1,基本概念
- Jenkins在DevOps工具链中是核心的流程管理中心,负责串联系统的构建流程、测试流程、镜像制作流程、部署流程等,在持续集成中常用到的工具如下:
- Maven:源代码编译工具
- RobotFramework:自动化测试工具
- NewMan:接口自动化测试工具
- SonarQube Scanner:源代码扫描工具
- GitLab:代码仓库工具
- Docker:镜像制作工具
- kubectl:K8S工具
- 目前使用的流程是通过Redmine和GitLab中创建项目、开发提交代码、触发jenkins完成镜像构建并自动部署到k8s集群。
2,部署
2.1 下载代码
git clone https://github.com/xiaoqshuo/k8s-cluster.git
2.2 安装 Jenkins
[root@k8s-master01 jenkins-helm]# helm install --name jenkins . --namespace public-service
NAME: jenkins
LAST DEPLOYED: Fri Dec 21 08:49:59 2018
NAMESPACE: public-service
STATUS: DEPLOYED
RESOURCES:
==> v1/Service
NAME AGE
jenkins-agent 1s
jenkins 1s
==> v1beta1/Deployment
jenkins 1s
==> v1/Secret
jenkins 2s
==> v1/ConfigMap
jenkins 2s
jenkins-tests 2s
==> v1/PersistentVolumeClaim
jenkins 2s
NOTES:
1. Get your 'admin' user password by running:
printf $(kubectl get secret --namespace public-service jenkins -o jsonpath="{.data.jenkins-admin-password}" | base64 --decode);echo
2. Get the Jenkins URL to visit by running these commands in the same shell:
export POD_NAME=$(kubectl get pods --namespace public-service -l "component=jenkins-master" -o jsonpath="{.items[0].metadata.name}")
echo http://127.0.0.1:8080
kubectl port-forward $POD_NAME 8080:8080
3. Login with the password from step 1 and the username: admin
For more information on running Jenkins on Kubernetes, visit:
https://cloud.google.com/solutions/jenkins-on-container-engine
2.3 创建 ingress
[root@k8s-master01 jenkins-helm]# kubectl create -f traefik-jenkins.yaml
ingress.extensions/jenkins created
2.4 查看状态
[root@k8s-master01 jenkins-helm]# kubectl get po,svc,ingress,pvc -n public-service | grep jenkins
pod/jenkins-678c74d8f8-dzvcm 1/1 Running 1 16m
service/glusterfs-dynamic-jenkins ClusterIP 10.96.104.25 <none> 1/TCP 15m
service/jenkins ClusterIP 10.103.109.143 <none> 8080/TCP 16m
service/jenkins-agent ClusterIP 10.104.102.106 <none> 50000/TCP 16m
ingress.extensions/jenkins jenkins.k8s.net 80 19h
