tls/ssl
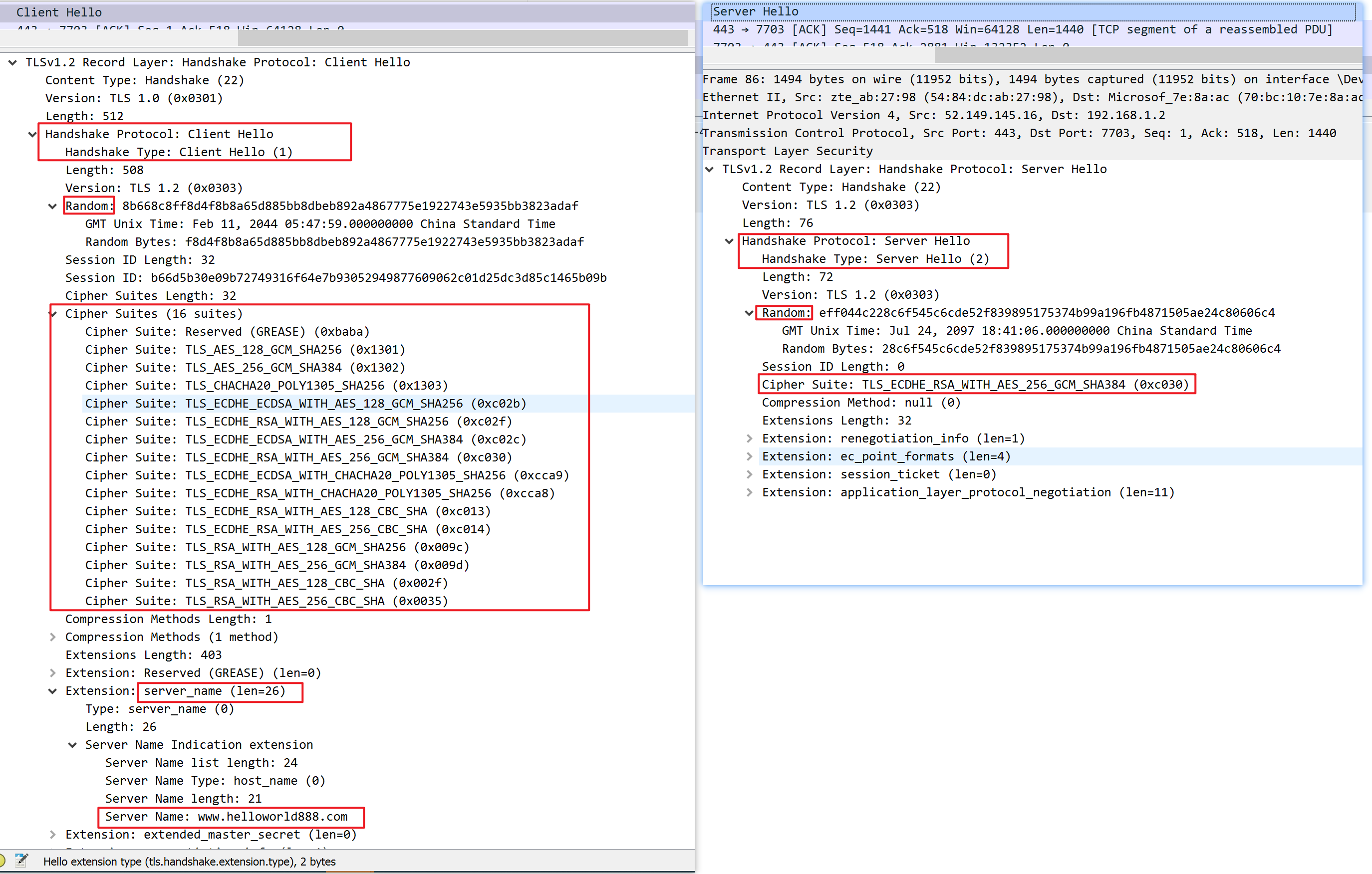
client hello
server hello
https://www.cloudflare.com/learning/ssl/what-happens-in-a-tls-handshake/
What is a TLS handshake?
TLS is an encryption protocol designed to secure Internet communications. A TLS handshake is the process that kicks off a communication session that uses TLS encryption. During a TLS handshake, the two communicating sides exchange messages to acknowledge each other, verify each other, establish the encryption algorithms they will use, and agree on session keys. TLS handshakes are a foundational part of how HTTPS works.
TLS vs. SSL handshakes
SSL, or Secure Sockets Layer, was the original encryption protocol developed for HTTP. SSL was replaced by TLS, or Transport Layer Security, some time ago. SSL handshakes are now called TLS handshakes, although the "SSL" name is still in wide use.
When does a TLS handshake occur?
