XSS (跨站脚本攻击) 的原理分析,测试 && 应对措施
1
1
1
XSS (跨站脚本攻击) 的原理分析,测试
1
demo:
<!DOCTYPE html><html lang="en"><head><meta charset="UTF-8"><title>Document</title></head><body><div><h1>XSS test using PHP!</h1><form action="XSS.php"method="GET"><labelfor="">XSS input test!</label><input type="text"name="xss_input"placeholder=""><!-- --><input type="submit"value="Submit"></form><!--<script>alert("XSS alert test!");</script><script>console.log("XSS console.log test!");</script><script>console.log("XSS console.log test!");<⁄script>--></div></body></html><?php$xss=$_GET['xss_input'];// echo "你输入的字符为:<br><mark>".$xss."</mark>";echo"你输入的字符为: <mark>{$xss}</mark>";?>
1 XSS test using PHP!
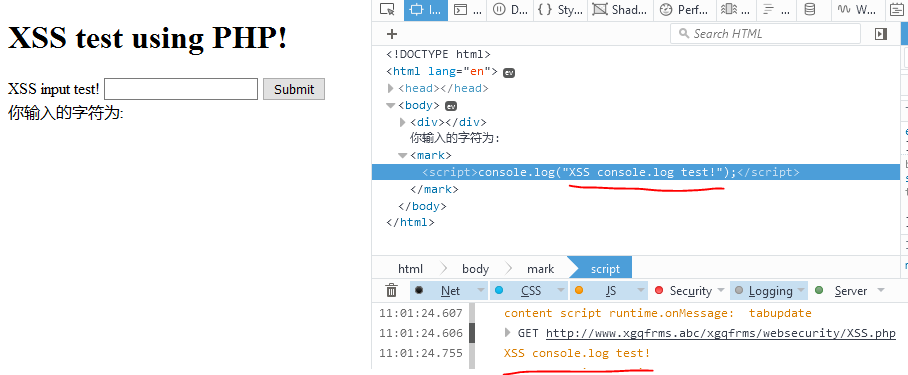
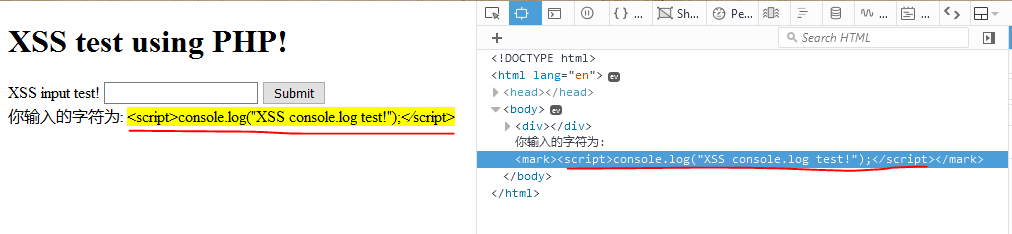
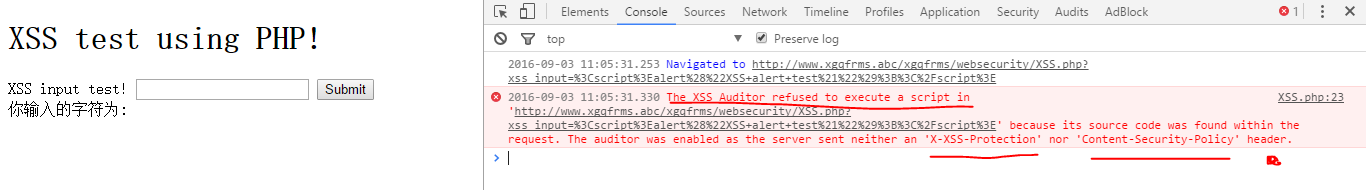
1 <script>console.log("XSS console.log test!");</script>
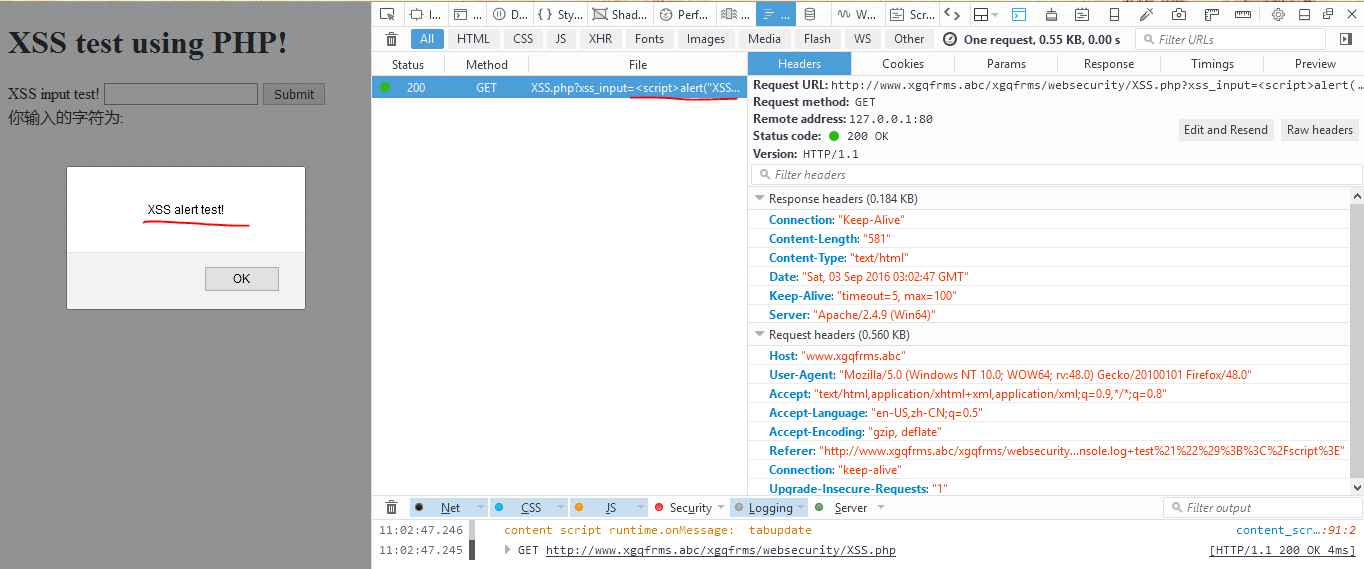
1 <script>alert("XSS alert test!");</script>
1 实体字符: <script>console.log("XSS console.log test!");<⁄script>
1 Chrome 测试: version 52
