How to fix IP filter regular expressions written using grep command in Linux shell script All In One
How to fix IP filter regular expressions written using grep command in Linux shell script All In One
如何修复在 Linux shell 脚本中使用 grep 命令编写的 IP 过滤器正则表达式?
question ❓
It doesn't work in shell script, but in javascript, it works fine, what's wrong?
I just want to filter out all IPs that are not in the range of 2~254, for example, ignore the
255
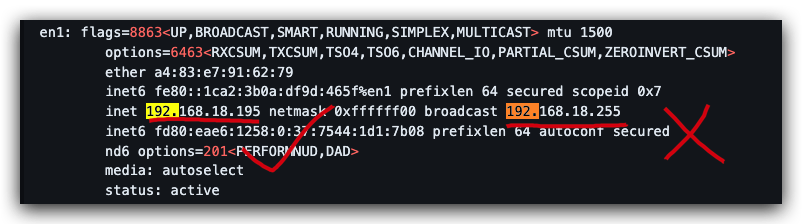
error ❌
just want to filter out the
192.168.18.255
#!/usr/bin/env bash
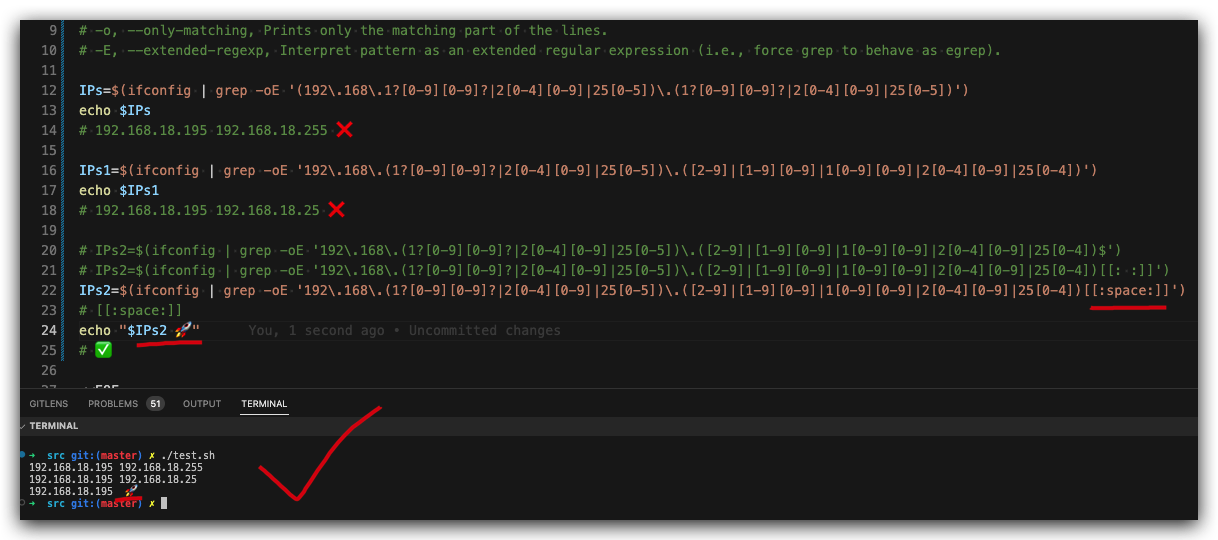
IPs=$(ifconfig | grep -oE '(192\.168\.1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])')
echo $IPs
# 192.168.18.195 192.168.18.255 ❌
IPs1=$(ifconfig | grep -oE '192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])')
echo $IPs1
# 192.168.18.195 192.168.18.25 ❌
IPs2=$(ifconfig | grep -oE '192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])$')
echo $IPs2
# ❌
# wanted, ignore 192.168.18.255 ❓
# IPs=$(ifconfig | grep -oE '❓')
# echo $IPs
# 192.168.18.195
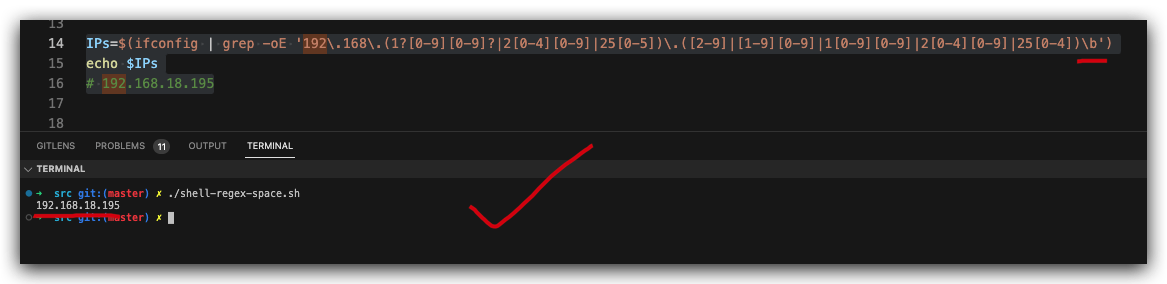
solutions ✅
\b
