2021starctf misc部分复现
链接:https://pan.baidu.com/s/1W-3eMXDqFjhp0nsbxf2yAw
提取码:9n6x
little tricks
VHDX (Virtual Hard Disk v2) is the successor format to VHD. Where VHD has a capacity limit of 2040 GB, VHDX has a capacity limit of 64 TB. For disk images with this newer format the filename extension vhdx is used instead of vhd. VHDX protects against power failures and is used by Hyper-V.[23] VHDX can be mounted like VHD.
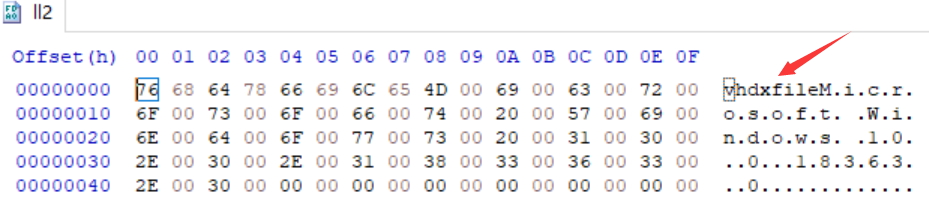
发现是虚拟硬盘(Hyper-V virtual hard disk),添加文件后缀vhdx,双击即可挂载
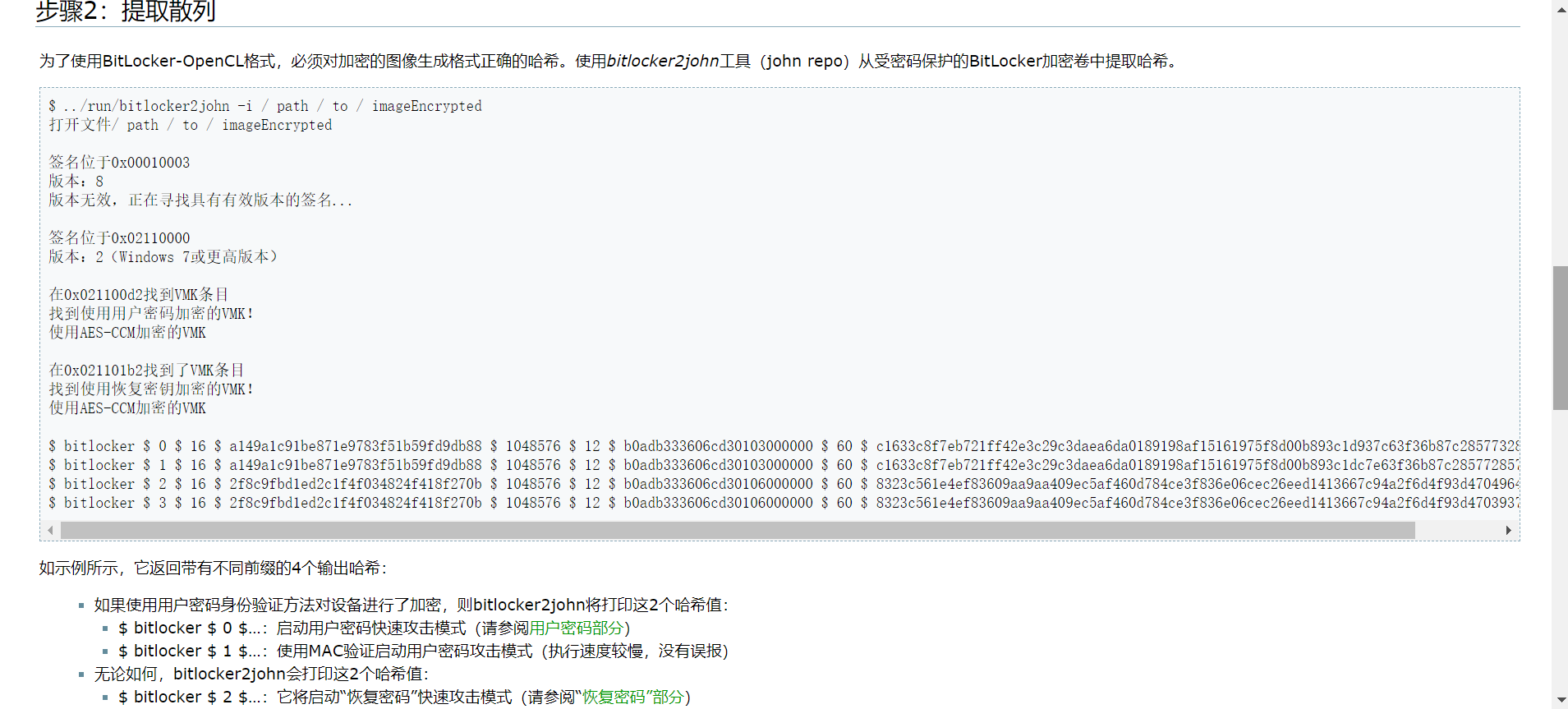
对于虚拟磁盘的破解,尝试用kali自带的bitlocker2john工具提取哈希
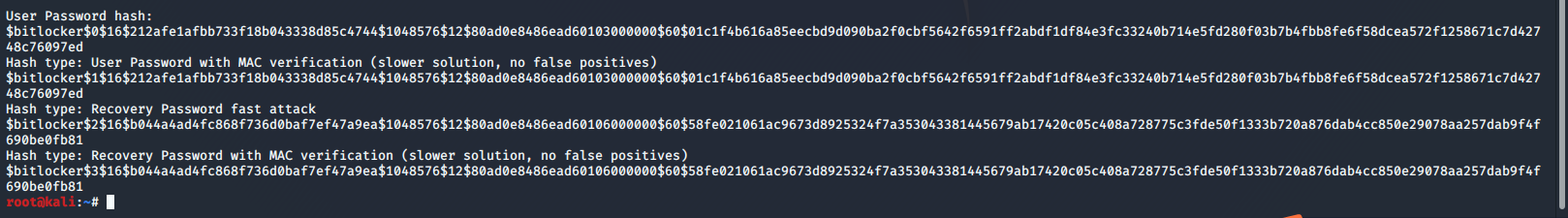
bitlocker2john -i ll2.vhdx