A TLS handshake takes place whenever a user navigates to a website over HTTPS and the browser first begins to query the website's origin server. A TLS handshake also happens whenever any other communications use HTTPS, including API calls and DNS over HTTPS queries.
TLS handshakes occur after a TCP connection has been opened via a TCP handshake.
What happens during a TLS handshake?
During the course of a TLS handshake, the client and server together will do the following:
- Specify which version of TLS (TLS 1.0, 1.2, 1.3, etc.) they will use
- Decide on which cipher suites (see below) they will use
- Authenticate the identity of the server via the server’s public key and the SSL certificate authority’s digital signature
- Generate session keys in order to use symmetric encryption after the handshake is complete
What are the steps of a TLS handshake?
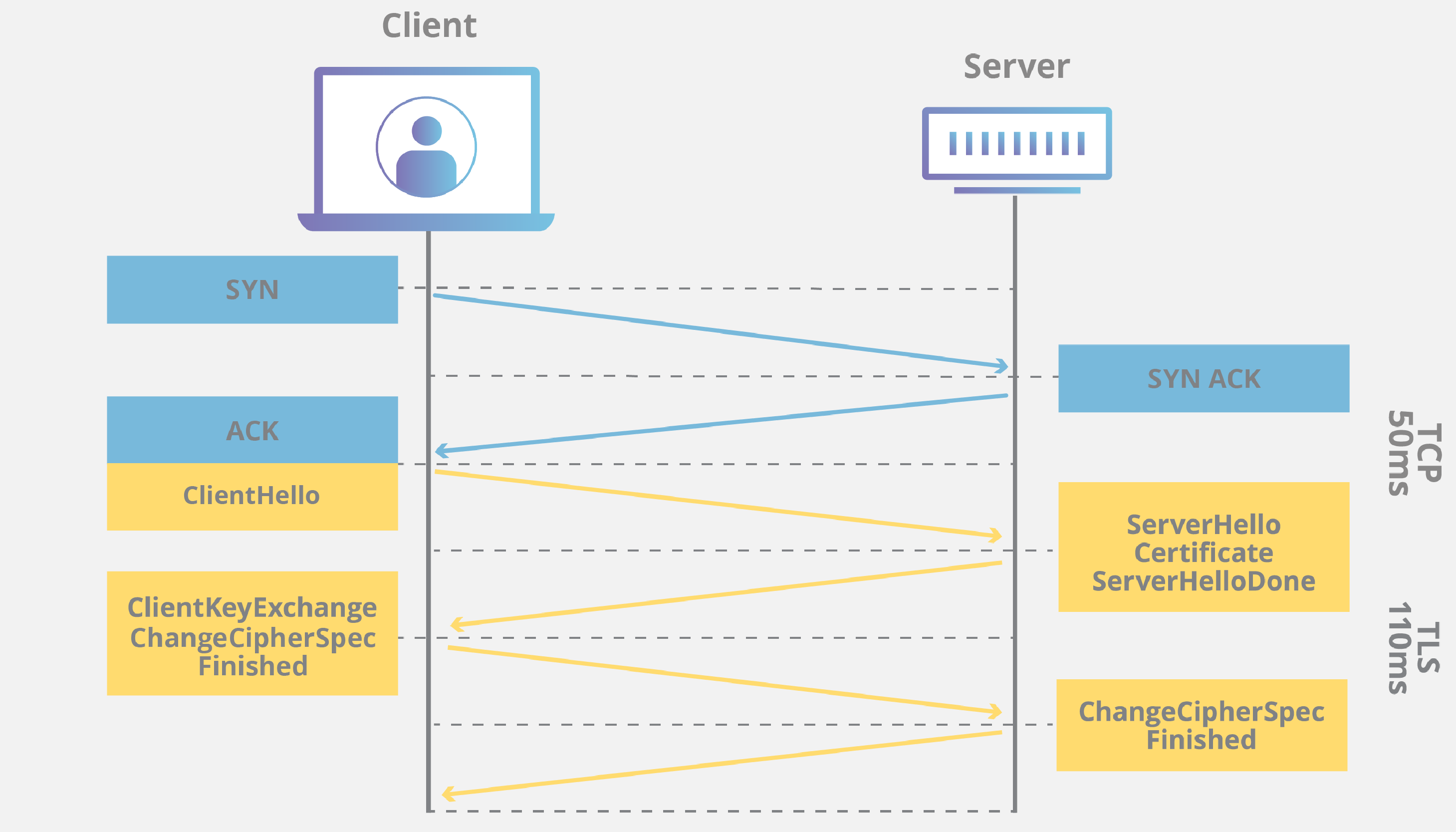
TLS handshakes are a series of datagrams, or messages, exchanged by a client and a server. A TLS handshake involves multiple steps, as the client and server exchange the information necessary for completing the handshake and making further conversation possible.
