“古剑山”第一届全国大学生网络攻防大赛-Crtpto | Misc WP
Crypto
babyRSA#
题目信息
p=105570604806073931560404187362816308950408774915960751676958845800335871518600455146040240314204606944641098914858159386588868785987100524581699043605351952348586132553458702298393907476955946990849442034441882748278181148503329309660427627438266645843535466462936882505833453738522673603026747578372964995367
q=143288358949089585215266953016278524463612148007190135453434243047032456958207376091733443584531919755660149037321119885867830905350806865862130270602628423547624190876473872180462192096873381471710899246073298439365336797201672838785511965949336068032011363484044690916570288372443303750426476423930352603827
e=33
c=2015688184356018702340063509729974600786840546364122789630929715337660295810961474144939260049892177486759513271253257458112942844435453563521353664294799145214833075575682837104619902593712323020851788866158742546117774717790910939444986189326649593286629046732910564929050955013637088916579175350308099506220813882274665233182543235264034038626524248300357250276274833999274982434790398489181021739913941634249265775997527901903799819193254397528348894700572493228638350806878366316533768758273322476421225382269304595973225131694907875536065669987510951854843686992445396860396865892650745594418900376500862332616我的解答:
信息都给了,签到题。直接梭
exp:
import gmpy2
from Crypto.Util.number import long_to_bytes
p=105570604806073931560404187362816308950408774915960751676958845800335871518600455146040240314204606944641098914858159386588868785987100524581699043605351952348586132553458702298393907476955946990849442034441882748278181148503329309660427627438266645843535466462936882505833453738522673603026747578372964995367
q=143288358949089585215266953016278524463612148007190135453434243047032456958207376091733443584531919755660149037321119885867830905350806865862130270602628423547624190876473872180462192096873381471710899246073298439365336797201672838785511965949336068032011363484044690916570288372443303750426476423930352603827
e=33
c=2015688184356018702340063509729974600786840546364122789630929715337660295810961474144939260049892177486759513271253257458112942844435453563521353664294799145214833075575682837104619902593712323020851788866158742546117774717790910939444986189326649593286629046732910564929050955013637088916579175350308099506220813882274665233182543235264034038626524248300357250276274833999274982434790398489181021739913941634249265775997527901903799819193254397528348894700572493228638350806878366316533768758273322476421225382269304595973225131694907875536065669987510951854843686992445396860396865892650745594418900376500862332616
n = p*q
phi = (p-1) * (q-1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(long_to_bytes(m))
#flag{39f7ba00d4050d5c51ba6fc1172ac0ed}Vigenere+++#
题目
import sys
from secret_file import *
def _l(idx, s):
return s[idx:] + s[:idx]
def main(p, k1, k2):
s = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz_{}"
t = [[_l((i+j) % len(s), s) for j in range(len(s))] for i in range(len(s))]
i1 = 0
i2 = 0
c = ""
for a in p:
c += t[s.find(a)][s.find(k1[i1])][s.find(k2[i2])]
i1 = (i1 + 1) % len(k1)