IPs=$(ifconfig | grep -oE '192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])\b')
echo $IPs
# 192.168.18.195
[[:space:]]
#!/usr/bin/env bash
# [[:space:]] ✅
IPs2=$(ifconfig | grep -oE '192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])[[:space:]]')
echo "$IPs2 🚀"
# ✅
| test environment | result |
|---|---|
| macOS 13.1 | ✅ |
| Raspberry Pi OS x64 | ✅ |
input IPs
$ ifconfig
$ ifconfig
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> mtu 16384
options=1203<RXCSUM,TXCSUM,TXSTATUS,SW_TIMESTAMP>
inet 127.0.0.1 netmask 0xff000000
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x1
nd6 options=201<PERFORMNUD,DAD>
gif0: flags=8010<POINTOPOINT,MULTICAST> mtu 1280
stf0: flags=0<> mtu 1280
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=50b<RXCSUM,TXCSUM,VLAN_HWTAGGING,AV,CHANNEL_IO>
ether f0:18:98:f3:0d:de
nd6 options=201<PERFORMNUD,DAD>
media: autoselect (none)
status: inactive
en6: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
ether ac:de:48:00:11:22
inet6 fe80::aede:48ff:fe00:1122%en6 prefixlen 64 scopeid 0x5
nd6 options=201<PERFORMNUD,DAD>
media: autoselect (100baseTX <full-duplex>)
status: active
ap1: flags=8802<BROADCAST,SIMPLEX,MULTICAST> mtu 1500
