什么是ob混淆?
- OB 混淆和变量名混淆是常用的代码混淆技术。
- OB 混淆是指在代码中添加一些无用的代码和函数,以增加代码的复杂度和难以理解性,从而增加代码的保护性。
- 变量名混淆是指将变量名替换为无意义的字符串,增加代码的难度和防止代码的逆向分析。
ob混淆的特点
- 它会把常规的所有的
.操作处理成[]操作
- 把所有的字符串进行加密处理. 进行统一管理, 同时提供字符串解密函数
- 对数组进行打乱. 同时提供可以还原该数组的算法
实战
- 1、获取电影年度排行榜数据:https://www.xxx.com.cn/BoxOffice/BO/Year/index.html
- 2、经过分析,数据不在页面源代码;于是切换到Fetch/XHR,经过调试,发现返回的数据被加密了
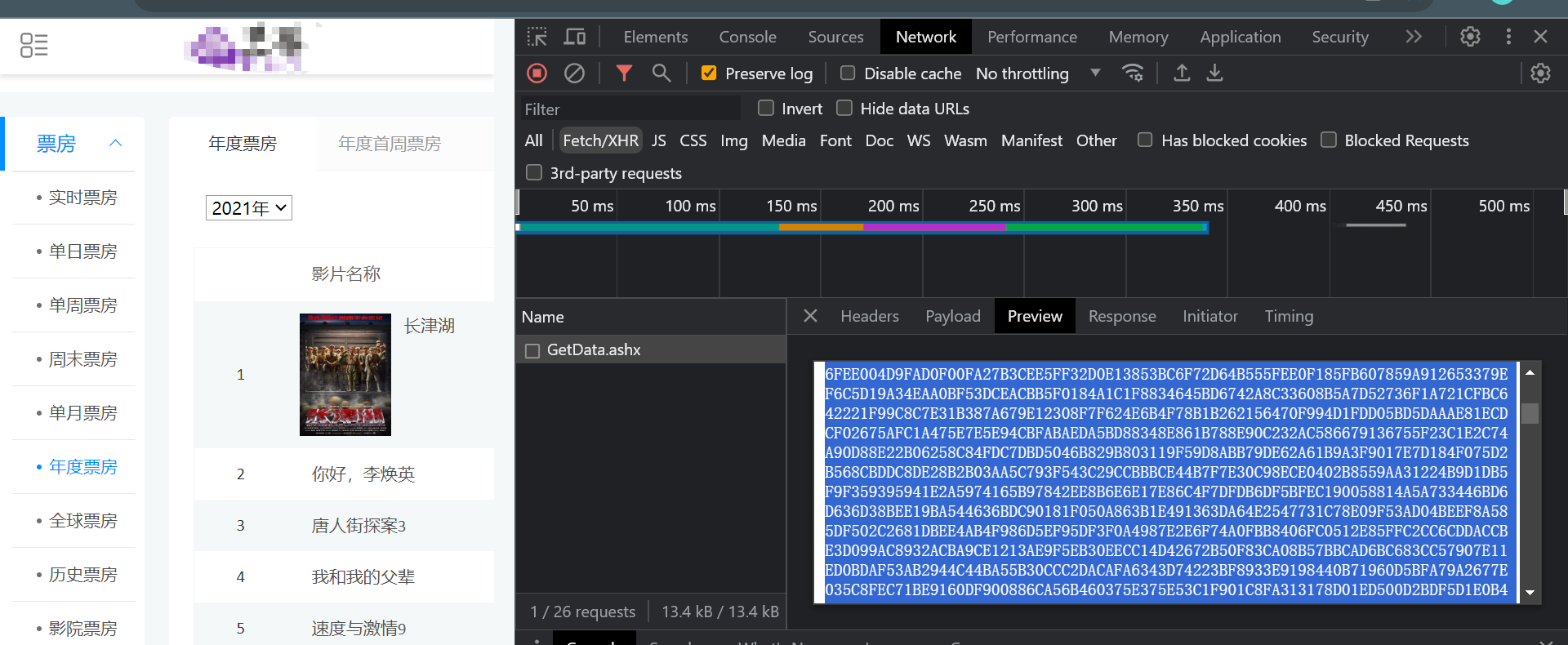
- 3、加密入口

- 4、经过分析,加密数据大概率是由:JSON.parse(JSON.parse(webInstace.shell(e)))解密
- 5、验证,console中将接口返回的加密数据,放到JSON.parse(webInstace.shell(e))中验证

- 6、注意:由于此处是三元表达式,我们在滑动鼠标显示参数值的时候会运行代码,最好在console中输入函数,进入加密函数
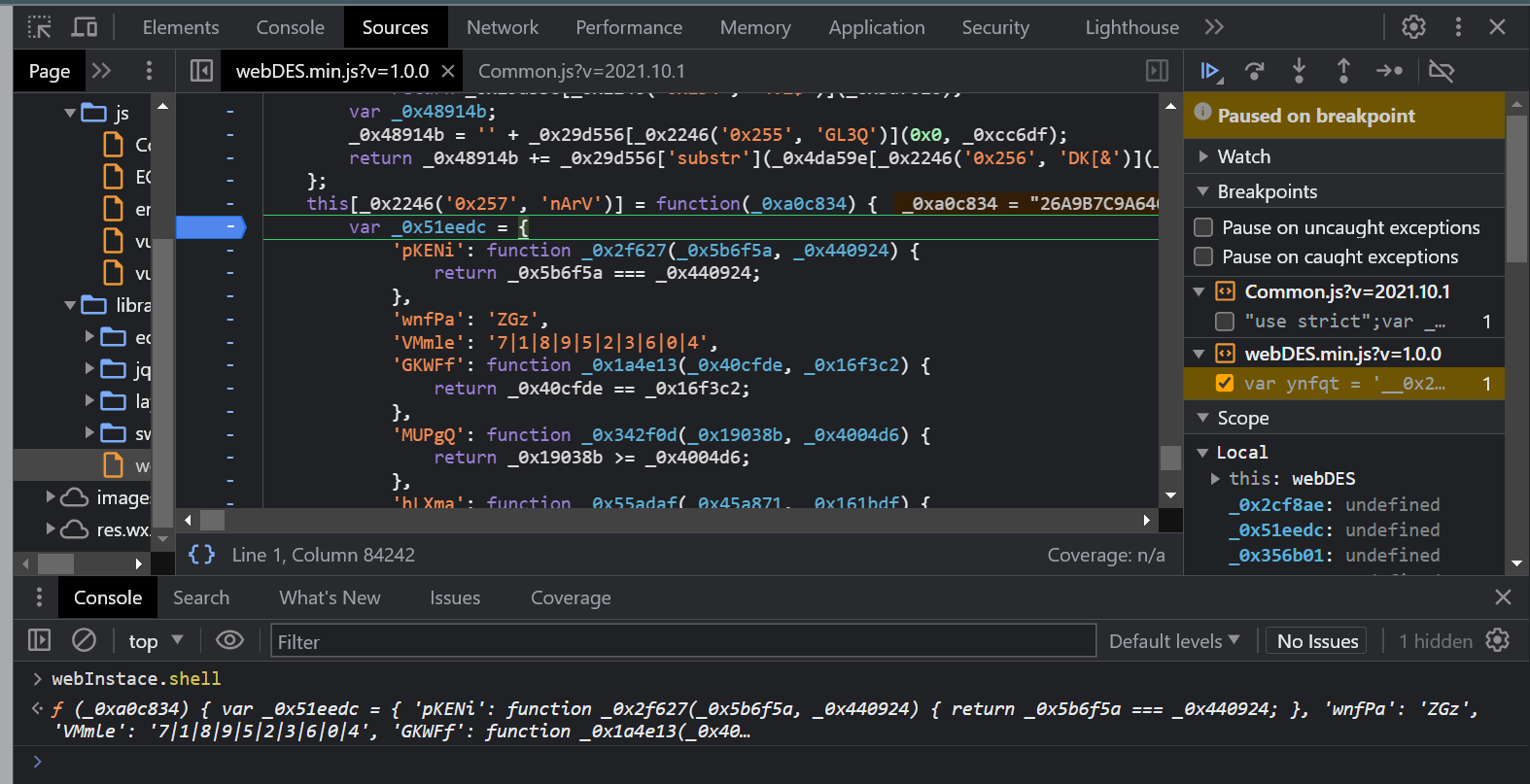
- 7、扣取此处代码
var _0x4da59e = {
'bUIIa': function _0x2a2af9(_0x779387, _0x4a4fec) {
return _0x779387 + _0x4a4fec;
}
};
var _0x9843d3 = function(_0x29d556, _0xcc6df, _0x3d7020) {
if (0x0 == _0xcc6df)
return _0x29d556[_0x2246('0x254', '4VZ$')](_0x3d7020);
var _0x48914b;
_0x48914b = '' + _0x29d556[_0x2246('0x255', 'GL3Q')](0x0, _0xcc6df);
return _0x48914b += _0x29d556['substr'](_0x4da59e[_0x2246('0x256', 'DK[&')](_0xcc6df, _0x3d7020));
};
this[_0x2246('0x257', 'nArV')] = function(_0xa0c834) {
var _0x51eedc = {
'pKENi': function _0x2f627(_0x5b6f5a, _0x440924) {
return _0x5b6f5a === _0x440924;
},
'wnfPa': 'ZGz',
'VMmle': '7|1|8|9|5|2|3|6|0|4',
'GKWFf': function _0x1a4e13(_0x40cfde, _0x16f3c2) {
return _0x40cfde == _0x16f3c2;
},
'MUPgQ': function _0x342f0d(_0x19038b, _0x4004d6) {
return _0x19038b >= _0x4004d6;
