ipsec - IKE
In symmetric cryptographic systems, both communicating parties use the same key for encryption and decryption. The material used to build these keys must be exchanged in a secure fashion. Information can be securely exchanged only if the key belongs exclusively to the communicating parties.
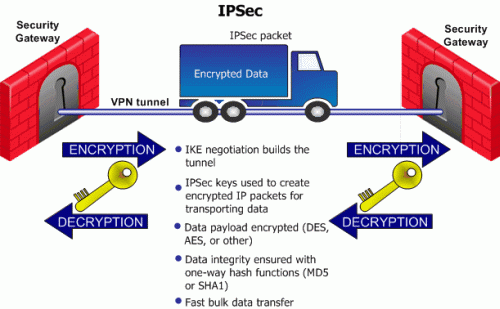
The goal of the Internet Key Exchange (IKE) is for both sides to independently produce the same symmetrical key. This key then encrypts and decrypts the regular IP packets used in the bulk transfer of data between VPN peers. IKE builds the VPN tunnel by authenticating both sides and reaching an agreement on methods of encryption and integrity. The outcome of an IKE negotiation is a Security Association (SA).
This agreement upon keys and methods of encryption must also be performed securely. For this reason, IKE is composed of two phases. The first phase lays the foundations for the second. Both IKEv1 and IKEv2 are supported in Security Gateways of version R71 and higher.
Diffie-Hellman (DH) is that part of the IKE protocol used for exchanging the material from which the symmetrical keys are built. The Diffie-Hellman algorithm builds an encryption key known as a "shared secret" from the private key of one party and the public key of the other. Since the IPSec symmetrical keys are derived from this DH key shared between the peers, at no point are symmetric keys actually exchanged.
IKE Phase I
During IKE Phase I:
- The peers authenticate, either by certificates or via a pre-shared secret.
- A Diffie-Hellman key is created. The nature of the Diffie-Hellman protocol means that both sides can independently create the shared secret, a key which is known only to the peers.
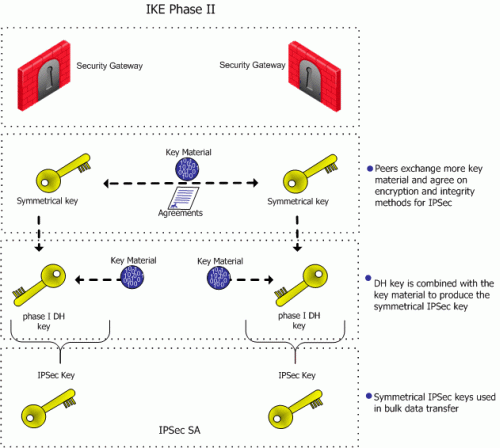
- Key material (random bits and other mathematical data) as well as an agreement on methods for IKE phase II are exchanged between the peers.
In terms of performance, the generation of the Diffie Hellman Key is slow and heavy. The outcome of this phase is the IKE SA, an agreement on keys and methods for IKE phase II. Figure 2‑1 illustrates the process that takes place during IKE phase I but does not necessarily reflect the actual order of events.

IKE Phase II (Quick mode or IPSec Phase)
IKE phase II is encrypted according to the keys and methods agreed upon in IKE phase I. The key material exchanged during IKE phase II is used for building the IPSec keys. The outcome of phase II is the IPSec Security Association. The IPSec SA is an agreement on keys and methods for IPSec, thus IPSec takes place according to the keys and methods agreed upon in IKE phase II.
