kubernetes之Ingress发布应用实现rewrite重写并配置HTTPS;(二)
1.使用Ingress发布应用准备;
后续内容会更新在个人站点: https.malusspectabilis.top
1.1准备Tomcat应用的配置文件
root@ks-master01-10:~/ingress-test# cat tomcat-deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: tomcat-test
namespace: default
spec:
replicas: 1
selector:
matchLabels:
app: tomcat
template:
metadata:
labels:
app: tomcat
spec:
containers:
- name: java-test
image: tomcat:9.0.63
ports:
- containerPort: 80
lifecycle:
postStart:
exec:
command:
- "/bin/bash"
- "-c"
- "cp -rf /usr/local/tomcat/webapps.dist/* /usr/local/tomcat/webapps/"
root@ks-master01-10:~/ingress-test# kubectl apply -f tomcat-deployment.yaml
1.1.2查看Pod是否正常;
root@ks-master01-10:~/ingress-test# kubectl get pods -l app=tomcat
NAME READY STATUS RESTARTS AGE
tomcat-test-5fb68b5569-hwf4b 1/1 Running 0 25m
1.2准备Tomcat的Service
root@ks-master01-10:~/ingress-test# cat tomcat-svc.yaml
apiVersion: v1
kind: Service
metadata:
name: tomcat-svc
spec:
type: ClusterIP
selector:
app: tomcat
ports:
- port: 8080
targetPort: 8080
root@ks-master01-10:~/ingress-test# kubectl apply -f tomcat-svc.yaml
service/tomcat-svc created
1.2.1查看Service
root@ks-master01-10:~/ingress-test# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
tomcat-svc ClusterIP 10.96.123.199 <none> 8080/TCP 4s
1.2.2describe查看可以看见后端就一个端点正好是该Pod的IP地址
root@ks-master01-10:~/ingress-test# kubectl describe svc tomcat-svc
Name: tomcat-svc
Namespace: default
Labels: <none>
Annotations: <none>
