ipsec - ESP
Protocol: Encapsulated Security Payload (ESP)
ESP is the wire-level protocol designed to secure communication by encrypting the encapsulated data and can allow for authentication.
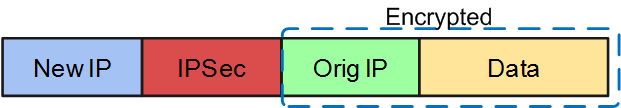
ESP being used in tunnel mode allows for encryption of the full packet. To an entity viewing this traffic externally, the only clear-text data in the packets are the new IP header and the ESP header:
Encapsulating Security Payload (ESP) is a member of the Internet Protocol Security (IPsec) set of protocols that encrypt and authenticate the packets of data between computers using a Virtual Private Network (VPN).
Security Authentication Header (AH) is another IPsec member protocol. ESP and AH can operate between hosts and between networks. The can also operate in two modes: the less-secure Transport Mode that encrypts the data packet, for use between two workstations that are running a VPN client; and Tunnel Mode, which is more secure. Tunnel Mode encrypts the whole packet including header info and source, and is used between networks.
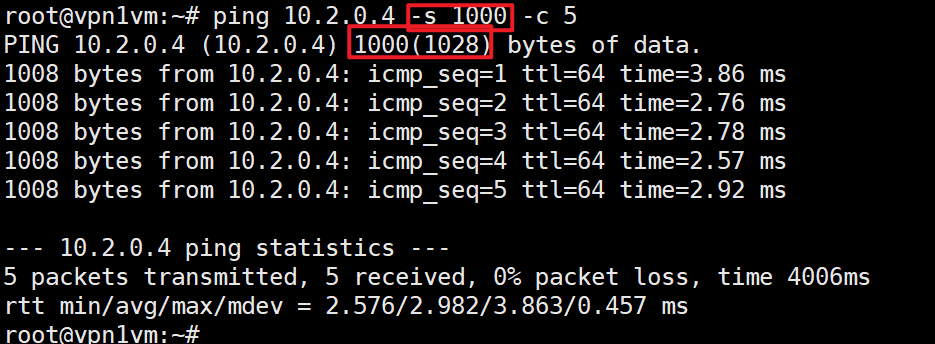
ping test:
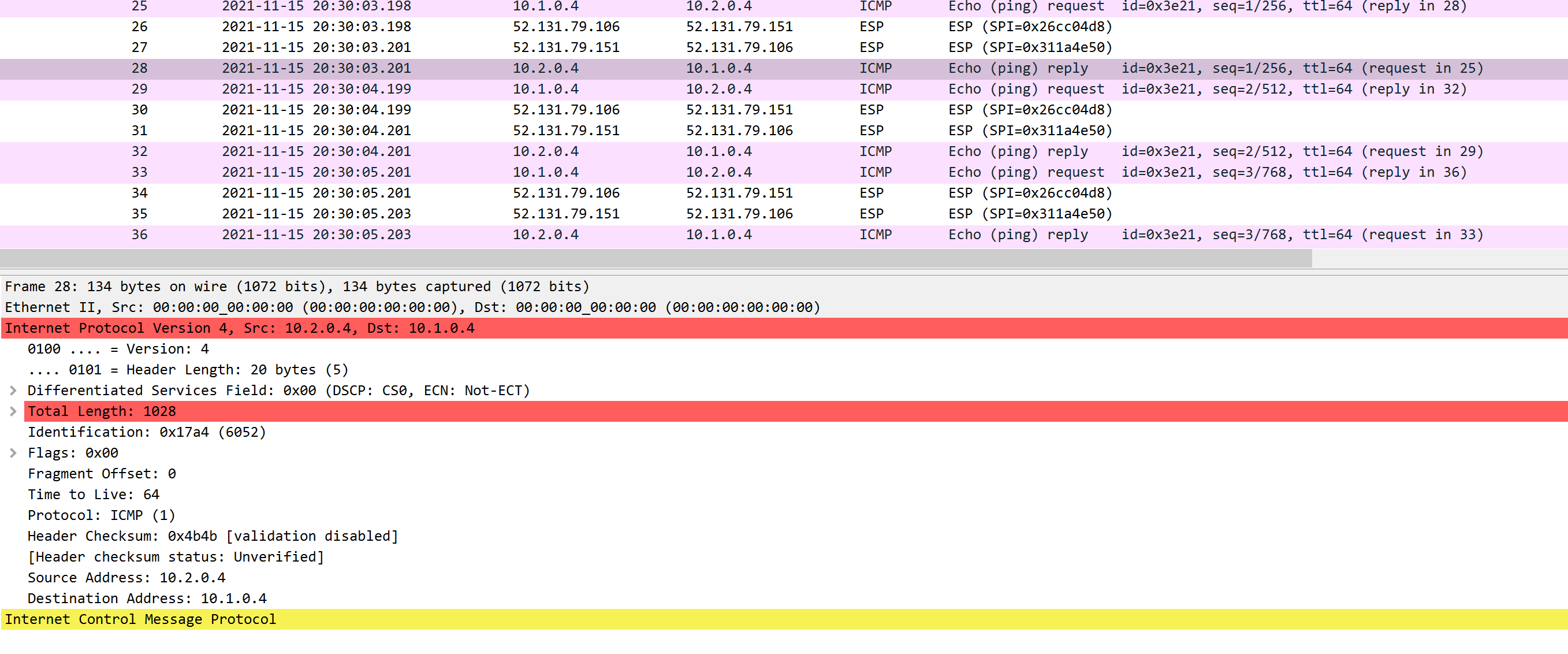
ESP (Encapsulating Security Payload) Protocol
ESP is the more popular choice of the two since it allows you to encrypt IP traffic. We can use it in transport or tunnel mode
