Dest0g3 520迎新赛-CRYPTO MISC 复现
CRYPTO
babyRSA
题目
from Crypto.Util.number import bytes_to_long, getPrime
from gmpy2 import next_prime
p = getPrime(1024)
q = next_prime(p)
n = p*q
flag = open('flag.txt', 'rb').read()
m = bytes_to_long(flag)
e = 65537
c = pow(m, e, n)
print(n)
print(c)
'''
27272410937497615429184017335437367466288981498585803398561456300019447702001403165885200936510173980380489828828523983388730026101865884520679872671569532101708469344562155718974222196684544003071765625134489632331414011555536130289106822732544904502428727133498239161324625698270381715640332111381465813621908465311076678337695819124178638737015840941223342176563458181918865641701282965455705790456658431641632470787689389714643528968037519265144919465402561959014798324908010947632834281698638848683632113623788303921939908168450492197671761167009855312820364427648296494571794298105543758141065915257674305081267
14181751948841206148995320731138166924841307246014981115736748934451763670304308496261846056687977917728671991049712129745906089287169170294259856601300717330153987080212591008738712344004443623518040786009771108879196701679833782022875324499201475522241396314392429412747392203809125245393462952461525539673218721341853515099201642769577031724762640317081252046606564108211626446676911167979492329012381654087618979631924439276786566078856385835786995011067720124277812004808431347148593882791476391944410064371926611180496847010107167486521927340045188960373155894717498700488982910217850877130989318706580155251854
'''我的解答:
白给,直接分解n即可
import gmpy2
from Crypto.Util.number import long_to_bytes
p=165143607013706756535226162768509114446233024193609895145003307138652758365886458917899911435630452642271040480670481691733000313754732183700991227511971005378010205097929462099354944574007393761811271098947894183507596772524174007304430976545608980195888302421142266401500880413925699125132100053801973969401
q=165143607013706756535226162768509114446233024193609895145003307138652758365886458917899911435630452642271040480670481691733000313754732183700991227511971005378010205097929462099354944574007393761811271098947894183507596772524174007304430976545608980195888302421142266401500880413925699125132100053801973971467
c= 14181751948841206148995320731138166924841307246014981115736748934451763670304308496261846056687977917728671991049712129745906089287169170294259856601300717330153987080212591008738712344004443623518040786009771108879196701679833782022875324499201475522241396314392429412747392203809125245393462952461525539673218721341853515099201642769577031724762640317081252046606564108211626446676911167979492329012381654087618979631924439276786566078856385835786995011067720124277812004808431347148593882791476391944410064371926611180496847010107167486521927340045188960373155894717498700488982910217850877130989318706580155251854
e = 65537
n = p*q
phi = (p-1) * (q-1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(long_to_bytes(m))
#Dest0g3{96411aad-032c-20a8-bc43-b473f6f08536}babyAES
题目
from Crypto.Cipher import AES
import os
iv = os.urandom(16)
key = os.urandom(16)
my_aes = AES.new(key, AES.MODE_CBC, iv)
flag = open('flag.txt', 'rb').read()
flag += (16 - len(flag) % 16) * b'\x00'
c = my_aes.encrypt(flag)
print(c)
print(iv)
print(key)
'''
b'C4:\x86Q$\xb0\xd1\x1b\xa9L\x00\xad\xa3\xff\x96 hJ\x1b~\x1c\xd1y\x87A\xfe0\xe2\xfb\xc7\xb7\x7f^\xc8\x9aP\xdaX\xc6\xdf\x17l=K\x95\xd07'
b'\xd1\xdf\x8f)\x08w\xde\xf9yX%\xca[\xcb\x18\x80'
b'\xa4\xa6M\xab{\xf6\x97\x94>hK\x9bBe]F'
'''我的解答:
签到AES。
from Crypto.Cipher import AES
import os
# 读取密文和密钥
c = b'C4:\x86Q$\xb0\xd1\x1b\xa9L\x00\xad\xa3\xff\x96 hJ\x1b~\x1c\xd1y\x87A\xfe0\xe2\xfb\xc7\xb7\x7f^\xc8\x9aP\xdaX\xc6\xdf\x17l=K\x95\xd07'