User Password hash:
$bitlocker$0$16$212afe1afbb733f18b043338d85c4744$1048576$12$80ad0e8486ead60103000000$60\(01c1f4b616a85eecbd9d090ba2f0cbf5642f6591ff2abdf1df84e3fc33240b714e5fd280f03b7b4fbb8fe6f58dcea572f1258671c7d42748c76097ed Hash type: User Password with MAC verification (slower solution, no false positives) \)bitlocker$1$16$212afe1afbb733f18b043338d85c4744$1048576$12$80ad0e8486ead60103000000$60\(01c1f4b616a85eecbd9d090ba2f0cbf5642f6591ff2abdf1df84e3fc33240b714e5fd280f03b7b4fbb8fe6f58dcea572f1258671c7d42748c76097ed Hash type: Recovery Password fast attack \)bitlocker$2\(16\)b044a4ad4fc868f736d0baf7ef47a9ea$1048576$12$80ad0e8486ead60106000000$60\(58fe021061ac9673d8925324f7a353043381445679ab17420c05c408a728775c3fde50f1333b720a876dab4cc850e29078aa257dab9f4f690be0fb81 Hash type: Recovery Password with MAC verification (slower solution, no false positives) \)bitlocker$3\(16\)b044a4ad4fc868f736d0baf7ef47a9ea$1048576$12$80ad0e8486ead60106000000$60$58fe021061ac9673d8925324f7a353043381445679ab17420c05c408a728775c3fde50f1333b720a876dab4cc850e29078aa257dab9f4f690be0fb81
https://openwall.info/wiki/john/OpenCL-BitLocker#Step-2Extract-the-hash
在https://hashcat.net/wiki/doku.php?id=example_hashes这个网站查找BitLocker对应的hash-mode,或者hashcat --help搜索。
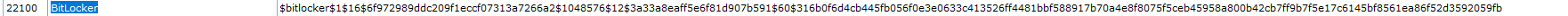