After the IPSec keys are created, bulk data transfer takes place:
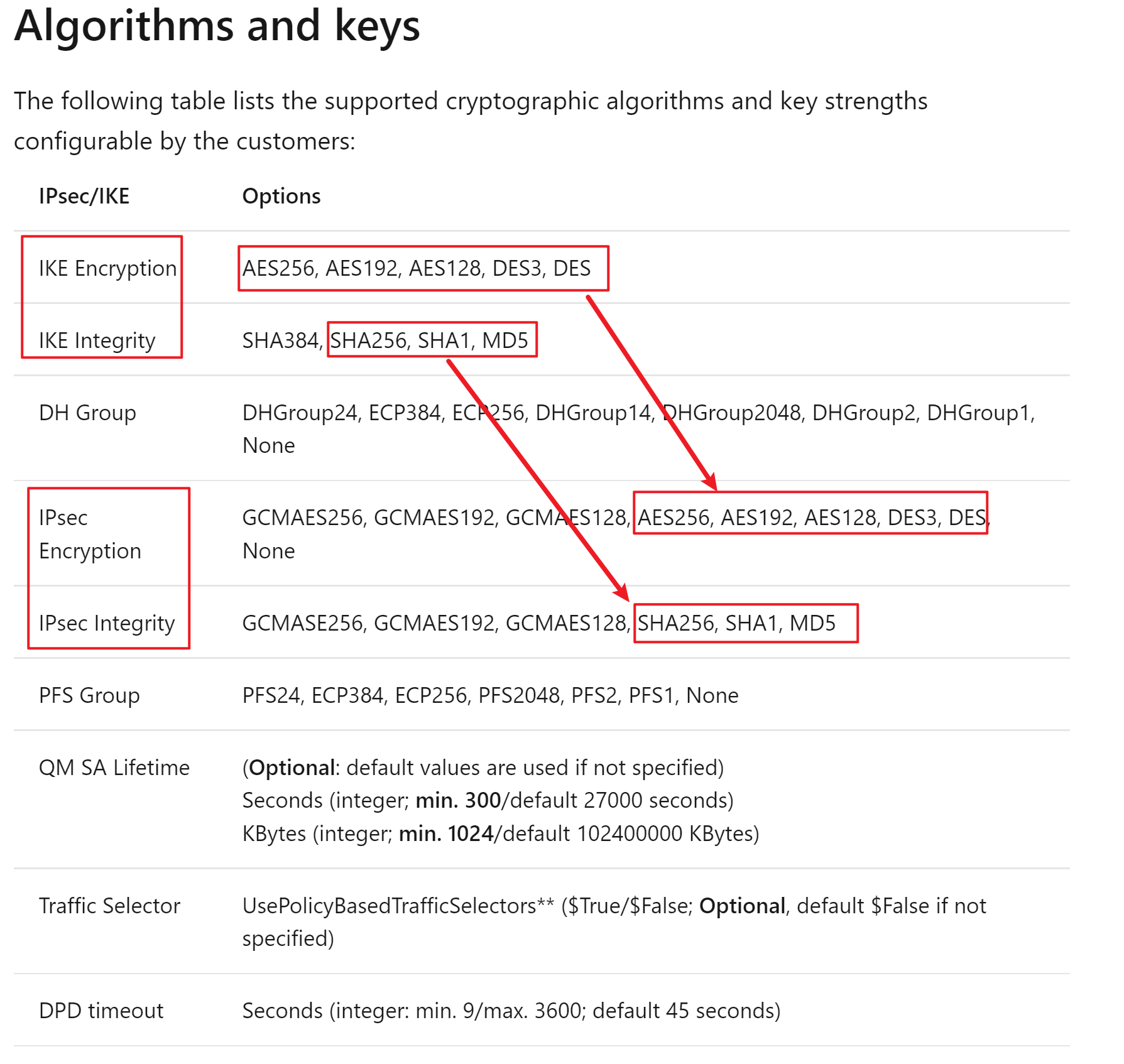
Methods of Encryption and Integrity
Two parameters are decided during the negotiation:
- Encryption algorithm
- Hash algorithm
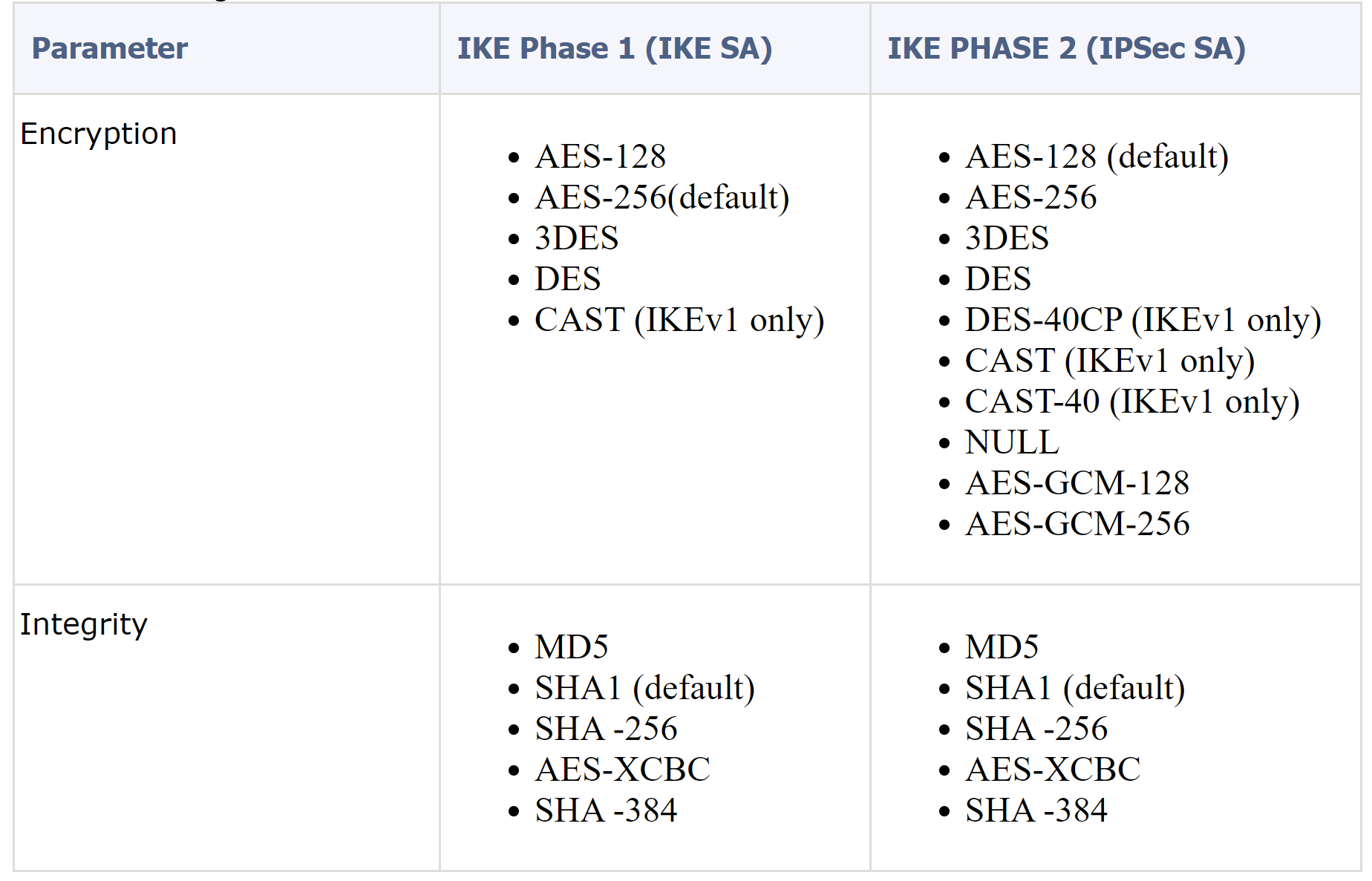
Diffie Hellman Groups
The Diffie-Hellman key computation (also known as exponential key agreement) is based on the Diffie Hellman (DH) mathematical groups. A Security Gateway supports these DH groups during the two phases of IKE.
IKEv2
IKE_SA_INIT
IKE_AUTH
IKEv2 defines three types of exchanges: initial exchanges, CREATE_CHILD_SA exchange, and INFORMATIONAL exchange.
IKEv2 uses two exchanges during the initial exchange process: IKE_SA_INIT and IKE_AUTH, each with two messages.
IKE_SA_INIT exchange—Negotiates IKE SA parameters and exchanges keys.
IKE_AUTH exchange—Authenticates the identity of the peer and establishes IPsec SAs.
After the four-message initial exchanges, IKEv2 sets up one IKE SA and one pair of IPsec SAs.
To set up one more pair of IPsec SAs within the IKE SA, IKEv2 goes on to perform an additional two-message exchange—the CREATE_CHILD_SA exchange. One CREATE_CHILD_SA exchange creates one pair of IPsec SAs. IKEv2 also uses the CREATE_CHILD_SA exchange to rekey IKE SAs and Child SAs.
IKEv2 uses the INFORMATIONAL exchange to convey control messages about errors and notifications.
As a framework, IPsec uses a variety of protocols to implement the features I described above. Here’s an overview:

Don’t worry about all the boxes you see in the picture above, we will cover each of those. To give you an example, for encryption we can choose if we want to use DES, 3DES or AES. For authentication you can choose between MD5 or SHA.
IPsec can be used on many different devices, it’s used on routers, firewalls, hosts and servers. Here are some examples how you can use it:
- Between two routers to create a site-to-site VPN that “bridges” two LANs together.
- Between a firewall and windows host for remote access VPN.
- Between two linux servers to protect an insecure protocol like telnet.
IPsec is pretty complex and there are a lot of different ways to implement it. In this lesson I will start with an overview and then we will take a closer look at each of the components.
