两个异地私有网络通过各自的静态公网地址配置GRE,实现两个跨区域内网互通
网络拓扑图
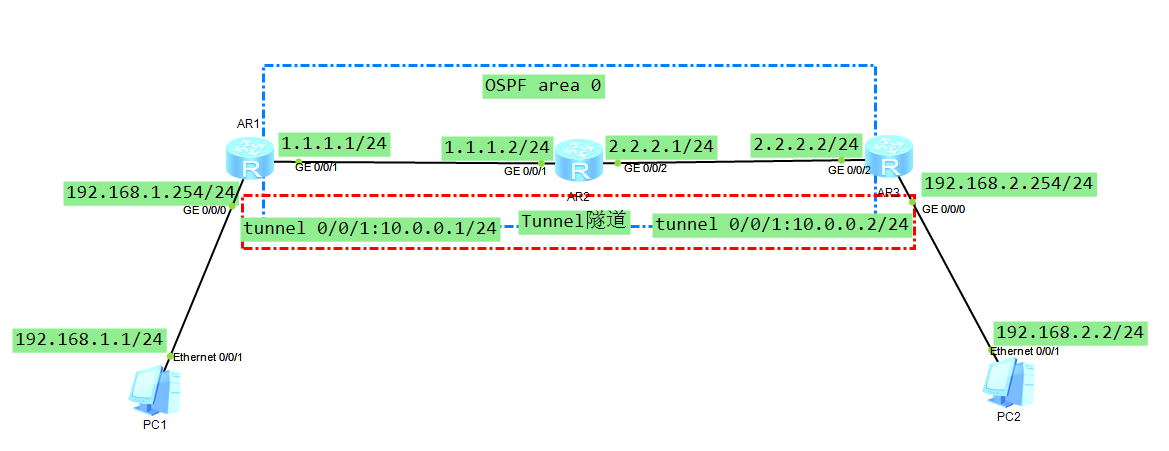
解释:pc1和pc2分别属于一个公司的两个地区的不同私网,pc1所属的区域出口为静态公网地址1.1.1.1,pc2所属的区域出口为静态公网地址2.2.2.2。
需求:
1.实现pc1所在网段可以访问外网;
2.实现pc2所在网段可以访问外网;
3.实现pc1所在网段可以直接通过内网地址访问pc2所在网络。
4.实现pc2所在网段可以直接通过内网地址访问pc1所在网络。
配置步骤:
1.配置路由器和pc机的端口IP。
2.AR1、AR2、AR3直接通过ospf实现路由互通。
3.分别在AR1的ge0/0/1和AR3的ge0/0/2做nat,实现内网访问互联网。
3.分别在AR1和AR3配置GRE。
4.分别在AR1和AR3上配置两个私网到对端内网的路由,使其走gre隧道。
路由器和pc配置如下。
PC1:

AR1:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 | [AR1]display current-configuration [V200R003C00]# sysname AR1# snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00#portal local-server load flash:/portalpage.zip# drop illegal-mac alarm# wlan ac-global carrier id other ac id 0# set cpu-usage threshold 80 restore 75#acl number 2000 rule 5 permit #aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http#firewall zone Local priority 15#interface GigabitEthernet0/0/0 ip address 192.168.1.254 255.255.255.0 #interface GigabitEthernet0/0/1 ip address 1.1.1.1 255.255.255.0 nat outbound 2000#interface GigabitEthernet0/0/2#interface NULL0#interface Tunnel0/0/1 ip address 10.0.0.1 255.255.255.0 tunnel-protocol gre source 1.1.1.1 destination 2.2.2.2#ospf 1 router-id 1.1.1.1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 #ip route-static 192.168.2.0 255.255.255.0 Tunnel0/0/1#user-interface con 0 authentication-mode passworduser-interface vty 0 4user-interface vty 16 20#wlan ac#return |
AR2:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 | [AR2]display current-configuration [V200R003C00]# sysname AR2# snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00#portal local-server load flash:/portalpage.zip# drop illegal-mac alarm# wlan ac-global carrier id other ac id 0# set cpu-usage threshold 80 restore 75#aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http#firewall zone Local priority 15#interface GigabitEthernet0/0/0#interface GigabitEthernet0/0/1 ip address 1.1.1.2 255.255.255.0 #interface GigabitEthernet0/0/2 ip address 2.2.2.1 255.255.255.0 #interface NULL0#ospf 1 router-id 2.2.2.2 area 0.0.0.0 network 1.1.1.2 0.0.0.0 network 2.2.2.1 0.0.0.0 #user-interface con 0 authentication-mode passworduser-interface vty 0 4user-interface vty 16 20#wlan ac#return |
AR3:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 | [AR3]display current-configuration [V200R003C00]# sysname AR3# snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00#portal local-server load flash:/portalpage.zip# drop illegal-mac alarm# wlan ac-global carrier id other ac id 0# set cpu-usage threshold 80 restore 75#acl number 2000 rule 5 permit #aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http#firewall zone Local priority 15#interface GigabitEthernet0/0/0 ip address 192.168.2.254 255.255.255.0 #interface GigabitEthernet0/0/1#interface GigabitEthernet0/0/2 ip address 2.2.2.2 255.255.255.0 nat outbound 2000#interface NULL0#interface Tunnel0/0/1 description 1.1.1.1 ip address 10.0.0.2 255.255.255.0 tunnel-protocol gre source 2.2.2.2 destination 1.1.1.1#ospf 1 router-id 3.3.3.3 area 0.0.0.0 network 2.2.2.2 0.0.0.0 #ip route-static 192.168.1.0 255.255.255.0 Tunnel0/0/1#user-interface con 0 authentication-mode passworduser-interface vty 0 4user-interface vty 16 20#wlan ac#return |
PC2:
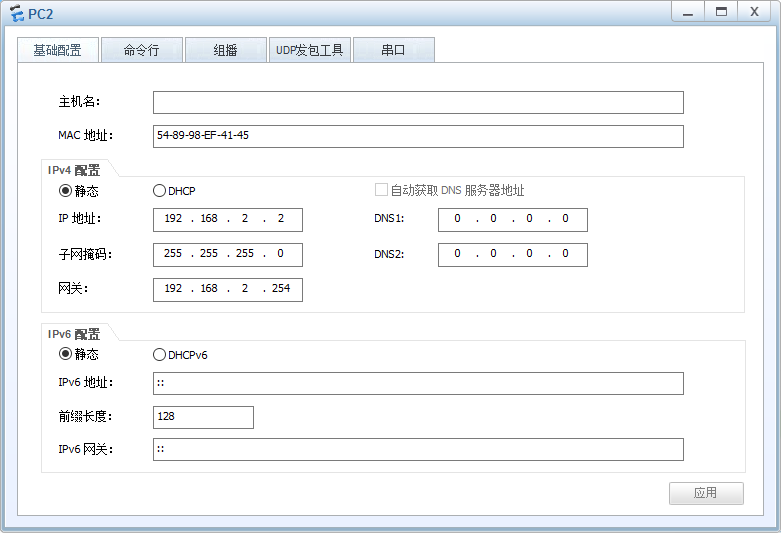
实验结果:

分类:
网络





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)