iv = b'\xd1\xdf\x8f)\x08w\xde\xf9yX%\xca[\xcb\x18\x80'
key = b'\xa4\xa6M\xab{\xf6\x97\x94>hK\x9bBe]F'
# 创建AES解密器
my_aes = AES.new(key, AES.MODE_CBC, iv)
# 解密密文
flag = my_aes.decrypt(c)
flag = flag.rstrip(b'\x00')
# 打印解密后的flag
print(flag)
#Dest0g3{d0e5fa76-e50f-76f6-9cf1-b6c2d576b6f4}ezDLP
题目
from Crypto.Util.number import *
flag = open('flag.txt', 'rb').read()
x = bytes_to_long(flag)
g = 19
p = 335215034881592512312398694238485179340610060759881511231472142277527176340784432381542726029524727833039074808456839870641607412102746854257629226877248337002993023452385472058106944014653401647033456174126976474875859099023703472904735779212010820524934972736276889281087909166017427905825553503050645575935980580803899122224368875197728677516907272452047278523846912786938173456942568602502013001099009776563388736434564541041529106817380347284002060811645842312648498340150736573246893588079033524476111268686138924892091575797329915240849862827621736832883215569687974368499436632617425922744658912248644475097139485785819369867604176912652851123185884810544172785948158330991257118563772736929105360124222843930130347670027236797458715653361366862282591170630650344062377644570729478796795124594909835004189813214758026703689710017334501371279295621820181402191463184275851324378938021156631501330660825566054528793444353
h = pow(g, x, p)
print(h)
'''
199533304296625406955683944856330940256037859126142372412254741689676902594083385071807594584589647225039650850524873289407540031812171301348304158895770989218721006018956756841251888659321582420167478909768740235321161096806581684857660007735707550914742749524818990843357217489433410647994417860374972468061110200554531819987204852047401539211300639165417994955609002932104372266583569468915607415521035920169948704261625320990186754910551780290421057403512785617970138903967874651050299914974180360347163879160470918945383706463326470519550909277678697788304151342226439850677611170439191913555562326538607106089620201074331099713506536192957054173076913374098400489398228161089007898192779738439912595619813699711049380213926849110877231503068464392648816891183318112570732792516076618174144968844351282497993164926346337121313644001762196098432060141494704659769545012678386821212213326455045335220435963683095439867976162
'''我的解答:
又是一个签到,考察Pohlig-Hellman算法
#计算DLP的通用方法
discrete_log(y,g)==x
#n为合数(Pohlig-Hellman)
x = discrete_log(mod(b,n),mod(a,n)) 脚本如下:
#sage
from Crypto.Util.number import long_to_bytes
h = 199533304296625406955683944856330940256037859126142372412254741689676902594083385071807594584589647225039650850524873289407540031812171301348304158895770989218721006018956756841251888659321582420167478909768740235321161096806581684857660007735707550914742749524818990843357217489433410647994417860374972468061110200554531819987204852047401539211300639165417994955609002932104372266583569468915607415521035920169948704261625320990186754910551780290421057403512785617970138903967874651050299914974180360347163879160470918945383706463326470519550909277678697788304151342226439850677611170439191913555562326538607106089620201074331099713506536192957054173076913374098400489398228161089007898192779738439912595619813699711049380213926849110877231503068464392648816891183318112570732792516076618174144968844351282497993164926346337121313644001762196098432060141494704659769545012678386821212213326455045335220435963683095439867976162