options=400<CHANNEL_IO>
ether a6:83:e7:91:62:79
media: autoselect
en1: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=6463<RXCSUM,TXCSUM,TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM>
ether a4:83:e7:91:62:79
inet6 fe80::1ca2:3b0a:df9d:465f%en1 prefixlen 64 secured scopeid 0x7
inet 192.168.18.195 netmask 0xffffff00 broadcast 192.168.18.255
inet6 fd80:eae6:1258:0:37:7544:1d1:7b08 prefixlen 64 autoconf secured
nd6 options=201<PERFORMNUD,DAD>
media: autoselect
status: active
en4: flags=8963<UP,BROADCAST,SMART,RUNNING,PROMISC,SIMPLEX,MULTICAST> mtu 1500
options=460<TSO4,TSO6,CHANNEL_IO>
ether 82:c5:92:66:c0:05
media: autoselect <full-duplex>
status: inactive
en5: flags=8963<UP,BROADCAST,SMART,RUNNING,PROMISC,SIMPLEX,MULTICAST> mtu 1500
options=460<TSO4,TSO6,CHANNEL_IO>
ether 82:c5:92:66:c0:04
media: autoselect <full-duplex>
status: inactive
en3: flags=8963<UP,BROADCAST,SMART,RUNNING,PROMISC,SIMPLEX,MULTICAST> mtu 1500
options=460<TSO4,TSO6,CHANNEL_IO>
ether 82:c5:92:66:c0:00
media: autoselect <full-duplex>
status: inactive
en2: flags=8963<UP,BROADCAST,SMART,RUNNING,PROMISC,SIMPLEX,MULTICAST> mtu 1500
options=460<TSO4,TSO6,CHANNEL_IO>