Before we can protect any IP packets, we need two IPsec peers that build the IPsec tunnel.
To establish an IPsec tunnel, we use a protocol called IKE (Internet Key Exchange).
There are two phases to build an IPsec tunnel:
- IKE phase 1
- IKE phase 2
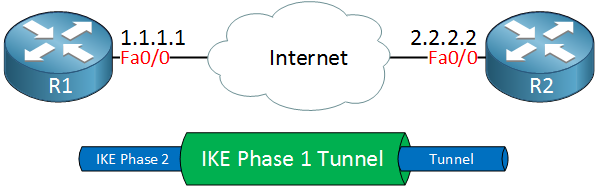
In IKE phase 1, two peers will negotiate about the encryption, authentication, hashing and other protocols that they want to use and some other parameters that are required. In this phase, an ISAKMP (Internet Security Association and Key Management Protocol) session is established. This is also called the ISAKMP tunnel or IKE phase 1 tunnel.
The collection of parameters that the two devices will use is called a SA (Security Association). Here’s an example of two routers that have established the IKE phase 1 tunnel:

The IKE phase 1 tunnel is only used for management traffic. We use this tunnel as a secure method to establish the second tunnel called the IKE phase 2 tunnel or IPsec tunnel and for management traffic like keepalives.
Here’s a picture of our two routers that completed IKE phase 2:
Once IKE phase 2 is completed, we have an IKE phase 2 tunnel (or IPsec tunnel) that we can use to protect our user data. This user data will be sent through the IKE phase 2 tunnel:
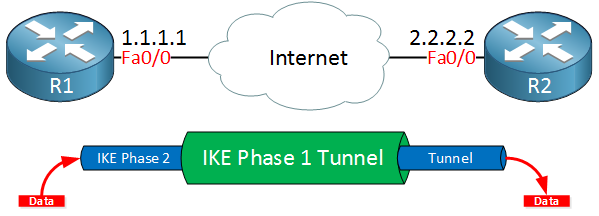
IKE builds the tunnels for us but it doesn’t authenticate or encrypt user data. We use two other protocols for this:
- AH (Authentication Header)
- ESP (Encapsulating Security Payload)
AH and ESP both offer authentication and integrity but only ESP supports encryption. Because of this, ESP is the most popular choice nowadays.
Both protocols support two different modes:
- Transport mode
- Tunnel mode
The main difference between the two is that with transport mode we will use the original IP header while in tunnel mode, we use a new IP header. Here’s an example to help you visualize this:
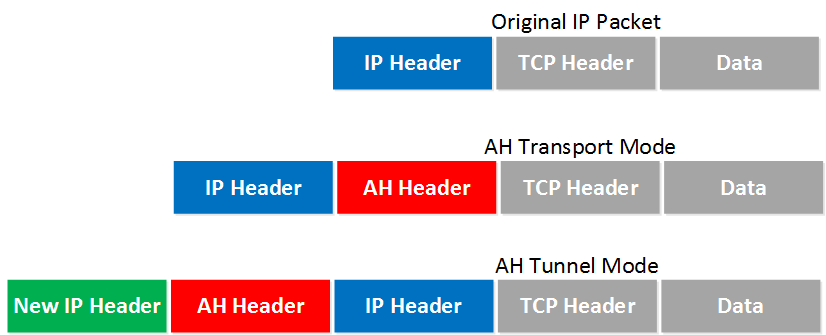
Transport mode is often between two devices that want to protect some insecure traffic (example: telnet traffic). Tunnel mode is typically used for site-to-site VPNs where we need to encapsulate the original IP packet since these are mostly private IP addresses and can’t be routed on the Internet. I will explain these two modes in detail later in this lesson.
The entire process of IPsec consists of five steps:
- Initiation: something has to trigger the creation of our tunnels. For example when you configure IPsec on a router, you use an access-list to tell the router what data to protect. When the router receives something that matches the access-list, it will start the IKE process. It’s also possible to manually initiate the tunnel.
- IKE phase 1: we negotiate a security association to build the IKE phase 1 tunnel (ISAKMP tunnel).
- IKE phase 2: within the IKE phase 1 tunnel, we build the IKE phase 2 tunnel (IPsec tunnel).
- Data transfer: we protect user data by sending it through the IKE phase 2 tunnel.
- Termination: when there is no user data to protect then the IPsec tunnel will be terminated after awhile.
Now you have an idea of the basics of IPsec, let’s take a closer look at each of the different components.


