kubernetes之部署Dashboard(一)
1.什么是Dashboard?
Dashboard是kubernetes的Web GUI,可用于在kubernetes集群上部署容器化应用,应用排障、管理集群本身及其附加的资源等。它常被管理员用于集群及应用速览,创建或修改单个资源(deployment、jobs和daemonset)以及扩展deployment、启动滚动更新、重启pod或使用部署向导一个新应用等;
这里需注意一点是Dashboard依赖于Metrics-Server完成指标数据的采集和可视化;
官方地址: https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/
GitHub地址: https://github.com/kubernetes/dashboard
2.安装Dashboard
2.1下载Dashboard的yaml文件到本地
root@ks-master01-10:~# wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.6.1/aio/deploy/recommended.yaml
2.2修改访问类型为NodePort
修改完Service的类型之后执行apply
root@ks-master01-10:~# vim recommended.yaml
root@ks-master01-10:~# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
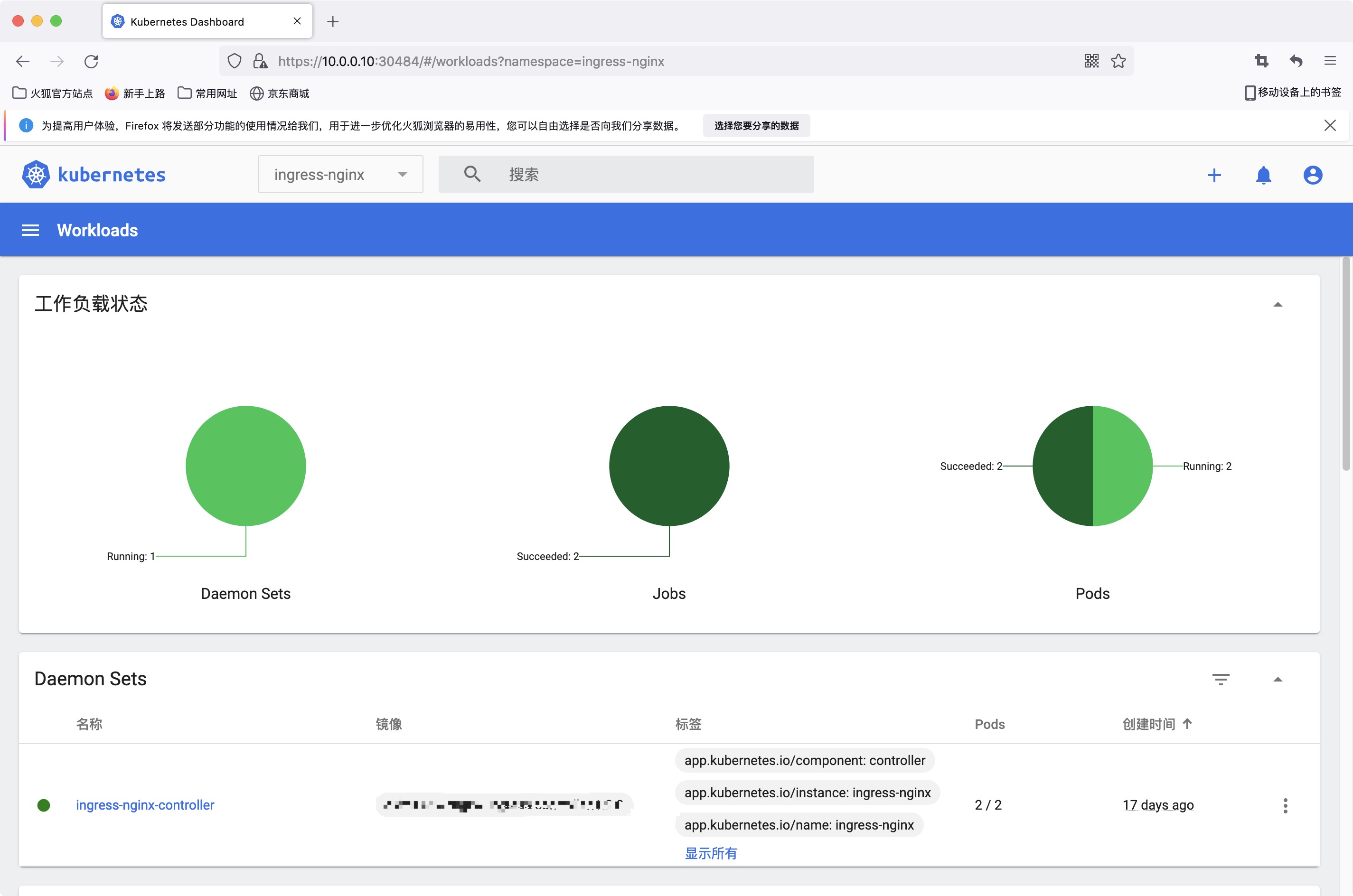
2.3查看Pod与Service
运行正常。
root@ks-master01-10:~# kubectl get pods,service -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-c45b7869d-czzgh 1/1 Running 0 3m19s
pod/kubernetes-dashboard-79b5779bf4-bcxcg 1/1 Running 0 3m19s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP XX.XX.XXX.xxx <none> 8000/TCP 3m19s
service/kubernetes-dashboard NodePort XX.XX.XXX.xxx <none> 443:30484/TCP 3m19s
2.4浏览器访问;
3.创建授权
安装好了,没有账号还是无法访问的。所以要授权;
3.1基于token认证与授权;
3.1.1创建ServiceAccount
创建ServiceAccount然后通过dashboard的token进行验证。
root@ks-master01-10:~# kubectl create serviceaccount haitang-ui -n kubernetes-dashboard
serviceaccount/haitang-ui created
3.1.2绑定用户
将sa账户通过clusterrolebinding绑定到cluster-admin集群角色上,以便拥有集群管理员权限;
root@ks-master01-10:~# kubectl create clusterrolebinding haitang-ui --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:haitang-ui
clusterrolebinding.rbac.authorization.k8s.io/haitang-ui created
3.1.3查看secret
