android R:FingerprintBoundKeysTest闪退
异常日志:
26634 09-12 19:45:34.213 299 299 I OpteeKeymaster_ipc: TEEC_InvokeCommand cmd 4 failed with code 0xffffffe6 (User is not authenticated) origin 0x00000004 26635 09-12 19:45:34.214 299 299 E OpteeKeymaster_ipc: Response of size 8192 contained error code -26 26636 09-12 19:45:34.214 299 299 E OpteeKeymaster_cpp: Failed to send cmd 4 err: -26 26637 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: encryptInternal: [6]: User not authenticated 26638 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: android.security.keystore.UserNotAuthenticatedException: User not authenticated 26639 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.security.KeyStore.getInvalidKeyException(KeyStore.java:1372) 26640 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.security.KeyStore.getInvalidKeyException(KeyStore.java:1391) 26641 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.security.keystore.KeyStoreCryptoOperationUtils.getInvalidKeyExceptionForInit(KeyStoreCryptoOperationUtils.java:54) 26642 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.security.keystore.KeyStoreCryptoOperationUtils.getExceptionForCipherInit(KeyStoreCryptoOperationUtils.java:89) 26643 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.security.keystore.AndroidKeyStoreCipherSpiBase.ensureKeystoreOperationInitialized(AndroidKeyStoreCipherSpiBase.java:265) 26644 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.security.keystore.AndroidKeyStoreCipherSpiBase.engineInit(AndroidKeyStoreCipherSpiBase.java:109) 26645 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at javax.crypto.Cipher.tryTransformWithProvider(Cipher.java:2984) 26646 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at javax.crypto.Cipher.tryCombinations(Cipher.java:2891) 26647 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at javax.crypto.Cipher$SpiAndProviderUpdater.updateAndGetSpiAndProvider(Cipher.java:2796) 26648 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at javax.crypto.Cipher.chooseProvider(Cipher.java:773) 26649 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at javax.crypto.Cipher.init(Cipher.java:1143) 26650 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at javax.crypto.Cipher.init(Cipher.java:1084) 26651 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at com.android.cts.verifier.security.FingerprintBoundKeysTest.encryptInternal(FingerprintBoundKeysTest.java:228) 26652 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at com.android.cts.verifier.security.FingerprintBoundKeysTest.prepareEncrypt(FingerprintBoundKeysTest.java:189) 26653 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at com.android.cts.verifier.security.FingerprintBoundKeysTest.startTest(FingerprintBoundKeysTest.java:139) 26654 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at com.android.cts.verifier.security.FingerprintBoundKeysTest$1.onClick(FingerprintBoundKeysTest.java:118) 26655 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.view.View.performClick(View.java:7448) 26656 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.view.View.performClickInternal(View.java:7425) 26657 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.view.View.access$3600(View.java:810) 26658 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.view.View$PerformClick.run(View.java:28305) 26659 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.os.Handler.handleCallback(Handler.java:938) 26660 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.os.Handler.dispatchMessage(Handler.java:99) 26661 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.os.Looper.loop(Looper.java:223) 26662 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at android.app.ActivityThread.main(ActivityThread.java:7664) 26663 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at java.lang.reflect.Method.invoke(Native Method) 26664 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:592) 26665 09-12 19:45:34.241 4288 4288 W FingerprintBoundKeysTest: at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:948)
26672 --------- beginning of crash 26673 09-12 19:45:34.245 4288 4288 E AndroidRuntime: FATAL EXCEPTION: main 26674 09-12 19:45:34.245 4288 4288 E AndroidRuntime: Process: com.android.cts.verifier, PID: 4288 26675 09-12 19:45:34.245 4288 4288 E AndroidRuntime: java.lang.IllegalStateException: Cipher not initialized 26676 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at javax.crypto.Cipher.checkCipherState(Cipher.java:1640) 26677 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at javax.crypto.Cipher.doFinal(Cipher.java:2047) 26678 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at com.android.cts.verifier.security.FingerprintBoundKeysTest.encryptInternal(FingerprintBoundKeysTest.java:233) 26679 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at com.android.cts.verifier.security.FingerprintBoundKeysTest.tryEncrypt(FingerprintBoundKeysTest.java:198) 26680 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at com.android.cts.verifier.security.FingerprintBoundKeysTest.startTest(FingerprintBoundKeysTest.java:140) 26681 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at com.android.cts.verifier.security.FingerprintBoundKeysTest$1.onClick(FingerprintBoundKeysTest.java:118) 26682 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.view.View.performClick(View.java:7448) 