p = 335215034881592512312398694238485179340610060759881511231472142277527176340784432381542726029524727833039074808456839870641607412102746854257629226877248337002993023452385472058106944014653401647033456174126976474875859099023703472904735779212010820524934972736276889281087909166017427905825553503050645575935980580803899122224368875197728677516907272452047278523846912786938173456942568602502013001099009776563388736434564541041529106817380347284002060811645842312648498340150736573246893588079033524476111268686138924892091575797329915240849862827621736832883215569687974368499436632617425922744658912248644475097139485785819369867604176912652851123185884810544172785948158330991257118563772736929105360124222843930130347670027236797458715653361366862282591170630650344062377644570729478796795124594909835004189813214758026703689710017334501371279295621820181402191463184275851324378938021156631501330660825566054528793444353
g = 19
x = discrete_log(mod(h, p), mod(g, p))
print(long_to_bytes(x))
#Dest0g3{07ed2a6f-182f-a05d-c81e-1318af820a78}ezStream
题目
from Crypto.Util.number import *
f = open('flag.txt', 'r')
flag = f.read()
f.close()
assert flag[:8] == "Dest0g3{"
class LCG:
def __init__(self):
self.a = getRandomNBitInteger(32)
self.b = getRandomNBitInteger(32)
self.m = getPrime(32)
self.seed = getRandomNBitInteger(32)
def next(self):
self.seed = (self.a * self.seed + self.b) % self.m
return self.seed >> 16
def output(self):
print("a = {}\nb = {}\nm = {}".format(self.a, self.b, self.m))
print("state1 = {}".format(self.next()))
print("state2 = {}".format(self.next()))
lcg = LCG()
lcg.output()
c = b''.join([long_to_bytes(ord(flag[i]) ^ (lcg.next() % 10))
for i in range(len(flag))])
print(bytes_to_long(c))
'''
a = 3939333498
b = 3662432446
m = 2271373817
state1 = 17362
state2 = 20624
600017039001091357643174067454938198067935635401496485588306838343558125283178792619821966678282131419050878
'''我的解答:
考点:LCG算法,脚本如下:
from gmpy2 import invert
from Crypto.Util.number import *
a = 3939333498
b = 3662432446
m = 2271373817
state1 = 17362
state2 = 20624
c = 600017039001091357643174067454938198067935635401496485588306838343558125283178792619821966678282131419050878
state1_ = state1 << 16
def next(seed):
seed_new = (a * seed + b) % m
return seed_new >> 16,seed_new
# 爆破低16位得到可能的state1的真实值
# for i in range(2**16):
# t = state1_ + i
# if (a * t + b) % m >> 16 == state2:
# print(t)
t_list = [1137839988,1137855425,1137870862]
# 求出可能的seed
for i in t_list:
seed = (i - b) * invert(a,m)%m
print(seed)
seed_list = [1315807869,710396196,104984523]
c_bytes = long_to_bytes(c)
print(len(c_bytes))
key_list = []
seed = 104984523
for i in range(47):
key,seed = next(seed)
key_list.append(key%10)
for i in range(45):
print(chr(key_list[i+2]^c_bytes[i]),end='')
#Dest0g3{f21c7180-c35e-f912-e4bc-bfd235759a25}
# 这道题并不需要求seed,拿到t_list之后递推就可以了Mr.Doctor
题目
from Crypto.Util.number import *
from hashlib import sha256
import string
table = string.ascii_letters + string.digits
flag = open('flag.txt', 'rb').read()[8:-1]
seed = getRandomNBitInteger(40)
class SHA256:
def __init__(self):
self.proof = []
self.sha = 0
self.sha_flag = []
def encryption(self):
for i in range(len(flag) // 4):
self.proof.append(flag[4 * i:4 + 4 * i])
self.sha = sha256(self.proof[i]).hexdigest().encode()
self.sha_flag.append(bytes_to_long(self.sha))
return self.sha_flag
class RHODES_ELITE:
def __init__(self):
self.Doctor = getPrime(64)
self.Amiya = getRandomNBitInteger(40)
self.Rosmontis = getRandomNBitInteger(40)
self.Blaze = getRandomNBitInteger(40)
self.seed = seed
def next(self):
self.seed = (self.Amiya * self.seed * self.seed + self.Rosmontis * self.seed + self.Blaze) % self.Doctor
return self.seed >> 12
def output(self):
print("Amiya = ", self.Amiya)
print("Rosmontis = ", self.Rosmontis)
print("Blaze = ", self.Blaze)
print("Doctor = ", self.Doctor)
sha = SHA256()
