How to fix the problem that Raspberry Pi cannot use the root user for SSH login All In One
How to fix the problem that Raspberry Pi cannot use the root user for SSH login All In One
如何修复树莓派无法使用 root 用户进行 SSH 登录的问题
应用场景
修改树莓派默认的 pi 用户名和密码后,需要使用 root 用户进行 SSH 登录;
- 对
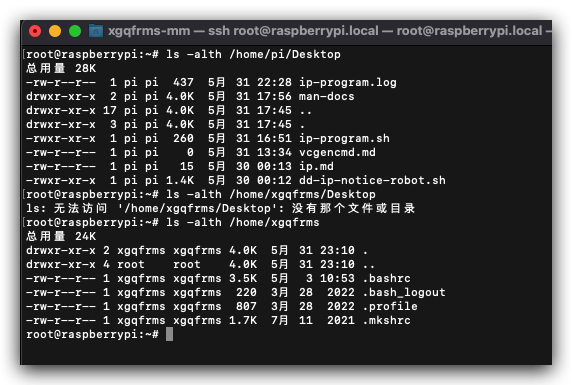
pi/home文件夹进行备份,复制到新用户下xgqfrms/home - 备份后,要
删除pi 用户, 必须切换到其他用户,毕竟 pi 用户不能自己删除自己呀!⚠️
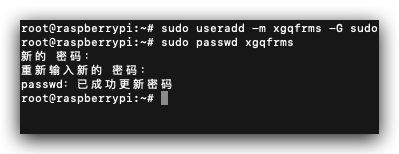
# 添加新用户 xgqfrms, 并且把该用户添加到 sudo 组下
$ sudo useradd -m xgqfrms -G sudo
# 设置新用户的密码
$ sudo passwd xgqfrms
# 备份整个 home 目录
# $ cp /home/pi /home/xgqfrms
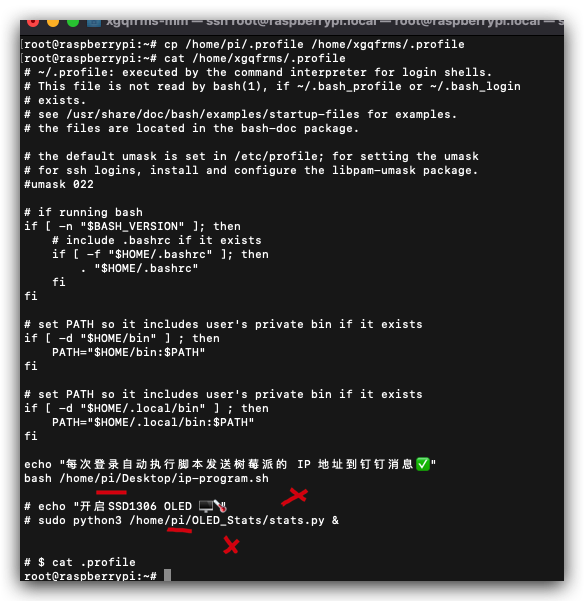
# 仅备份开机后登录自启动配置文件
$ cp /home/pi/.profile /home/xgqfrms/.profile
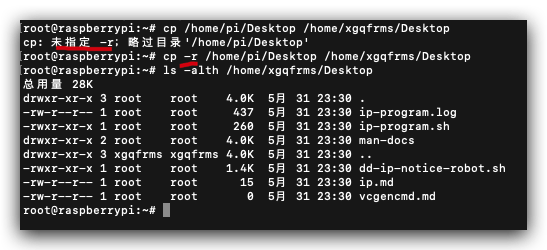
# 仅备份 home 目录下的 Desktop 目录
$ cp -r /home/pi/Desktop /home/xgqfrms/Desktop
# 仅删除用户 pi,保留 pi 的家目录 /pi/home/ (可以复用)
$ sudo deluser pi
# 永久的删除用户 pi 的家目录
$ sudo deluser -remove-home pi
给 root 设置密码后,直接修改并复用
/pi/home/的文件夹 ???
# 待验证 ❓
$ man usermod
# rename, home directory
$ usermod -l xgqfrms pi
# reflect
$ usermod -m -d /home/xgqfrms xgqfrms
# test
$ sudo apt-get update
# disable the root account by locking the password
$ sudo passwd -l root
errors ❌
# pi 用户切换到 root 用户
$ sudo su
# 设置 root 用户的密码
root@raspberrypi:/home/pi# passwd
新的 密码:
重新输入新的 密码:
passwd:已成功更新密码
# 退回到 pi 用户
root@raspberrypi:/home/pi# exit
exit
# pi 用户退出 SSH 登录
$ logout
# pi 用户 SSH 登录正常 ✅
$ ssh pi@raspberrypi.local
# 密码没有错误,但是 root 用户一直无法 SSH 登录 ❌
$ ssh root@raspberrypi.local
root@raspberrypi.local's password:
Permission denied, please try again.
root@raspberrypi.local's password:
Permission denied, please try again.
root@raspberrypi.local's password:
root@raspberrypi.local: Permission denied (publickey,password).