26683 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.view.View.performClickInternal(View.java:7425) 26684 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.view.View.access$3600(View.java:810) 26685 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.view.View$PerformClick.run(View.java:28305) 26686 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.os.Handler.handleCallback(Handler.java:938) 26687 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.os.Handler.dispatchMessage(Handler.java:99) 26688 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.os.Looper.loop(Looper.java:223) 26689 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at android.app.ActivityThread.main(ActivityThread.java:7664) 26690 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at java.lang.reflect.Method.invoke(Native Method) 26691 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:592) 26692 09-12 19:45:34.245 4288 4288 E AndroidRuntime: at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:948)
【调试】optee_keymaster_ipc.cpp中添加log:
dump函数:
void dump_data(uint8_t *data, uint32_t data_len) { char buf[128]; int n = 0; int size = 0; int count = data_len/16; if(data_len % 16 != 0) { count++; } ALOGD("dump_data data_len = %u, count = %d\n", data_len, count); for (uint32_t i = 0; i < count; i++) { n = 0; size = snprintf(&buf[n], sizeof(buf) - n, "[%03x]", i); n += size; uint32_t count_j = 16; if (i == count - 1 && data_len % 16 != 0) { count_j = data_len % 16; } for (uint32_t j = 0; j < count_j; j++) { size = snprintf(&buf[n], sizeof(buf) - n, " %02x", data[16 * i + j]); n += size; } buf[n] = '\0'; ALOGD("%s\n", buf); } }
【调试】关键函数中dump request数据:
如generateKey,begin,update,finish等函数
ALOGD("%s line:%d len = %u", __func__, __LINE__, len); uint8_t data[KEYMASTER_MAX_BUFFER_LENGTH]; request.Serialize(data, data + len); dump(data, len);
带dump数据的log:
0846 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: optee_keymaster_call 273 0 = KM_GENERATE_KEY 0847 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: dump_data data_len = 92, count = 6 0848 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: [000] 00 00 00 00 09 00 00 00 50 00 00 00 03 00 00 30 0849 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: [001] 80 00 00 00 02 00 00 10 20 00 00 00 01 00 00 20 0850 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: [002] 00 00 00 00 01 00 00 20 01 00 00 00 04 00 00 20 0851 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: [003] 02 00 00 00 06 00 00 20 40 00 00 00 f6 01 00 a0 0852 09-13 14:53:21.240 301 301 D OpteeKeymaster_ipc: [004] 2c 53 35 b7 b2 a3 42 57 f8 01 00 10 02 00 00 00 0853 09-13 14:53:21.241 301 301 D OpteeKeymaster_ipc: [005] bd 02 00 60 e8 da 50 8d 8a 01 00 00
0905 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: optee_keymaster_call 273 4 = KM_BEGIN_OPERATION 0906 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: dump_data data_len = 493, count = 31 0907 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [000] 00 00 00 00 70 01 00 00 12 65 0e 94 a9 7f 3d 74 0908 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [001] 8c 89 f9 bb 2c 06 f6 49 1b 3a 78 29 99 29 c7 1b 0909 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [002] cf 36 47 0e 75 a3 2c 56 8d ed 78 92 ee ea 24 d6 0910 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [003] fa a8 f2 83 05 84 58 a0 ac b3 ae a8 de 31 08 79 0911 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [004] 89 b9 8c c5 84 b4 81 77 99 f3 d9 74 c7 81 75 0b 0912 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [005] 49 54 98 56 7b b8 e6 21 6a 1f a0 79 42 51 4d fe 0913 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [006] 6d 00 c3 b9 02 1c bd f2 62 26 39 23 f0 72 fa 12 0914 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [007] 6c 52 6b 7b ac 10 a5 f8 4b ad a7 c5 ac 44 b1 f1 0915 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [008] 38 d3 70 7b ad 0d ce 80 fd a4 df 66 9d 09 81 1e 0916 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [009] 6c af 03 3f bb 38 93 53 1b 7e 38 2b 25 6f 52 ad 0917 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [00a] b8 74 7b 01 f4 6b 9a 55 a6 9f e3 82 a0 d9 aa 98 0918 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [00b] 1d a7 8e 2e 9f 9a 9e 64 57 5e 8b bd 60 7c b3 5d 0919 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [00c] 5c e0 55 f3 99 24 af d3 fb 72 1d 71 66 7b ef 29 0920 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [00d] 9d 04 86 7d bb ed 3d 90 89 47 87 91 88 c9 0f 7f 0921 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [00e] 62 50 ae cc 5f cb ca 88 18 27 df 11 8f 72 98 09 0922 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [00f] cb 41 ac ae 8c c2 e3 50 14 f9 5e 59 af 31 79 78 0923 09-13 14:53:21.822 301 301 D OpteeKeymaster_ipc: [010] df a5 e2 84 4e 13 39 3e e4 e7 f4 fc 12 bc cb 0a 0924 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [011] 7d b5 89 1a 23 0e 32 6d 16 fc ed 73 82 4b 00 05 0925 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [012] ef 3e 68 ba a5 7a f5 cf bf 44 e4 e6 b9 0a bf ec 0926 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [013] 3f 56 af ef ab 1d fb f3 00 36 7f d0 79 16 02 63 0927 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [014] 6a 07 76 3f cb 05 3b c9 c9 f0 c7 a5 fb 25 f7 24 0928 