i2 = (i2 + 1) % len(k2)
return c
flag="flag{************************}"
key="**********"
# * 为马赛克,长度为1。
# hint: 可以自己尝试下运行加密函数,看看秘钥对加密结果的影响。
# hint: 首先根据线索求秘钥,秘钥不唯一,找到一个有效的,就能爆破flag了。
print main(flag, key, key[::-1])
# 程序运行结果(即密文为):
kqTyKgfxgXT5a_RiTAua4_sbMkjDyE我的解答:
1、我们考虑到在程序正常运行下,数组访问不会越界,我们在讨论时做以下约定:
2、关于 python 程序中定义的 _l 函数,发现以下等价关系:
3、关于 python 的 main 函数中三维矩阵 t 的定义,发现以下等价关系:
4、综合第 2 第 3 点的观察,有如下等价关系:
由于我们知道标志的 5 个字符,即flag{,还知道密钥长度为 10。那么脚本如下:
enc_str = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz_{}'
dec_dic = {k:v for v,k in enumerate(enc_str)}
encrypt = 'kqTyKgfxgXT5a_RiTAua4_sbMkjDyE'
flag_bg = 'flag{************************}'
sim_key = [dec_dic[encrypt[i]]-dec_dic[flag_bg[i]] for i in range(5)] # 破解模拟密钥
sim_key = sim_key + sim_key[::-1]
flag_ed = [dec_dic[v]-sim_key[k%10] for k,v in enumerate(encrypt)] # 模拟密钥解密
flag_ed = ''.join([enc_str[i%len(enc_str)] for i in flag_ed]) # 解码
print(flag_ed)
#flag{4XLbSO0riF6BRp5ZvGTA81Ut}guess_the_key#
题目
主函数
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv) {
if (argc != 3) {
printf("USAGE: %s INPUT OUTPUT\n", argv[0]);
return 0;
}
FILE* input = fopen(argv[1], "rb");
FILE* output = fopen(argv[2], "wb");
if (!input || !output) {
printf("Error\n");
return 0;
}
char key[] = "guessthekey";
char d, q, t = 0;
int ijk = 0;
while ((q = fgetc(input)) != EOF) {
d = (q + (key[ijk % strlen( key )] ^ t) + ijk*ijk) & 0xff;
t = q;
ijk++;
fputc(d, output);
}
return 0;
}msg01
Hi,there is nothing here,heiheihei.msg01.enc
灄K覛嫮 蕲i#Nvp桪"亶"#p?hr谅Kmsg02.enc
僂顕沶迷檎a6乸栐座渖層贽瑊农剹烁▕昑m豪{?h?ㄍ*RI戠Jqk?幓茼|
\tk?罽辑蔓陔&盿磬]蛉?艝X峊糋?槔疕%
色o[70?惹蜖O偌r~凷祰H鍗挬羌?鏬s橸)?铴欢?唫~Lo労鱎€?百@?暞苫桤?u赳
?6I?i鳡磐?k剧{怄K証U?T覾y?詰P龃6AF??噔8?q鱾VM"?顗
СF鷤?睂厭稲?簉C?锠[9诔惘)/倯nAXw拳▔? 扯'_浦
k??犙壓???櫦?砐魡C?
y?我的解答:
显然主函数是一段加密的密码,而msg01中是一段明文文字 ,msg01.enc中是其加密后的文字,我们要找的flag应该是msg02.enc对应的解密后的明文。
这道题看上去就是一道写逆向代码的题目,但是里面有一个坑,我们尝试后发现msg01加密后并非是msg01.enc中的内容,这是因为它的加密代码中key是错误的,所以我们需要找出正确的key。
找出key的代码如下:
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv) {
FILE* input = fopen("msg01.enc", "rb");
if (!input ) {//如果有一个文件无法打开
printf("Error\n");
return 0;
}
char c, p, t = 0;
int i=0;
char w[] = "Hi,there is nothing here,heiheihei.\n"; //原来input中的值
unsigned int j = 0;
while ((p = fgetc(input)) != EOF) {
for (j=31;j<125;j++) {//在找k的真正值,只有当能够逆向回w时,真正找到k
c = (p - (j ^ t) - i*i) & 0xff;
if (c == w[i]) {
printf("%c",j);
t = c;
i++;
break;
}
}
}
return 0;
}得到key为
VeryVeryLongKeyYouWillNeverKnowVery然后使用密钥去得到解密结果,代码如下:
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv) {
FILE* input = fopen("msg02.enc", "rb");
FILE* output = fopen("msg02.txt", "wb");
if (!input || !output) {
printf("Error\n");
return 0;
}
char c, p, t = 0;
int i = 0;
char k[] = "VeryVeryLongKeyYouWillNeverKnowVery";
i = 0;
c, p, t = 0;
int g = 0;
while ((p = fgetc(input)) != EOF) {
//printf("%c",p);
c = (p - (k[i % strlen(k)] ^ t) - i*i) & 0xff;
printf("Decrypting %x i=%d t=%d k=%d -> %d\n",p,i,t,(k[i % strlen(k)] ^ t),c);
t = c;//c是改变之前的c
i++;
printf("%c",c);
fputc(c, output);
g++;
if (g>450) {break;}
}
return 0;
}得到
flag{101a6ec9f938885df0a44f20458d2eb4}
MISC
i_have_the_flag#
题目

js代码
查看代码
function hm(s) {
return rh(rstr(str2rstr_utf8(s)));
}
function bm(s) {