Transport Mode
When we use transport mode, we use the original IP header and insert an ESP header. Here’s what it looks like:

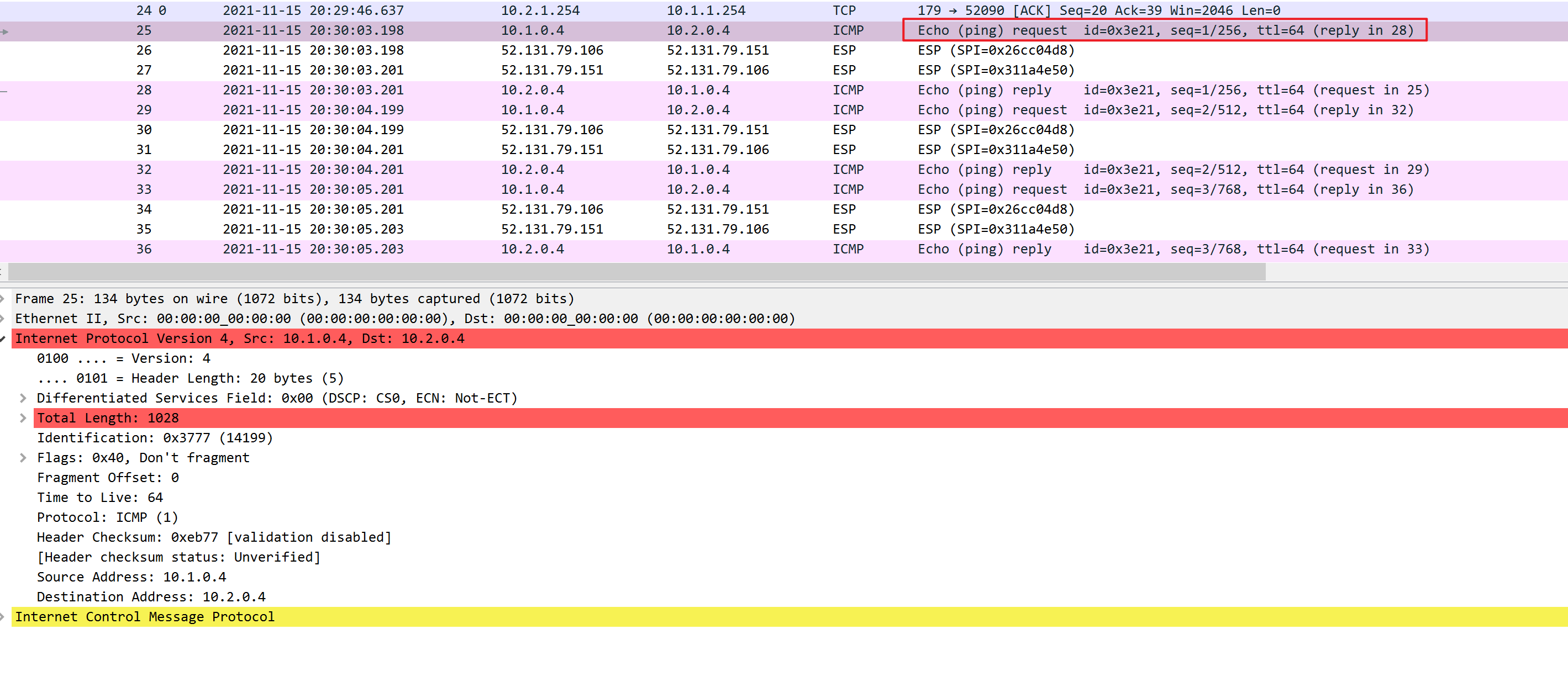
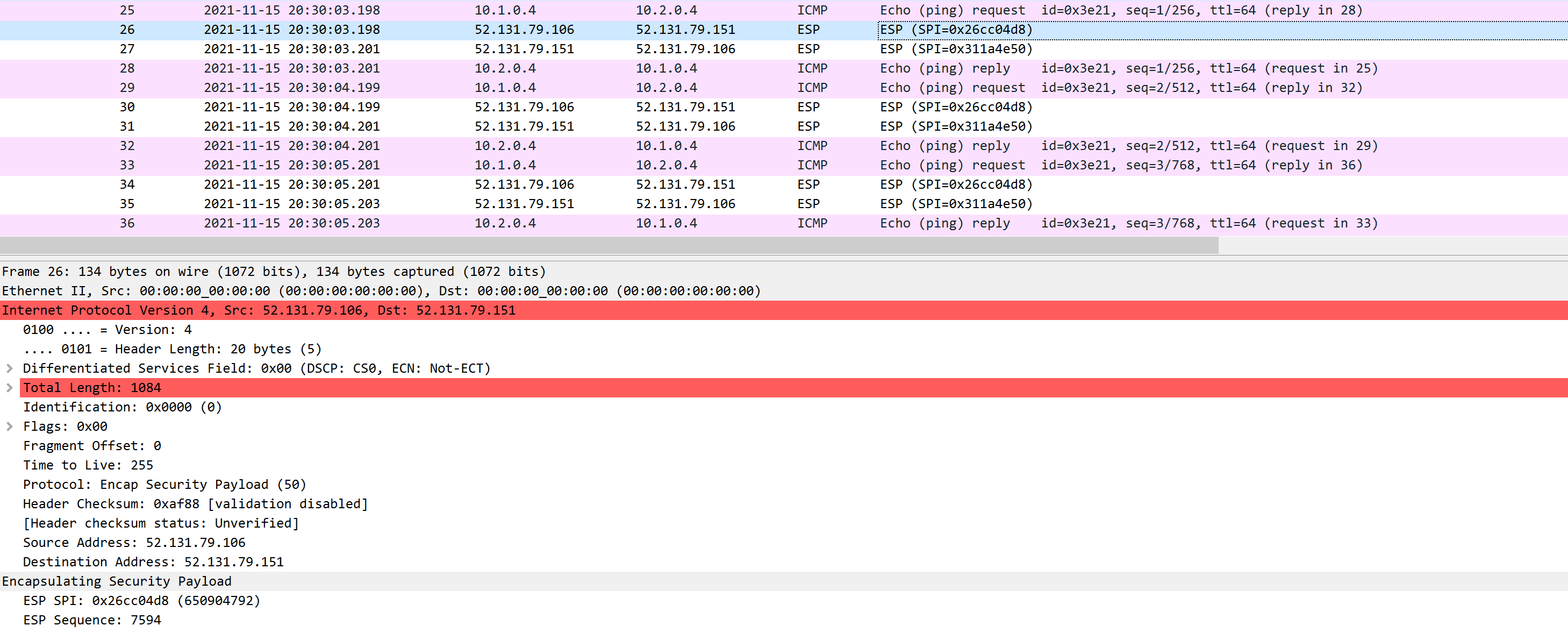
Above you can see that we add an ESP header and trailer. Our transport layer (TCP for example) and payload will be encrypted. It also offers authentication but unlike AH, it’s not for the entire IP packet. Here’s what it looks like in wireshark:
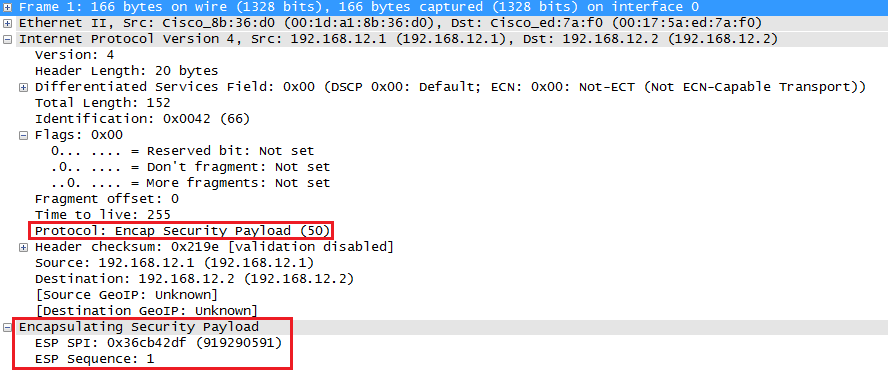
Above you can see the original IP packet and that we are using ESP. The IP header is in cleartext but everything else is encrypted.