Selector: app=tomcat
Type: ClusterIP
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.96.123.199
IPs: 10.96.123.199
Port: <unset> 8080/TCP
TargetPort: 8080/TCP
Endpoints: 192.168.2.25:8080
Session Affinity: None
Events: <none>
1.3准备应用的Ingress
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: tomcat-ingress-test
annotations: # 注解
nginx.ingress.kubernetes.io/rewrite-target: /$2 # 重写
spec:
ingressClassName: "nginx" # 控制器选择为Nginx
rules:
- host: haitangone.tomcat.net
http:
paths:
- path: /java(/|$)(.*)
pathType: Prefix
backend:
service:
name: tomcat-svc
port:
number: 8080
root@ks-master01-10:~/ingress-test# kubectl apply -f tomcat-ingress.yaml
ingress.networking.k8s.io/tomcat-ingress-test created
1.3.1查看Ingress资源
root@ks-master01-10:~/ingress-test# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
tomcat-ingress-test nginx haitangone.tomcat.net xx.xx.xx.xx 80 34s
1.3.2确保已经关联到Service
Default backend: default-http-backend:80 (<error: endpoints "default-http-backend" not found>)
Rules:
Host Path Backends
---- ---- --------
haitang.tomcat.net
/java(/|$)(.*) tomcat-svc:8080 (192.168.2.25:8080)
Annotations: nginx.ingress.kubernetes.io/rewrite-target: /$2
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Sync 104s (x2 over 104s) nginx-ingress-controller Scheduled for sync
Normal Sync 104s (x2 over 104s) nginx-ingress-controller Scheduled for sync
1.4准备Tomcat的TLS资源
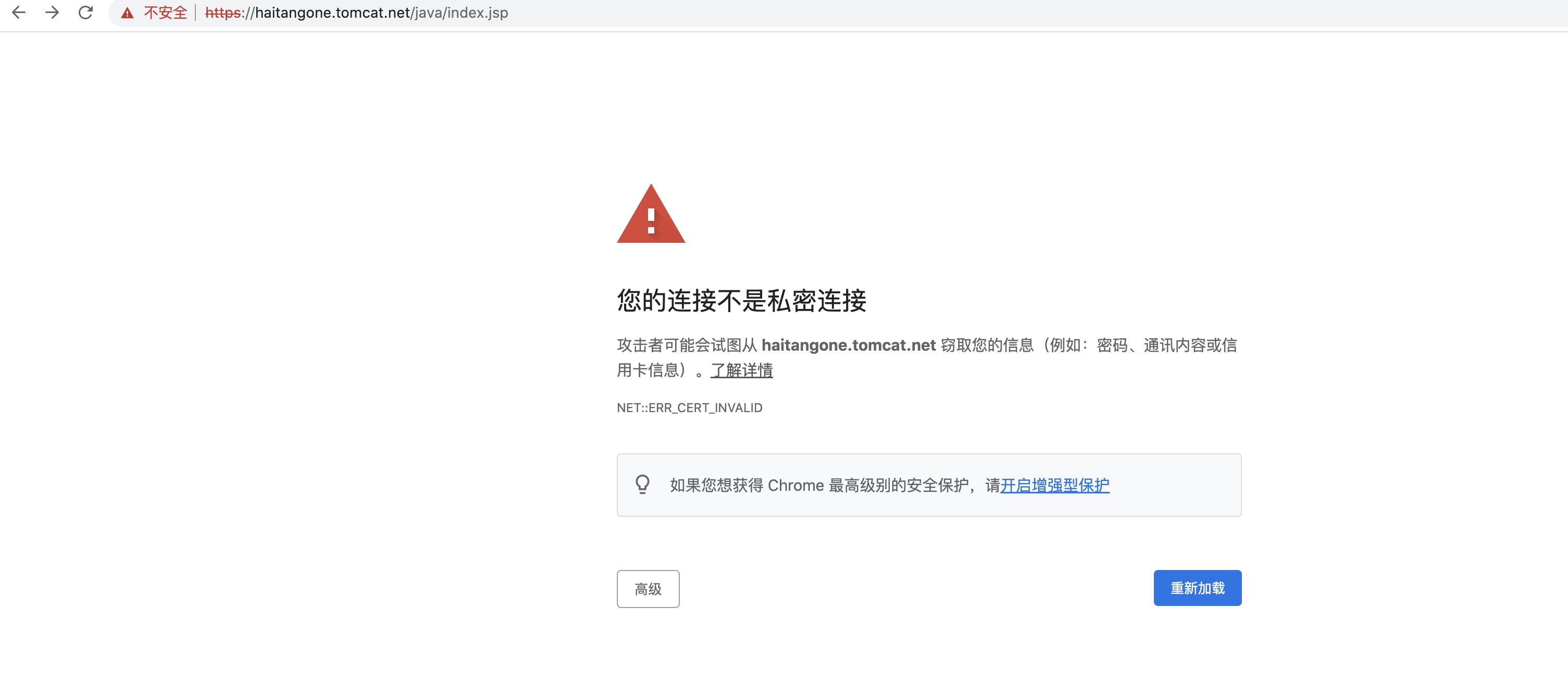