ether 82:c5:92:66:c0:01
media: autoselect <full-duplex>
status: inactive
awdl0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=6463<RXCSUM,TXCSUM,TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM>
ether b2:1c:61:d6:e4:c3
inet6 fe80::b01c:61ff:fed6:e4c3%awdl0 prefixlen 64 scopeid 0xc
nd6 options=201<PERFORMNUD,DAD>
media: autoselect
status: active
bridge0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=63<RXCSUM,TXCSUM,TSO4,TSO6>
ether 82:c5:92:66:c0:01
Configuration:
id 0:0:0:0:0:0 priority 0 hellotime 0 fwddelay 0
maxage 0 holdcnt 0 proto stp maxaddr 100 timeout 1200
root id 0:0:0:0:0:0 priority 0 ifcost 0 port 0
ipfilter disabled flags 0x0
member: en2 flags=3<LEARNING,DISCOVER>
ifmaxaddr 0 port 11 priority 0 path cost 0
member: en3 flags=3<LEARNING,DISCOVER>
ifmaxaddr 0 port 10 priority 0 path cost 0
member: en4 flags=3<LEARNING,DISCOVER>
ifmaxaddr 0 port 8 priority 0 path cost 0
member: en5 flags=3<LEARNING,DISCOVER>
ifmaxaddr 0 port 9 priority 0 path cost 0
nd6 options=201<PERFORMNUD,DAD>
media: <unknown type>
status: inactive
llw0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=400<CHANNEL_IO>
ether b2:1c:61:d6:e4:c3