The exact steps within a TLS handshake will vary depending upon the kind of key exchange algorithm used and the cipher suites supported by both sides. The RSA key exchange algorithm is used most often. It goes as follows:
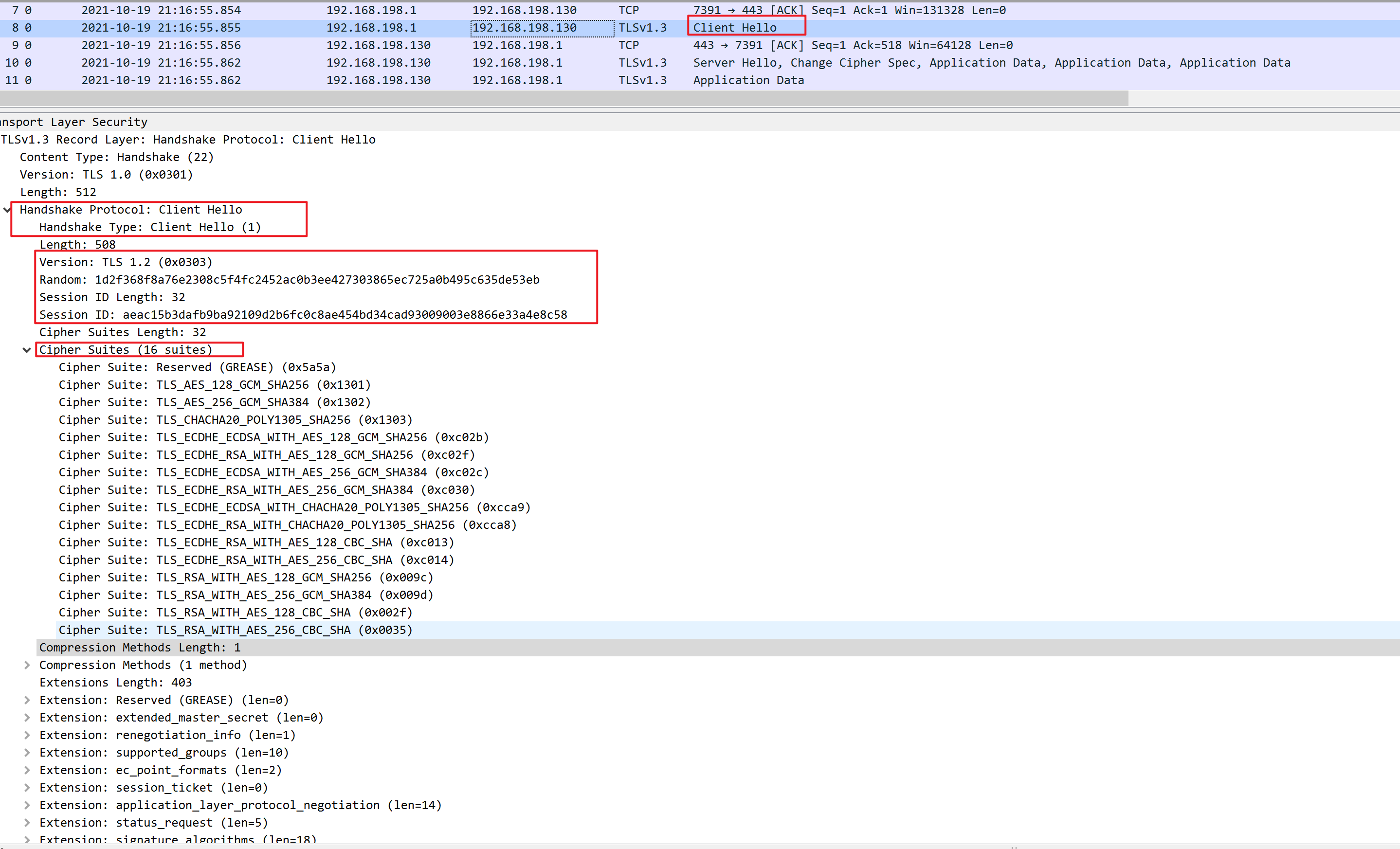
- The 'client hello' message: The client initiates the handshake by sending a "hello" message to the server. The message will include which TLS version the client supports, the cipher suites supported, and a string of random bytes known as the "client random."