- 在Ingress控制器上配置HTTPS主机时,不能直接使用私钥和证书文件,而是要使用Secret资源对象来传递相关的数据;
- 一般来说,如果有基于HTTPS通信的需求,那么它应该由外部的负载均衡器(external lb)予以实现,并在SSL会话卸载后将其访问请求转发到Ingress控制器。不过,如果外部负载均衡工作于传输层而不是工作于应用层的反向代理服务器,或者存在直接通过Ingress控制器接受客户端的请求的需求,又期望他们能够提供HTTPS服务时,就应该配置TLS类型的Ingress资源;
- 将此类服务公开发布到互联网时,HTTPS服务用到的证书由公信CA签署并颁发,用户遵循其相应流程准备好相关的证书即可。如果出于测试或内部使用,那么也可以选择自制私有证书。openssl工具程序是用于生成自签证书的常用工具,那么使用它生成用于测试的私钥和自签证书;
root@ks-master01-10:~/ingress-test# mkdir ssl
root@ks-master01-10:~/ingress-test# cd ssl/
root@ks-master01-10:~/ingress-test/ssl# openssl genrsa -out tls.key 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
............................................................................................................................................................+++++
.......................+++++
e is 65537 (0x010001)
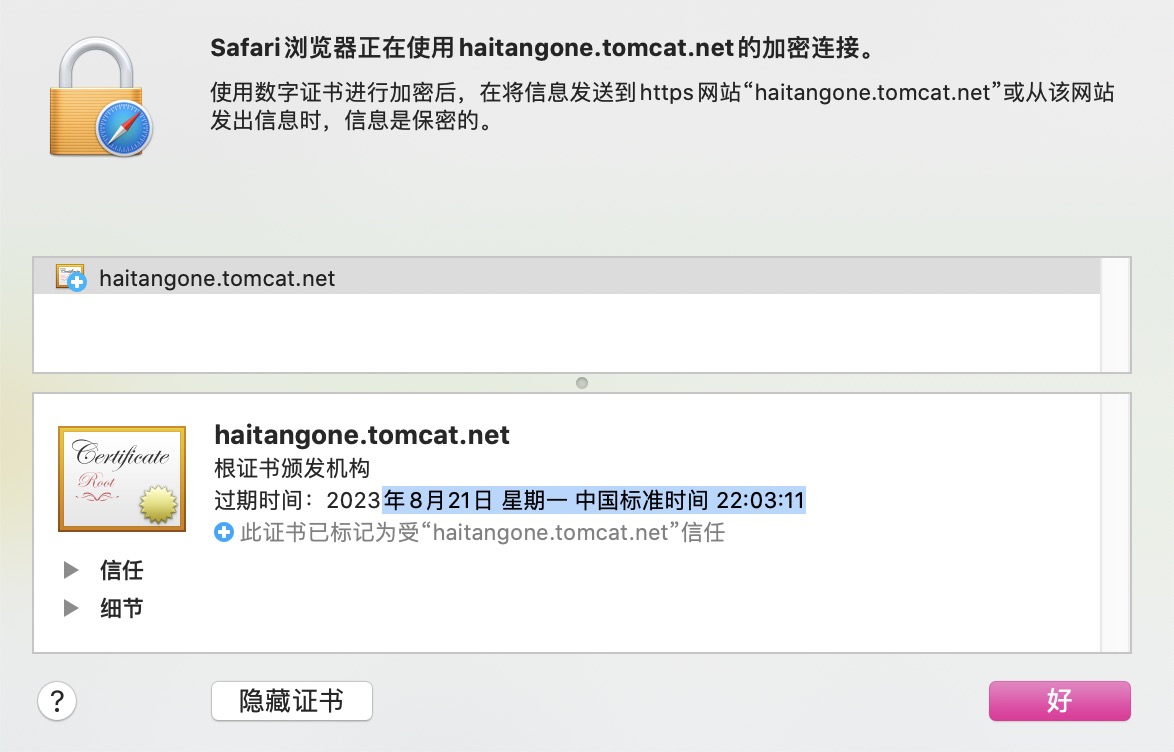
root@ks-master01-10:~# openssl req -new -x509 -key tls.key -out tls.cert -days 360 -subj /CN=haitangone.tomcat.net
1.5创建Secrets
根据私钥和证书文件生成配置TLS Ingress的Secret资源,在创建Ingress规则时由其将用到的Secret资源的信息注入Ingress控制器的Pod中,用于为配置的HTTPS虚拟主机提供相应的私钥和证书。下面会创建一个TLS类型名为tomcat-tls-test的Secret资源:
TLS Secret中包含的文件必须以tls.crt作为其键名,私钥文件必须以tls.key为键名,因此上面生成的私钥文件和证书文件名将直接保存为键名形式,便于后面创建Secret对象时直接作为键名引用;
root@ks-master01-10:~/ingress-test/ssl# kubectl create secret tls tomcat-tls-test --cert=tls.cert --key=tls.key
secret/tomcat-tls-test created
1.5.1查看Secret
这里的TYPE类型应该为"kubernetes.io/tls"