return rb(rstr(str2rstr_utf8(s)));
}
function rstr(s) {
return binl2rstr(binl(rstr2binl(s), s.length * 8));
}
function checkToken(s) {
return s === "FAKE-TOKEN";
}
function rh(ip) {
try {
hc
} catch (e) {
hc = 0;
}
var ht = hc ? "0123456789ABCDEF" : "0123456789abcdef";
var op = "";
var x;
for (var i = 0; i < ip.length; i++) {
x = ip.charCodeAt(i);
op += ht.charAt((x >>> 4) & 0x0F) + ht.charAt(x & 0x0F);
}
return op;
}
function rb(ip) {
try {
bp
} catch (e) {
bp = '';
}
var b = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";
var op = "";
var len = ip.length;
for (var i = 0; i < len; i += 3) {
var t = (ip.charCodeAt(i) << 16) | (i + 1 < len ? ip.charCodeAt(i + 1) << 8 : 0) | (i + 2 < len ? ip.charCodeAt(i + 2) : 0);
for (var j = 0; j < 4; j++) {
if (i * 8 + j * 6 > ip.length * 8)
op += bp;
else
op += b.charAt((t >>> 6 * (3 - j)) & 0x3F);
}
}
return op;
}
function ck(s) {
try {
ic
} catch (e) {
return;
}
var a = [118, 108, 112, 115, 111, 104, 104, 103, 120, 52, 53, 54];
if (s.length == a.length) {
for (i = 0; i < s.length; i++) {
if (a[i] - s.charCodeAt(i) != 3)
return ic = false;
}
return ic = true;
}
return ic = false;
}
function str2rstr_utf8(input) {
var output = "";
var i = -1;
var x, y;
while (++i < input.length) {
x = input.charCodeAt(i);
y = i + 1 < input.length ? input.charCodeAt(i + 1) : 0;
if (0xD800 <= x && x <= 0xDBFF && 0xDC00 <= y && y <= 0xDFFF) {
x = 0x10000 + ((x & 0x03FF) << 10) + (y & 0x03FF);
i++;
}
if (x <= 0x7F)
output += String.fromCharCode(x);
else if (x <= 0x7FF)
output += String.fromCharCode(0xC0 | ((x >>> 6) & 0x1F), 0x80 | (x & 0x3F));
else if (x <= 0xFFFF)
output += String.fromCharCode(0xE0 | ((x >>> 12) & 0x0F), 0x80 | ((x >>> 6) & 0x3F), 0x80 | (x & 0x3F));
else if (x <= 0x1FFFFF)
output += String.fromCharCode(0xF0 | ((x >>> 18) & 0x07), 0x80 | ((x >>> 12) & 0x3F), 0x80 | ((x >>> 6) & 0x3F), 0x80 | (x & 0x3F));
}
return output;
}
function rstr2binl(input) {
var output = Array(input.length >> 2);
for (var i = 0; i < output.length; i++)
output[i] = 0;
for (var i = 0; i < input.length * 8; i += 8)
output[i >> 5] |= (input.charCodeAt(i / 8) & 0xFF) << (i % 32);
return output;
}
function binl2rstr(i) {
var o = "";
for (var j = 0; j < i.length * 32; j += 8)
o += String.fromCharCode((i[j >> 5] >>> (j % 32)) & 0xFF);
return o;
}
function binl(x, len) {
s = binl2rstr(x);
x[len >> 5] |= 0x80 << ((len) % 32);
x[(((len + 64) >>> 9) << 4) + 14] = len;
var a = 1732584193;
var b = -271733879;
var c = -1732584194;
var d = 271733878;
for (var i = 0; i < x.length; i += 16) {
var olda = a;
var oldb = b;
var oldc = c;
var oldd = d;
a = ff(a, b, c, d, x[i + 0], 7, -680876936);
d = ff(d, a, b, c, x[i + 1], 12, -389564586);
c = ff(c, d, a, b, x[i + 2], 17, 606105819);
b = ff(b, c, d, a, x[i + 3], 22, -1044525330);
a = ff(a, b, c, d, x[i + 4], 7, -176418897);
d = ff(d, a, b, c, x[i + 5], 12, 1200080426);
c = ff(c, d, a, b, x[i + 6], 17, -1473231341);
b = ff(b, c, d, a, x[i + 7], 22, -45705983);
a = ff(a, b, c, d, x[i + 8], 7, 1770035416);
d = ff(d, a, b, c, x[i + 9], 12, -1958414417);
c = ff(c, d, a, b, x[i + 10], 17, -42063);
b = ff(b, c, d, a, x[i + 11], 22, -1990404162);