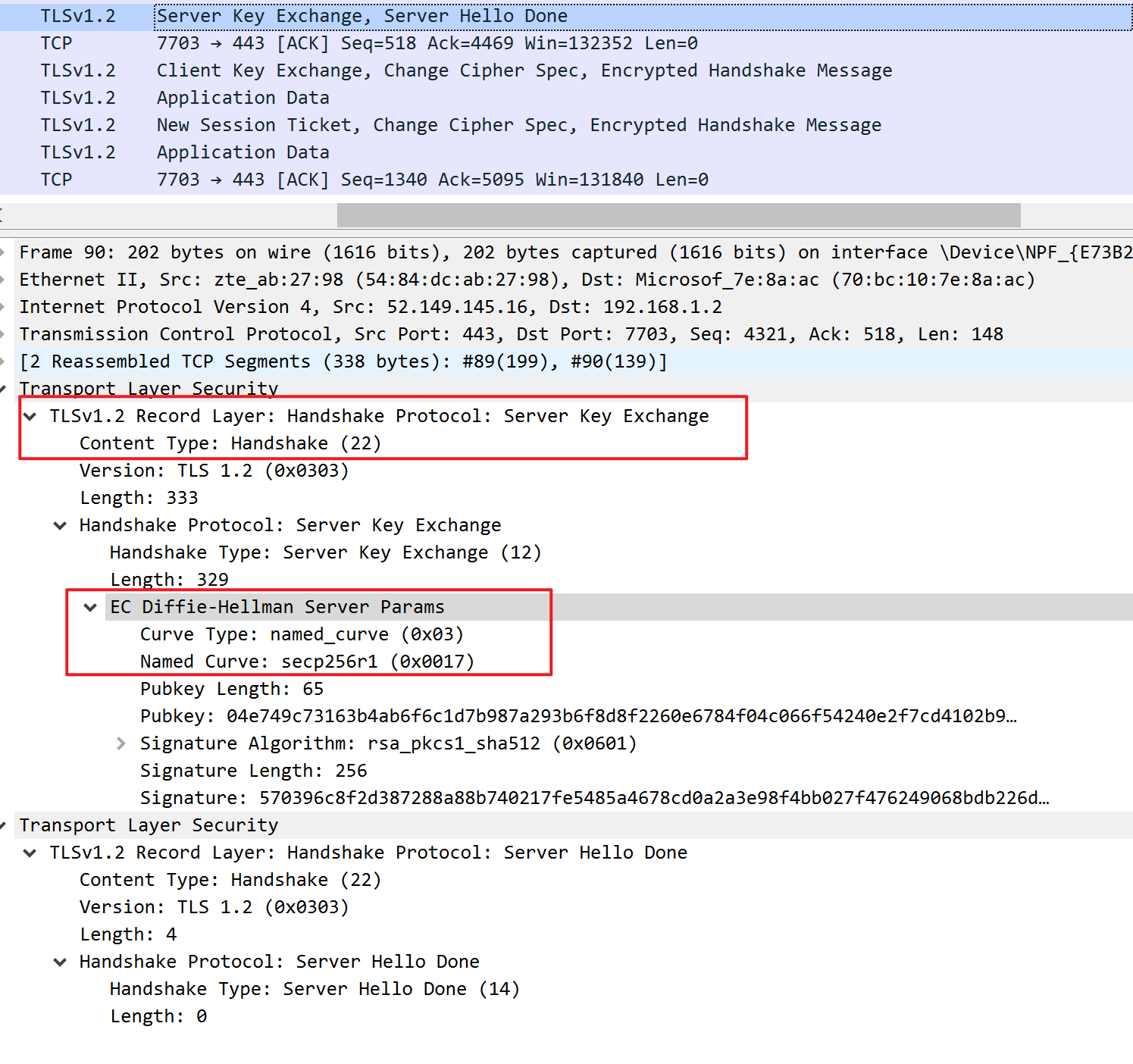
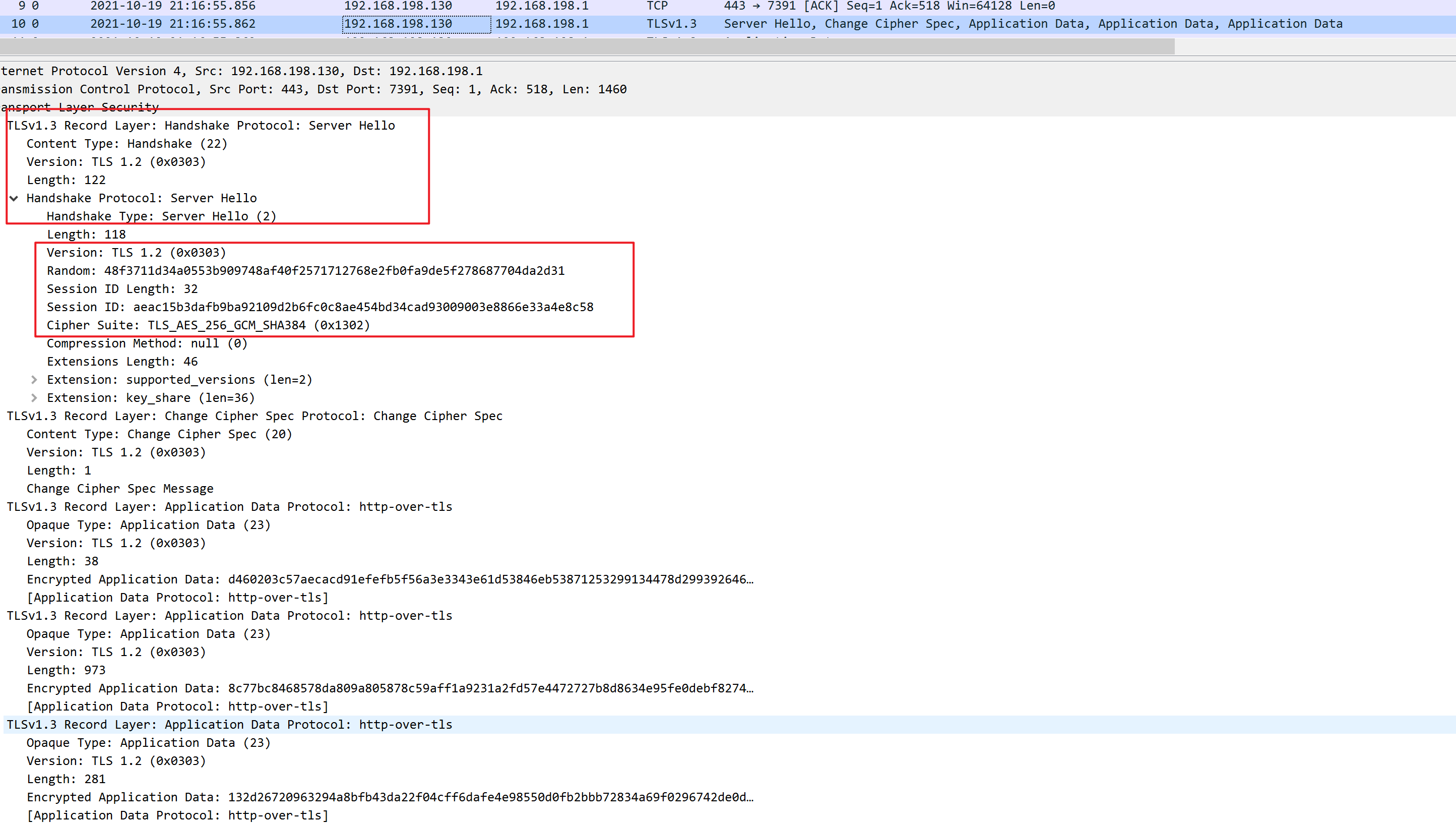
- The 'server hello' message: In reply to the client hello message, the server sends a message containing the server's SSL certificate, the server's chosen cipher suite, and the "server random," another random string of bytes that's generated by the server.
- Authentication: The client verifies the server's SSL certificate with the certificate authority that issued it. This confirms that the server is who it says it is, and that the client is interacting with the actual owner of the domain.
- The premaster secret: The client sends one more random string of bytes, the "premaster secret." The premaster secret is encrypted with the public key and can only be decrypted with the private key by the server. (The client gets the public key from the server's SSL certificate.)
- Private key used: The server decrypts the premaster secret.
- Session keys created: Both client and server generate session keys from the client random, the server random, and the premaster secret. They should arrive at the same results.
- Client is ready: The client sends a "finished" message that is encrypted with a session key.
- Server is ready: The server sends a "finished" message encrypted with a session key.
- Secure symmetric encryption achieved: The handshake is completed, and communication continues using the session keys.
All TLS handshakes make use of asymmetric encryption (the public and private key), but not all will use the private key in the process of generating session keys. For instance, an ephemeral Diffie-Hellman handshake proceeds as follows:
- Client hello: The client sends a client hello message with the protocol version, the client random, and a list of cipher suites.
- Server hello: The server replies with its SSL certificate, its selected cipher suite, and the server random. In contrast to the RSA handshake described above, in this message the server also includes the following (step 3):
- Server's digital signature: The server uses its private key to encrypt the client random, the server random, and its DH parameter*. This encrypted data functions as the server's digital signature, establishing that the server has the private key that matches with the public key from the SSL certificate.
- Digital signature confirmed: The client decrypts the server's digital signature with the public key, verifying that the server controls the private key and is who it says it is. Client DH parameter: The client sends its DH parameter to the server.
- Client and server calculate the premaster secret: Instead of the client generating the premaster secret and sending it to the server, as in an RSA handshake, the client and server use the DH parameters they exchanged to calculate a matching premaster secret separately.
- Session keys created: Now, the client and server calculate session keys from the premaster secret, client random, and server random, just like in an RSA handshake.
- Client is ready: Same as an RSA handshake.
