All about Using Burp Suite
1、how to use burpsuite
I can't thank them enough for allowing us to test web application ,making sure they are secure against threats . if you ues it another way ,all duty afford yousleves.
this version is 2.0.04 before load running ,you should function the key burp-loader-keygen-jas502n,because the authentic burpsuite not cheap , besids ,burp offers many options for only 350USD per year . we can use burp differentiate the real vulnerabilities from the false ones.
2、if you use the perburpSuite ,you can you commands : java -jar -Xmx2G /[path ]/[burp.jar] fireStart
3、Visualizing the application structure using Burp Suite
The Burpsuite offers the following function :
Visualize , Scope 、 Search the web hindder contents 、 lists comments 、scripts 、analyze 、report
4、we can se the burp Proxy it as a man-in-the-middle between your browser and destination wen servers ,it let you intercept,inspect and modify the raw trafficc passing in the bouth directions.
take notes: if you penetration with the https website you should install Burp's CA cerficate .an follow

5、Crawling the web application using Burp Splider
ususlly speaking Spider the website there is therr ways :
the first: Manually crawing by use the Intruder tool ; the second Automatically Crawing by use Spider ; finally use the Discover Content tool
if you want a manual as follow (the aims is to find intersting directions )
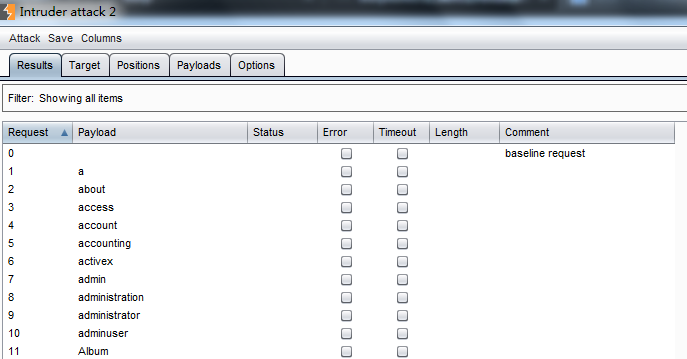
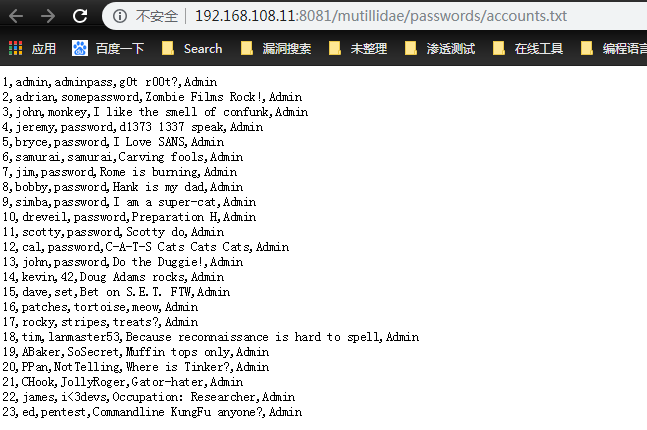
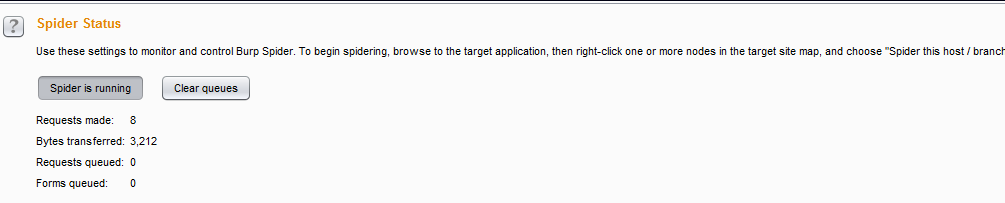
besides it , another way automated crawing and finding hidden spots,but ,you should be careful ,and it can cause the site to malfunction

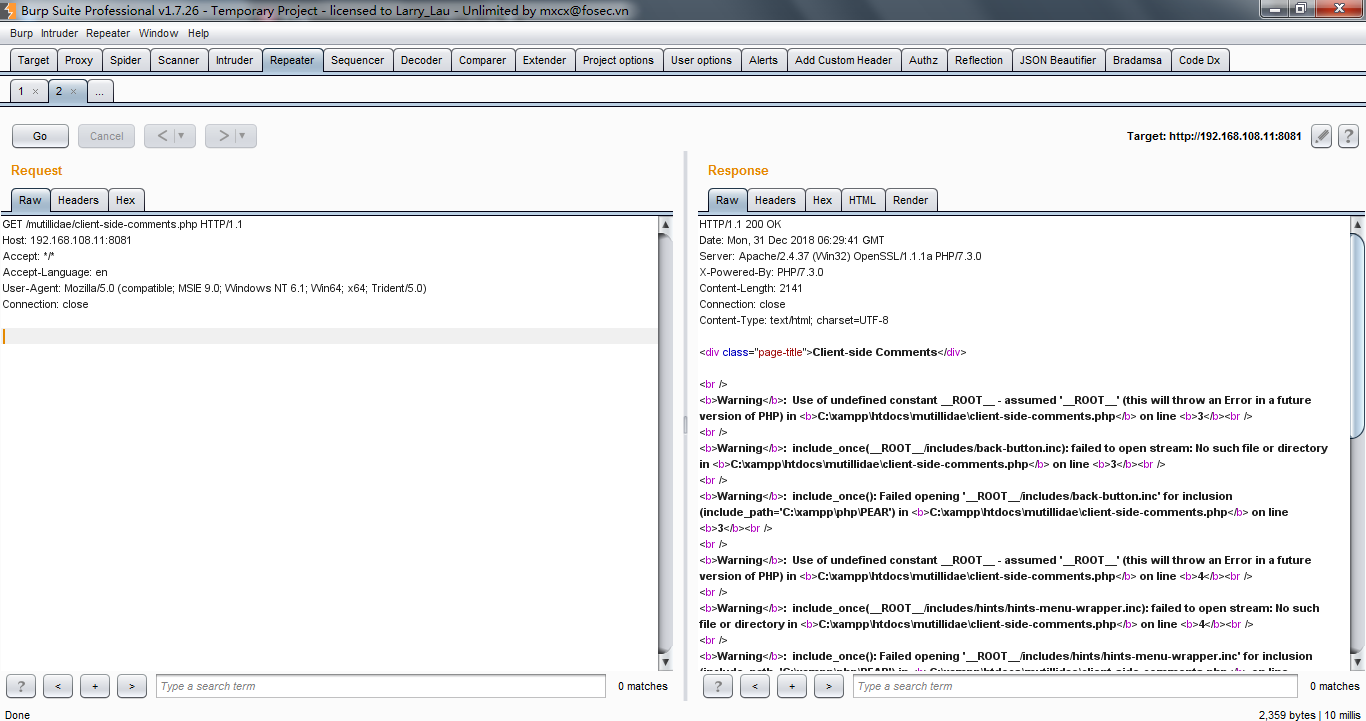
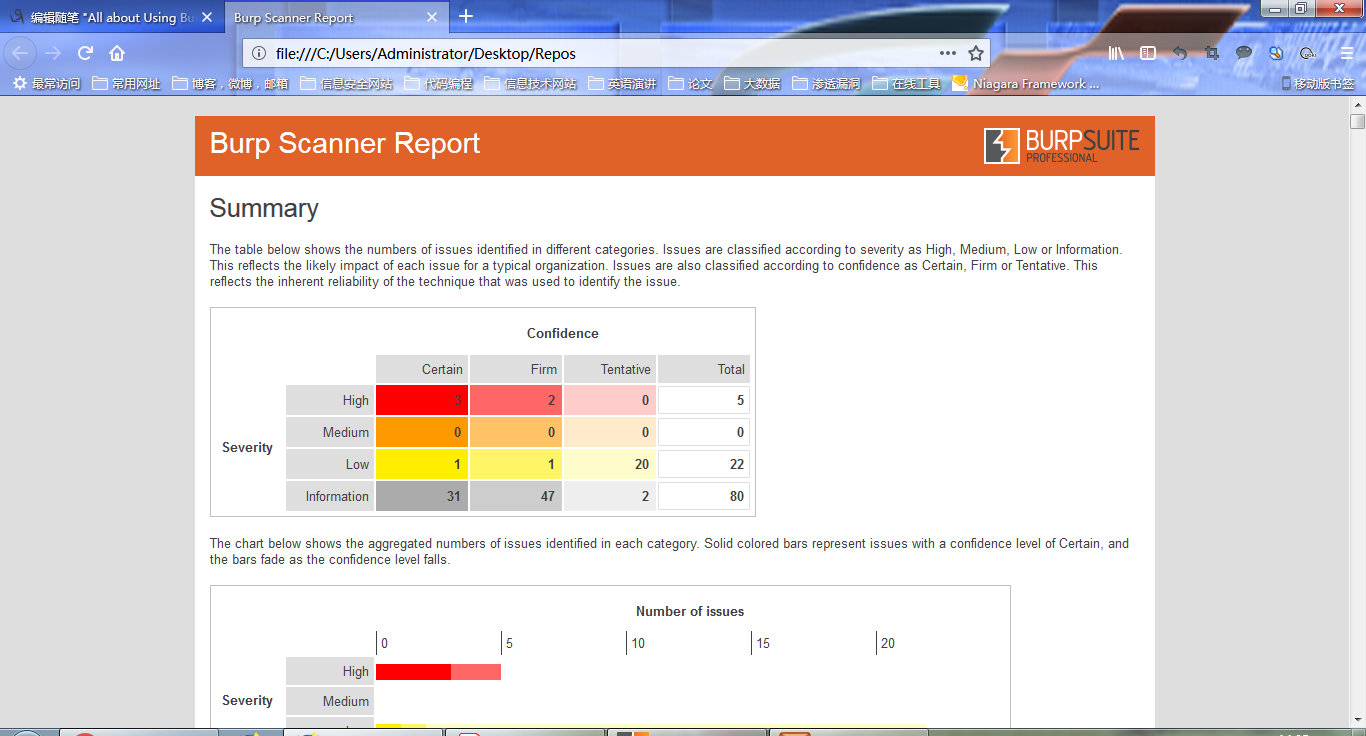
6、looking for the web vulnerablities using the Scanner,you can use the repeater to make sure that there's not a false positive
finally it's time to generate a report ,back the Target tab select the aim target host and selece issue,report the issue.