hashcat -m 22100 hash.txt example.dict
执行成功后再加--show查看或查看hashcat.potfile
hashcat -m 22100 hash.txt example.dict --show
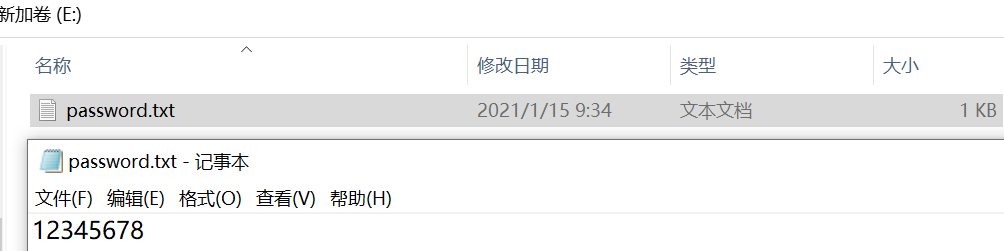
用DiskGenius看看刚挂载的E盘有没有能恢复的数据
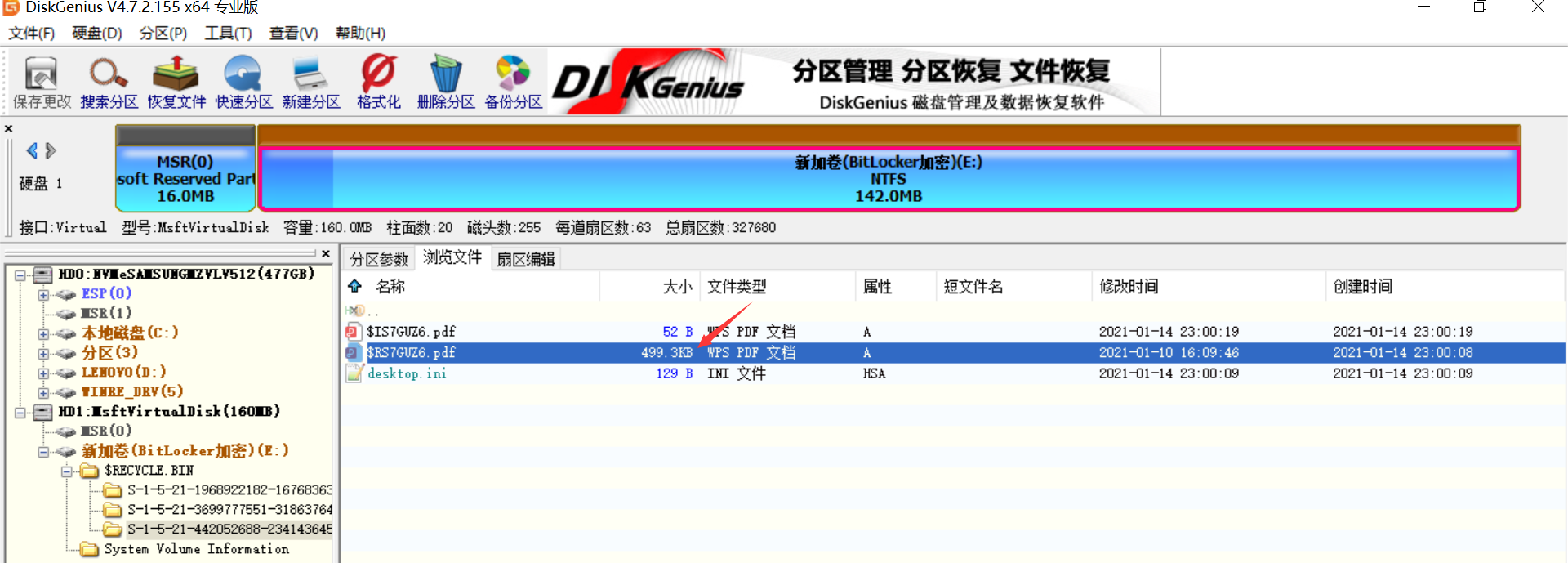
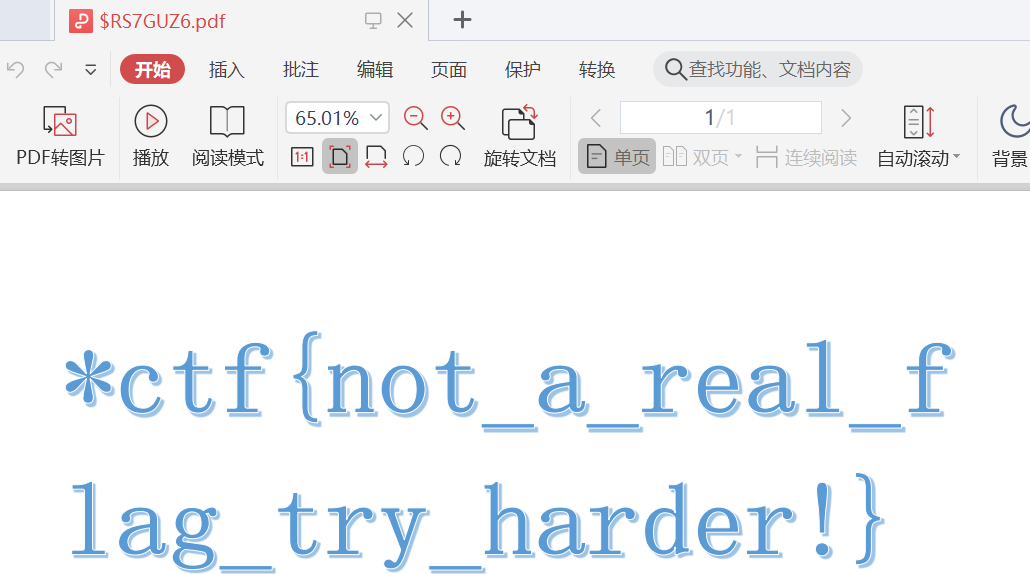
打开大的pdf,看到是一个假flag
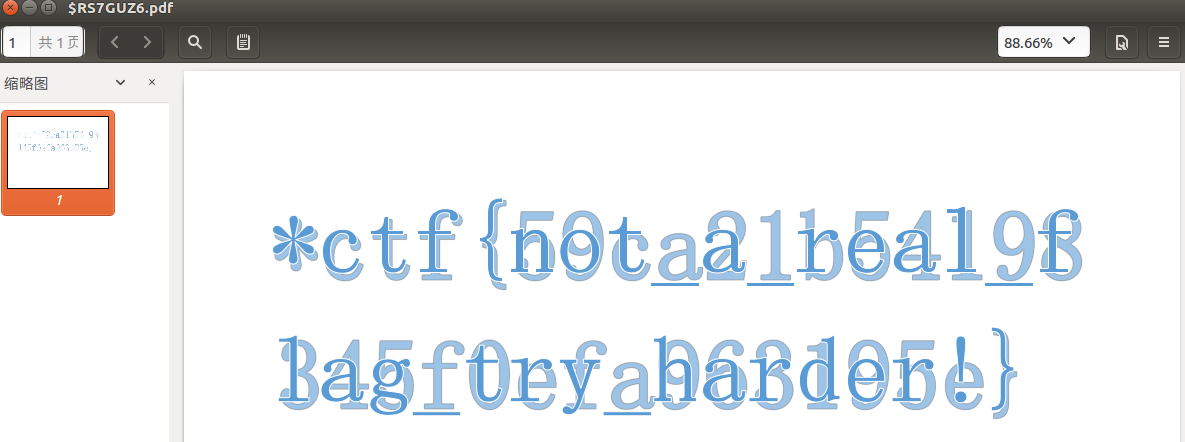
在linux下打开看到真flag
puzzle
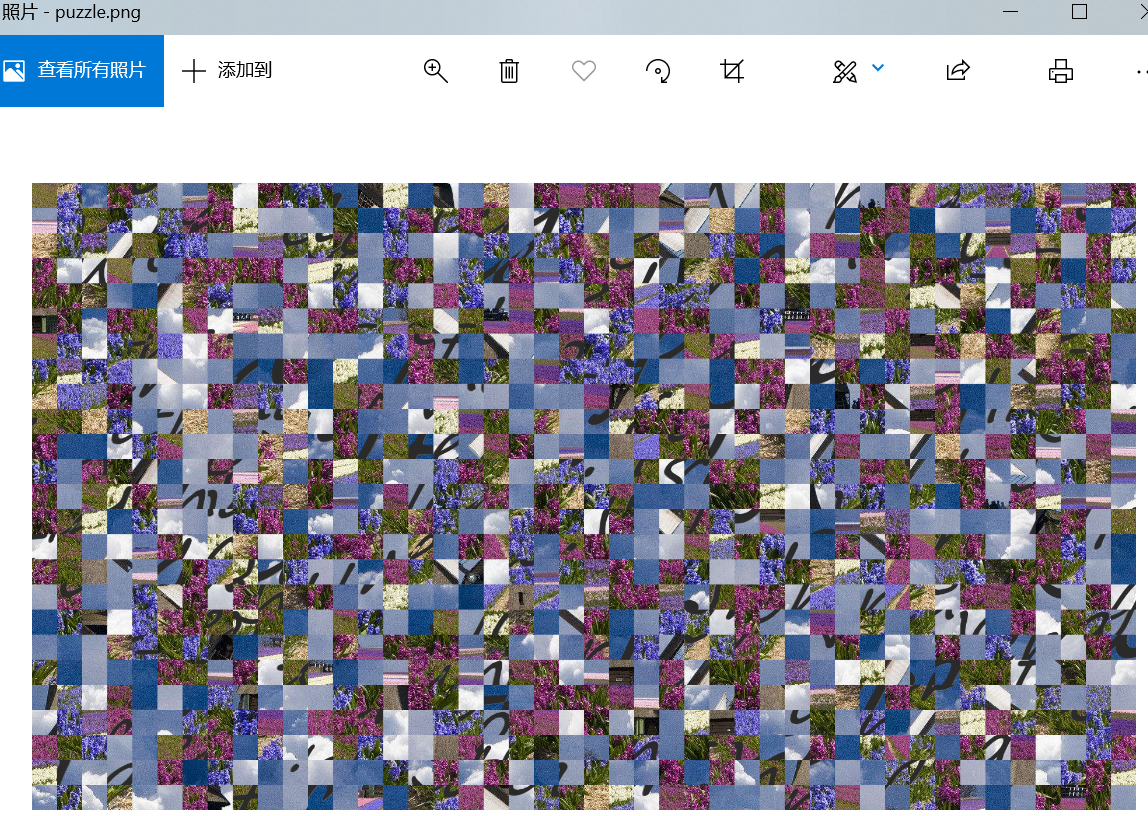
原图是1892*1075pixel,共44*25=1100pieces,each piece is 43*43 pixel
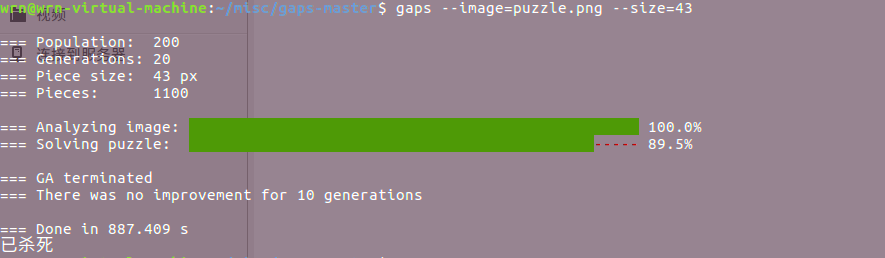
用gaps工具恢复:
gaps --image=puzzle.png --size=43
放弃了放弃了
2020DDCTF有一道拼图题,给了原图和6400个小图
这题原图我找不出来
把puzzle.png分割成1100个小图,脚本:
from PIL import Image
import os
def split_image(img_path, row ,col):
img = Image.open(img_path)
img_name = os.path.splitext(img_path)[0]
width, height = img.size
img_num = 0
for y in range(0, height, height // row):
for x in range(0,width, width // col):
img_num += 1
img_sub = img.crop((x, y, x + width / col, y + height / row))
img_sub.save(f"{img_name}_{img_num}.png")
split_image("puzzle.png", 25, 44)
贴一个官方wp:
这道题有四种思路:
1、手动拼
2、写脚本,对比图片边缘进行拼合,flag使用的颜色比较独特(43,42,42),相邻两块的flag断开后,(43,42,42)在两边缘上的位置只有1~2像素之差,长度也是一样,照此拼合即可。
3、比较简单的一种方法,通过Google识图等找到原图,将原图切成同样块数,和puzzle对比每一块的像素,没有flag的块存在100%符合的对应块,有flag的块的符合度也应在70%以上,按原图拼回即可。
4、最简单的一种方法,通过gaps工具拼图,然后猜测未拼出的字段内容即可(这种算是非预期方法,flag忘记混淆了 😦 )