- Server is ready
- Secure symmetric encryption achieved
*DH parameter: DH stands for Diffie-Hellman. The Diffie-Hellman algorithm uses exponential calculations to arrive at the same premaster secret. The server and client each provide a parameter for the calculation, and when combined they result in a different calculation on each side, with results that are equal.
To read more about the contrast between ephemeral Diffie-Hellman handshakes and other kinds of handshakes, and how they achieve forward secrecy, see What is Keyless SSL?
What is a cipher suite?
A cipher suite is a set of encryption algorithms for use in establishing a secure communications connection. (An encryption algorithm is a set of mathematical operations performed on data for making data appear random.) There are a number of cipher suites in wide use, and an essential part of the TLS handshake is agreeing upon which cipher suite will be used for that handshake.
What is SSL?
SSL stands for Secure Sockets Layer, and it refers to a protocol for encrypting and securing communications that take place on the Internet. Although SSL was replaced by an updated protocol called TLS (Transport Layer Security) some time ago, "SSL" is still a commonly used term for this technology.
The main use case for SSL/TLS is securing communications between a client and a server, but it can also secure email, VoIP, and other communications over unsecured networks.
How does SSL/TLS work?
These are the essential principles to grasp for understanding how SSL/TLS works:
- Secure communication begins with a TLS handshake, in which the two communicating parties open a secure connection and exchange the public key
- During the TLS handshake, the two parties generate session keys, and the session keys encrypt and decrypt all communications after the TLS handshake
- Different session keys are used to encrypt communications in each new session
- TLS ensures that the party on the server side, or the website the user is interacting with, is actually who they claim to be
- TLS also ensures that data has not been altered, since a message authentication code (MAC) is included with transmissions
With TLS, both HTTP data that users send to a website (by clicking, filling out forms, etc.) and the HTTP data that websites send to users is encrypted. Encrypted data has to be decrypted by the recipient using a key.
The TLS handshake
TLS communication sessions begin with a TLS handshake. A TLS handshake uses something called asymmetric encryption, meaning that two different keys are used on the two ends of the conversation. This is possible because of a technique called public key cryptography.
In public key cryptography, two keys are used: a public key, which the server makes available publicly, and a private key, which is kept secret and only used on the server side. Data encrypted with the public key can only be decrypted with the private key, and vice versa.
During the TLS handshake, the client and server use the public and private keys to exchange randomly generated data, and this random data is used to create new keys for encryption, called the session keys.
Symmetric encryption with session keys
Unlike asymmetric encryption, in symmetric encryption the two parties in a conversation use the same key. After the TLS handshake, both sides use the same session keys for encryption. Once session keys are in use, the public and private keys are not used anymore. Session keys are temporary keys that are not used again once the session is terminated. A new, random set of session keys will be created for the next session.
Authenticating the origin server
TLS communications from the server include a message authentication code, or MAC, which is a digital signature confirming that the communication originated from the actual website. This authenticates the server, preventing on-path attacks and domain spoofing. It also ensures that the data has not been altered in transit.
What is an SSL certificate?
An SSL certificate is a file installed on a website's origin server. It's simply a data file containing the public key and the identity of the website owner, along with other information. Without an SSL certificate, a website's traffic can't be encrypted with TLS.
Technically, any website owner can create their own SSL certificate, and such certificates are called self-signed certificates. However, browsers do not consider self-signed certificates to be as trustworthy as SSL certificates issued by a certificate authority.
How does a website get an SSL certificate?
Website owners need to obtain an SSL certificate from a certificate authority, and then install it on their web server (often a web host can handle this process). A certificate authority is an outside party who can confirm that the website owner is who they say they are. They keep a copy of the certificates they issue.
Is it possible to get a free SSL certificate?
Many certificate authorities charge for SSL certificates. To help make the Internet more secure, Cloudflare offers free SSL certificates. Cloudflare was the first Internet security and performance company to do so. Cloudflare also has worked to optimize SSL/TLS performance so that websites moving from HTTP to HTTPS do not have their performance impacted.