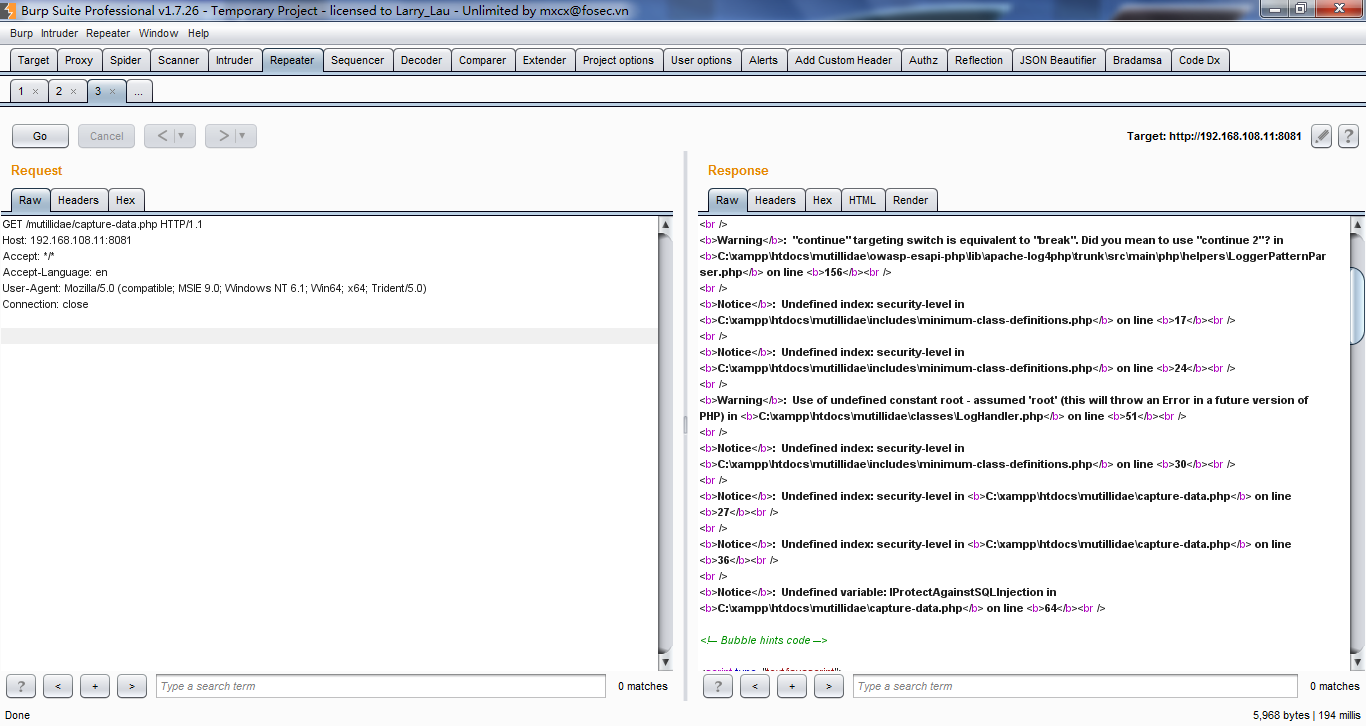
7、replaying web requests using the repeater tab
I usually check the parameter ,changing the parameter values (for example, testing input-based vulnerabilities )
8、Fuzzing web requesting using the Intruder tab
Brup inttruder use for automation and it can enumerate 、fuzz、and harvest data form the target web application . when i started using Burp ,the first thing that I lerned was to burp—force login credentials .
so let see the Intreder attack types:
Sniper ------> you can use it for only one payload ,you can use for fuzzing direction names.fuzzing the query string value,fuzzing the product name in the url
Battering Ram --------> this uses a single payload ,it alows sb palce the same payload into all defined position
Cluster bomb-------> this ones can use multiple payloads foe each position (maximum is 20 )
Pitchfork---------> this attack is used when an attack requries different ,but related, input to be inserted in multiple places in the request
9、installing third-party apps using Burp Extender
as this section if you use the proBurpSuite you can install third-party apps
but before you install ,you need configure a library an follow,(Some of these libraries need to be turned over )