谷歌浏览器提示客户端和服务器不支持一般 SSL 协议版本或加密套件(亲测有效)SSL
访问网站时,出现如下图所示 “ 此网站无法提供案例连接,客户端和服务器不支持一般 SSL 协议版本或加密套件 ” 的问题。
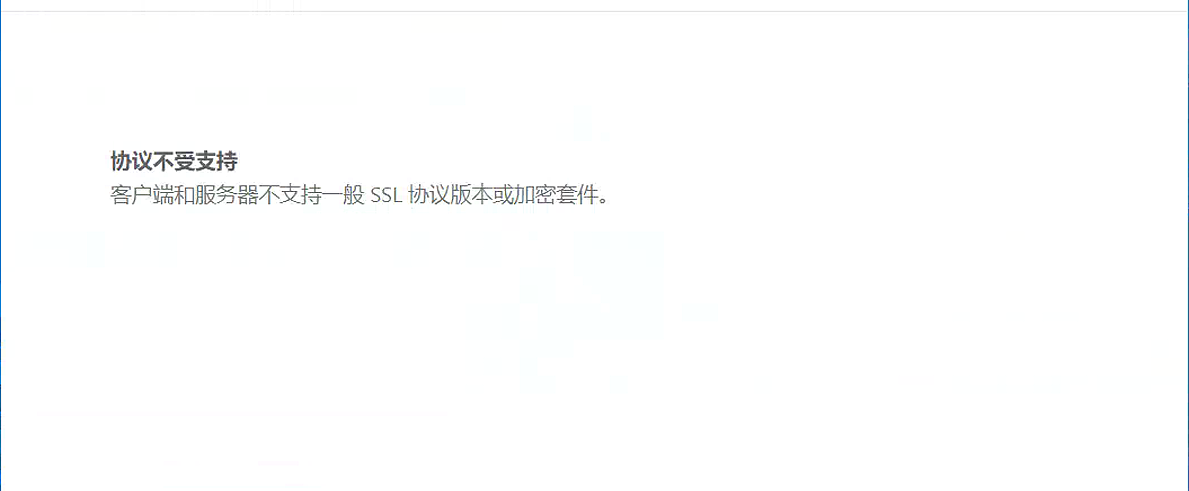
一、定位问题
点击浏览器中网址上面锁头出现如下:
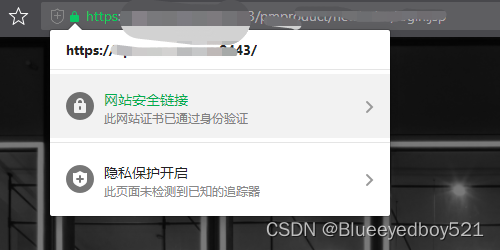
然后点击网站安全链接,出现如下:
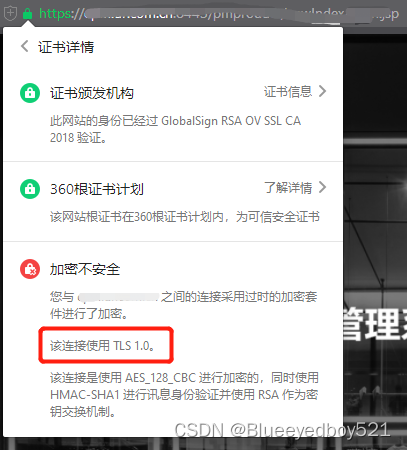
通过对比,可以看到,该域名因为使用的是 TLS 1.0,所以会出现问题,因为谷歌等大部分浏览器已经开始全面禁止TLS1.0了。所以我们需要升级我们的服务端支持TLS1.2以上。
二、升级TLS1.2
1、原理

之前架构
之前Tomcat是监听https的8443端口,在tomcat/conf/server.xml中配置如下:
<Connector port="8080" protocol="HTTP/1.1" URIEncoding="UTF-8" connectionTimeout="20000" compression="on" compressionMinSize="512" compressableMimeType="text/html,text/xml,text/plain,text/javascript,text/csv,application/javascript,application/json,application/xml" /> <Connector protocol="org.apache.coyote.http11.Http11Protocol" URIEncoding="UTF-8" port="8443" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" disableUploadTimeout="false" sslEnabledProtocols="TLSv1,TLSv1.1,TLSv1.2" keystoreFile="../ssl3/sggk.jks" keystorePass="sggk123" ciphers="TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA,TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA,TLS_ECDH_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA,TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA,TLS_ECDH_RSA_WITH_AES_128_CBC_SHA,TLS_ECDH_ECDSA_WITH_RC4_128_SHA,TLS_ECDH_RSA_WITH_RC4_128_SHA,TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA,TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA,TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA,TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA" />
虽然看到tomcat配置支持TLSv1.2,但是由于低版本支持不好,所以配置无效。
调整架构
所以我们需要通过nginx反向代理来监听HTTPS:8443端口,然后转发到tomcat的HTTP:8080
2、配置nginx
配置参考如下:
worker_processes 1; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; underscores_in_headers on;#表示如果header name中包含下划线,则不忽略 #access_log logs/access.log main; sendfile on; keepalive_timeout 65; gzip on; #服务器的集群 upstream www_test { #服务器集群名字 #ip_hash; server 127.0.0.1:8080 ;#服务器配置 weight是权重的意思,权重越大,分配的概率越大。 #server 127.0.0.1:9092 weight=1; } server { listen 443 ssl; server_name www.test.cn; ssl_certificate D:/Tomcat 7.0/ssl/www.test.cn.pem; ssl_certificate_key D:/Tomcat 7.0/ssl/www.test.cn.key; ssl_session_cache shared:SSL:1m; ssl_session_timeout 5m; ssl_ciphers HIGH:!aNULL:!MD5; ssl_prefer_server_ciphers on; # 配置静态资源 location /pm/v4/{ alias "D:/Tomcat 7.0/webapps/pm/v4/"; } location /pm/jslib/{ alias "D:/Tomcat 7.0/webapps/pm/jslib/"; } location /pm/css/{ alias "D:/Tomcat 7.0/webapps/pm/css/"; } location /pm/images/{ alias "D:/Tomcat 7.0/webapps/pm/images/"; } location /pm/temp/{ alias "D:/Tomcat 7.0/webapps/pm/temp/"; } location /pm/main4.0/{ alias "D:/Tomcat 7.0/webapps/pm/main4.0/"; } location /pm{ add_header Cache-Control 'no-store'; client_max_body_size 300m; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_redirect off; proxy_connect_timeout 1; proxy_send_timeout 240; proxy_read_timeout 240; proxy_pass http://www_test/pm; } } }
注意两个ssl证书文件路径
ssl_certificate D:/Tomcat 7.0/ssl/www.test.cn.pem;
ssl_certificate_key D:/Tomcat 7.0/ssl/www.test.cn.key;
证书需要客户提供或者自己去阿里云或者腾讯云申请,它属于nginx专用证书,跟tomcat的不一样
可以参考:nginx配置阿里云/腾讯云申请的免费SSL证书(nginx配置https)
3、配置tomcat
去掉https的配置,只保留http即可
<Connector port="8080" protocol="HTTP/1.1" URIEncoding="UTF-8" connectionTimeout="20000" compression="on" compressionMinSize="512" compressableMimeType="text/html,text/xml,text/plain,text/javascript,text/csv,application/javascript,application/json,application/xml" />
三、访问nginx即可
版权声明:本文为CSDN博主「Blueeyedboy521」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/Blueeyedboy521/article/details/124963562

 浙公网安备 33010602011771号
浙公网安备 33010602011771号