sha_flag = sha.encryption()
elite = RHODES_ELITE()
elite.output()
print("Ash = ", elite.next())
print("SliverAsh = ", elite.next())
W = b''.join([long_to_bytes(sha_flag[i] % (seed ** 3) ^ (elite.next() % 100)) for i in range(len(sha_flag))])
print(bytes_to_long(W))
'''
Amiya = 956366446278
Rosmontis = 1061992537343
Blaze = 636205571590
Doctor = 18068433704538283397
Ash = 1097363493609113
SliverAsh = 2051431344160327
1920358673646340365826516899186299898354902389402251443712585240681673718967552394250439615271108958695077816395789102908554482423707690040360881719002797624203057223577713119411615697309430781610828105111854807558984242631896605944487456402584672441464316236703857236007195673926937583757881853655505218912262929700452404084
'''我的解答:
Ash和SliverAsh是连续两次seed右移12位的整数值,我们通过推导公式暴力破解seed。
Amiya = 956366446278
Rosmontis = 1061992537343
Blaze = 636205571590
Doctor = 18068433704538283397
for i in range(4096):
bin1 = bin(1097363493609113)[2:]
bin2 = bin(i)[2:].ljust(12, '0')
pre_seed = int(bin1 + bin2, 2)
seed = (Amiya * pre_seed * pre_seed + Rosmontis * pre_seed + Blaze) % Doctor
if seed >> 12 == 2051431344160327:
print(pre_seed)
#4494800869822930172这里相当于知道了Ash对应的seed值,但仍不知道最初随机生成的seed,即Ash的前一次的seed值。求最初seed需要求解二次同余方程。
依然借助Sage求解。
Amiya = 956366446278
Rosmontis = 1061992537343
Blaze = 636205571590
Doctor = 18068433704538283397
R.<seed> = Zmod(Doctor)[]
f = Amiya * seed * seed + Rosmontis * seed + Blaze - 4494800869822930172
f.roots()
# [(12358488364449364025, 1), (626844643882, 1)]最后生成两个结果,根据题目seed二进制最大为40位,因此我们选择第二个值。然后根据代码逻辑,每4位计算哈希并拼接,暴力求解即可(时间较长)。
import string
from Crypto.Util.number import *
from hashlib import sha256
import math
Amiya = 956366446278
Rosmontis = 1061992537343
Blaze = 636205571590
Doctor = 18068433704538283397
seed = 626844643882
class RHODES_ELITE:
def __init__(self):
self.Doctor = Doctor
self.Amiya = Amiya
self.Rosmontis = Rosmontis
self.Blaze = Blaze
self.seed = seed
def next(self):
self.seed = (self.Amiya * self.seed * self.seed + self.Rosmontis * self.seed + self.Blaze) % self.Doctor
return self.seed >> 12
def output(self):
print("Amiya = ", self.Amiya)
print("Rosmontis = ", self.Rosmontis)
print("Blaze = ", self.Blaze)
print("Doctor = ", self.Doctor)
def find_flag(W_bytes):
for a in flag_chars:
for b in flag_chars:
for c in flag_chars:
for d in flag_chars:
W = W_bytes
flag_c = a + b + c + d
sha = sha256(flag_c.encode()).hexdigest().encode()
sha_flag = bytes_to_long(sha)
W += long_to_bytes(sha_flag % (seed ** 3) ^ (the_next % 100))
if c_bytes.startswith(W):
print(flag_c)
return W, flag_c
flag_chars = '-_' + string.ascii_letters + string.digits
c_num = 1920358673646340365826516899186299898354902389402251443712585240681673718967552394250439615271108958695077816395789102908554482423707690040360881719002797624203057223577713119411615697309430781610828105111854807558984242631896605944487456402584672441464316236703857236007195673926937583757881853655505218912262929700452404084
elite = RHODES_ELITE()
Ash = elite.next()
assert Ash == 1097363493609113
SliverAsh = elite.next()
assert SliverAsh == 2051431344160327
c_bytes = long_to_bytes(c_num)
W_bytes = b''
flag = ''
while c_bytes != W_bytes:
the_next = elite.next()
W_new, flag_c = find_flag(W_bytes)
W_bytes = W_new
flag += flag_c
print(flag)
# d2a4d1af-8a80-8794-99ac-635f89494cacMISC
Welcome to fxxking DestCTF
题目
关注公众号并回复:Give me the fxxking flag
我的解答:
按要求即可
Dest0g3{W31c0m3_t0_DestCTF2022!}
Pngenius
题目

我的解答:
010分析图片尾部藏有flag
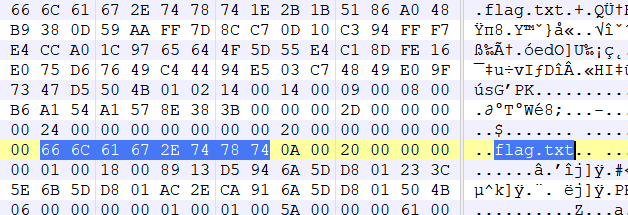
卡里分离出来得到一个压缩包,使用如下指令得到密码
zsteg 1.png Password for zip:Weak_Pas5w0rd解压得到
Dest0g3{2908C1AA-B2C1-B8E6-89D1-21B97D778603}
EasyEncode
题目

我的解答:
尝试了一些方法不行,直接爆破吧!
