Metasploit (二)
1、测试一台搭建的主机
msf > db_nmap -n -A 10.140.110.16
[*] Nmap: Starting Nmap 7.60 ( https://nmap.org ) at 2018-09-04 20:19 CST
[*] Nmap: Nmap scan report for 10.140.110.16
[*] Nmap: Host is up (0.093s latency).
[*] Nmap: Not shown: 982 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 135/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
[*] Nmap: 443/tcp open ssl/http VMware VirtualCenter Web service
[*] Nmap: |_http-title: Site doesn't have a title (text; charset=plain).
[*] Nmap: | ssl-cert: Subject: commonName=VMware/countryName=US
[*] Nmap: | Not valid before: 2017-03-12T12:26:45
[*] Nmap: |_Not valid after: 2018-03-12T12:26:45
[*] Nmap: |_ssl-date: 2018-09-04T12:23:06+00:00; +17s from scanner time.
[*] Nmap: | vmware-version:
[*] Nmap: | Server version: VMware Workstation 10.0.3
[*] Nmap: | Build: 1895310
[*] Nmap: | Locale version: INTL
[*] Nmap: | OS type: win32-x86
[*] Nmap: |_ Product Line ID: ws
[*] Nmap: 445/tcp open microsoft-ds Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
[*] Nmap: 514/tcp filtered shell
[*] Nmap: 902/tcp open nagios-nsca Nagios NSCA
[*] Nmap: 912/tcp open vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
[*] Nmap: 1688/tcp open msrpc Microsoft Windows RPC
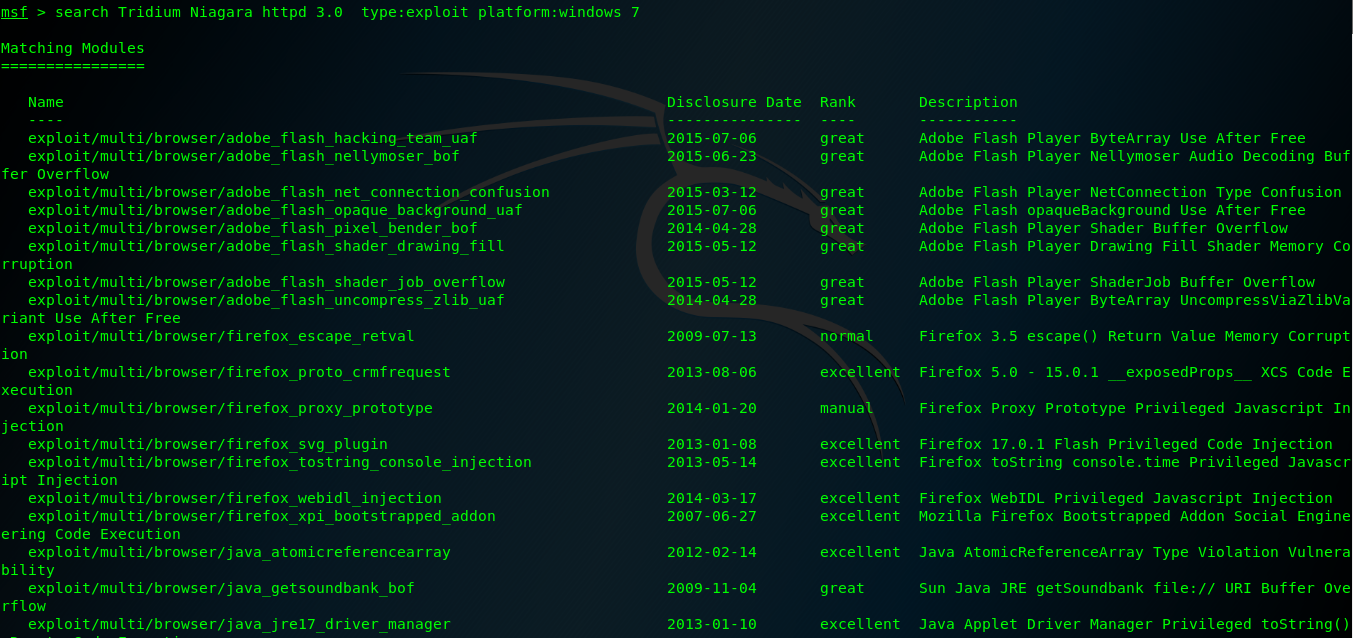
[*] Nmap: 3011/tcp open http Tridium Niagara httpd 3.0 (Platform: Windows 7)
[*] Nmap: | http-robots.txt: 1 disallowed entry
[*] Nmap: |_/
[*] Nmap: |_http-server-header: Niagara Web Server/3.0
[*] Nmap: |_http-title: Site doesn't have a title (text/html).