a = ff(a, b, c, d, x[i + 12], 7, 1804603682);
d = ff(d, a, b, c, x[i + 13], 12, -40341101);
c = ff(c, d, a, b, x[i + 14], 17, -1502002290);
b = ff(b, c, d, a, x[i + 15], 22, 1236535329);
ck(s);
a = gg(a, b, c, d, x[i + 1], 5, -165796510);
d = gg(d, a, b, c, x[i + 6], 9, -1069501632);
c = gg(c, d, a, b, x[i + 11], 14, 643717713);
b = gg(b, c, d, a, x[i + 0], 20, -373897302);
a = gg(a, b, c, d, x[i + 5], 5, -701558691);
d = gg(d, a, b, c, x[i + 10], 9, 38016083);
c = gg(c, d, a, b, x[i + 15], 14, -660478335);
b = gg(b, c, d, a, x[i + 4], 20, -405537848);
a = gg(a, b, c, d, x[i + 9], 5, 568446438);
d = gg(d, a, b, c, x[i + 14], 9, -1019803690);
c = gg(c, d, a, b, x[i + 3], 14, -187363961);
b = gg(b, c, d, a, x[i + 8], 20, 1163531501);
a = gg(a, b, c, d, x[i + 13], 5, -1444681467);
d = gg(d, a, b, c, x[i + 2], 9, -51403784);
c = gg(c, d, a, b, x[i + 7], 14, 1735328473);
b = gg(b, c, d, a, x[i + 12], 20, -1926607734);
a = hh(a, b, c, d, x[i + 5], 4, -378558);
d = hh(d, a, b, c, x[i + 8], 11, -2022574463);
c = hh(c, d, a, b, x[i + 11], 16, 1839030562);
b = hh(b, c, d, a, x[i + 14], 23, -35309556);
a = hh(a, b, c, d, x[i + 1], 4, -1530992060);
d = hh(d, a, b, c, x[i + 4], 11, 1272893353);
c = hh(c, d, a, b, x[i + 7], 16, -155497632);
b = hh(b, c, d, a, x[i + 10], 23, -1094730640);
a = hh(a, b, c, d, x[i + 13], 4, 681279174);
d = hh(d, a, b, c, x[i + 0], 11, -358537222);
c = hh(c, d, a, b, x[i + 3], 16, -722521979);
b = hh(b, c, d, a, x[i + 6], 23, 76029189);
a = hh(a, b, c, d, x[i + 9], 4, -640364487);
d = hh(d, a, b, c, x[i + 12], 11, -421815835);
c = hh(c, d, a, b, x[i + 15], 16, 530742520);
b = hh(b, c, d, a, x[i + 2], 23, -995338651);
a = ii(a, b, c, d, x[i + 0], 6, -198630844);
d = ii(d, a, b, c, x[i + 7], 10, 1126891415);
c = ii(c, d, a, b, x[i + 14], 15, -1416354905);
b = ii(b, c, d, a, x[i + 5], 21, -57434055);
a = ii(a, b, c, d, x[i + 12], 6, 1700485571);
d = ii(d, a, b, c, x[i + 3], 10, -1894986606);
c = ii(c, d, a, b, x[i + 10], 15, -1051523);
b = ii(b, c, d, a, x[i + 1], 21, -2054922799);
a = ii(a, b, c, d, x[i + 8], 6, 1873313359);
d = ii(d, a, b, c, x[i + 15], 10, -30611744);
c = ii(c, d, a, b, x[i + 6], 15, -1560198380);
b = ii(b, c, d, a, x[i + 13], 21, 1309151649);
a = ii(a, b, c, d, x[i + 4], 6, -145523070);
d = ii(d, a, b, c, x[i + 11], 10, -1120210379);
c = ii(c, d, a, b, x[i + 2], 15, 718787259);
b = ii(b, c, d, a, x[i + 9], 21, -343485551);
a = sa(a, olda);
b = sa(b, oldb);
c = sa(c, oldc);
d = sa(d, oldd);
}
return Array(a, b, c, d);
}
function cmn(q, a, b, x, s, t) {
return sa(br(sa(sa(a, q), sa(x, t)), s), b);
}
function ff(a, b, c, d, x, s, t) {
return cmn((b & c) | ((~b) & d), a, b, x, s, t);
}
function gg(a, b, c, d, x, s, t) {
return cmn((b & d) | (c & (~d)), a, b, x, s, t);
}
function hh(a, b, c, d, x, s, t) {
return cmn(b ^ c ^ d, a, b, x, s, t);
}
function ii(a, b, c, d, x, s, t) {
return cmn(c ^ (b | (~d)), a, b, x, s, t);
}
function sa(x, y) {
var lsw = (x & 0xFFFF) + (y & 0xFFFF);
var msw = (x >> 16) + (y >> 16) + (lsw >> 16);
return (msw << 16) | (lsw & 0xFFFF);
}
function br(n, c) {
return (n << c) | (n >>> (32 - c));
}我的解答:
点击get flag得到信息
Wrong!