解压得到摩斯
..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- ..--- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- --... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- -.... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- --... -.... .---- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... ...-- ....- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- ....- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- ..--- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... -.... ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- -.... ....- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ...-- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- --... ...-- ....- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... -.... .---- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- --... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ----. ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... -.... ..--- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... ...-- .---- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- --... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... -.... ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- ---.. ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- --... -.... .---- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- -.... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- --... -.... .---- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- ---.. ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ..--- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ----- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... ...-- ...-- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ...-- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... -.... ...-- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... ...-- -.... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- -.... ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- -.... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ----. ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- -.... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- -.... ...-- -.... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..... ...-- .---- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..--- ...-- ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ...-- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- ....- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ..--- ...-- ..... ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ...-- ...-- ...-- ..... -.-. --... ..... ...-- ----- ...-- ----- ...-- ....- ...-- ....- 
Escape解码得到:RGVzdDBnM3tEZW9kaW5nXzFzX2U0c3lfNF9VfQ==
base64解码得到:Dest0g3{Deoding_1s_e4sy_4_U}
你知道js吗
题目
我的解答:
010打开发现存在docx特征,故修改后缀为docx打开

字体看不懂,我们换一种字体看看
然后base64解码得到
+++++ ++[-> +++++ ++<]> +++.. ++.-. ++.-- --.++ ++.--
-.-.- --.++ ++++.
+.--- -..++ ++.<+ ++[-> +++<] >++.< +++[-
>---< ]>--- ---.+ ++++. -----
.+++. ...-- ---.+ ++++. ---.+ ++.-- ---.+ ++++. ---.. +++++ +.--- ----.
<++++ [->++ ++<]> ++.<+ +++[- >---- <]>-. ---.+
+++++ .---- -.++. ++.+.
--.-- .<+++ +[->+ +++<] >++.< ++++[ ->--- -<]>-
.+.-. ---.+ ++.+. -.+++
+.--- --.<+ +++[- >++++ <]>++ .<+++ [->-- -<]>- ----. ----. +.+++ +.---
-.--- .+++. -..<+ +++[- >++++ <]>++
.<+++ +[->- ---<] >-.++ +++.- ----.
+++.. ---.+ ++.-- --.+. ..+++ +.-.- ----. +++++
.---- .+.++ ++.-- --.++
++.-. ----. +.-.+ ++++.
<+++[ ->+++ <]>++ ++.<brainfuck解码得到
446573743067337B38366661636163392D306135642D343034372D623730322D3836636233376162373762327Dhex解码得到
Dest0g3{86facac9-0a5d-4047-b702-86cb37ab77b2}
StrangeTraffic
题目:

我的解答:
抓包工具打开追踪TCP流得到

hex转储

发现如下内容,每一个循环的结尾都存在base64一部分
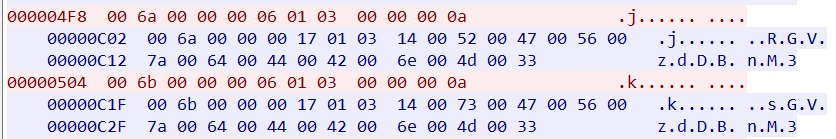
手撸得到密文:
RGVzdDBnM3szMUE1QkVBNi1GMjBELUYxOEEtRThFQS0yOUI0RjI1NzEwOEJ9
base64解码得到
Dest0g3{31A5BEA6-F20D-F18A-E8EA-29B4F257108B}
4096
Just relax and always be aware of the changes on the web!