inet6 fe80::b01c:61ff:fed6:e4c3%llw0 prefixlen 64 scopeid 0xe
nd6 options=201<PERFORMNUD,DAD>
media: autoselect
status: inactive
utun0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1380
inet6 fe80::cd36:3613:d45c:3ef5%utun0 prefixlen 64 scopeid 0xf
nd6 options=201<PERFORMNUD,DAD>
utun1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 2000
inet6 fe80::b421:12b2:245a:cced%utun1 prefixlen 64 scopeid 0x10
nd6 options=201<PERFORMNUD,DAD>
utun2: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1000
inet6 fe80::ce81:b1c:bd2c:69e%utun2 prefixlen 64 scopeid 0x11
nd6 options=201<PERFORMNUD,DAD>
utun3: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1380
inet6 fe80::9e8d:e6dc:c364:f6df%utun3 prefixlen 64 scopeid 0x12
nd6 options=201<PERFORMNUD,DAD>
utun4: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1380
inet6 fe80::facb:f21b:e5cf:ef54%utun4 prefixlen 64 scopeid 0x13
nd6 options=201<PERFORMNUD,DAD>
utun5: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1380
inet6 fe80::9b81:5e7e:afff:8f8b%utun5 prefixlen 64 scopeid 0x14
nd6 options=201<PERFORMNUD,DAD>
utun6: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1380