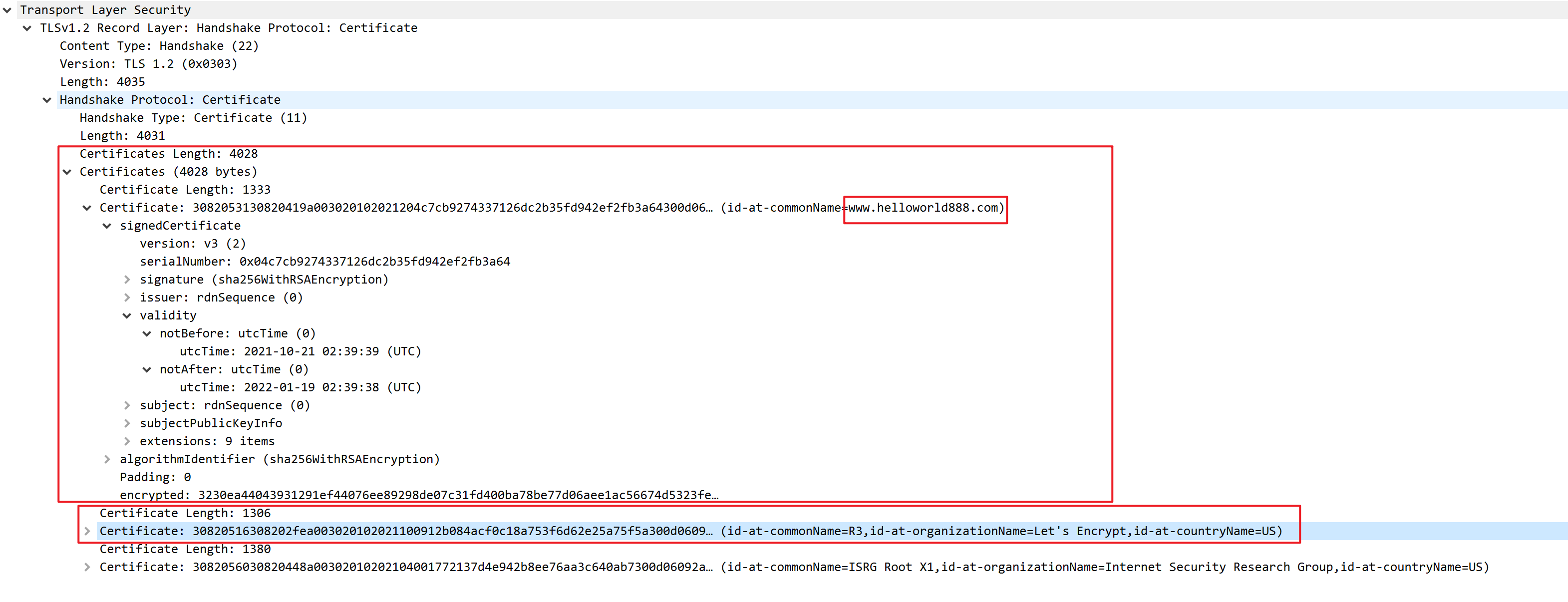
Certificate
大多数key交换方法都不是匿名的,这意味着服务器必须使用公钥证书向客户端认证自己(除了DH group)。因此,服务器向客户端发送完ServerHello消息,马上发送Certificate消息(在同一个flight内)。同样,在SSL握手的时候,当服务器发送CertificateRequest消息,客户端就要回复Certificate消息。不论如何,Certificate消息传送公钥证书,或者是公钥证书链(certificate_list)。公钥证书链以发送者的证书开始,然后是一系列的CA证书,向上一直到根CA证书。证书类型必须适合使用的key交换算法。一般是X.509证书。
二、对称加密
对称密码 (symmetric cryptography)是指在加密和解密时使用同一密钥的方式。目前广泛使用 AES。
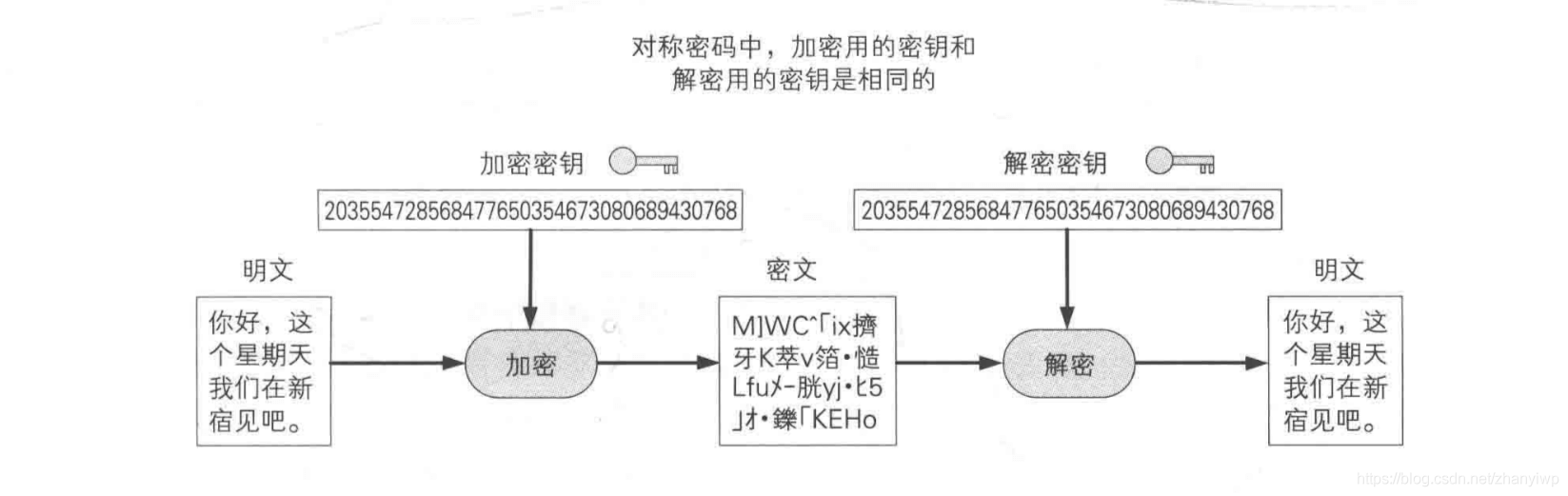
对称加密有一个问题就是密钥配送问题, 即发送方和接收方如何在一个不安全的信道上共享密码的问题。
三、非对称加密
非对称加密(也叫公钥密码 (public-key cryptography))则是指在加密和解密时使用不同密钥的方式。目前广泛使用 RSA和ECDH。(RSA、ElGamal、Rabin、DH、ECDH)