我的解答:
打开靶机进入
查看源代码,在js里发现base64
Q29uZ3JhdHVsYXRpb25zLCB0aGlzIGlzIHBhcnQgb2YgdGhlIGZsYWc6IE5HVmxOeTFpTmpjekxUazNNV1E0TVdZNFlqRTNOMzA9Lg==
解码得到flag后半段。。。
4ee7-b673-971d81f8b177}
接下来寻找前半段。。
从源代码下载favicon.png。卡里分离得到一个压缩包和一个wav文件
听一下wav,发现前面是按键音,中间是SSTV,后面也是按键音。我们使用AU处理,将中间的SSTV删除后让两段拨号音拼接
然后使用demf2num进行拨号音识别,得到74958097831
然后我们将它进行reserve操作,得到手机号13879085947
然后我们听一下中间的SSTV,用手机即可(软件名:Robot36)

按照指示将手机号进行md5加密,得到最终的解压密码
32fc1b5487cb447f792a19418b92544e
解压得到

使用拼图工具得到
RGVzdDBnM3tlZDRkMTE0Zi05ZWU0LQ==
解码得到 Dest0g3{ed4d114f-9ee4-
拼接有
Dest0g3{ed4d114f-9ee4-4ee7-b673-971d81f8b177}
Python_jail
题目
听说python是最好的语言,那我把它锁起来,我就是最好的语言了!
我的解答:
先查看hint文件
我们是隐形的,但你不能忽略我们!
这是不公平的!
我要让他们注意到我们.
怎么做呢?
我们也来组成一门语言, 就是最好的语言!发现空白字符,使用在线网址解码password空白文件
https://vii5ard.github.io/whitespace/
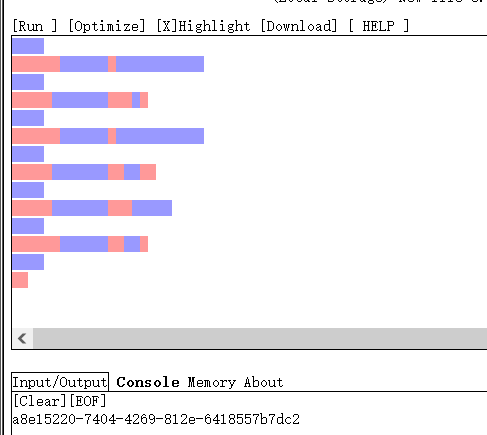
得到:a8e15220-7404-4269-812e-6418557b7dc2
使用此密码解压压缩包得到