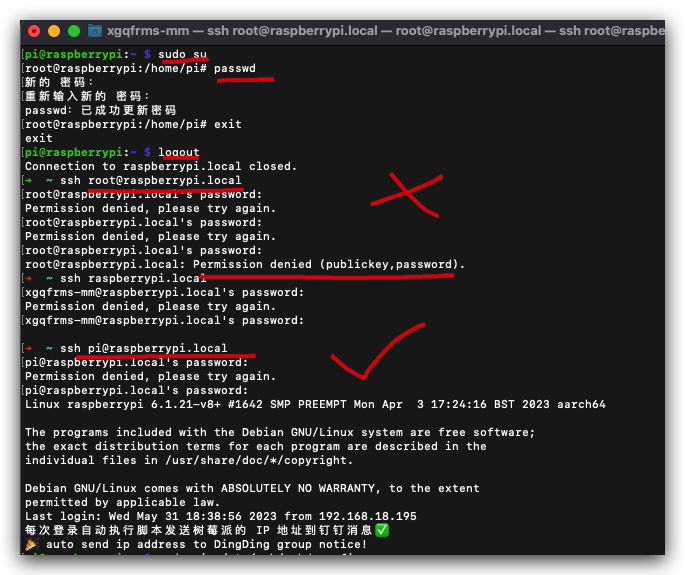
solution ✅
-
要给 root 设置登录密码,默认 root 没有密码
-
要开启 root 的 SSH 登录权限,默认是不允许 root 进行 SSH 访问的
/etc/ssh/sshd_config
# 修改
$ sudo vim /etc/ssh/sshd_config
systemctl
# 重启 sshd 服务
$ systemctl restart sshd
==== AUTHENTICATING FOR org.freedesktop.systemd1.manage-units ===
重新启动“ssh.service”需要认证。
Authenticating as: ,,, (pi)
Password:
==== AUTHENTICATION COMPLETE ===

prohibit-password=>yes
# Authentication:
# 临时打开 ⚠️
LoginGraceTime 2m
PermitRootLogin yes
StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
# Authentication:
+ # 临时打开 ⚠️
+ LoginGraceTime 2m
+ PermitRootLogin yes
+ StrictModes yes
- # LoginGraceTime 2m
- # PermitRootLogin prohibit-password
- # StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
demos
SSH &
/etc/ssh/sshd_config
$ cat /etc/ssh/sshd_config
$ cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
Include /etc/ssh/sshd_config.d/*.conf
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
#HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_ecdsa_key
#HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
#LogLevel INFO
# Authentication:
# 临时打开 ⚠️
LoginGraceTime 2m
PermitRootLogin yes
StrictModes yes
#LoginGraceTime 2m
#PermitRootLogin prohibit-password
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# Expect .ssh/authorized_keys2 to be disregarded by default in future.
#AuthorizedKeysFile .ssh/authorized_keys .ssh/authorized_keys2
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
# Change to yes to enable challenge-response passwords (beware issues with
# some PAM modules and threads)
ChallengeResponseAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
# GSSAPI options
#GSSAPIAuthentication no
#GSSAPICleanupCredentials yes
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
PrintMotd no
#PrintLastLog yes
#TCPKeepAlive yes
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# Allow client to pass locale environment variables
AcceptEnv LANG LC_*
# override default of no subsystems
Subsystem sftp /usr/lib/openssh/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
(🐞 反爬虫测试!打击盗版⚠️)如果你看到这个信息, 说明这是一篇剽窃的文章,请访问 https://www.cnblogs.com/xgqfrms/ 查看原创文章!
passwd & useradd
$ man passwd
$ man passwd > passwd.md
$ cat ./passwd.md
$ man useradd
$ man useradd > useradd.md
$ cat ./useradd.md
passwd generator
# 密码生成器
$ openssl passwd -6
Password:
Verifying - Password:
$6$lamhqyRZlhl38Rzw$G2bIMwmYKnonpg1bLXFiZR233zjkXKzPb12mHD0dsRuWJvTl.be6uJmBl8pcWx2k6n2EeoORnjZawJDfcCATT/

/boot/userconf.txt
$ cat /boot/userconf.txt
pi:/4g6TptuTP5B6
https://www.raspberrypi.com/documentation/computers/configuration.html#configuring-a-user
refs
https://www.cnblogs.com/xgqfrms/p/17446689.html#5181665
©xgqfrms 2012-2021
www.cnblogs.com/xgqfrms 发布文章使用:只允许注册用户才可以访问!
原创文章,版权所有©️xgqfrms, 禁止转载 🈲️,侵权必究⚠️!
本文首发于博客园,作者:xgqfrms,原文链接:https://www.cnblogs.com/xgqfrms/p/17447592.html
未经授权禁止转载,违者必究!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号