inet6 fe80::b3a5:3e87:f36d:c096%utun6 prefixlen 64 scopeid 0x15
nd6 options=201<PERFORMNUD,DAD>
RegExp tools
regexper
/192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])$/
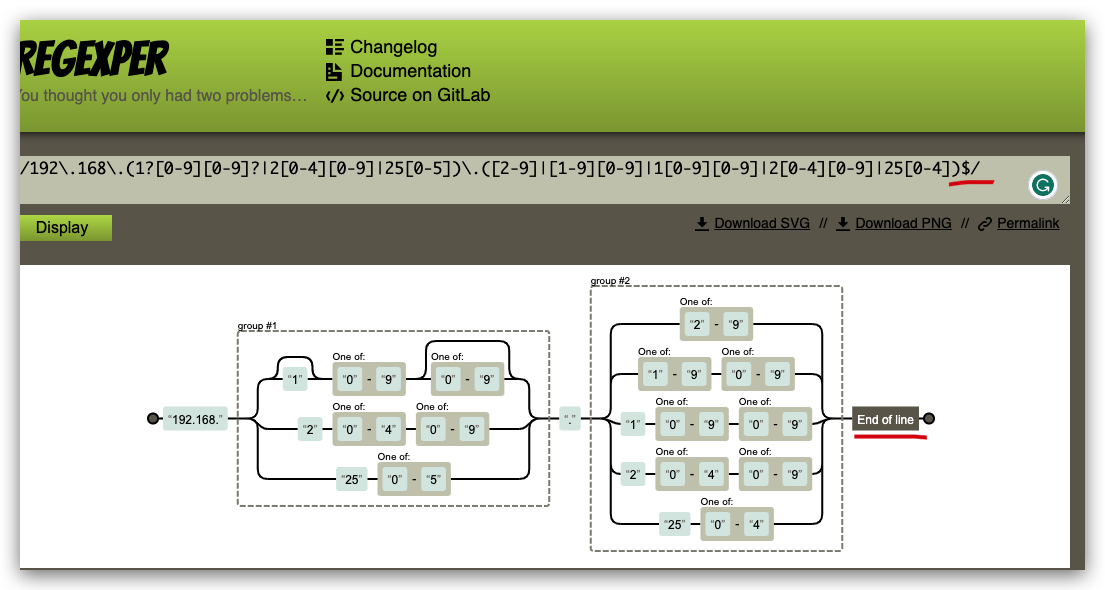
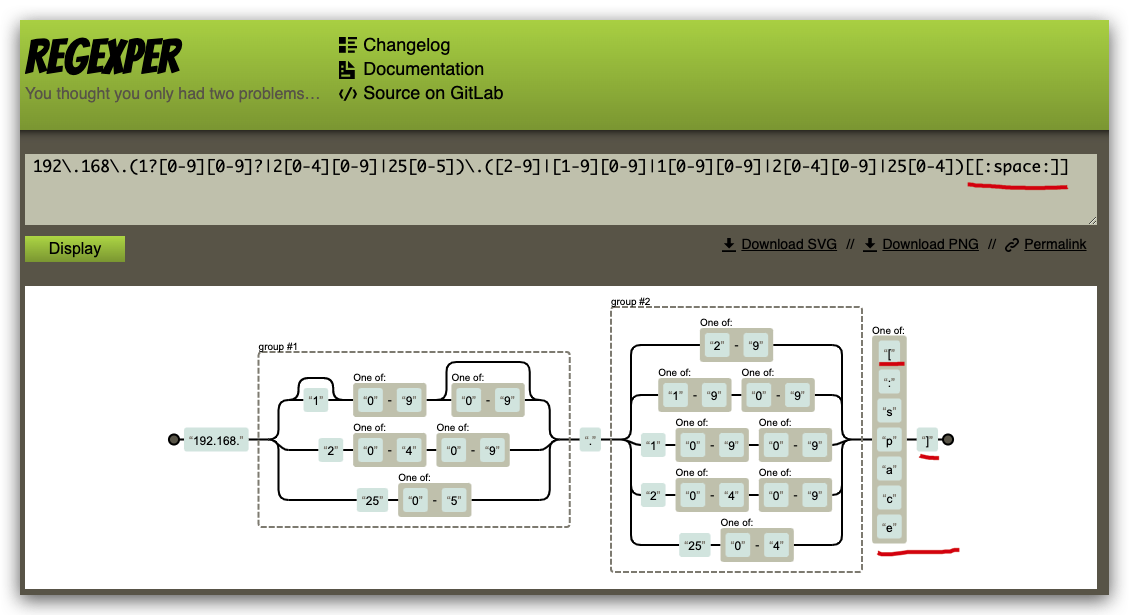
/192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])[[:space:]]/
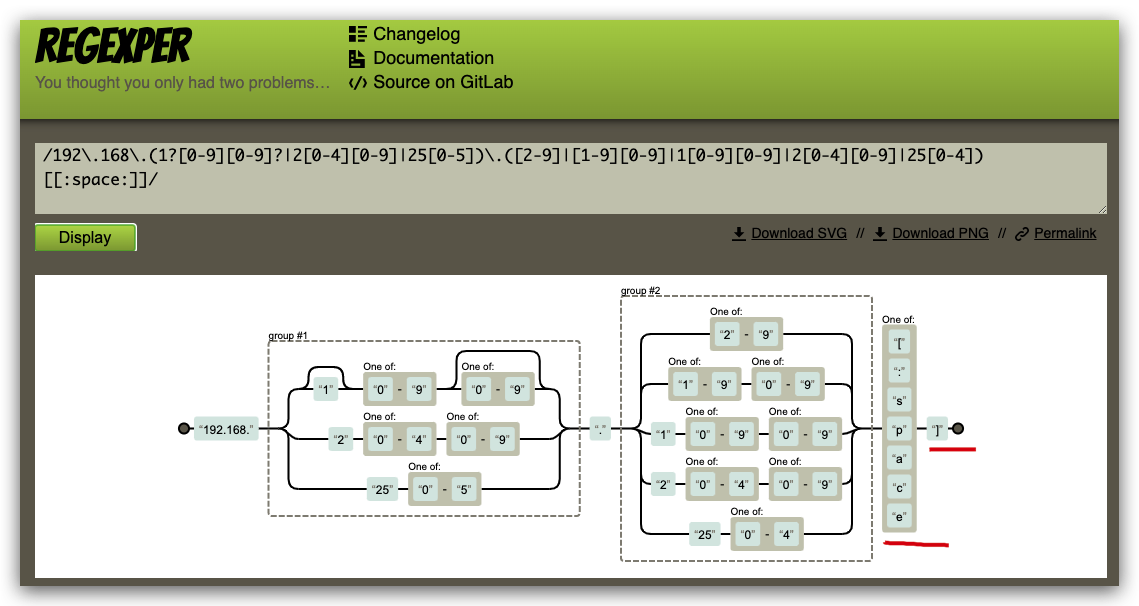
192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])[[:space:]]
regex101
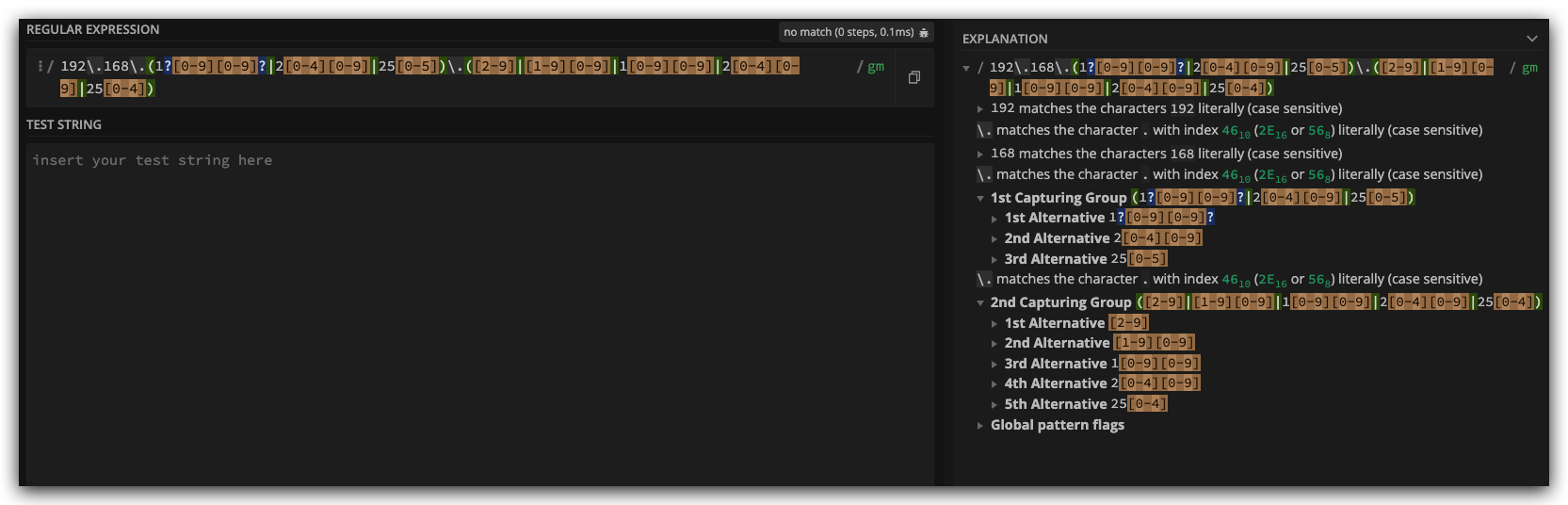
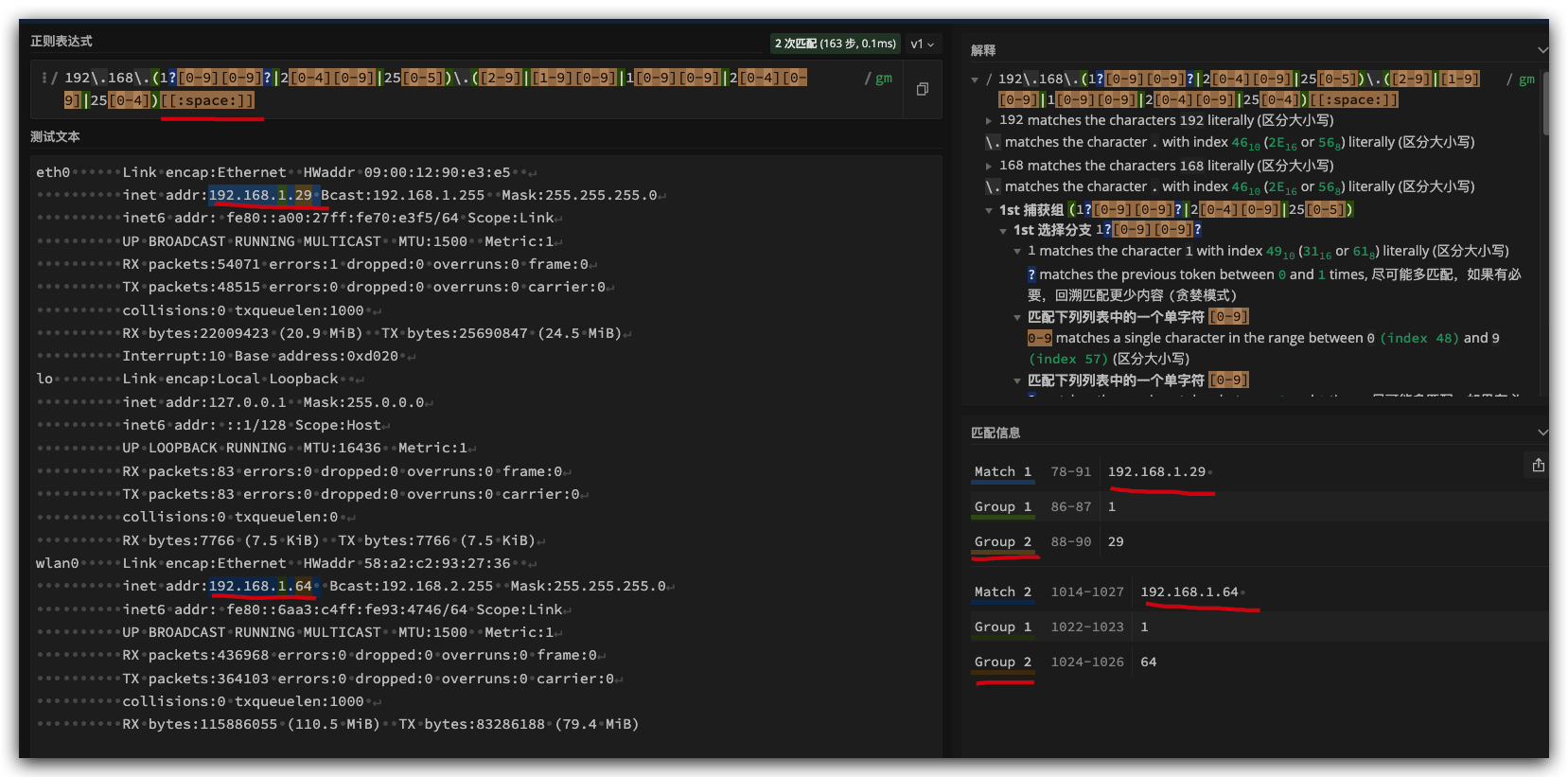
https://regex101.com/r/LY2pjB/1
demos
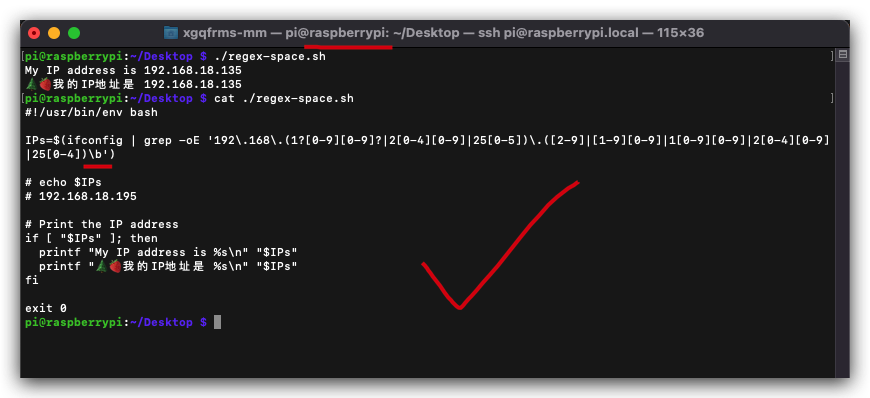
$ ./regex-space.sh
$ cat ./regex-space.sh
#!/usr/bin/env bash
IPs=$(ifconfig | grep -oE '192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])\b')
# echo $IPs
# 192.168.18.195
# Print the IP address
if [ "$IPs" ]; then
printf "My IP address is %s\n" "$IPs"
printf "🌲🍓我的IP地址是 %s\n" "$IPs"
fi
exit 0
$ cat ./ip.sh
#!/usr/bin/env bash
# Print the IP address
_IP=$(hostname -I) || true
if [ "$_IP" ]; then
printf "My IP address is %s\n" "$_IP"
printf "🌲🍓我的IP地址是 %s\n" "$_IP"
fi
exit 0
(🐞 反爬虫测试!打击盗版⚠️)如果你看到这个信息, 说明这是一篇剽窃的文章,请访问 https://www.cnblogs.com/xgqfrms/ 查看原创文章!