},
'hLXma': function _0x55adaf(_0x45a871, _0x161bdf) {
return _0x45a871 + _0x161bdf;
},
'JdOlO': function _0x13e00a(_0x5899a9, _0x4bb34d) {
return _0x5899a9 + _0x4bb34d;
},
'qrTpg': function _0x1198fb(_0x55b317, _0x22e1db, _0x1b091a) {
return _0x55b317(_0x22e1db, _0x1b091a);
},
'pdmMk': function _0xe2b022(_0x4af286, _0x4c2fd4) {
return _0x4af286 - _0x4c2fd4;
},
'xVKWW': function _0x1094a3(_0x5f3627, _0x2a0ac5, _0x3ad2e5) {
return _0x5f3627(_0x2a0ac5, _0x3ad2e5);
}
};
if (_0x51eedc[_0x2246('0x258', '@1Ws')](_0x2246('0x259', 'E&PI'), _0x51eedc['wnfPa'])) {
this['_append'](a);
return this[_0x2246('0x25a', 'GL3Q')]();
} else {
var _0x492a62 = _0x51eedc[_0x2246('0x25b', '&59Q')][_0x2246('0x25c', ')q#9')]('|')
, _0x356b01 = 0x0;
while (!![]) {
switch (_0x492a62[_0x356b01++]) {
case '0':
_0x554c90 = _grsa_JS[_0x2246('0x25d', 'E&PI')]['decrypt']({
'ciphertext': _grsa_JS['enc'][_0x2246('0x25e', 'sy^o')]['parse'](_0xa0c834)
}, _0x2cf8ae, {
'iv': _0x554c90,
'mode': _grsa_JS[_0x2246('0x16c', 'O^50')][_0x2246('0x25f', 'Who^')],
'padding': _grsa_JS[_0x2246('0x260', '7IfV')][_0x2246('0x261', 'E&PI')]
})[_0x2246('0x1c', 'yY#5')](_grsa_JS['enc'][_0x2246('0x262', ']2BX')]);
continue;
case '1':
if (_0x51eedc[_0x2246('0x263', 'Jsmq')](null, _0xa0c834) || _0x51eedc[_0x2246('0x264', '!2eC')](0x10, _0xa0c834['length']))
return _0xa0c834;
continue;
case '2':
_0xa0c834 = _0x9843d3(_0xa0c834, _0x2cf8ae, 0x8);
continue;
case '3':