[*] Nmap: 3306/tcp open mysql MySQL (unauthorized)
[*] Nmap: 3389/tcp open ms-wbt-server?
[*] Nmap: 8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
[*] Nmap: |_ajp-methods: Failed to get a valid response for the OPTION request
[*] Nmap: 8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
[*] Nmap: |_http-favicon: Apache Tomcat
[*] Nmap: |_http-open-proxy: Proxy might be redirecting requests
[*] Nmap: |_http-server-header: Apache-Coyote/1.1
[*] Nmap: |_http-title: Apache Tomcat/7.0.37
[*] Nmap: 49152/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49153/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49154/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49156/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49163/tcp open msrpc Microsoft Windows RPC
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Microsoft Windows XP|7|2012
[*] Nmap: OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2012
[*] Nmap: OS details: Microsoft Windows XP SP3, Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012
[*] Nmap: Network Distance: 2 hops
[*] Nmap: Service Info: Host: MS-20160714YUJH; OS: Windows; Device: specialized; CPE: cpe:/o:microsoft:windows
[*] Nmap: Host script results:
[*] Nmap: |_clock-skew: mean: 17s, deviation: 0s, median: 16s
[*] Nmap: |_nbstat: NetBIOS name: MS-20160714YUJH, NetBIOS user: <unknown>, NetBIOS MAC: 34:97:f6:90:9e:c9 (Asustek Computer)
[*] Nmap: | smb-os-discovery:
[*] Nmap: | OS: Windows 7 Ultimate 7601 Service Pack 1 (Windows 7 Ultimate 6.1)
[*] Nmap: | OS CPE: cpe:/o:microsoft:windows_7::sp1
[*] Nmap: | Computer name: MS-20160714YUJH
[*] Nmap: | NetBIOS computer name: MS-20160714YUJH\x00
[*] Nmap: | Workgroup: WORKGROUP\x00
[*] Nmap: |_ System time: 2018-09-04T20:23:07+08:00
[*] Nmap: | smb-security-mode:
[*] Nmap: | account_used: guest
[*] Nmap: | authentication_level: user
[*] Nmap: | challenge_response: supported
[*] Nmap: |_ message_signing: disabled (dangerous, but default)
[*] Nmap: | smb2-security-mode:
[*] Nmap: | 2.02:
[*] Nmap: |_ Message signing enabled but not required
[*] Nmap: | smb2-time:
[*] Nmap: | date: 2018-09-04 20:23:06
[*] Nmap: |_ start_date: 2018-09-04 08:28:38
[*] Nmap: TRACEROUTE (using port 80/tcp)
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.18 ms 192.168.142.2
[*] Nmap: 2 0.14 ms 10.140.110.16
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 233.14 seconds
查询开启的服务
msf > service
[*] exec: service
Usage: service < option > | --status-all | [ service_name [ command | --full-restart ] ]
msf > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.140.110.16 135 tcp msrpc open Microsoft Windows RPC
10.140.110.16 139 tcp netbios-ssn open Microsoft Windows netbios-ssn
10.140.110.16 443 tcp ssl/http open VMware VirtualCenter Web service
10.140.110.16 445 tcp microsoft-ds open Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds workgroup: WORKGROUP
10.140.110.16 514 tcp shell filtered
10.140.110.16 902 tcp nagios-nsca open Nagios NSCA
10.140.110.16 912 tcp vmware-auth open VMware Authentication Daemon 1.0 Uses VNC, SOAP
10.140.110.16 1688 tcp msrpc open Microsoft Windows RPC
10.140.110.16 3011 tcp http open Tridium Niagara httpd 3.0 Platform: Windows 7
10.140.110.16 3306 tcp mysql open MySQL unauthorized
10.140.110.16 3389 tcp ms-wbt-server open
10.140.110.16 8009 tcp ajp13 open Apache Jserv Protocol v1.3
10.140.110.16 8080 tcp http open Apache Tomcat/Coyote JSP engine 1.1
10.140.110.16 49152 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49153 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49154 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49156 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49163 tcp msrpc open Microsoft Windows RPC
202.201.39.51 22 tcp ssh open OpenSSH 5.3 protocol 2.0
202.201.39.51 80 tcp http open Apache httpd 2.2.15 (CentOS)
202.201.39.51 135 tcp msrpc filtered
202.201.39.51 139 tcp netbios-ssn filtered
202.201.39.51 445 tcp microsoft-ds filtered
202.201.39.51 514 tcp shell filtered
202.201.39.51 3306 tcp mysql open MySQL unauthorized