javascript
function test(n) {
let reg = /192\.168\.(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.([2-9]|[1-9][0-9]|1[0-9][0-9]|2[0-4][0-9]|25[0-4])$/;
for (let i = 0; i < n; i++) {
let result = reg.test(`192.168.18.${i}`);
if(result) {
// console.log(`192.168.18.${i} ✅`, i, result)
} else {
console.log(`192.168.18.${i} ❌`, i, result)
}
}
}
test(256);
192.168.18.0 ❌ 0 false
192.168.18.1 ❌ 1 false
192.168.18.255 ❌ 255 false
GNU Linux
$ uname -a
Darwin xgqfrms-mm.local 22.2.0 Darwin Kernel Version 22.2.0: Fri Nov 11 02:08:47 PST 2022; root:xnu-8792.61.2~4/RELEASE_X86_64 x86_64
$ uname -a
Linux raspberrypi 5.15.84-v8+ #1613 SMP PREEMPT Thu Jan 5 12:03:08 GMT 2023 aarch64 GNU/Linux
https://raspberrytips.com/which-raspberry-pi-os-is-running/
# Raspberry Pi OS
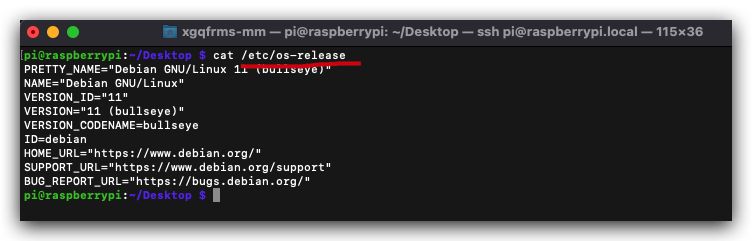
pi@raspberrypi:~/Desktop $ cat /etc/os-release
PRETTY_NAME="Debian GNU/Linux 11 (bullseye)"
NAME="Debian GNU/Linux"
VERSION_ID="11"
VERSION="11 (bullseye)"
VERSION_CODENAME=bullseye
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
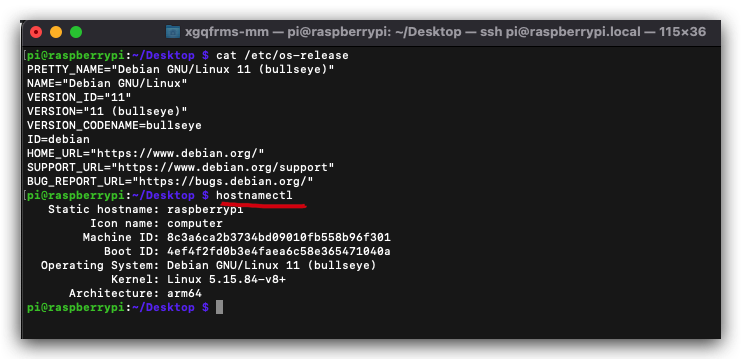
pi@raspberrypi:~/Desktop $ hostnamectl
Static hostname: raspberrypi