Tunnel Mode
This is where we use a new IP header which is useful for site-to-site VPNs:
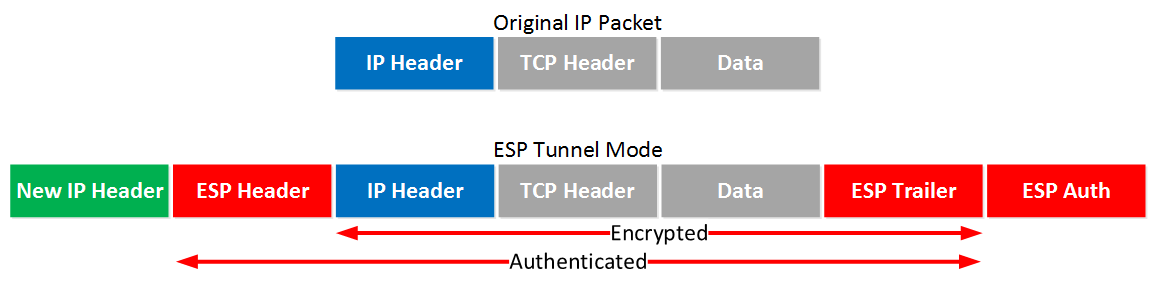
It’s similar to transport mode but we add a new header. The original IP header is now also encrypted.
Here’s what it looks like in wireshark:
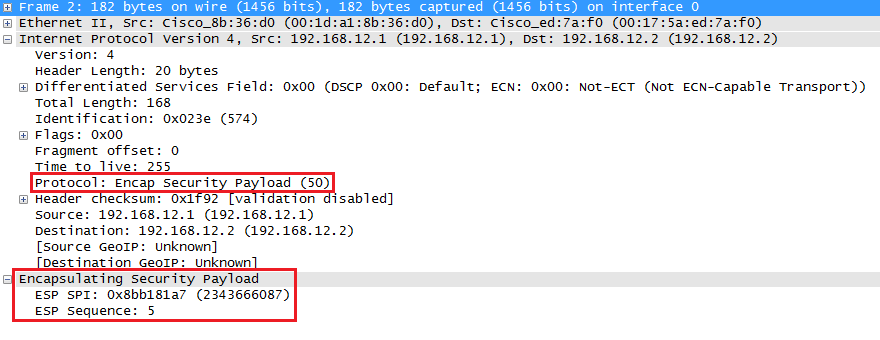
The output of the capture is above is similar to what you have seen in transport mode. The only difference is that this is a new IP header, you don’t get to see the original IP header.
AH and ESP
This one confuses a lot of people, it’s possible to use AH and ESP at the same time. Let’s check it out!
Transport Mode
Let’s start with transport mode, here’s what the IP packet will look like:
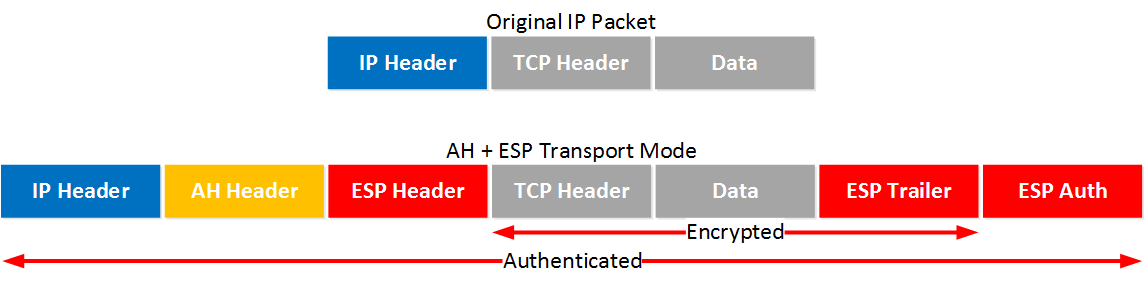
With transport mode we will use the original IP header, followed by an AH and ESP header. The transport layer, payload and ESP trailer will be encrypted.