root@ks-master01-10:~/ingress-test/ssl# kubectl get secret
kNAME TYPE DATA AGE
tomcat-tls-test kubernetes.io/tls 2 50s
root@ks-master01-10:~/ingress-test/ssl# kubectl describe secret tomcat-tls-test
Name: tomcat-tls-test
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/tls
Data
====
tls.crt: 1147 bytes
tls.key: 1675 bytes
1.6Ingress引用Secret资源实现HTTPS
tls对象由两个内嵌字段组成,仅在定义TLS主机的转发规则时才需要定义此类对象。
- hosts: 包含于使用TLS证书之内的主机名称字符串列表,因此,此处使用的主机名必须匹配tlsSecret中的名称;
- secretName: 用于引用SSL会话的secret对象名称,在基于SNI实现多主机路由的场景中,此字段为可选;
- 目前来说,Ingress资源仅支持单TLS端口,并且还会卸载TLS会话,在Ingress资源中引用此Secret即可让Ingress控制器加载并配置为HTTPS服务;
编辑Ingress资源,引入Secret资源
root@ks-master01-10:~/ingress-test# cat tomcat-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: tomcat-ingress-test
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /$2 # 重写
spec:
ingressClassName: "nginx" # 这里选择为nginx
rules:
- host: haitangone.tomcat.net
http:
paths:
- path: /java(/|$)(.*)
pathType: Prefix
backend:
service:
name: tomcat-svc
port:
number: 8080
tls: # tls资源
- hosts:
- haitangone.tomcat.net
secretName: tomcat-tls-test
root@ks-master01-10:~/ingress-test# kubectl apply -f tomcat-ingress.yaml
ingress.networking.k8s.io/tomcat-ingress-test configured
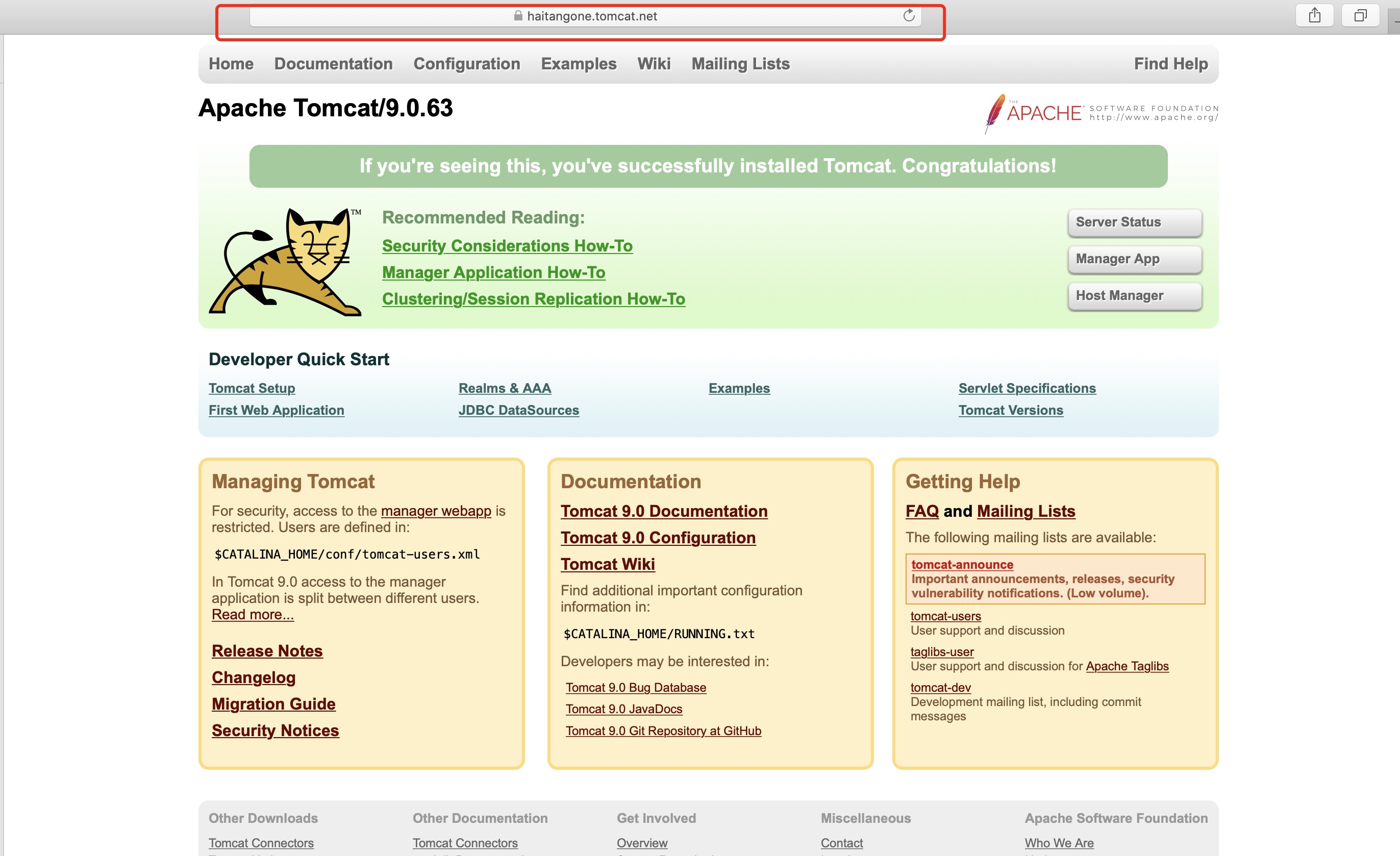
1.7测试是否可以访问;
作者:梨花海棠
出处:https://www.cnblogs.com/xunweidezui/p/16629250.html
版权:本作品采用「署名-非商业性使用-相同方式共享 4.0 国际」许可协议进行许可。



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 上周热点回顾(3.3-3.9)
· AI 智能体引爆开源社区「GitHub 热点速览」