Icon name: computer
Machine ID: 8c3a6ca2b3734bd09010fb558b96f301
Boot ID: 4ef4f2fd0b3e4faea6c58e365471040a
Operating System: Debian GNU/Linux 11 (bullseye)
Kernel: Linux 5.15.84-v8+
Architecture: arm64
pi@raspberrypi:~/Desktop $
bullseye 靶心
How to see Raspberry Pi OS
versionon Raspberry PI
https://www.cyberciti.biz/faq/linux-command-print-raspberry-pi-os-version-on-raspberry-pi/
refs
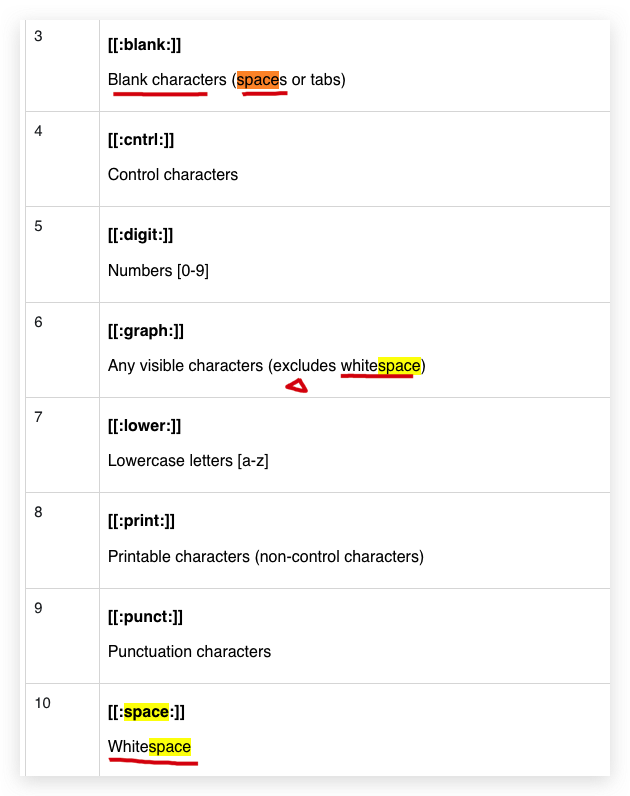
[[:space:]]空格 / Whitespace
https://www.cnblogs.com/xgqfrms/p/17358543.html
https://www.cnblogs.com/xgqfrms/p/17351421.html#5171976
©xgqfrms 2012-2021
www.cnblogs.com/xgqfrms 发布文章使用:只允许注册用户才可以访问!
原创文章,版权所有©️xgqfrms, 禁止转载 🈲️,侵权必究⚠️!
本文首发于博客园,作者:xgqfrms,原文链接:https://www.cnblogs.com/xgqfrms/p/17356060.html
未经授权禁止转载,违者必究!

 How to fix IP filter regular expressions written using grep command in Linux shell script All In One
如何修复在 Linux shell 脚本中使用 grep 命令编写的 IP 过滤器正则表达式?
\b
[[:space:]]
regexper
regex101
How to fix IP filter regular expressions written using grep command in Linux shell script All In One
如何修复在 Linux shell 脚本中使用 grep 命令编写的 IP 过滤器正则表达式?
\b
[[:space:]]
regexper
regex101


 浙公网安备 33010602011771号
浙公网安备 33010602011771号