1B2M2Y8AsgTpgAmY7PhCfg不知道是啥?base也解不出来。。但我们会发现输入不同的数据去get得到的字符串都不一样。肯定跟第二个文件有关。
我们分析下js代码,我们看到HTML网页上有提示:也就是我们直观看到的那串英文。
在js代码里发现一处关键地方:函数ck(s)。
首先,函数ck(s)接收了一个字符串s作为参数。其函数内部有一个数组a,存储了一组ASCII值。
其次,函数通过比较输入字符串s的字符编码与数组a中的ASCII值来检查if条件。
最后,如果输入字符串s的长度与数组a的长度相等,并且每个字符的编码与数组a中对应位置的ASCII值之差为3,则函数返回true,否则返回false。
因此,根据函数ck(s)的逻辑,我们需要做的就是找到一个字符串,使其满足条件。
通过观察数组a中的ASCII值的范围。可知ASCII值主要集中在小写字母和数字范围内,因此我们可以猜测目标字符串可能是一个由小写字母和数字组成的字符串。
其实我们只需要反着算一下就行了,把数组里的数字都减去3,然后遍历输出字符即可。
def output():
a = [115, 105, 109, 112, 108, 101, 101, 100, 117, 49, 50, 51]
i = 0
while (i < len(a)):
print(chr(a[i]), end='')
i = i + 1
output()
#simpleedu123得到结果后输入到HTML中拿flag
Congratulations!!
flag{muWn9NU0H6erBN/w+C7HVg}
幸运饼干#
题目

我的解答:
打开flag.zip压缩包发现里面还有一个和hint.jpg一模一样的图片,一眼丁真,明文攻击获得压缩包密码
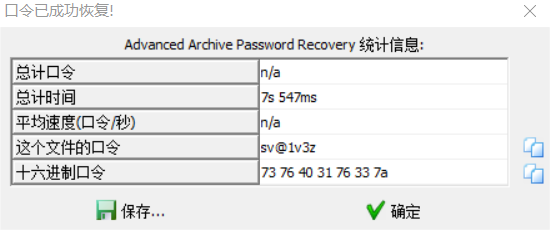
sv@1v3z解压得到:
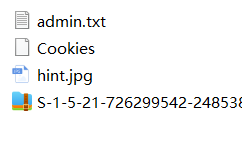
会发现admin.txt里有一个ntlm加密,直接解密即可。
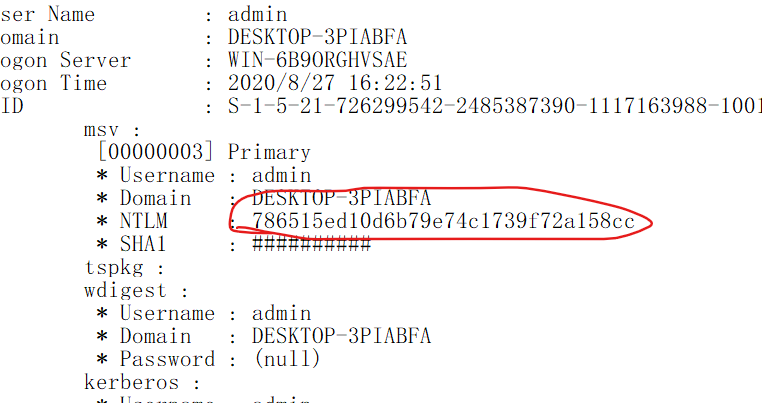
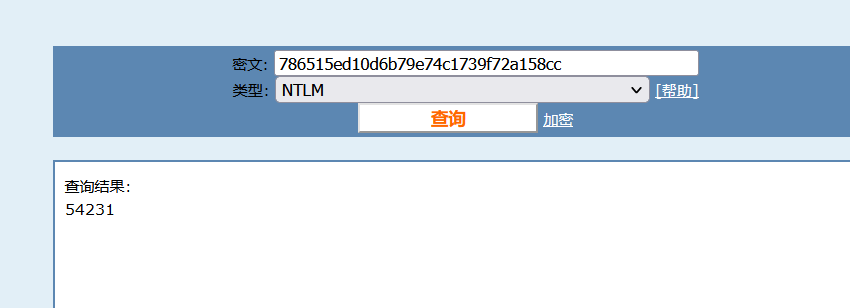
使用010打开 Cookies,很明显的chrome 数据解密
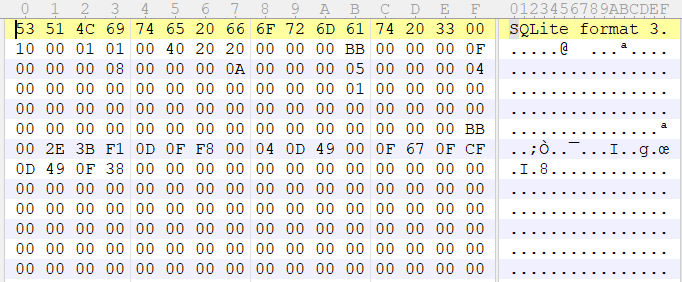
利用上述密码,使用mimikatz工具先爆出masterkey

然后用masterkey解密 Cookies即可。
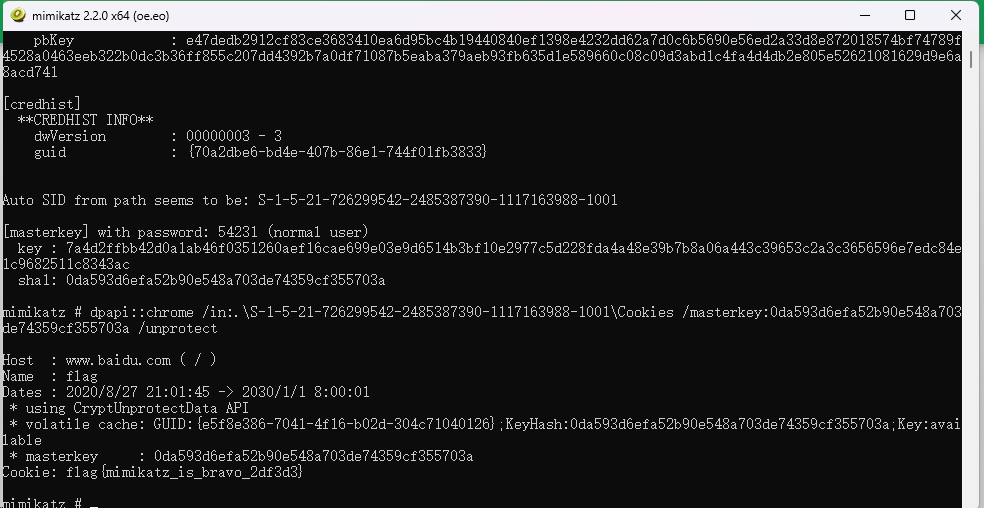
最后flag为flag{mimikatz_is_bravo_2df3d3}
数独#
题目

我的解答:
看到此图感觉里面的数据就是flag,应该是拼图没跑了!

还有一个数独图片,使用在线工具 数独求解 按图片数据位置输进去,点击求解没反应。。。暂时不清楚它要表达什么,先搁着

试试能不能直接拼出来,第一幅图分辨率630x630,分了9个同样大小的方块,因此一个方块是630/9=70,70x70
使用以下工具进行拼图
首先选择新增,导入图片,参数是70;70 注意:参数之间分号隔开。
导入成功后,选择脚本-自动拼接(gaps),参数仍是70;70
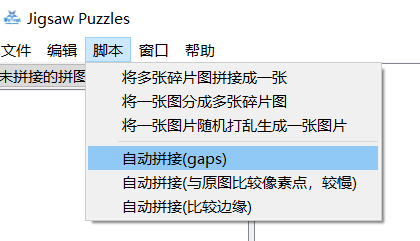
然后等待拼接即可,完成后如下:

根据图中数据读出flag为
flag{4e4d6c332b6fe62a63afe56171fd3725}
算是非预期了,暂时还不知道那个数独图片目的是什么。应该不至于就是为了告诉你可以清楚地看到方块是9x9吧!!耶比!。。

jpginside(未出)#





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通