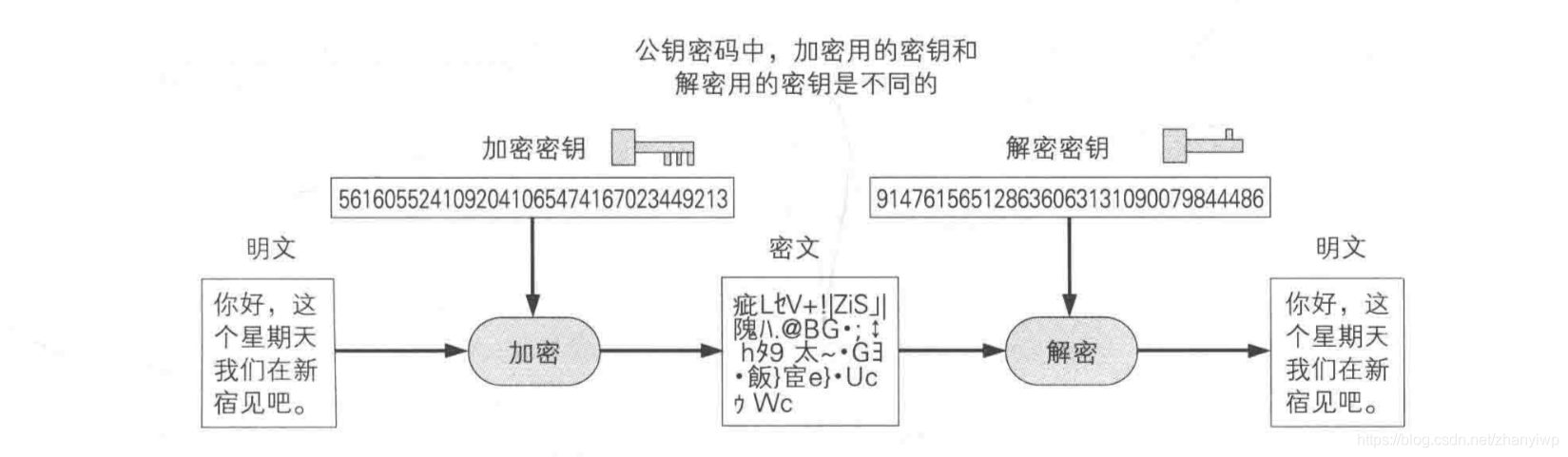
非对称加密的加密密钥和解密密钥不同,形成一对,具有强烈的数学关系。其中可以公开的一个一般称为公钥,可以给任何人,另一个则不能公开,称为私钥。私钥一定严格妥善保管。通过公钥加密的密文只能由私钥解密。因此接收者Bob可以将公钥发给发送者Alice,然后Alice用公钥加密消息,并发送。即使被窃听者窃取到公钥也没关系。因为用公钥加密的密文只能由对应的私钥解密,而私钥只有接收者Bob才有。因此非对称加密解决了密钥配送问题,但依然存在下面两个问题:
处理速度远远低于对称加密
难以抵御中间人攻击
四、混合密码系统
混合密码系统是将对称加密和非对称加密优势相结合的一种混合方式。可以解决对称加密密钥配送和非对称加密处理速度低的问题。主要流程如下
发送者用接收者的公钥加密对称加密的密钥,并发送
接受者得到用公钥加密的密钥,然后用私钥解密,得到对称加密的密钥
发送者用对称加密的密钥加密消息内容,并发送
接收者用对称加密的密钥解密消息
对于使用DHE/ECDHE非对称密钥协商算法的SSL握手,将发送该类型握手。
RSA算法不会继续该握手流程(DH、ECDH也不会发送server key exchange)