persistentvolumeclaim/jenkins Bound pvc-5ba828d9-04ba-11e9-a5f6-000c2927a0d0 20Gi RWX gluster-heketi 16m
2.5 访问测试
3,配置 Jenkins
3.1 登录
3.1.1 查看密码
[root@k8s-master01 jenkins-helm]# kubectl get secret --namespace public-service jenkins -o jsonpath="{.data.jenkins-admin-password}" | base64 --decode
OZy8B3uklZ
3.1.2 登录
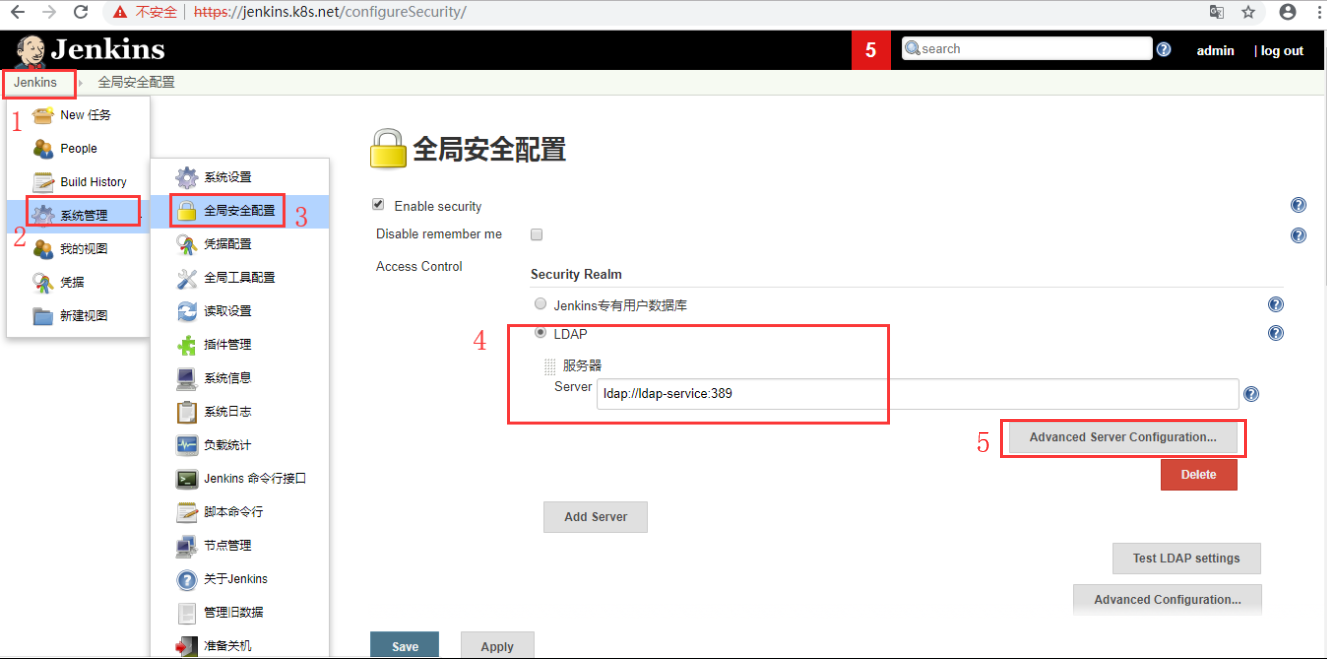
3.2 配置LDAP登录
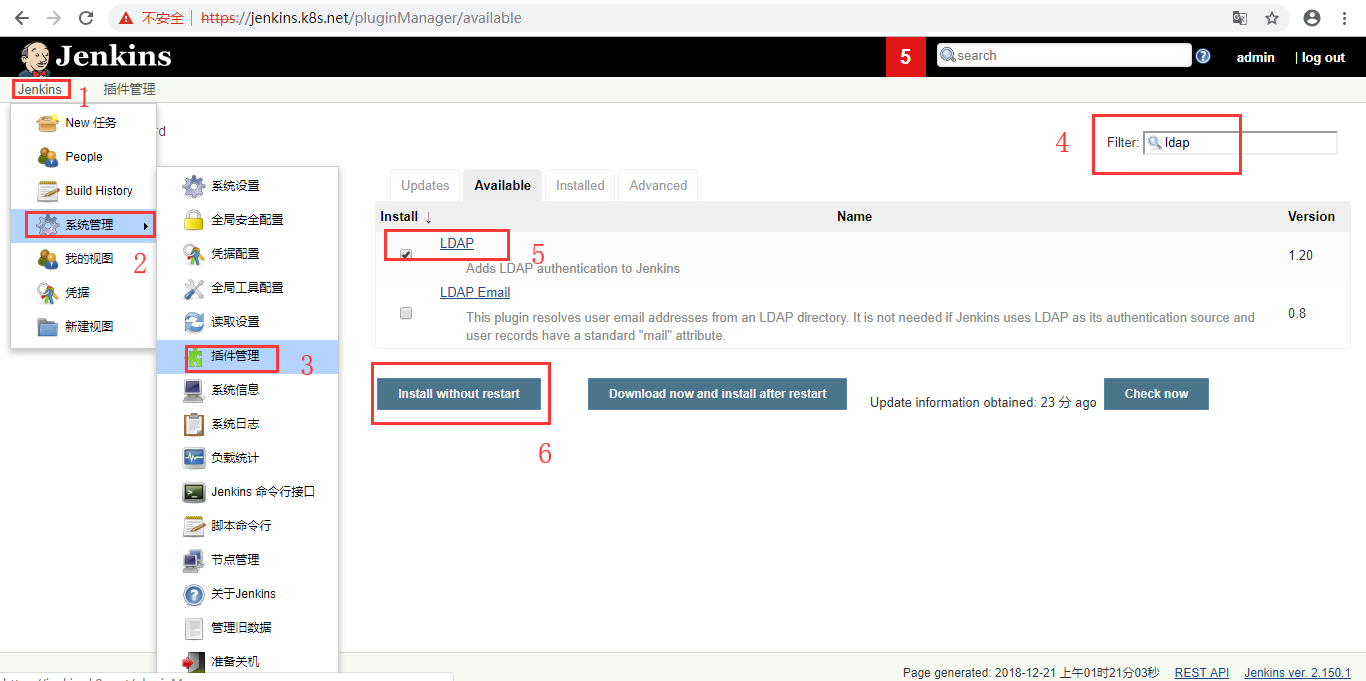