_0x2cf8ae = _grsa_JS[_0x2246('0x265', 'RQ2o')][_0x2246('0x266', '3j7z')][_0x2246('0x267', 'RQ2o')](_0x554c90);
continue;
case '4':
return _0x554c90[_0x2246('0x268', 'cs*4')](0x0, _0x51eedc[_0x2246('0x269', 'MVsm')](_0x554c90[_0x2246('0x26a', '0J6f')]('}'), 0x1));
case '5':
_0x554c90 = _0xa0c834[_0x2246('0x26b', 'UwHa')](_0x2cf8ae, 0x8);
continue;
case '6':
_0x554c90 = _grsa_JS[_0x2246('0x26c', '4VZ$')]['Utf8']['parse'](_0x554c90);
continue;
case '7':
if (!navigator || !navigator[_0x2246('0x26d', '0I#o')])
return '';
continue;
case '8':
var _0x554c90 = _0x51eedc[_0x2246('0x26e', 'Yb4P')](_0x51eedc[_0x2246('0x26f', 'BQ5p')](parseInt, _0xa0c834[_0x51eedc[_0x2246('0x270', 'Z2VK')](_0xa0c834['length'], 0x1)], 0x10), 0x9)
, _0x2cf8ae = _0x51eedc[_0x2246('0x271', 'yY#5')](parseInt, _0xa0c834[_0x554c90], 0x10);
continue;
case '9':
_0xa0c834 = _0x9843d3(_0xa0c834, _0x554c90, 0x1);
continue;
}
break;
}
}
}
- 8、逐步解析
- 8.1:_0x51eedc,花指令--将一些简单表达式封装成了函数或者属性
- 8.2:将所有的_0x2246()函数替换

- 8.3:将所有的_0x51eedc[]还原
- 8.4:如果是函数,扣取源代码;如果是函数参数,使用简单的a、b等代替;最后的还原效果
var CryptoJS = require('crypto-js');
var func = function(a, b, c) {
if (0 == b)
return a['substr'](c);
var ret;
ret = '' + a['substr'](0, b);
return ret += a['substr'](b + c);
};
var shell = function(data) {
var a = parseInt(data[data['length'] -1], 16) + 9
, b = parseInt(data[a], 16);
data = func(data, a, 1);
a = data['substr'](b, 8);
data = func(data, b, 8);
b = CryptoJS['enc']['Utf8']['parse'](a);