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [015] c8 02 25 65 27 a4 3b cd 8d 1e 97 7c cd 68 03 3d 0929 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [016] 19 ae 61 5d 7f f7 19 c0 d2 b9 ce a1 de f0 d0 68 0930 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [017] 2c 84 2a 11 41 5b 73 91 45 00 00 00 00 00 00 00 0931 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [018] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0932 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [019] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0933 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [01a] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0934 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [01b] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0935 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [01c] 00 04 00 00 00 24 00 00 00 02 00 00 10 20 00 00 0936 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [01d] 00 04 00 00 20 02 00 00 00 06 00 00 20 40 00 00 0937 09-13 14:53:21.823 301 301 D OpteeKeymaster_ipc: [01e] 00 ea 03 00 90 45 00 00 00 00 00 00 00 0939 09-13 14:53:22.432 301 301 I OpteeKeymaster_ipc: TEEC_InvokeCommand cmd 4 failed with code 0xffffffe6 (User is not authenticated) origin 0x00000004 0940 09-13 14:53:22.432 301 301 E OpteeKeymaster_ipc: Response of size 8192 contained error code -26 0941 09-13 14:53:22.432 301 301 E OpteeKeymaster_cpp: Failed to send cmd 4 err: -26
generateKey函数:
hardware/interfaces/keymaster/3.0/IKeymasterDevice.hal
/** * Generates a key, or key pair, returning a key blob and/or a description of the key. * * @param keyParams Key generation parameters are defined as keymaster tag/value pairs, provided * in params. See Tag in types.hal for the full list. * * @return error See the ErrorCode enum in types.hal. * * @return keyBlob Opaque, encrypted descriptor of the generated key, which generally contains a * copy of the key material, wrapped in a key unavailable outside secure hardware. * * @return keyCharacteristics Description of the generated key. See KeyCharacteristis in * types.hal. */ generateKey(vec<KeyParameter> keyParams) generates(ErrorCode error, vec<uint8_t> keyBlob, KeyCharacteristics keyCharacteristics);
GenerateKeyRequest:
system/keymaster/include/keymaster/android_keymaster_messages.h
struct GenerateKeyRequest : public KeymasterMessage { explicit GenerateKeyRequest(int32_t ver = MAX_MESSAGE_VERSION) : KeymasterMessage(ver) {} size_t SerializedSize() const override { return key_description.SerializedSize(); } uint8_t* Serialize(uint8_t* buf, const uint8_t* end) const override { return key_description.Serialize(buf, end); } bool Deserialize(const uint8_t** buf_ptr, const uint8_t* end) override { return key_description.Deserialize(buf_ptr, end); } AuthorizationSet key_description; };
AuthorizationSet::Serialize
system/keymaster/android_keymaster/authorization_set.cpp
uint8_t* AuthorizationSet::Serialize(uint8_t* buf, const uint8_t* end) const { buf = append_size_and_data_to_buf(buf, end, indirect_data_, indirect_data_size_); buf = append_uint32_to_buf(buf, end, elems_size_); buf = append_uint32_to_buf(buf, end, SerializedSizeOfElements()); for (size_t i = 0; i < elems_size_; ++i) { buf = serialize(elems_[i], buf, end, indirect_data_); } return buf; }
generateKey的request:
optee_keymaster_call 273 0 = KM_GENERATE_KEY
dump_data data_len = 92, count = 6
[000] 00 00 00 00 09 00 00 00 50 00 00 00 03 00 00 30 --->key_size
[001] 80 00 00 00 02 00 00 10 20 00 00 00 01 00 00 20 --->algorithm和purpose
[002] 00 00 00 00 01 00 00 20 01 00 00 00 04 00 00 20 --->purpose和block mode
[003] 02 00 00 00 06 00 00 20 40 00 00 00 f6 01 00 a0 --->padding 和 user secure id
[004] 2c 53 35 b7 b2 a3 42 57 f8 01 00 10 02 00 00 00 ---> user auth type
[005] bd 02 00 60 e8 da 50 8d 8a 01 00 00 --->creation datetime
TA对应也打印了一份,解析过程也打印了部分:
13284 [59663.374600] 59672.405 D/TA: TA_generateKey:287 TA_generateKey 287, dump data start, size = 92 13285 [59663.380402] 59672.413 D/TA: dump_data:1620 dump data_len = 92, count = 6 13286 [59663.380431] 59672.419 D/TA: dump_data:1634 [000] 00 00 00 00 09 00 00 00 50 00 00 00 03 00 00 30 13287 [59663.395833] 59672.427 D/TA: dump_data:1634 [001] 80 00 00 00 02 00 00 10 20 00 00 00 01 00 00 20 13288 [59663.403584] 59672.435 D/TA: dump_data:1634 [002] 00 00 00 00 01 00 00 20 01 00 00 00 04 00 00 20 13289 [59663.411315] 59672.442 D/TA: dump_data:1634 [003] 02 00 00 00 06 00 00 20 40 00 00 00 f6 01 00 a0 13290 [59663.419042] 59672.450 D/TA: dump_data:1634 [004] 2c 53 35 b7 b2 a3 42 57 f8 01 00 10 02 00 00 00 13291 [59663.425729] 59672.458 D/TA: dump_data:1634 [005] bd 02 00 60 e8 da 50 8d 8a 01 00 00 13292 [59663.432126] 59672.464 D/TA: TA_generateKey:289 TA_generateKey 289, dump data end 13293 [59663.437963] 59672.471 D/TA: TA_deserialize_auth_set:192 check_presence = 0 13294 [59663.443955] 59672.477 D/TA: TA_deserialize_auth_set:215 indirect_data_size:0 13295 [59663.450297] 59672.483 D/TA: TA_deserialize_auth_set:223 indirect_base:0xc00fef30 13296 [59663.455409] 59672.489 D/TA: TA_deserialize_auth_set:242 elem cnt:9 13297 [59663.461651] 59672.494 D/TA: TA_deserialize_auth_set:252 elem serialized size:80 13298 [59663.467535] 59672.500 D/TA: TA_deserialize_auth_set:254 param_set->length:9 13299 [59663.473000] 59672.506 D/TA: param_deserialize:113 param tag:0x30000003//KM_TAG_KEY_SIZE 