获取ServiceAccount对应用户的token信息
root@ks-master01-10:~# kubectl describe sa haitang-ui -n kubernetes-dashboard
Name: haitang-ui
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: haitang-ui-token-849zp
Tokens: haitang-ui-token-849zp
Events: <none>
root@ks-master01-10:~# kubectl describe secrets haitang-ui-token-849zp -n kubernetes-dashboard
Name: haitang-ui-token-849zp
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: haitang-ui
kubernetes.io/service-account.uid: 5b0ff847-7a31-40c9-a889-5ff25c74a330
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1099 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InZ3WENRaC1uMVFwUmZsMFNjYzZZS2RFbkNWcTdQZWs5UXB5Uk43WUZLNHMifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJoYWl0YW5nLXVpLXRva2VuLTg0OXpwIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImhhaXRhbmctdWkiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI1YjBmZjg0Ny03YTMxLTQwYzktYTg4OS01ZmYyNWM3NGEzMzAiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6aGFpdGFuZy11aSJ9.TyPdqQggL5VRC-768K76AYi6BcAs3DRPcom-mGzTSSPDv-oG9-pYPOFPbjiGLJnvm7GrYHytncir9tY5A4CReEBMoapbbORIlBwH_yLJ5tKRUUZt7HELeIONlvJzF9s8luR4DkIPkTP_7Naj0GXL8pguio-O6mNHPIeQI2E1Y_qLHtI-Pzme66gi1qWGR1sMknitLMCv6hQlzFeOQ7Jy_j_-xB5pCKsSxoS0KtHn_6qhXgHnedXFr4-ySK1eU5jY27bImljGA2IICzbJ9tnxvggaeegbIO741TA-_pf99Sl-Z82xwIxrQmSKFDYYKnrr62LvQsLBeSesq-63GQeEBQ
3.1.4访问即可;
作者:梨花海棠
出处:https://www.cnblogs.com/xunweidezui/p/14458930.html
版权:本作品采用「署名-非商业性使用-相同方式共享 4.0 国际」许可协议进行许可。



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· winform 绘制太阳,地球,月球 运作规律
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 上周热点回顾(3.3-3.9)
· AI 智能体引爆开源社区「GitHub 热点速览」