Because we also use AH, the entire IP packet is authenticated. Here’s what it looks like in wireshark:
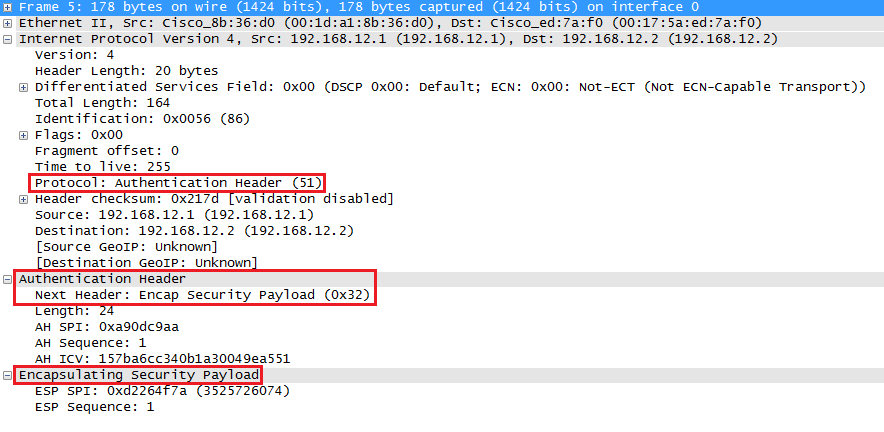
Above you can see the original IP packet, the AH header and the ESP header.
Tunnel Mode
What about tunnel mode? We will add a new IP header:
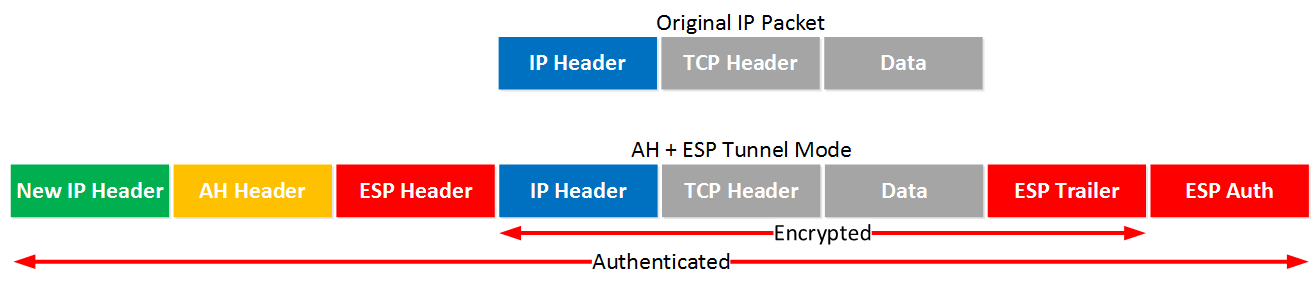
First we will have a new IP header followed by the AH and ESP header. The original IP packet will be completely encrypted and everything will be authenticated thanks to AH. Here’s what it looks like in wireshark:
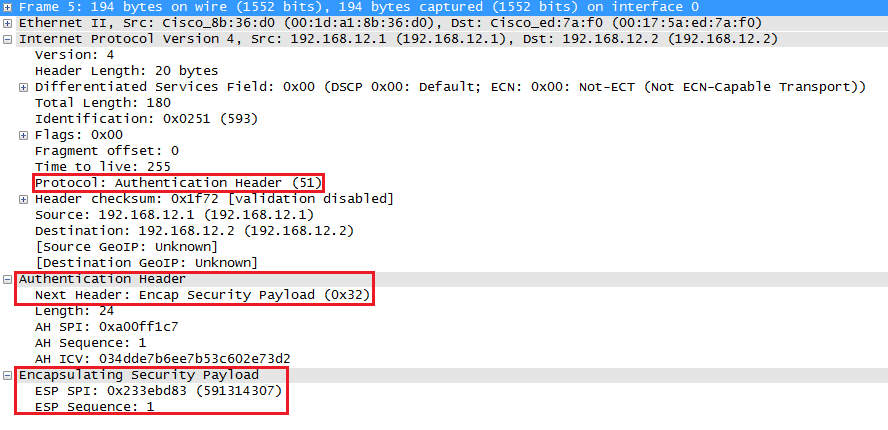
Above you can see the new IP header followed by the AH and ESP header.


【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步