13300 [59663.478457] 59672.512 D/TA: param_deserialize:113 param tag:0x10000002//KM_TAG_ALGORITHM 13302 [59663.483719] 59672.517 D/TA: param_deserialize:113 param tag:0x20000001//KM_TAG_PURPOSE 13303 [59663.488998] 59672.528 D/TA: param_deserialize:113 param tag:0x20000001//KM_TAG_PURPOSE 13304 [59663.499864] 59672.533 D/TA: param_deserialize:113 param tag:0x20000004//KM_TAG_BLOCK_MODE 13305 [59663.505327] 59672.539 D/TA: param_deserialize:113 param tag:0x20000006//KM_TAG_PADDING 13306 [59663.510775] 59672.544 D/TA: param_deserialize:113 param tag:0xa00001f6//KM_TAG_USER_SECURE_ID 13307 [59663.516228] 59672.549 D/TA: param_deserialize:113 param tag:0x100001f8//KM_TAG_USER_AUTH_TYPE 13308 [59663.521683] 59672.555 D/TA: param_deserialize:113 param tag:0x600002bd//KM_TAG_CREATION_DATETIME
generateKey的response:
360 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: dump_data data_len = 504, count = 32 361 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [000] 00 00 00 00 70 01 00 00 12 65 0e 94 a9 7f 3d 74 //ErrorCode,KM_ERROR_OK,值为0,前面4个字节为keyblob的size,0x0170=368 362 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [001] 8c 89 f9 bb 2c 06 f6 49 29 53 17 85 37 d6 c6 ef 363 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [002] 42 ff ba 9e d9 a4 a2 a2 8d ed 78 92 ee ea 24 d6 364 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [003] fa a8 f2 83 05 84 58 a0 ac b3 ae a8 de 31 08 79 365 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [004] 89 b9 8c c5 84 b4 81 77 99 f3 d9 74 c7 81 75 0b 366 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [005] 49 54 98 56 7b b8 e6 21 6a 1f a0 79 42 51 4d fe 367 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [006] 6d 00 c3 b9 02 1c bd f2 62 26 39 23 f0 72 fa 12 368 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [007] 6c 52 6b 7b ac 10 a5 f8 4b ad a7 c5 ac 44 b1 f1 369 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [008] 38 d3 70 7b ad 0d ce 80 fd a4 df 66 9d 09 81 1e 370 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [009] 6c af 03 3f bb 38 93 53 1b 7e 38 2b 25 6f 52 ad 371 09-13 22:25:56.324 298 298 D OpteeKeymaster_ipc: [00a] b8 74 7b 01 f4 6b 9a 55 a6 9f e3 82 a0 d9 aa 98 372 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [00b] 1d a7 8e 2e 9f 9a 9e 64 57 5e 8b bd 60 7c b3 5d 373 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [00c] 5c e0 55 f3 99 24 af d3 fb 72 1d 71 66 7b ef 29 374 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [00d] 9d 04 86 7d bb ed 3d 90 89 47 87 91 88 c9 0f 7f 375 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [00e] 62 50 ae cc 5f cb ca 88 18 27 df 11 8f 72 98 09 376 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [00f] cb 41 ac ae 8c c2 e3 50 14 f9 5e 59 af 31 79 78 377 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [010] df a5 e2 84 4e 13 39 3e 2f 10 79 ff 12 bc cb 0a 378 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [011] 7d b5 89 1a 23 0e 32 6d 16 fc ed 73 82 4b 00 05 379 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [012] ef 3e 68 ba a5 7a f5 cf bf 44 e4 e6 b9 0a bf ec 380 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [013] 3f 56 af ef ab 1d fb f3 00 36 7f d0 79 16 02 63 381 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [014] 6a 07 76 3f cb 05 3b c9 c9 f0 c7 a5 fb 25 f7 24 382 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [015] c8 02 25 65 27 a4 3b cd 8d 1e 97 7c cd 68 03 3d 383 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [016] 19 ae 61 5d 7f f7 19 c0 22 24 a5 7e 3a d0 48 30 384 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [017] 72 1f d7 c9 0e 94 bf af 00 00 00 00 0a 00 00 00 //keyblob到这里结束(绿底色部分),接下来是hw_enforced和sw_enforced,indirect_data_size为0,elems count为0x0a 385 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [018] 54 00 00 00 03 00 00 30 80 00 00 00 02 00 00 10 //element size为0x54=84. tag:KM_TAG_KEY_SIZE;tag:KM_TAG_ALGORITHM 386 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [019] 20 00 00 00 01 00 00 20 00 00 00 00 01 00 00 20 //tag: KM_TAG_PURPOSE,两个 387 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [01a] 01 00 00 00 04 00 00 20 02 00 00 00 06 00 00 20 //tag: KM_TAG_BLOCK_MODE, tag: KM_TAG_PADDING 388 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [01b] 40 00 00 00 f6 01 00 a0 2c 53 35 b7 b2 a3 42 57 //tag: KM_TAG_USER_SECURE_ID,值占8个字节 389 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [01c] be 02 00 10 00 00 00 00 c1 02 00 30 b0 ad 01 00 //tag: KM_TAG_ORIGIN, tag: KM_TAG_OS_VERSION 390 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [01d] c2 02 00 30 43 16 03 00 00 00 00 00 02 00 00 00 //tag: KM_TAG_OS_PATCHLEVEL, 到黄底色部分结束,sw_enforced类似,前4个字节为0,表示indirect_data_size,element count为2,element size为0x14 391 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [01e] 14 00 00 00 f8 01 00 10 02 00 00 00 bd 02 00 60 //tag:KM_TAG_USER_AUTH_TYPE,tag:KM_TAG_CREATION_DATETIME 392 09-13 22:25:56.325 298 298 D OpteeKeymaster_ipc: [01f] 3e 70 03 00 00 00 00 00
返回值为3部分:
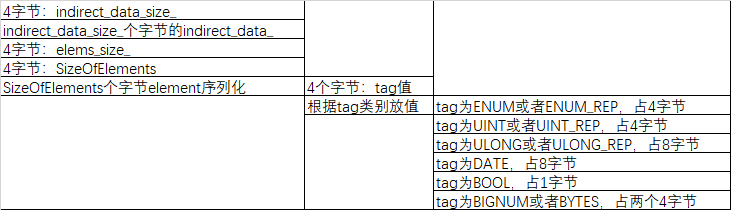
ErrorCode:占4个字节
keyBlob:4个字节的size + size长度的数据
KeyCharacteristics,参考上述注释部分
KeyCharacteristics的序列化大致如下:
其他tee方案的对比log:
其他厂商的ctsverifier测试log:
082 09-15 17:47:32.886 315 315 D bpkm: [000] 00 00 00 00 4b 01 00 00 01 00 00 00 10 10 28 96 //keyblob size为0x014b = 331 083 09-15 17:47:32.886 315 315 D bpkm: [001] de 8b dc a7 78 d5 d2 cf a9 74 5e 82 8e 3c cf 9f 084 09-15 17:47:32.886 315 315 D bpkm: [002] 0f b0 eb 19 b5 d0 ea 29 ff a4 92 00 7a 84 06 c0 085 09-15 17:47:32.886 315 315 D bpkm: [003] c7 be a9 c2 e7 5a 6b 2d 0d 11 69 e0 e3 4a 04 b7 086 09-15 17:47:32.886 315 315 D bpkm: [004] f7 0e e4 54 1f 8a c7 2e b0 69 6b 38 c8 23 35 63 087 09-15 17:47:32.887 315 315 D bpkm: [005] 8d 66 9b f2 58 68 d6 3e 6a ac 08 5a f2 67 87 06 091 09-15 17:47:32.887 315 315 D bpkm: [006] 19 c8 2a 5f c9 a3 7c 53 a3 42 e9 e5 ae 8d 7b 75 092 09-15 17:47:32.887 315 315 D bpkm: [007] 8d 58 56 3b c0 f6 03 ab 3e 2d 73 7c 66 12 99 1e 093 09-15 17:47:32.887 315 315 D bpkm: [008] 89 ed 1a 9d 10 6b 28 61 58 a5 03 14 6f 74 e6 fe 094 09-15 17:47:32.887 315 315 D bpkm: [009] 2a af 21 5b 3c 63 42 91 7c be 7f cd 52 be 3e 75 095 09-15 17:47:32.887 315 315 D bpkm: [00a] f7 81 7e cc 2e 42 50 2e 54 95 1a 2a 6c 08 0d 53 096 09-15 17:47:32.887 315 315 D bpkm: [00b] 4c 41 e5 87 cd 60 6e c6 b8 88 69 80 ce aa 07 17 097 09-15 17:47:32.887 315 315 D bpkm: [00c] a2 fa d6 03 fd c6 46 2c 52 43 f5 bc 6e 09 d3 8b 098 09-15 17:47:32.887 315 315 D bpkm: [00d] f7 a1 56 5a 38 0d 2a 30 28 4f 7a 0d 69 98 6d 2f 099 09-15 17:47:32.887 315 315 D bpkm: [00e] 9b 5b 4a e0 d2 53 6e 47 1a 21 b7 cd 92 35 88 1d 100 09-15 17:47:32.888 315 315 D bpkm: [00f] 4f 3e dd de b4 04 e9 32 12 5a 24 24 ba 67 b8 47 101 09-15 17:47:32.888 315 315 D bpkm: [010] f5 ac 57 af 8b 73 61 46 bf 0f f9 c1 70 ec 1b 51 102 09-15 17:47:32.888 315 315 D bpkm: [011] 1a 37 9b e2 b8 b8 f4 5d e9 f8 14 80 de 4e 52 c5 103 09-15 17:47:32.888 315 315 D bpkm: [012] de 4f 5b 8a 27 71 12 64 12 60 97 0a d0 84 1d 40 104 09-15 17:47:32.888 315 315 D bpkm: [013] be 0e 3f d1 b6 3e 23 6c 3d 61 b7 7a cc b4 e5 91 105 09-15 17:47:32.888 315 315 D bpkm: [014] 5b 04 a3 f9 b4 1c ad 5d 3c c8 b1 4f 02 e5 db c4 106 09-15 17:47:32.888 315 315 D bpkm: [015] bf 6d f6 00 00 00 00 0b 00 00 00 5c 00 00 00 03 //keyblob到此结束(绿底色部分),element cout为0xb,11,长度为0x5c=92 107 09-15 17:47:32.888 315 315 D bpkm: [016] 00 00 30 80 00 00 00 02 00 00 10 20 00 00 00 01 //tag:KM_TAG_KEY_SIZE, tag:KM_TAG_ALGORITHM 108 09-15 17:47:32.889 315 315 D bpkm: [017] 00 00 20 00 00 00 00 01 00 00 20 01 00 00 00 04 //tag: KM_TAG_PURPOSE,两个 109 09-15 17:47:32.889 315 315 D bpkm: [018] 00 00 20 02 00 00 00 06 00 00 20 40 00 00 00 f6 //tag: KM_TAG_BLOCK_MODE, tag: KM_TAG_PADDING 110 09-15 17:47:32.889 315 315 D bpkm: [019] 01 00 a0 4c 8c 2d c1 92 6d b1 f8 f8 01 00 10 02 //tag: KM_TAG_USER_SECURE_ID,值占8个字节; tag:KM_TAG_USER_AUTH_TYPE 111 09-15 17:47:32.889 315 315 D bpkm: [01a] 00 00 00 be 02 00 10 00 00 00 00 c1 02 00 30 b0 //tag: KM_TAG_ORIGIN; tag: KM_TAG_OS_VERSION 112 09-15 17:47:32.889 315 315 D bpkm: [01b] ad 01 00 c2 02 00 30 45 16 03 00 00 00 00 00 01 //1个element,size为0x0c 113 09-15 17:47:32.889 315 315 D bpkm: [01c] 00 00 00 0c 00 00 00 bd 02 00 60 20 0b 3d 98 8a //tag: KM_TAG_CREATION_DATETIME 114 09-15 17:47:32.889 315 315 D bpkm: [01d] 01 00 00
差异分析及修改:
optee和对比log的差异,在于hw_enforced和sw_enforced的element count不一样。
在optee中,tag:KM_TAG_USER_AUTH_TYPE被打包到sw_enforced中。
而对比log中,tag:KM_TAG_USER_AUTH_TYPE被打包到hw_enforced中了。
此处修改keymaster ta中代码,TA_fill_characteristics函数中针对tag:KM_TAG_USER_AUTH_TYPE做下调整。
Begin函数:
hardware/interfaces/keymaster/3.0/IKeymasterDevice.hal
/** * Begins a cryptographic operation using the specified key. If all is well, begin() will return * ErrorCode::OK and create an operation handle which must be passed to subsequent calls to * update(), finish() or abort(). * * It is critical that each call to begin() be paired with a subsequent call to finish() or * abort(), to allow the keymaster implementation to clean up any internal operation state. * Failure to do this may leak internal state space or other internal resources and may * eventually cause begin() to return ErrorCode::TOO_MANY_OPERATIONS when it runs out of space * for operations. Any result other than ErrorCode::OK from begin(), update() or finish() * implicitly aborts the operation, in which case abort() need not be called (and will return * ErrorCode::INVALID_OPERATION_HANDLE if called). * * @param purpose The purpose of the operation, one of KeyPurpose::ENCRYPT, KeyPurpose::DECRYPT, * KeyPurpose::SIGN or KeyPurpose::VERIFY. Note that for AEAD modes, encryption and * decryption imply signing and verification, respectively, but must be specified as * KeyPurpose::ENCRYPT and KeyPurpose::DECRYPT. * * @param keyBlob The opaque key descriptor returned by generateKey() or importKey(). The key * must have a purpose compatible with purpose and all of its usage requirements * must be satisfied, or begin() will return an appropriate error code. * * @param inParams Additional parameters for the operation. This is typically used to provide * authentication data, with Tag::AUTH_TOKEN. If Tag::APPLICATION_ID or * Tag::APPLICATION_DATA were provided during generation, they must be provided * here, or the operation will fail with ErrorCode::INVALID_KEY_BLOB. For operations * that require a nonce or IV, on keys that were generated with Tag::CALLER_NONCE, * inParams may contain a tag Tag::NONCE. * * @return error See the ErrorCode enum in types.hal. * * @return outParams Output parameters. Used to return additional data from the operation * initialization, notably to return the IV or nonce from operations that generate * an IV or nonce. * * @return operationHandle The newly-created operation handle which must be passed to update(), * finish() or abort(). */ begin(KeyPurpose purpose, vec<uint8_t> key, vec<KeyParameter> inParams) generates(ErrorCode error, vec<KeyParameter> outParams, OperationHandle operationHandle);