a = CryptoJS['enc']['Utf8']['parse'](a);
a = CryptoJS['DES']['decrypt']({
'ciphertext': CryptoJS['enc']['Hex']['parse'](data)
}, b, {
'iv': a,
'mode': CryptoJS['mode']['ECB'],
'padding': CryptoJS['pad']['Pkcs7']
})['toString'](CryptoJS['enc']['Utf8']);
return a['substring'](0, a['lastIndexOf']('}')+1);
};
function fn(s) {
return JSON.parse(shell(s))
}
s = '接口中返回的加密数据'
console.log(shell(s));
- 9、试跑以上代码
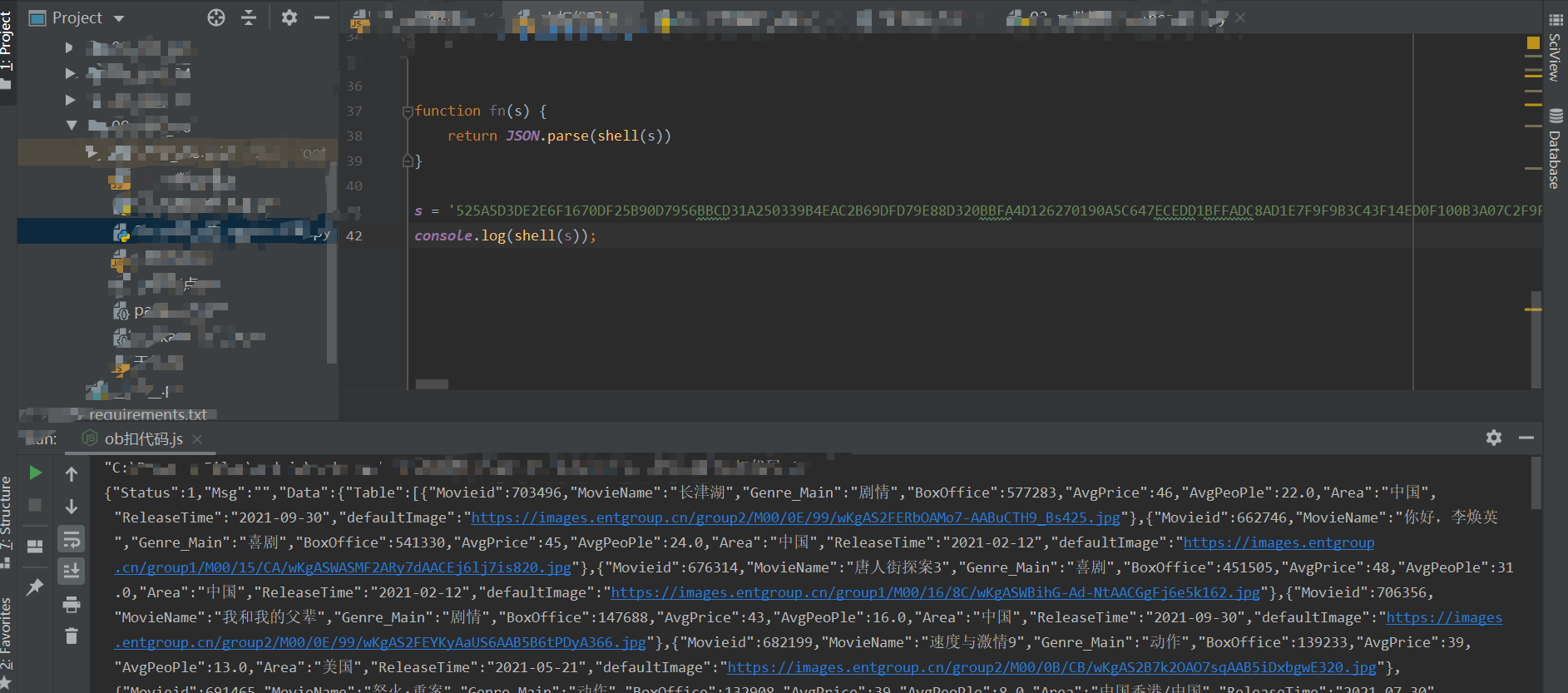
- 10、支持,解密过程全部完整
完整代码实现
import subprocess
from functools import partial
subprocess.Popen = partial(subprocess.Popen, encoding='utf-8')
import execjs
import requests
session = requests.session()
session.headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36"
}
f = open("01_en数据库.js", mode="r", encoding="utf-8")
js = execjs.compile(f.read())
f.close()
def get_movie_info_by_year(year):
url = "https://www.xxxx.com.cn/API/GetData.ashx"
data = {
"year": year,
"MethodName": "BoxOffice_GetYearInfoData",
}
resp = session.post(url, data=data)
return js.call("fn", resp.text)
if __name__ == '__main__':
for i in range(2008, 2024):
print(get_movie_info_by_year(i))
from Crypto.Cipher import DES
from Crypto.Util.Padding import unpad
import binascii
import json
import requests
"""
var func = function(a, b, c) {
if (0x0 == b)
return a['substr'](c);
var ret;
ret = '' + a['substr'](0x0, b);
return ret += a['substr']((b+ c));
};
"""
def func(a, b, c):
if 0 == b:
return a[c:]