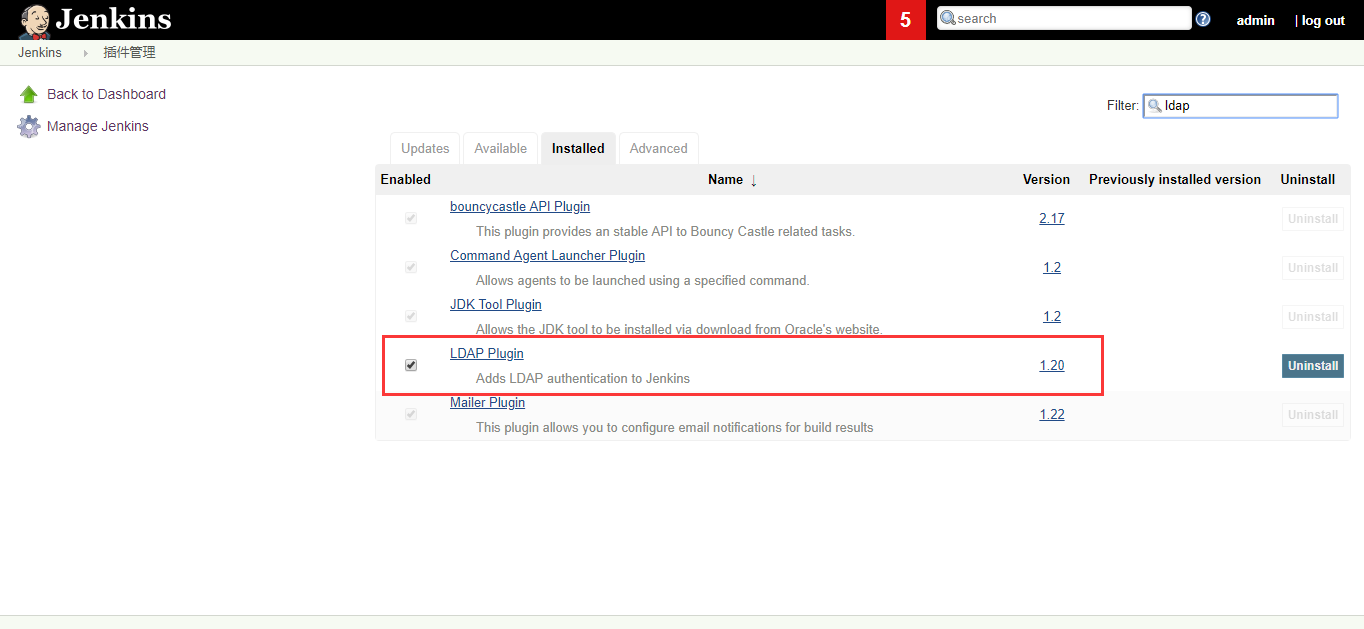
3.2.1 安装LDAP插件
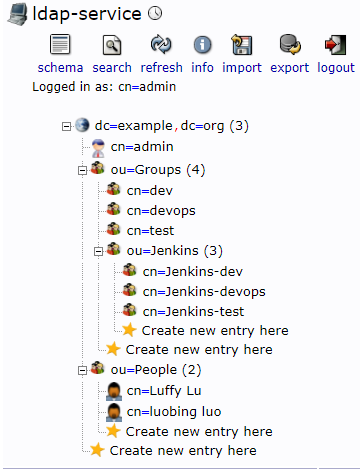
3.2.2 建立openLDAP组织架构如下
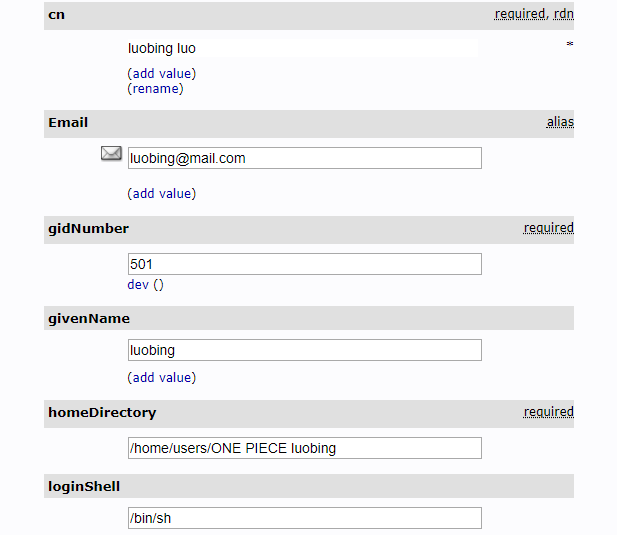
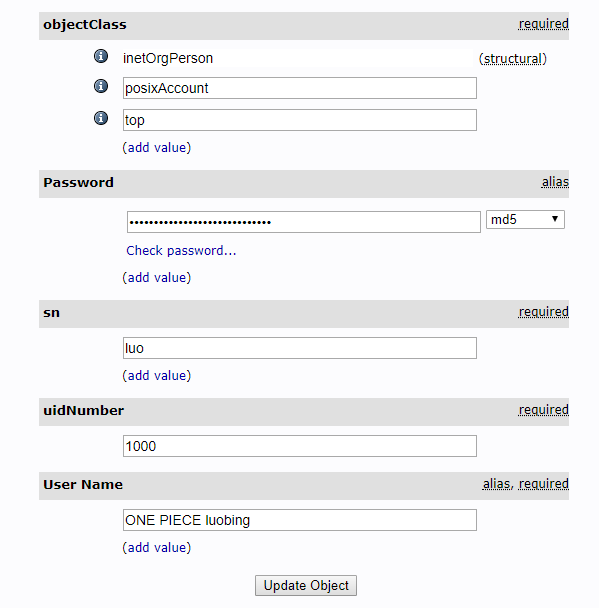
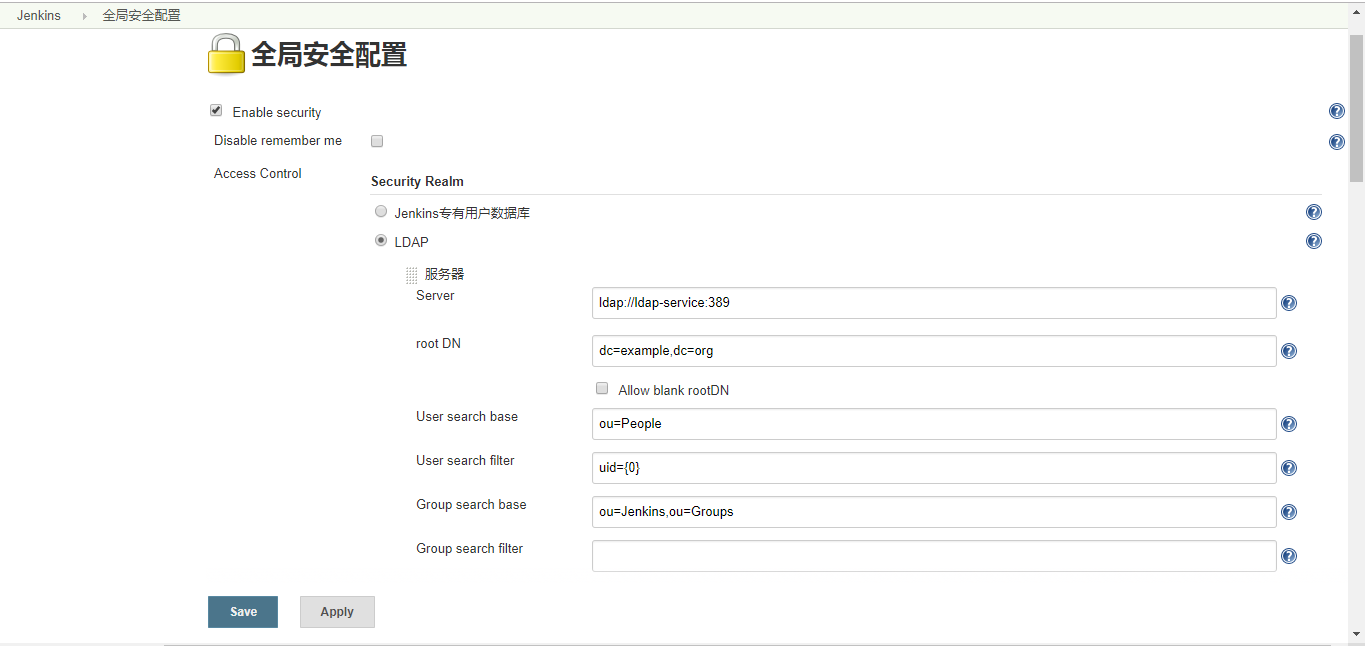
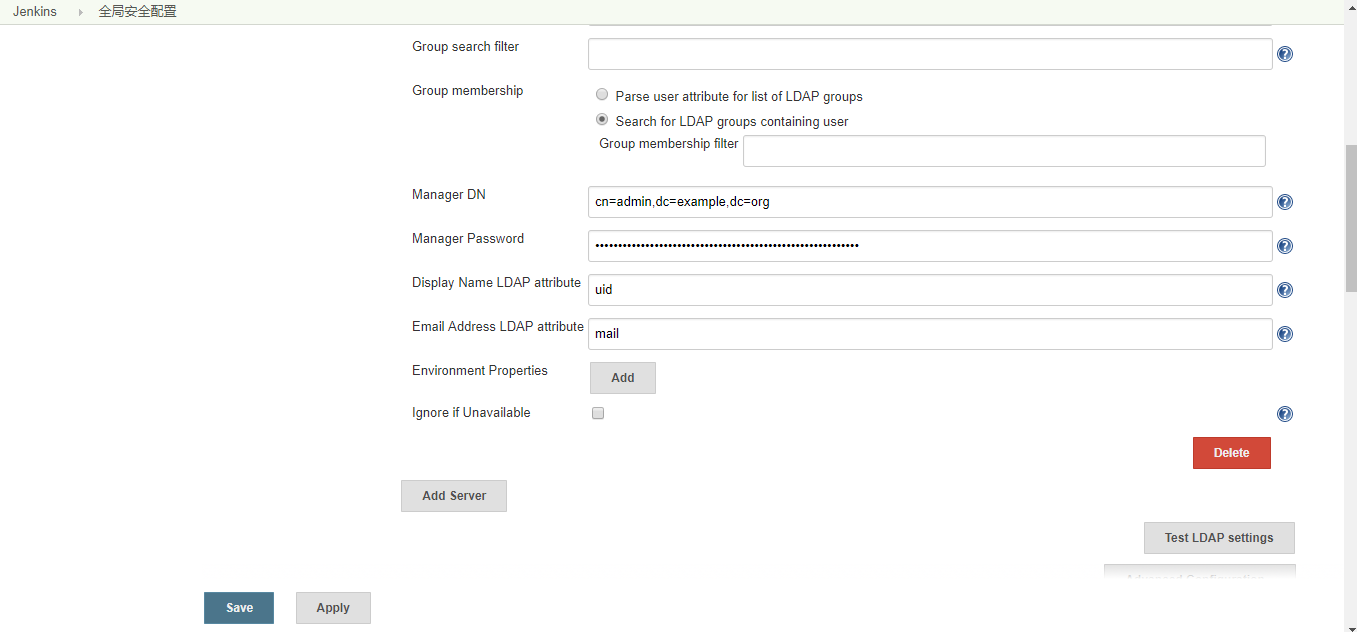
3.2.3 配置
- ou=People对应的用户的组为ou=jenkins,ou=Groups里面的组
- 配置完LDAP登陆以后,本地认证就会失效
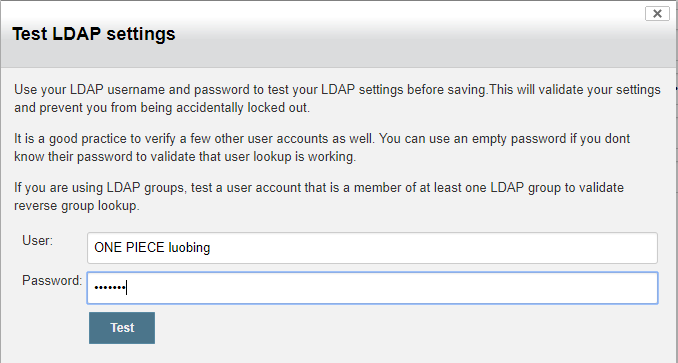