Begin函数的序列化:
uint8_t* BeginOperationRequest::Serialize(uint8_t* buf, const uint8_t* end) const { buf = append_uint32_to_buf(buf, end, purpose); buf = serialize_key_blob(key_blob, buf, end); return additional_params.Serialize(buf, end); } static uint8_t* serialize_key_blob(const keymaster_key_blob_t& key_blob, uint8_t* buf, const uint8_t* end) { return append_size_and_data_to_buf(buf, end, key_blob.key_material, key_blob.key_material_size); } uint8_t* AuthorizationSet::Serialize(uint8_t* buf, const uint8_t* end) const { buf = append_size_and_data_to_buf(buf, end, indirect_data_, indirect_data_size_); buf = append_uint32_to_buf(buf, end, elems_size_); buf = append_uint32_to_buf(buf, end, SerializedSizeOfElements()); for (size_t i = 0; i < elems_size_; ++i) { buf = serialize(elems_[i], buf, end, indirect_data_); } return buf; }
Begin操作的Request log:
433 09-13 22:25:56.399 298 298 D OpteeKeymaster_ipc: optee_keymaster_call 273 4 = KM_BEGIN_OPERATION 434 09-13 22:25:56.399 298 298 D OpteeKeymaster_ipc: dump_data data_len = 493, count = 31 435 09-13 22:25:56.399 298 298 D OpteeKeymaster_ipc: [000] 00 00 00 00 70 01 00 00 12 65 0e 94 a9 7f 3d 74 //purpose, keysize:0x0170 436 09-13 22:25:56.399 298 298 D OpteeKeymaster_ipc: [001] 8c 89 f9 bb 2c 06 f6 49 29 53 17 85 37 d6 c6 ef 437 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [002] 42 ff ba 9e d9 a4 a2 a2 8d ed 78 92 ee ea 24 d6 438 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [003] fa a8 f2 83 05 84 58 a0 ac b3 ae a8 de 31 08 79 439 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [004] 89 b9 8c c5 84 b4 81 77 99 f3 d9 74 c7 81 75 0b 440 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [005] 49 54 98 56 7b b8 e6 21 6a 1f a0 79 42 51 4d fe 441 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [006] 6d 00 c3 b9 02 1c bd f2 62 26 39 23 f0 72 fa 12 442 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [007] 6c 52 6b 7b ac 10 a5 f8 4b ad a7 c5 ac 44 b1 f1 443 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [008] 38 d3 70 7b ad 0d ce 80 fd a4 df 66 9d 09 81 1e 444 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [009] 6c af 03 3f bb 38 93 53 1b 7e 38 2b 25 6f 52 ad 445 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [00a] b8 74 7b 01 f4 6b 9a 55 a6 9f e3 82 a0 d9 aa 98 446 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [00b] 1d a7 8e 2e 9f 9a 9e 64 57 5e 8b bd 60 7c b3 5d 447 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [00c] 5c e0 55 f3 99 24 af d3 fb 72 1d 71 66 7b ef 29 448 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [00d] 9d 04 86 7d bb ed 3d 90 89 47 87 91 88 c9 0f 7f 449 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [00e] 62 50 ae cc 5f cb ca 88 18 27 df 11 8f 72 98 09 450 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [00f] cb 41 ac ae 8c c2 e3 50 14 f9 5e 59 af 31 79 78 451 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [010] df a5 e2 84 4e 13 39 3e 2f 10 79 ff 12 bc cb 0a 452 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [011] 7d b5 89 1a 23 0e 32 6d 16 fc ed 73 82 4b 00 05 453 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [012] ef 3e 68 ba a5 7a f5 cf bf 44 e4 e6 b9 0a bf ec 454 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [013] 3f 56 af ef ab 1d fb f3 00 36 7f d0 79 16 02 63 455 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [014] 6a 07 76 3f cb 05 3b c9 c9 f0 c7 a5 fb 25 f7 24 456 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [015] c8 02 25 65 27 a4 3b cd 8d 1e 97 7c cd 68 03 3d 457 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [016] 19 ae 61 5d 7f f7 19 c0 22 24 a5 7e 3a d0 48 30 458 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [017] 72 1f d7 c9 0e 94 bf af 45 00 00 00 00 00 00 00 //indirect_data_size_=0x45 459 09-13 22:25:56.400 298 298 D OpteeKeymaster_ipc: [018] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 460 09-13 22:25:56.401 298 298 D OpteeKeymaster_ipc: [019] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 461 09-13 22:25:56.401 298 298 D OpteeKeymaster_ipc: [01a] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 462 09-13 22:25:56.401 298 298 D OpteeKeymaster_ipc: [01b] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 463 09-13 22:25:56.401 298 298 D OpteeKeymaster_ipc: [01c] 00 04 00 00 00 24 00 00 00 02 00 00 10 20 00 00 //element coucnt=0x04,element size=0x24,tag:KM_TAG_ALGORITHM 464 09-13 22:25:56.401 298 298 D OpteeKeymaster_ipc: [01d] 00 04 00 00 20 02 00 00 00 06 00 00 20 40 00 00 //tag: KM_TAG_BLOCK_MODE; tag: KM_TAG_PADDING 465 09-13 22:25:56.401 298 298 D OpteeKeymaster_ipc: [01e] 00 ea 03 00 90 45 00 00 00 00 00 00 00 //tag: KM_TAG_AUTH_TOKEN
对比log:
17:47:32.929 315 315 D bpkm: dump_data data_len = 456, count = 29 17:47:32.929 315 315 D bpkm: [000] 00 00 00 00 4b 01 00 00 01 00 00 00 10 10 28 96 //keysize = 0x014b 17:47:32.929 315 315 D bpkm: [001] de 8b dc a7 78 d5 d2 cf a9 74 5e 82 8e 3c cf 9f 17:47:32.929 315 315 D bpkm: [002] 0f b0 eb 19 b5 d0 ea 29 ff a4 92 00 7a 84 06 c0 17:47:32.930 315 315 D bpkm: [003] c7 be a9 c2 e7 5a 6b 2d 0d 11 69 e0 e3 4a 04 b7 17:47:32.930 315 315 D bpkm: [004] f7 0e e4 54 1f 8a c7 2e b0 69 6b 38 c8 23 35 63 17:47:32.930 315 315 D bpkm: [005] 8d 66 9b f2 58 68 d6 3e 6a ac 08 5a f2 67 87 06 17:47:32.930 315 315 D bpkm: [006] 19 c8 2a 5f c9 a3 7c 53 a3 42 e9 e5 ae 8d 7b 75 17:47:32.930 315 315 D bpkm: [007] 8d 58 56 3b c0 f6 03 ab 3e 2d 73 7c 66 12 99 1e 17:47:32.930 315 315 D bpkm: [008] 89 ed 1a 9d 10 6b 28 61 58 a5 03 14 6f 74 e6 fe 17:47:32.930 315 315 D bpkm: [009] 2a af 21 5b 3c 63 42 91 7c be 7f cd 52 be 3e 75 17:47:32.930 315 315 D bpkm: [00a] f7 81 7e cc 2e 42 50 2e 54 95 1a 2a 6c 08 0d 53 17:47:32.930 315 315 D bpkm: [00b] 4c 41 e5 87 cd 60 6e c6 b8 88 69 80 ce aa 07 17 17:47:32.930 315 315 D bpkm: [00c] a2 fa d6 03 fd c6 46 2c 52 43 f5 bc 6e 09 d3 8b 17:47:32.931 315 315 D bpkm: [00d] f7 a1 56 5a 38 0d 2a 30 28 4f 7a 0d 69 98 6d 2f 17:47:32.931 315 315 D bpkm: [00e] 9b 5b 4a e0 d2 53 6e 47 1a 21 b7 cd 92 35 88 1d 17:47:32.931 315 315 D bpkm: [00f] 4f 3e dd de b4 04 e9 32 12 5a 24 24 ba 67 b8 47 17:47:32.931 315 315 D bpkm: [010] f5 ac 57 af 8b 73 61 46 bf 0f f9 c1 70 ec 1b 51 17:47:32.931 315 315 D bpkm: [011] 1a 37 9b e2 b8 b8 f4 5d e9 f8 14 80 de 4e 52 c5 17:47:32.931 315 315 D bpkm: [012] de 4f 5b 8a 27 71 12 64 12 60 97 0a d0 84 1d 40 17:47:32.931 315 315 D bpkm: [013] be 0e 3f d1 b6 3e 23 6c 3d 61 b7 7a cc b4 e5 91 17:47:32.931 315 315 D bpkm: [014] 5b 04 a3 f9 b4 1c ad 5d 3c c8 b1 4f 02 e5 db c4 17:47:32.931 315 315 D bpkm: [015] bf 6d f6 45 00 00 00 00 00 00 00 00 00 00 00 00 //indirect_data_size_=0x45 17:47:32.931 315 315 D bpkm: [016] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 17:47:32.931 315 315 D bpkm: [017] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 17:47:32.932 315 315 D bpkm: [018] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 17:47:32.932 315 315 D bpkm: [019] 00 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 17:47:32.932 315 315 D bpkm: [01a] 24 00 00 00 02 00 00 10 20 00 00 00 04 00 00 20 17:47:32.932 315 315 D bpkm: [01b] 02 00 00 00 06 00 00 20 40 00 00 00 ea 03 00 90 17:47:32.932 315 315 D bpkm: [01c] 45 00 00 00 00 00 00 00
begin函数的response:
uint8_t* BeginOperationResponse::NonErrorSerialize(uint8_t* buf, const uint8_t* end) const { buf = append_uint64_to_buf(buf, end, op_handle);//8个字节的operation handle if (message_version > 0) buf = output_params.Serialize(buf, end); return buf; } uint8_t* AuthorizationSet::Serialize(uint8_t* buf, const uint8_t* end) const { buf = append_size_and_data_to_buf(buf, end, indirect_data_, indirect_data_size_);//4个字节存indirect_data_size_,再有indirect_data_size_大小的数据 buf = append_uint32_to_buf(buf, end, elems_size_);//element count,4个字节 buf = append_uint32_to_buf(buf, end, SerializedSizeOfElements());//element size,4个字节 for (size_t i = 0; i < elems_size_; ++i) { buf = serialize(elems_[i], buf, end, indirect_data_);//4个字节tag,value根据tag类型来,一般是4个字节 } return buf; }
optee log:
1500 09-12 17:35:26.840 301 301 D OpteeKeymaster_ipc: response size = 8192, op.params[1].tmpref.size = 52 1501 09-12 17:35:26.840 301 301 D OpteeKeymaster_ipc: dump_data data_len = 52, count = 4 1502 09-12 17:35:26.840 301 301 D OpteeKeymaster_ipc: [000] 00 00 00 00 1c d8 b5 56 1c b4 50 99 10 00 00 00 1503 09-12 17:35:26.840 301 301 D OpteeKeymaster_ipc: [001] 9e 15 be 6c b1 a3 ed 4c 7b e3 15 9a 91 cc 22 d0 1504 09-12 17:35:26.840 301 301 D OpteeKeymaster_ipc: [002] 01 00 00 00 0c 00 00 00 e9 03 00 90 10 00 00 00 1505 09-12 17:35:26.840 301 301 D OpteeKeymaster_ipc: [003] 00 00 00 00
对比机log:
264 09-15 17:47:32.974 315 315 D bpkm: response size = 52 265 09-15 17:47:32.974 315 315 D bpkm: dump_data data_len = 52, count = 4 266 09-15 17:47:32.975 315 315 D bpkm: [000] 00 00 00 00 15 70 a9 26 e5 21 b9 9e 10 00 00 00 267 09-15 17:47:32.975 315 315 D bpkm: [001] 15 6c 49 0b 0f 56 22 77 4f 2b 4c f8 58 8e 21 74 268 09-15 17:47:32.975 315 315 D bpkm: [002] 01 00 00 00 0c 00 00 00 e9 03 00 90 10 00 00 00//KM_TAG_NONCE 269 09-15 17:47:32.975 315 315 D bpkm: [003] 00 00 00 00
异常log分析及修改:
9381 [ 262.191407] 0268.856 D/TA: TA_InvokeCommandEntryPoint:1612 KM_BEGIN 9498 [ 262.938479] 0269.602 D/TA: TA_check_params:678 KM_TAG_USER_SECURE_ID, suid_count = 1 9513 [ 263.033112] 0269.696 E/TA: TA_check_params:1058 Authentication failed. Key can not be used 9514 [ 263.037746] 0269.703 D/TA: TA_serialize_rsp_err:459 res: -26
在android官网中,对begin操作的密钥强制授权部分的说明如下:https://source.android.com/docs/security/features/keystore/implementer-ref?hl=zh-cn#begin
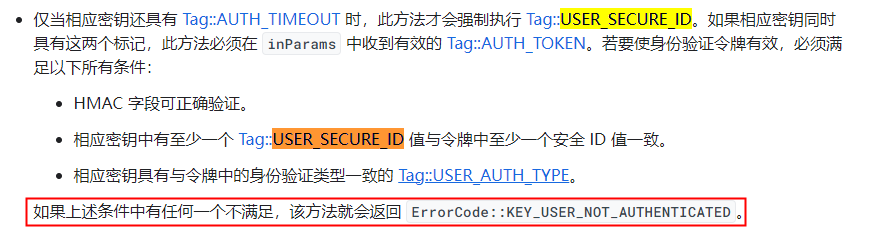
红色框内的部分,我的理解是针对tag::AUTH_TIMEOUT和tag::USER_SECURE_ID两者完全存在的情况。
parameters.c中的校验部分,下面红色字体,在我看来属于多余的部分。因为do_auth赋值为true之后,会有后续的update和finish进行校验。
所以把红色部分给注释掉了。
if (!no_auth_req) { if (auth_timeout == UNDEFINED && suid_count > 0) *do_auth = true; if (suid_count > 0 && auth_timeout != UNDEFINED) { res = TA_check_auth_token(suid, suid_count, auth_type, &auth_token); if (res != KM_ERROR_OK) goto out_cp; } else { EMSG("Authentication failed. Key can not be used"); res = KM_ERROR_KEY_USER_NOT_AUTHENTICATED; goto out_cp; } }
update函数:
/** * Provides data to, and possibly receives output from, an ongoing cryptographic operation begun * with begin(). * * If operationHandle is invalid, update() will return ErrorCode::INVALID_OPERATION_HANDLE. * * update() may not consume all of the data provided in the data buffer. update() will return * the amount consumed in inputConsumed. The caller may provide the unconsumed data in a * subsequent call. * * @param operationHandle The operation handle returned by begin(). * * @param inParams Additional parameters for the operation. For AEAD modes, this is used to * specify Tag::ADDITIONAL_DATA. Note that additional data may be provided in * multiple calls to update(), but only until input data has been provided. * * @param input Data to be processed, per the parameters established in the call to begin(). * Note that update() may or may not consume all of the data provided. See * inputConsumed. * * @return error See the ErrorCode enum in types.hal. * * @return inputConsumed Amount of data that was consumed by update(). If this is less than the * amount provided, the caller may provide the remainder in a subsequent call to * update() or finish(). * * @return outParams Output parameters, used to return additional data from the operation The * caller takes ownership of the output parameters array and must free it with * keymaster_free_param_set(). * * @return output The output data, if any. */ update(OperationHandle operationHandle, vec<KeyParameter> inParams, vec<uint8_t> input) generates(ErrorCode error, uint32_t inputConsumed, vec<KeyParameter> outParams, vec<uint8_t> output);
序列化:
uint8_t* UpdateOperationRequest::Serialize(uint8_t* buf, const uint8_t* end) const { buf = append_uint64_to_buf(buf, end, op_handle);//8字节 buf = input.Serialize(buf, end); //4字节存长度len + 一段buffer,长度len if (message_version > 0) buf = additional_params.Serialize(buf, end); return buf; }
additional params:
uint8_t* AuthorizationSet::Serialize(uint8_t* buf, const uint8_t* end) const {
buf = append_size_and_data_to_buf(buf, end, indirect_data_, indirect_data_size_);//4字节 + buffer
buf = append_uint32_to_buf(buf, end, elems_size_);//4字节
buf = append_uint32_to_buf(buf, end, SerializedSizeOfElements());//4字节
for (size_t i = 0; i < elems_size_; ++i) {
buf = serialize(elems_[i], buf, end, indirect_data_);
}
return buf;
}
豆荚update log:
426 09-15 17:47:36.727 315 315 D bpkm: bp_keymaster_send 309 command: 8 = KM_UPDATE_OPERATION 427 09-15 17:47:36.727 315 315 D bpkm: dump_data data_len = 111, count = 7 428 09-15 17:47:36.727 315 315 D bpkm: [000] 15 70 a9 26 e5 21 b9 9e 06 00 00 00 01 02 03 04 //8个字节op handle,4个字节size,长度0x06 429 09-15 17:47:36.727 315 315 D bpkm: [001] 05 06 45 00 00 00 00 15 70 a9 26 e5 21 b9 9e 10 //4个字节,0x45=69,indirect_data_size大小为69 430 09-15 17:47:36.727 315 315 D bpkm: [002] d9 ed 35 07 be e8 40 4c 8c 2d c1 92 6d b1 f8 00 431 09-15 17:47:36.727 315 315 D bpkm: [003] 00 00 02 00 00 00 00 00 0f 05 c2 65 28 dc 68 b1 432 09-15 17:47:36.727 315 315 D bpkm: [004] cc b4 90 a9 8c f6 11 ae b9 30 21 0c 0e 6a df 45 433 09-15 17:47:36.727 315 315 D bpkm: [005] dd ec 41 39 98 29 13 52 8c e9 15 01 00 00 00 0c //indirect data到绿底色部分结束,黄底色部分表示1个element 434 09-15 17:47:36.727 315 315 D bpkm: [006] 00 00 00 ea 03 00 90 45 00 00 00 00 00 00 00 //长度0x0c,tag: 0x900003ea, KM_TAG_AUTH_TOKEN
optee update log:
14999 09-17 15:58:20.781 298 298 D OpteeKeymaster_ipc: optee_keymaster_call 273 8 = KM_UPDATE_OPERATION 15000 09-17 15:58:20.781 298 298 D OpteeKeymaster_ipc: dump_data data_len = 111, count = 7 15001 09-17 15:58:20.781 298 298 D OpteeKeymaster_ipc: [000] bb ca 63 b5 e2 9c 83 3c 06 00 00 00 01 02 03 04 15002 09-17 15:58:20.781 298 298 D OpteeKeymaster_ipc: [001] 05 06 45 00 00 00 00 bb ca 63 b5 e2 9c 83 3c 60 15003 09-17 15:58:20.781 298 298 D OpteeKeymaster_ipc: [002] b8 b0 e9 f4 89 3e ad 2c 53 35 b7 b2 a3 42 57 00 15004 09-17 15:58:20.781 298 298 D OpteeKeymaster_ipc: [003] 00 00 02 00 00 00 00 00 01 60 c3 76 b4 a9 e2 16 15005 09-17 15:58:20.782 298 298 D OpteeKeymaster_ipc: [004] 6d 55 8e 72 c0 db fe 93 27 48 63 dd fb 26 21 b0 15006 09-17 15:58:20.782 298 298 D OpteeKeymaster_ipc: [005] 7c 60 5c 2a 88 5c e6 3c 47 4d 7b 01 00 00 00 0c 15007 09-17 15:58:20.782 298 298 D OpteeKeymaster_ipc: [006] 00 00 00 ea 03 00 90 45 00 00 00 00 00 00 00
异常log分析及修改:
好了,begin操作不返回异常之后,update继续error了。
从log看,还是密钥授权的异常。
这块检查的就是secure user id和auth token中的user id了。
6305 [ 115.067453] 0124.097 D/TA: TA_InvokeCommandEntryPoint:1614 KM_UPDATE 6419 [ 115.783499] 0124.809 D/TA: TA_check_auth_token:409 suid_count = 1, auth_token->user_id = 0x8d72baed06c9b1de 6420 [ 115.789720] 0124.818 D/TA: TA_check_auth_token:411 suid[0] = 0x7044da77bd2f1066 6421 [ 115.797327] 0124.824 E/TA: TA_check_auth_token:418 Suid from auth token not in list of this key 6422 [ 115.802158] 0124.832 E/TA: TA_update:1309 Authentication failed 6423 [ 115.806729] 0124.837 D/TA: TA_serialize_rsp_err:483 res: -26
android官网的说明:https://source.android.com/docs/security/features/keystore/implementer-ref?hl=zh-cn#update
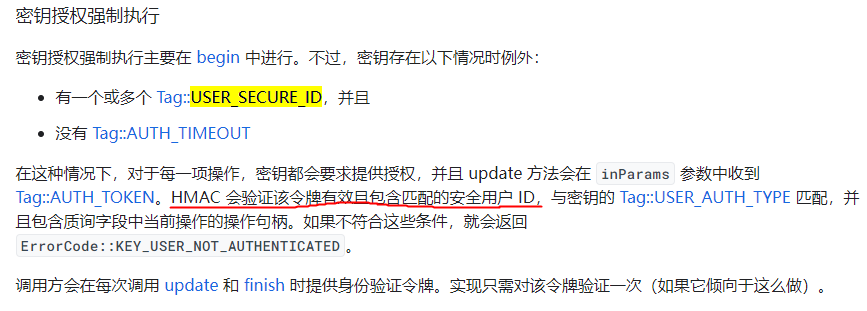
这里是说只有USER_SECURE_ID无AUTH_TIMEOUT时需要强制授权,在强制授权的时候,需要由HMAC来验证令牌有效。
auth.c中的授权检查是这么做的,在suid列表中去找和auth token的user id对应的值,找不到就认为异常。
这种检查,在官网的说明中是没有的。所以这里把红色部分注释掉了。
for (uint32_t i = 0; i < suid_count; i++) { if (auth_token->user_id == suid[i]) { in_list = true; break; } } if (!in_list) { EMSG("Suid from auth token not in list of this key"); return KM_ERROR_KEY_USER_NOT_AUTHENTICATED; }
在之后再跑就正常了。
总结:
问题解决耗时比较久。
主要分析手段是dump出keymaster关键操作的数据,结合keymaster hal中对数据的说明,一个字段一个字段进行含义梳理。
同时手上刚好有另一个tee解决方案,可以在CA侧加log进行对比。
另外就是android官网中对keymaster函数的说明。需要仔细阅读。
总体说来就是大胆修改,小心求证。ctsverifier验证通过之后,再把cts和vts都跑一遍。没问题的话,大致就问题不大了。