1
1
1
1
1
1
1
1
1
1
1
1
1
1
XSS 应对措施:
1. CORS
https://fetch.spec.whatwg.org/#http-cors-protocol
Cross-Origin Resource Sharing
W3C Recommendation 16 January 2014
2. CSP
Content Security Policy Level 2
W3C Candidate Recommendation, 21 July 2015
https://www.w3.org/TR/2012/CR-CSP-20121115/
Content Security Policy 1.0
W3C Candidate Recommendation 15 November 2012
1
1
1
1
reference links:
http://www.freebuf.com/articles/web/40520.html
https://segmentfault.com/a/1190000003852910
https://blog.wilddog.com/?p=210
1
1
本文首发于博客园,作者:xgqfrms,原文链接:https://www.cnblogs.com/xgqfrms/p/5836723.html
未经授权禁止转载,违者必究!

 XSS 的原理分析与解剖
实体字符,XSS原理,web 安全,XSS,跨站脚本攻击,
XSS 的原理分析与解剖
实体字符,XSS原理,web 安全,XSS,跨站脚本攻击,






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· AI与.NET技术实操系列(二):开始使用ML.NET
· 记一次.NET内存居高不下排查解决与启示
· 探究高空视频全景AR技术的实现原理
· 理解Rust引用及其生命周期标识(上)
· 浏览器原生「磁吸」效果!Anchor Positioning 锚点定位神器解析
· DeepSeek 开源周回顾「GitHub 热点速览」
· 记一次.NET内存居高不下排查解决与启示
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· .NET10 - 预览版1新功能体验(一)