Kali Linux Web 渗透测试— 第十二课-websploit
文/玄魂

目录
Kali Linux Web 渗透测试— 第十二课-websploit............................................... 1
Websploit 简介........................................................................................... 2
主要功能....................................................................................................... 2
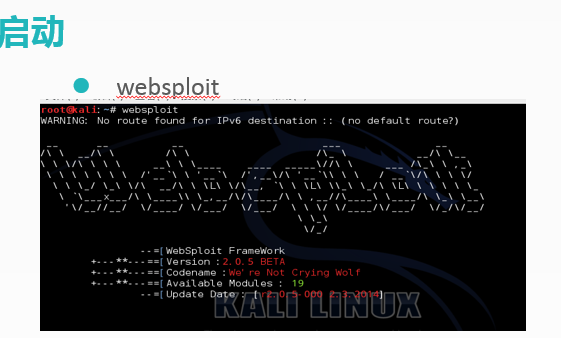
启动............................................................................................................... 3
show modules................................................................................................ 4
基本使用流程............................................................................................... 4
demo1-web/pma 模块使用......................................................................... 5
demo2-exploit/java applet 示例.................................................................. 5
demo-3 network/ mitm................................................................................. 5
教程地址:http://edu.51cto.com/course/course_id-1887.html
l 一个综合性的,高级的中间人漏洞攻击框架。
l 由python编写的开源项目。
l 源代码:https://github.com/websploit/websploit
l 项目地址:http://sourceforge.net/projects/websploit/
l # [+]Autopwn - Used From Metasploit For Scan and Exploit Target Service
l # [+]Browser AutoPWN - Exploit Victim Browser
l # [+]wmap - Scan,Crawler Target Used From Metasploit wmap plugin
l # [+]format infector - inject reverse & bind payload into file format
l # [+]MLITM,XSS Phishing - Man Left In The Middle Attack
l # [+]MITM - Man In The Middle Attack
l # [+]USB Infection Attack - Create Executable Backdoor For Windows
l # [+]Java Applet Attack Vector
l # [+]ARP DOS - ARP Cache Denial Of Service Attack With Random MAC
l # [+]Directory Scanner - Scan Target Directorys
l # [+]Apache US - Scan Apache users
l # [+]PHPMyAdmin - Scan PHPMyAdmin Login Page
l # [+]Web Killer - Using From The TCPKill For Down Your WebSite On Network
l # [+]Fake AP - Fake Access Point
l # [+]FakeUpdate - Fake update attack
l # [+]Wifi Jammer - Wifi Jammer Attack
l # [+]Wifi Dos - Wifi Dos RQ Attack
l # [+]Wifi Mass De-authentication attack
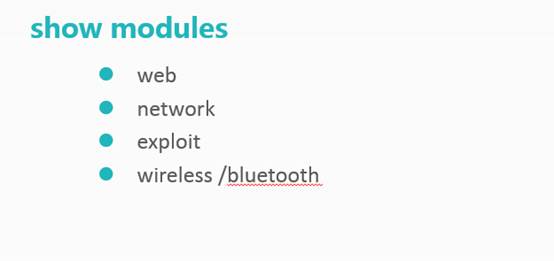
l web
l network
l exploit
l wireless /bluetooth
l 1.确定攻击目标
l 2.查找可用模块
l 3.use 使用模块
l 4. show options 显示配置项
l 5.set 配置选项
l 6.run 开始执行
l 7.如果成功,权限获取

l 中间人攻击

ps:对此文章感兴趣的读者,可以加qq群:Hacking:303242737;Hacking-2群:147098303;Hacking-3群:31371755;hacking-4群:201891680;Hacking-5群:316885176

作者:玄魂
出处:http://www.cnblogs.com/xuanhun/
原文链接:http://www.cnblogs.com/xuanhun/
更多内容,请访问我的个人站点 对编程,安全感兴趣的,加qq群:hacking-1群:303242737,hacking-2群:147098303,nw.js,electron交流群 313717550。
本文版权归作者和博客园共有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文连接,否则保留追究法律责任的权利。
关注我:





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律
2008-11-07 Web安全实践(7)web服务器简介及常用攻击软件