ret = str(a[0: b])
ret += a[b + c:]
return ret
def shell(data):
"""
if ((null == data) || 16 >= data['length'])
return data;
var a = parseInt(data[data['length']- 1], 16) + 9;
var b = parseInt(data[a], 16);
data = func(data, a, 1);
a = data['substr'](b, 8);
data = func(data, b, 8);
"""
if data is None or len(data) <= 16:
return data
a = int(data[-1], 16) + 9
b = int(data[a], 16)
data = func(data, a, 1)
a = data[b: b+8]
data = func(data, b, 8)
des = DES.new(key=a.encode("utf-8"), mode=DES.MODE_ECB)
ming_bs = des.decrypt(binascii.a2b_hex(data))
ming_bs = unpad(ming_bs, 8)
s = ming_bs.decode("utf-8")
return s[:s.rindex("}")+1]
def fn(data):
ret = shell(data)
return json.loads(ret)
def get_movie_info_by_year(year):
for i in range(10):
try:
url = "https://www.xxxx.com.cn/API/GetData.ashx"
data = {
"year": year,
"MethodName": "BoxOffice_GetYearInfoData",
}
resp = session.post(url, data=data)
return fn(resp.text)
except Exception as e:
print("本次解密有问题")
if __name__ == '__main__':
session = requests.session()
session.headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36"
}
for i in range(2008, 2024):
print(get_movie_info_by_year(i))
- 3、注意点
- 由于hex字符串在python与javascript中会稍有不同,例如:0123df在python总可能显示为:123df,会将第一位0去掉,所有需要在解析时加入循环与try处理












【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· AI编程工具终极对决:字节Trae VS Cursor,谁才是开发者新宠?
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
2022-08-27 【pytest】plugins插件开发