使用stegslove打开,在R0G0B0发现Zmxh开头的字符串,疑似flag进行了base64编码
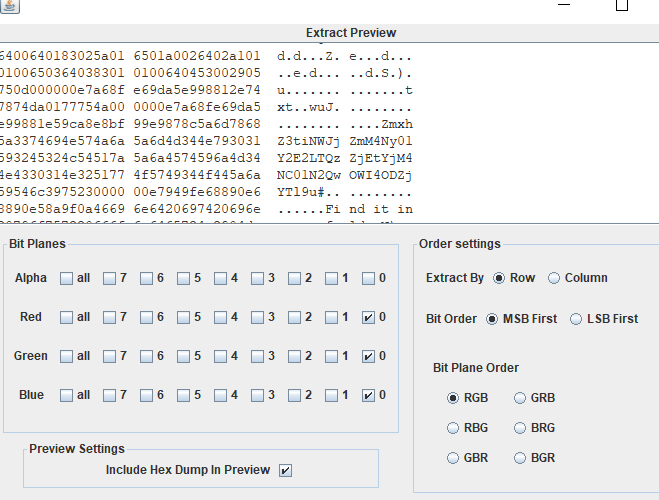
解base64得到flag
codegame
题目
Funny and ez codegame with Key to celebrate EDG
我的解答:
打开KEYcode得到
HAI EDGNB code
I HAS A CODE ITZ "THISISTHEPASSWORD"
I HAS A MSG ITZ ""
I HAS A COUNTER ITZ 0
I HAS A NUM
IM IN YR LOOP UPPIN YR COUNTER WILE COUNTER SMALLR THAN LEN OF CODE
I HAS A C ITZ CODE!COUNTER
NUM R ORD OF C
NUM R SUM OF NUM AN -3
IZ NUM SMALLR THAN 65?, NUM R SUM OF NUM AN 26, KTHX
NUM R CHR OF NUM
MSG R SMOOSH MSG AN NUM
IM OUTTA YR LOOP
VISIBLE MSG
KTHXBYE在线工具识别一下得知,这段代码是LOLCODE,LOLCODE在线运行
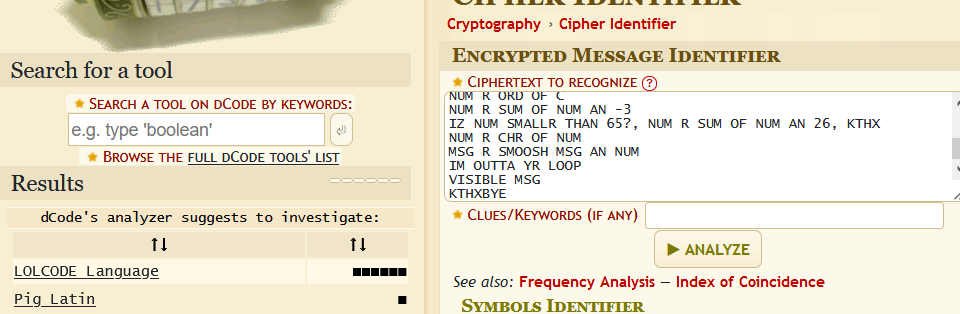
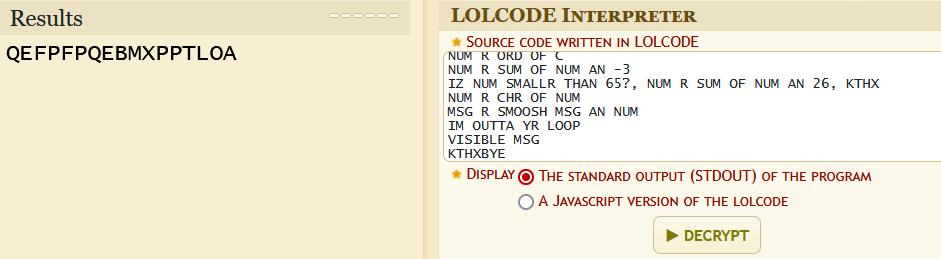
使用此密码解压压缩包得到
修改后缀为zip解压得到fllllllllll1ag.txt
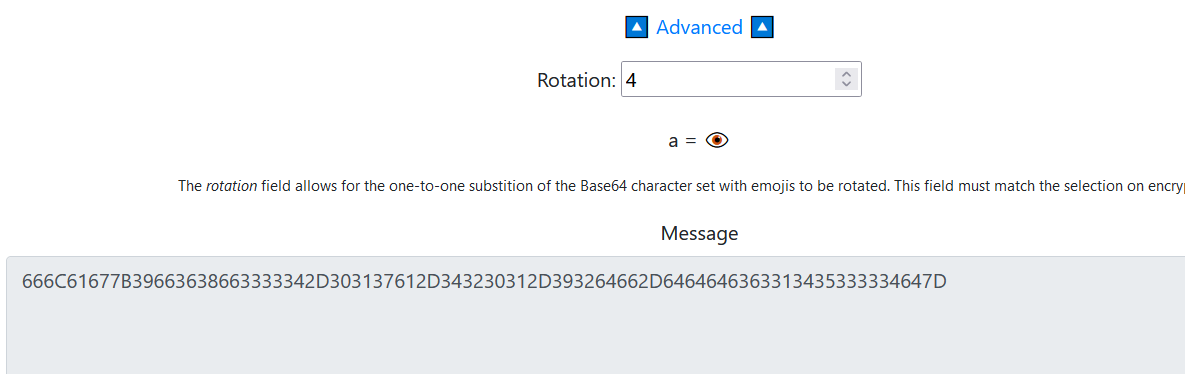
❓😇🍵💧🖐🍴⏩👌😆😊🗒✖🎅😊🐅🏹🎅🌉🎃☃✅👉☺ℹ⏩🍎🚫🗒🏹🍵🐅👌😁✅📮👉💧🍎🐎☂☀😇😆👉🐅🚰🐎💧🐎😆⌨✅🛩☂🦓⌨👁💵🕹❓🌏🎃🏹😎🐎🕹💵📂🛩✉🎈🚹🏎😎🍎👑💵☂🍵🍴🚹😂❓🏎🛩🌿🎃🔪🌊✖👁🍵😀🕹🍌☀👣😆😀🏹☺🐘🚨🖐🛩📮👉☃😂🍴🏹☀✅😍👌😁🤣🌏🍴📂😍😀🖐🎈🎅📮📂🔬😆🍍💧☀🏹💧💧😍😎🙃🎤✖🏹🦓📮🚰✅🐍🐎✅😆🐘🚪🚪emojiAES,同样用QEFPFPQEBMXPPTLOA进行emojiAES解密即可https://aghorler.github.io/emoji-aes/ (需要调整一下Advanced)
