打造自己的弱口令扫描工具
在内网检测中,弱口令扫描是必不可少的环节,选择一个好用的弱口令扫描工具,尤为重要。
我曾写过一款弱口令检测工具,经常有童鞋在后台询问关于iscan源代码的事情,但其实通过Python打造自己的弱口令扫描工具是一件非常简单的事情,无非就是将多个Python扫描脚本集成在一起。
今天,分享一些常见的端口服务扫描脚本,根据自己的需求来改写脚本,在实战中应用更切合实际游刃有余。
1、RDP 扫描模块
RDP协议相对复杂,想要使用Python实现RDP暴力破解,一直没找到比较简单实现的方式。后来,我在impacket 示例文件下找到了rdp_check.py,这个脚本可用于测试目标主机上的帐户是否有效。那么,通过它来改写Pyhton扫描脚本,就变得很简单。
demo代码有点长,这里就不贴了,演示截图如下:
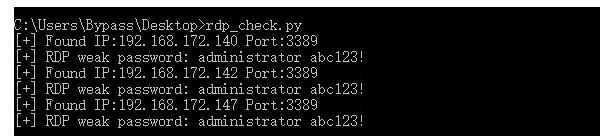
具体参考代码:
https://github.com/SecureAuthCorp/impacket/blob/master/examples/rdp_check.py2、SMB 扫描模块
用于检测共享文件夹和smb弱口令。
from impacket import smb def smb_login(ip,port,user,pwd): try: client = smb.SMB('*SMBSERVER',ip) client.login(user,pwd) flag ='[+] IPC$ weak password: '+user,pwd except: print '[-] checking for '+user,pwd+' fail'
3、FTP 扫描模块
FTP一般分为两种情况,匿名访问和弱口令。
import ftplib def ftp_anonymous(ip,port): try: ftp = ftplib.FTP() ftp.connect(ip,port,2) ftp.login() ftp.quit() print '[+] FTP login for anonymous' except: print '[-] checking for FTP anonymous fail' def ftp_login(ip,port,user,pwd): try: ftp = ftplib.FTP() ftp.connect(ip,port,2) ftp.login(user,pwd) ftp.quit() print '[+] FTP weak password: '+user,pwd except: print '[-] checking for '+user,pwd+' fail'
4、SSH 扫描模块
用于检测SSH弱口令。
import paramiko def ssh_login(ip,port,user,pwd): try: ssh = paramiko.SSHClient() ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy()) ssh.connect(ip,port,user,pwd,timeout=5) print '[+] SSH weak password: '+user,pwd ssh.close() except: print '[-] checking for '+user,pwd+' fail'
5、Telnet 扫描模块
模拟Telnet 登录验证过程,用于telnet弱口令的检测。
import telnetlib def telnet(ip,port,user,pwd): try: tn = telnetlib.Telnet(ip,timeout=5) tn.set_debuglevel(0) tn.read_until("login: ") tn.write(user + '\r\n') tn.read_until("assword: ") tn.write(pwd + '\r\n') result = tn.read_some() result = result+tn.read_some() if result.find('Login Fail')>0 or result.find('incorrect')>0: print "[-] Checking for "+user,pwd+" fail" else: print "[+] Success login for "+user,pwd tn.close()
6、MySQL 扫描模块
用于检测MySQL弱口令。
import MySQLdb def Mysql_login(ip,port,user,pwd): try: db = MySQLdb.connect(host=ip, user=user, passwd=pwd,port=port) print '[+] Mysql weak password: '+user,pwd db.close() except: print '[-] checking for '+user,pwd+' fail'
7、MSsql 扫描模块
用于检测MSSQL弱口令。
import pymssql def mssql_login(ip,port,user,pwd): try: db = pymssql.connect(host=ip,user=user,password=pwd,port=port) print '[+] MSsql weak password: '+user,pwd db.close() except: #pass print '[-] checking for '+user,pwd+' fail'
8、MongoDB 模块
用于检测MongoDB 匿名登录和弱口令。
from pymongo import MongoClient def mongodb(ip,port=27017): try: client = MongoClient(ip,port) db=client.local flag = db.collection_names() if flag: print "[+] Mongodb login for anonymous" except Exception, e: pass def mongodb_login(ip,port,user,pwd): try: client = MongoClient(ip,port) db_auth = client.admin flag = db_auth.authenticate(user, pwd) if flag == True: print '[+] Mongodb weak password: '+user,pwd except: print '[-] checking for '+user,pwd+' fail'
9、phpmyadmin 扫描模块
模拟http请求,检测phpmyadmin弱口令。
import requests def phpMyAdmin_login(ip,port,user,pwd): try: url = "http://"+ip+":"+str(port)+"/phpmyadmin/index.php" data={'pma_username':user,'pma_password':pwd} response = requests.post(url,data=data,timeout=5) result=response.content if result.find('name="login_form"')==-1: print '[+] find phpMyAdmin weak password in:'+url print '[+] find phpMyAdmin weak password:'+user,pwd else: print '[-] Checking for '+user,pwd+" fail" time.sleep(2) except: print '[-] Something Error'+user,pwd+" fail"
10、Tomcat 扫描模块
模拟http请求,检测tomcat控制台弱口令。
def tomcat_login(ip,port,user,pwd): try: url = "http://"+ip+":"+str(port)+"/manager/html" user_agent = "Mozilla/4.0 (compatible; MSIE 5.5; Windows NT)" Authorization = "Basic %s" % (base64.b64encode(user+':'+pwd)) header = { 'User-Agent' : user_agent , 'Authorization':Authorization} request = urllib2.Request(url,headers=header) response = urllib2.urlopen(request,timeout=5) result=response.read() if response.code ==200: print '[Success] ' + url+' '+user+':'+pwd except: print '[Login failed]' + url+' '+user+':'+pwd
本文由Bypass整理发布,转载请保留出处。
欢迎关注我的个人微信公众号:Bypass--,浏览更多精彩文章。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号