am hacked,maybe i could use this way to locate the hacker!
meanwhile but no offense, trying write this blog by English just for interests. i highly recommend this plugin 达达划词翻译 to make a better reading.
just download in chrome.

much easier to read my blog with help !







 浙公网安备 33010602011771号
浙公网安备 33010602011771号