被污染的二维码
题目
贪玩的小龙把墨水泼在了二维码上,你能帮他找回二维码中的秘密嘛?
我的解答:
修改文件后缀为zip解压得到
010查看flag1,发现是个png文件,但是尾部有意外收获,多了一个IDAT块,binwalk分离一下
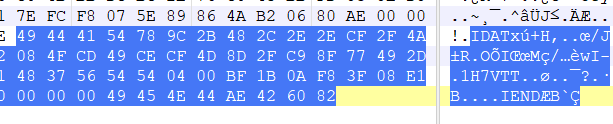
分离出来得到的文件其中有一个密码
password: Welcome_to_Dest0g3!!!看来是有什么东西需要密码,但flag1已经处理完了,我们看看flag2,发现是个7Z文件
但实际上这个7z的文件头损坏了,正确的应该是377ABCAF,而它是377AAFBC,将BCAF换位,得到正确的文件
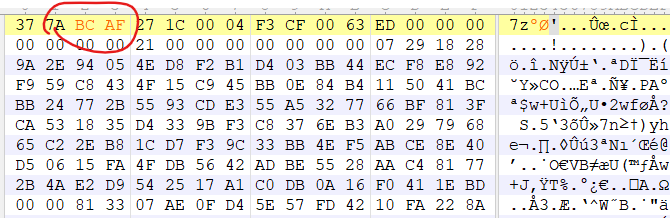
然后将flag2后缀改为7z,使用密码解压,得到密文,发现密文长度有问题,猜测有零宽存在
ETImqQOaZ3gxL2MxMzMuAP1wMGR5YG8/Cm8gBGNlLv1xMwquZGHlAGR2Lmq9 
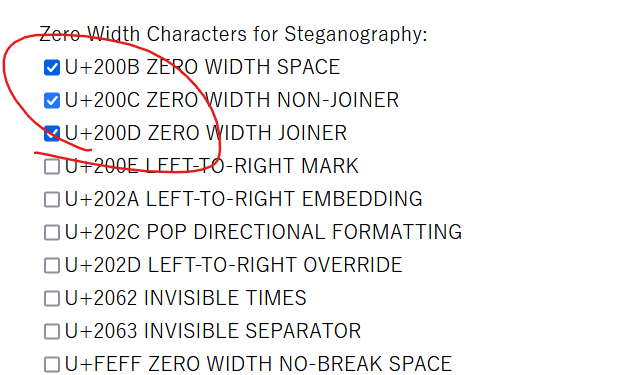
对解出来的字符base64解码(注意换表)

得到部分flag:Dest0g3{dcfdffa4-ce19-????-902b-df7a152516c7}
那么我们接下来的任务就是找到这四位字符,看来只能处理flag1中的二维码了,我们用QRazyBox手动补一下,这里的图片大小是315*315,但是二维码是21*21,所以每15*15代表二维码的一个像素,我们把已知的区域补充一下

然后
得到

最终flag:
Dest0g3{dcfdffa4-ce19-45cb-902b-df7a152516c7}