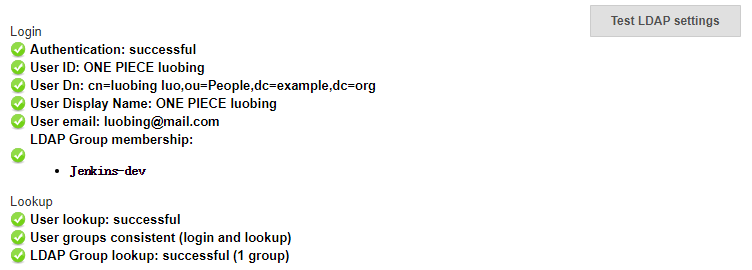
3.2.3.1 测试
- uid:ONE PIECE luobing
- passwd: luobing
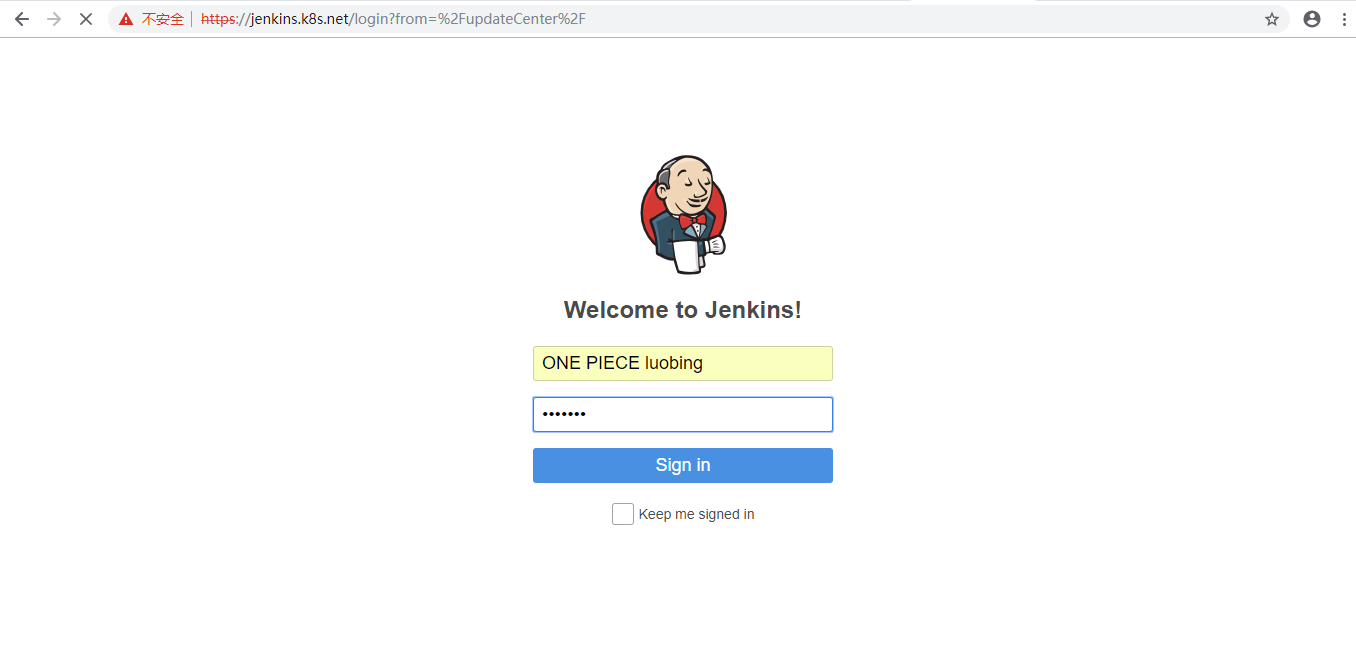
3.2.4 登录
4,权限控制
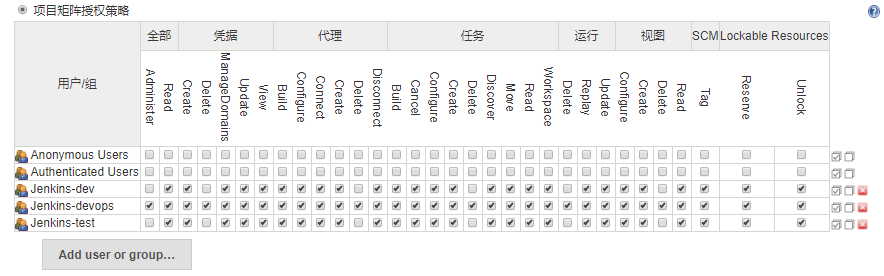
- Role Strategy Plugin插件可以对构建的项目进行授权管理,让不同的用户管理不同的项目,将测试和生产环境分开。
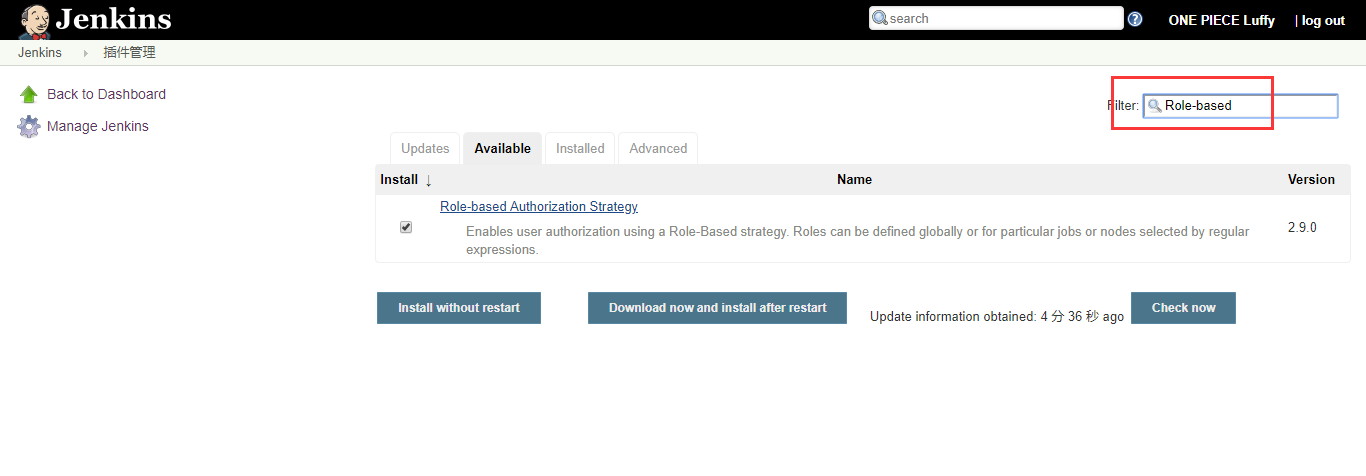
4.1 安装权限控制插件
- 插件名称:Role-based Authorization Strategy
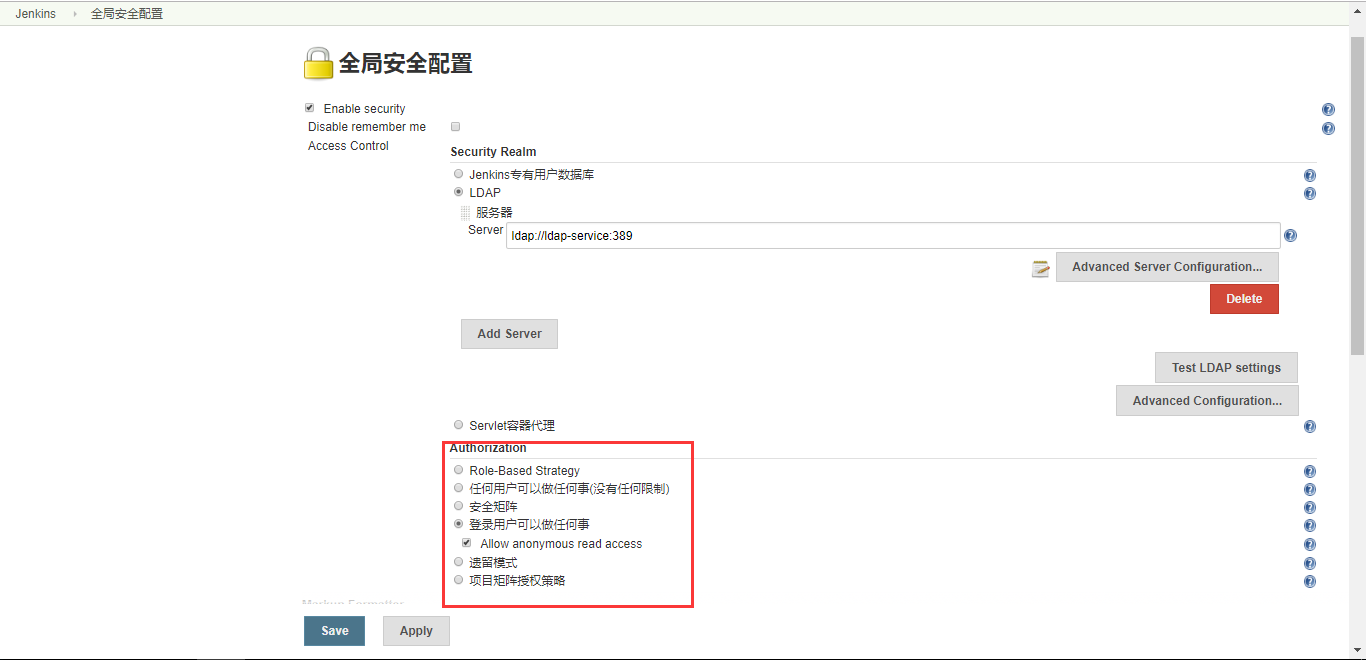
4.2 配置权限
4.3 登录测试